
February 2025 Android Updates by Google; Severe Flaws in VMware & Microsoft’s Azure AI
Recent days have brought a wave of critical security updates from major tech players, addressing vulnerabilities that could pose significant risks to users and organizations worldwide.
Google has rolled out its February 2025 Android security updates, addressing 46 vulnerabilities across its ecosystem. Among these, CVE-2024-53104, a Kernel vulnerability, has drawn particular attention due to reports of limited, targeted exploitation. This update also patches flaws in third-party components provided by Arm, Imagination Technologies, MediaTek, Unisoc, and Qualcomm.
Meanwhile, other tech giants are also on high alert. Broadcom and Microsoft have released updates to tackle severe flaws in products like VMware, Azure AI, as well as Microsoft Account.
Latest Android Vulnerabilities: Exploitation of CVE-2024-53104 and Other Risks
The actively exploited vulnerability announced in the February 2025 Android security updates, CVE-2024-53104, impacts the USB Video Class (UVC) driver within the Linux kernel. With a CVSS score of 7.8, this high-severity privilege escalation flaw enables attackers to gain elevated physical access privileges, posing a significant security risk.
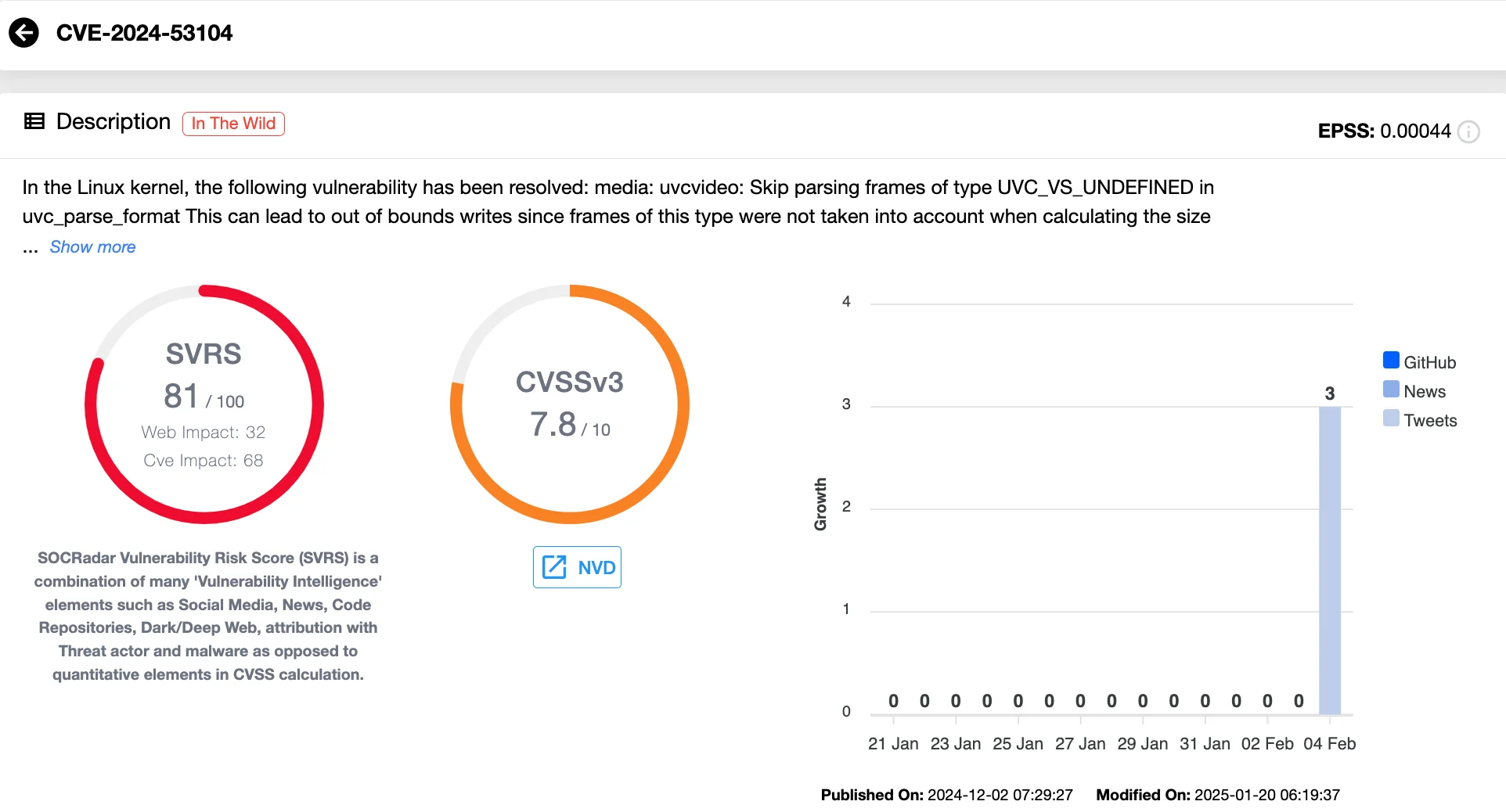
Vulnerability card of CVE-2024-53104 (SOCRadar Vulnerability Intelligence)
Details of CVE-2024-53104
The CVE-2024-53104 vulnerability stems from an out-of-bounds write issue within the UVC driver, specifically in the uvc_parse_format() function inside uvc_driver.c. The issue arises when frames of type UVC_VS_UNDEFINED are not accounted for while calculating the buffer size in uvc_parse_streaming. This oversight could lead to memory corruption, program crashes, or even arbitrary code execution.
A December Linux kernel CVE announcement confirmed that this vulnerability traces back to Linux kernel version 2.6.26, first released in 2008. To address the issue, a patch has been introduced that bypasses parsing frames of this type, effectively mitigating the exploit.
Qualcomm WLAN Vulnerability (CVE-2024-45569)
In addition, Google’s update also addresses CVE-2024-45569, a critical vulnerability in Qualcomm’s WLAN component with a CVSS score of 9.8. This flaw could result in memory corruption, posing significant risks to devices using Qualcomm hardware.
Apply the February 2025 Android Security Update
To ensure that your Android device is protected against these vulnerabilities, check the security patch level. Google has released two patch levels as part of the February updates:
- 2025-02-01 Patch Level: Addresses vulnerabilities associated with the 2025-02-01 security patch level.
- 2025-02-05 Patch Level: Addresses all vulnerabilities included in the 2025-02-01 patch level, as well as additional fixes.
For more information, visit the official Android security bulletin.
Identifying and addressing vulnerabilities quickly is vital to defending your business and reputation, but it can be a challenge with the emergence of new CVEs each day. SOCRadar’s Vulnerability Intelligence module helps you overcome this challenge by allowing the tracking, analysis, and assessment of vulnerabilities in real-time. It ensures you stay on top of critical vulnerabilities that could impact your digital assets, enabling you to prioritize your patching and remediation efforts effectively.
Track new CVEs and hacker trends with SOCRadar Vulnerability Intelligence
Additionally, the module helps you track vulnerability lifecycles, from discovery to exploitation, offering detailed insights into risk levels and potential impacts. With up-to-date intelligence on emerging vulnerabilities, trends, and exploits, SOCRadar ensures your defenses are always aligned with the latest threats, giving you the tools to keep track of and mitigate risks.
VMware Security Updates: Important Information Disclosure (CVE-2025-22218) and More
Shifting focus to another critical development, VMware has released patches to address multiple vulnerabilities in VMware Aria Operations for Logs and VMware Aria Operations. Among these, the most severe is CVE-2025-22218, an information disclosure vulnerability that has been assigned a CVSS score of 8.5, categorizing it as high severity.
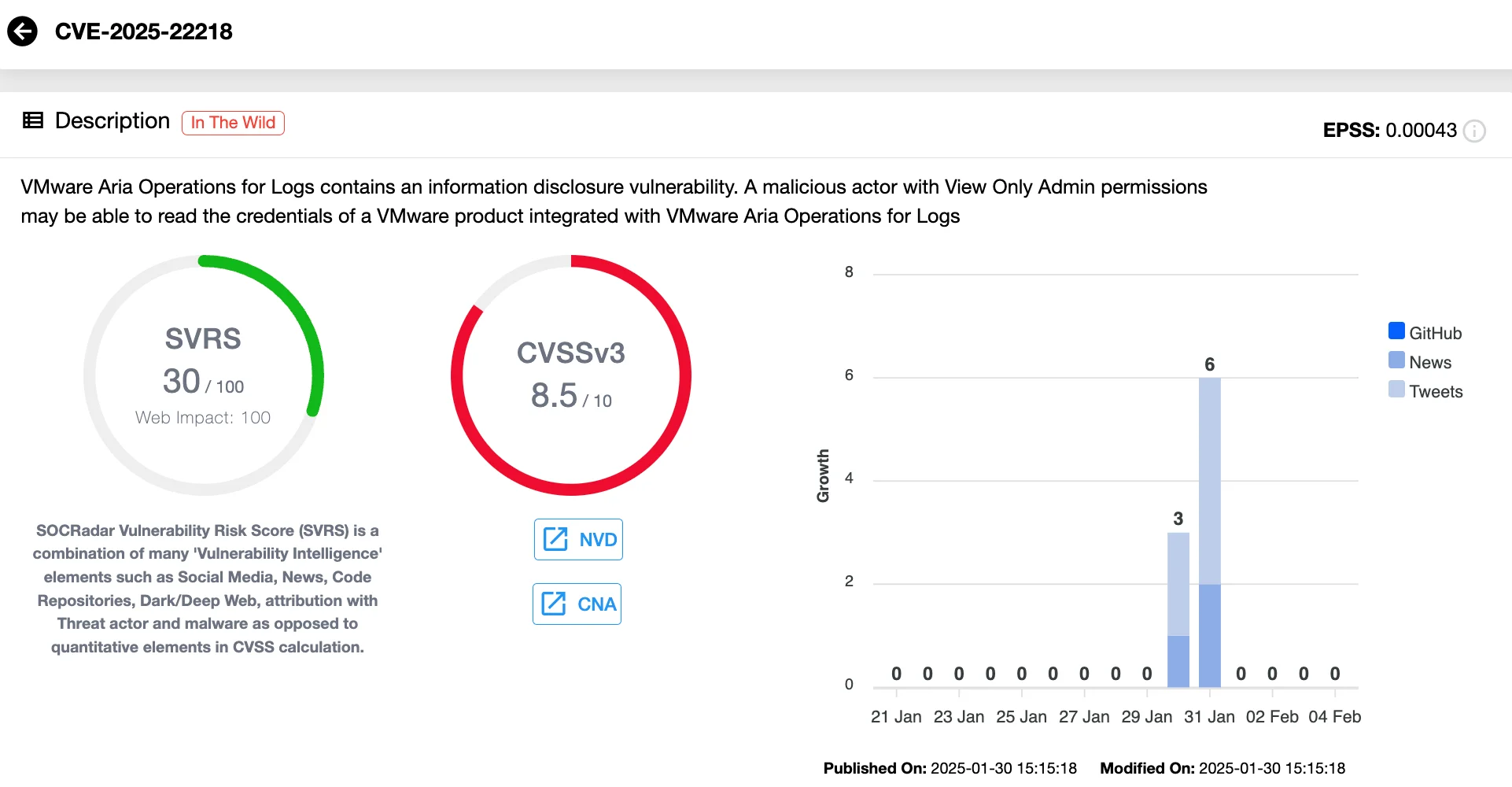
Vulnerability card of CVE-2025-22218 (SOCRadar Vulnerability Intelligence)
CVE-2025-22218 affects VMware Aria Operations for Logs and could allow a malicious actor with View Only Admin permissions to access credentials for an integrated VMware product. This could lead to unauthorized access and potential compromise of critical systems.
The issue has been addressed through patches, and organizations using the affected products are strongly urged to update to the fixed versions listed in VMware’s security advisory.
Alongside CVE-2025-22218, VMware has also patched several other vulnerabilities:
- CVE-2025-22222: An information disclosure vulnerability in VMware Aria Operations (CVSS 7.7)
- CVE-2025-22219: A stored cross-site scripting (XSS) vulnerability (CVSS 6.8)
- CVE-2025-22221: Another stored XSS vulnerability (CVSS 5.2)
- CVE-2025-22220: A privilege escalation flaw due to broken access control (CVSS 4.3)
The vulnerabilities impact the following VMware products:
- VMware Aria Operations for Logs: Versions 8.x
- VMware Aria Operations: Versions 8.x
- VMware Cloud Foundation: Versions 5.x, 4.x
No Workarounds Available
It is important to note that VMware has not provided any workarounds for these vulnerabilities. The only recommended mitigation is applying the available patches as soon as possible. Organizations using the affected VMware products should consult VMware’s security advisory for update instructions.
Critical Vulnerabilities in Azure AI and Microsoft Account
Let’s wrap up this list of important security updates by highlighting Microsoft’s most recent security patches, which fix two flaws in Azure AI Face Service and Microsoft Account that are considered critical in advisories and could give attackers the ability to escalate privileges.
The first vulnerability, CVE-2025-21415, is a critical severity authentication bypass vulnerability (CVSS 9.9) affecting Azure AI Face Service. Reportedly, its exploitation could allow an authenticated attacker to escalate privileges over a network by spoofing authentication mechanisms.
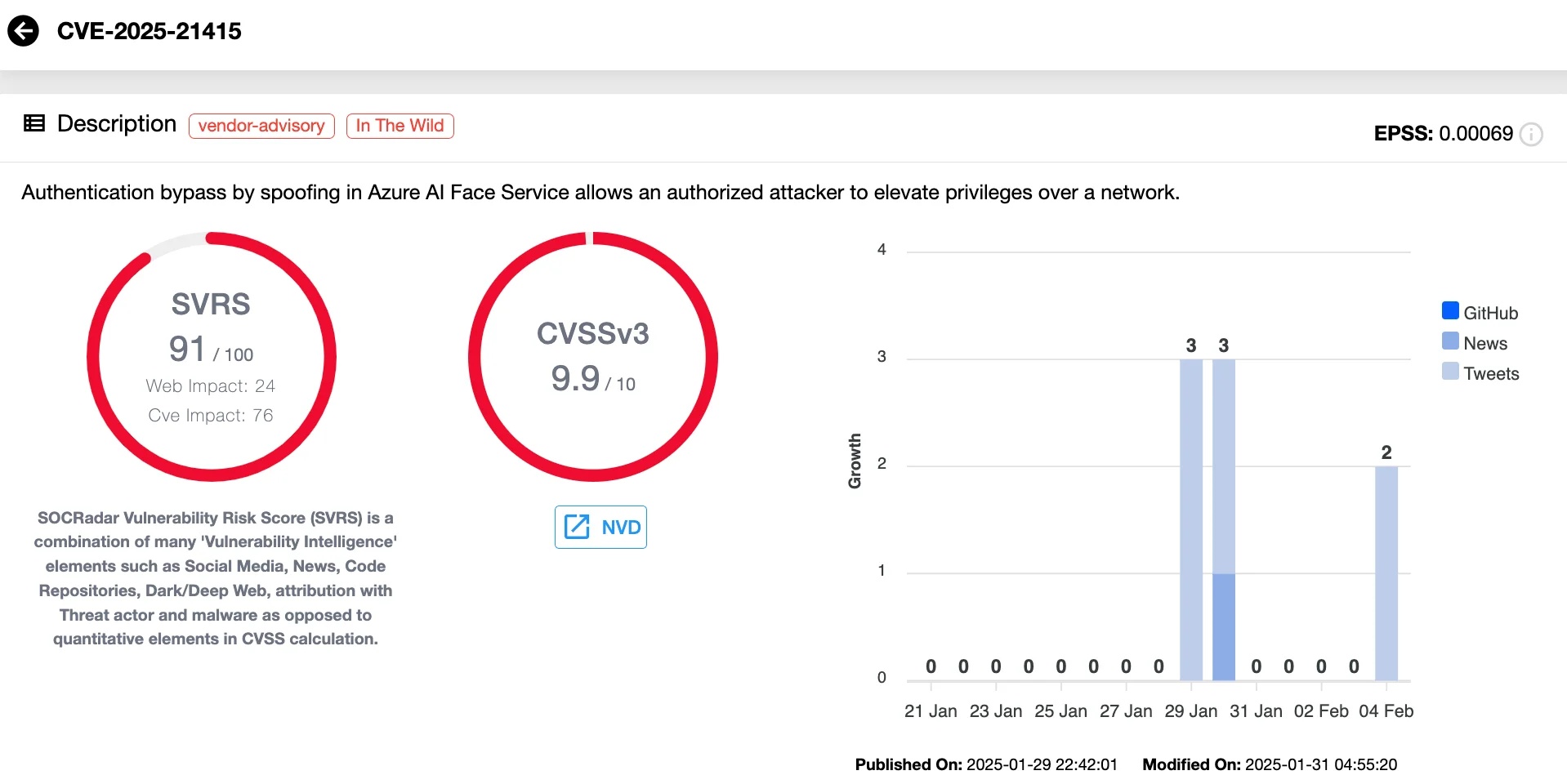
Vulnerability card of CVE-2025-21415 (SOCRadar Vulnerability Intelligence)
While Microsoft has acknowledged the existence of a Proof-of-Concept (PoC) exploit code, it notes that the attack is not practical for most systems and may require significant modifications by a skilled attacker. Organizations relying on Azure AI Face Service should prioritize applying the available patches to mitigate potential exploitation risks.
The second vulnerability, CVE-2025-21396 (CVSS 7.5), is less severe but still poses a high security risk. It is a privilege escalation flaw caused by missing authorization in Microsoft Account. An unauthorized attacker could exploit this flaw to elevate privileges over a network, potentially gaining unauthorized access to sensitive resources.
Cyber threats are becoming increasingly sophisticated, and every organization is at risk of being compromised. You need more than just basic defenses to keep up with the landscape. For this, SOCRadar’s Attack Surface Management (ASM) module offers continuous visibility into your digital assets.
Monitor your digital assets and company vulnerabilities with SOCRadar’s ASM module
With its advanced monitoring, the ASM module identifies vulnerabilities, malicious activities, and potential exploits targeting your systems. It ensures that your network is fully secured, helping you prevent threats before they can cause harm.



































