
What Do You Need to Know About Apache HTTP Server CVE-2021-41773 Vulnerability
One of the world’s most significant open-source projects, Apache is a free and open-source cross-platform HTTP web server. Apache is responsible for handling back-and-forth communication between the server and the browser. Apache has been developed since 1995 by a community consisting of all volunteers. Since 1995, more than 4.3 billion lines of code have been written and changed while creating Apache.
King of the Web: Apache
Apache is still one of the most used HTTP server clients even though it was first published in 1999. In 2009, Apache became the first web software to operate on more than 100 million websites. In 2021, Apache was found to be using %24.63 of the million busiest websites, ranking first in web server clients (source: Netcraft).
The reasons for Apache’s popularity are that it is stable and versatile, it is beginner-friendly and easy to configure, and it has a vast community to get help. However, it has its drawbacks. For example, on websites with extreme traffic, the Apache server can have performance issues.
Having been operating on a quarter of the million busiest websites, a flaw in Apache could have devastating results for most of the internet. Apache’s and other commonly used web clients’ security is vital for websites. Unfortunately, a vulnerability, CVE-2021-41773, was found exploited-in-the-wild affecting Apache version 2.4.49.
After the vulnerability was exposed, the Apache Foundation has released a fix for the Apache HTTP Server, version 2.4.50. However, the fix was incomplete. Luckily, the vulnerability was patched after the 2.4.51 update. Analysts at SOCRadar suggest updating the Apache HTTP server to the newest version for every company using it.
Simple yet Destructive: CVE-2021-41773
The vulnerability was found in a change made to path normalization in Apache 2.4.49. A threat actor was able to use a path traversal attack, where the threat actor aims to access files outside the webroot folder and map URLs to files outside the root directory. If these external files are not protected, the attacker could succeed in accessing the files by the path traversal attack. In addition, if CGI scripts were enabled for the exploited paths, a remote code execution attack was also possible.
The vulnerability was named “CWE-22: Improper Limitation of a Pathname to a Restricted Directory (Path Traversal)” by the Common Weakness Enumeration (CWE) community. The CWE community states that the vulnerability was that the software in the Apache HTTP server did not check and eliminate special characters that can enable the threat actor to access a location outside of the restricted directory.
Many servers were exploited with this vulnerability before it was patched, and many more could still be exploited if the Apache software is not updated to at least version 2.4.51.
Several researchers have provided different PoCs (proof of concepts) for the vulnerability in various platforms like GitHub and Twitter. A sample one-liner PoC taken from Twitter is given below:
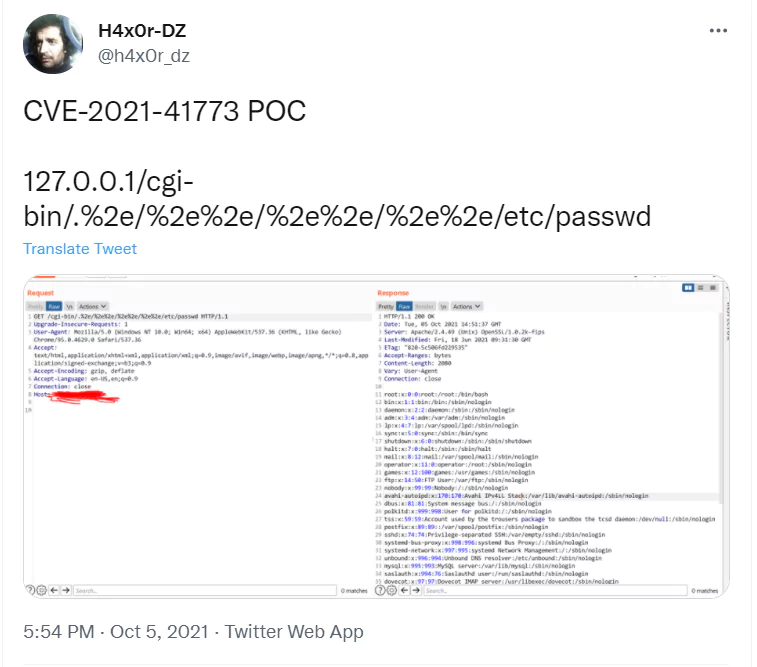
The vulnerability was reported by Juan Escobar from Dreamlab Technologies, Fernando Muñoz from NULL Life CTF Team, Shungo Kumasaka, and Nattapon Jongcharoen.
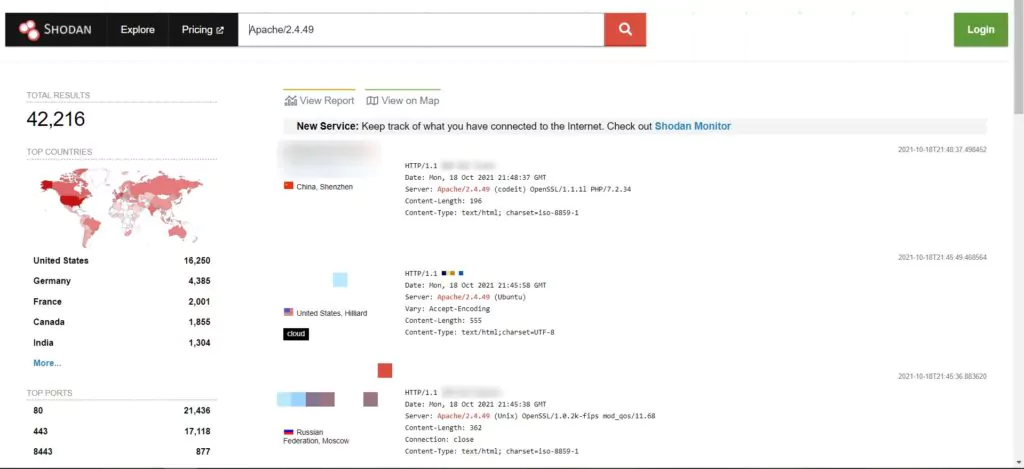
Even though the vulnerability was patched with the update 2.4.51, more than 42 thousand vulnerable Apache servers are still waiting for the attackers to exploit.
Stay Safe, Protect Yourself from CVE-2O21-41773
The vulnerability was fixed with the update 2.4.51, but even after a month, there are still more than 42 thousand vulnerable servers active. To protect oneself from CVE-2021-41773 and path traversal attack in general, analysts at SOCRadar suggest that:
- Apache HTTP Server is updated to at least version 2.4.51. (For further information, please visit https://www.apache.org/)
- The digital footprint is monitored thoroughly, software updates are checked frequently and applied if a new update is available.
- From a developer’s viewpoint, all inputs should be assumed to be malicious and should be processed accordingly.
- Security checks are carried out regularly.
- The directories outside the web root folder should be protected and encrypted.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free



































