
Ford Customer Data Breach, German Statistical Data Leak, and Bank of France Targeted
Recently, SOCRadar’s Dark Web Team has identified an alleged data breach at Ford Motor Company that exposed 44,000 customer records. A new stealer malware targeting Chrome v129+ browsers and cryptocurrency wallets has also surfaced, along with a hacking service offering tailored website and SQL injection attacks. Additional findings include an actor seeking credentials for the Bank of France and a claimed database leak from the German Federal Statistical Office, exposing extensive user and tax-related data.
Receive a Free Dark Web Report for Your Organization:
Alleged Customer Database of Ford Motor is Leaked
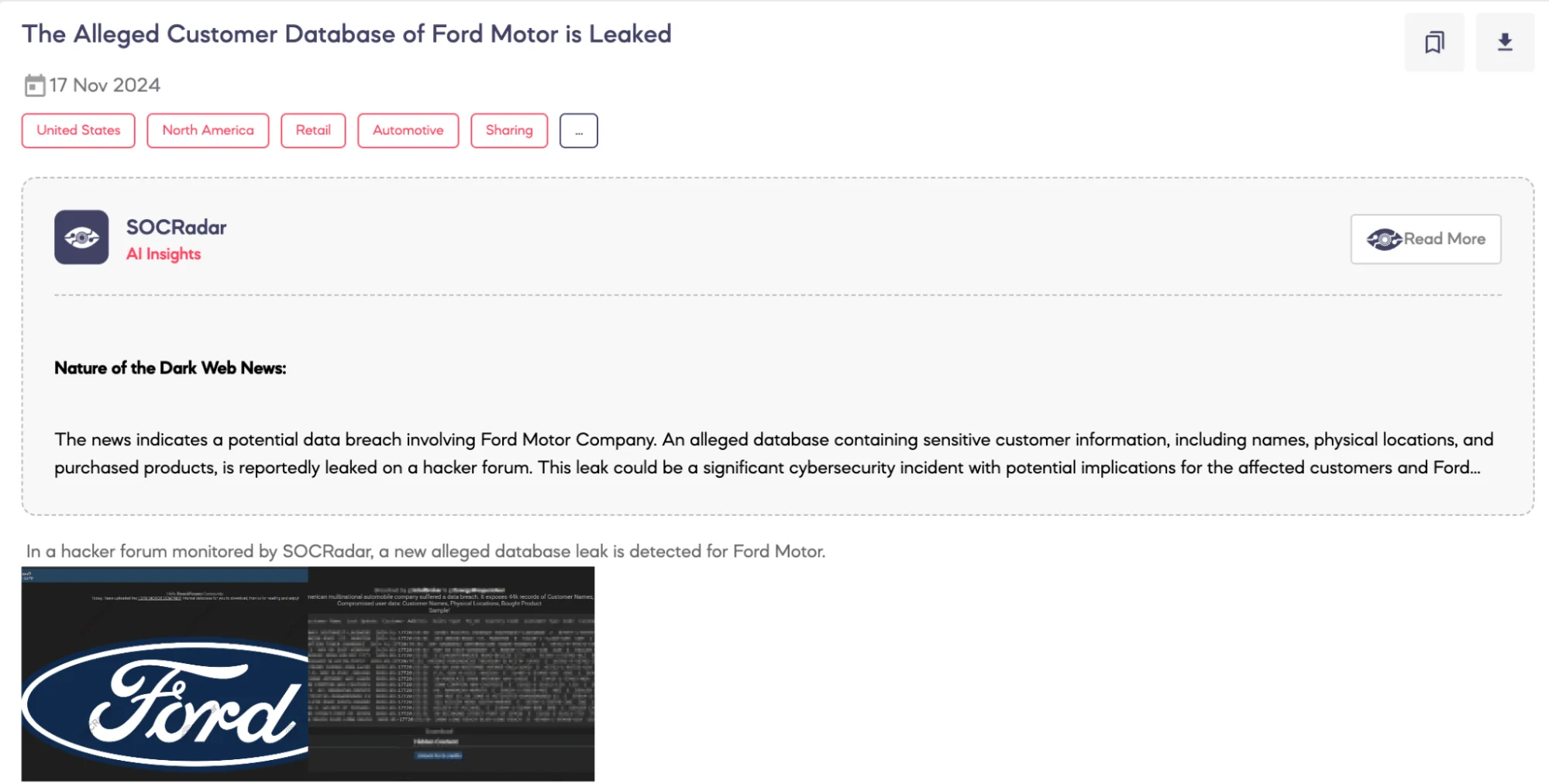
SOCRadar Dark Web Team detected a post on a hacker forum claiming a data breach involving Ford Motor Company. According to the threat actor, who is identified as a member of the CyberNiggers threat group, the breach occurred in November 2024. The database reportedly contains 44,000 records, including customer names, physical locations, and details of purchased products. The threat actor also stated that a sample of the internal database was uploaded for public access.
New Stealer Tool is on Sale
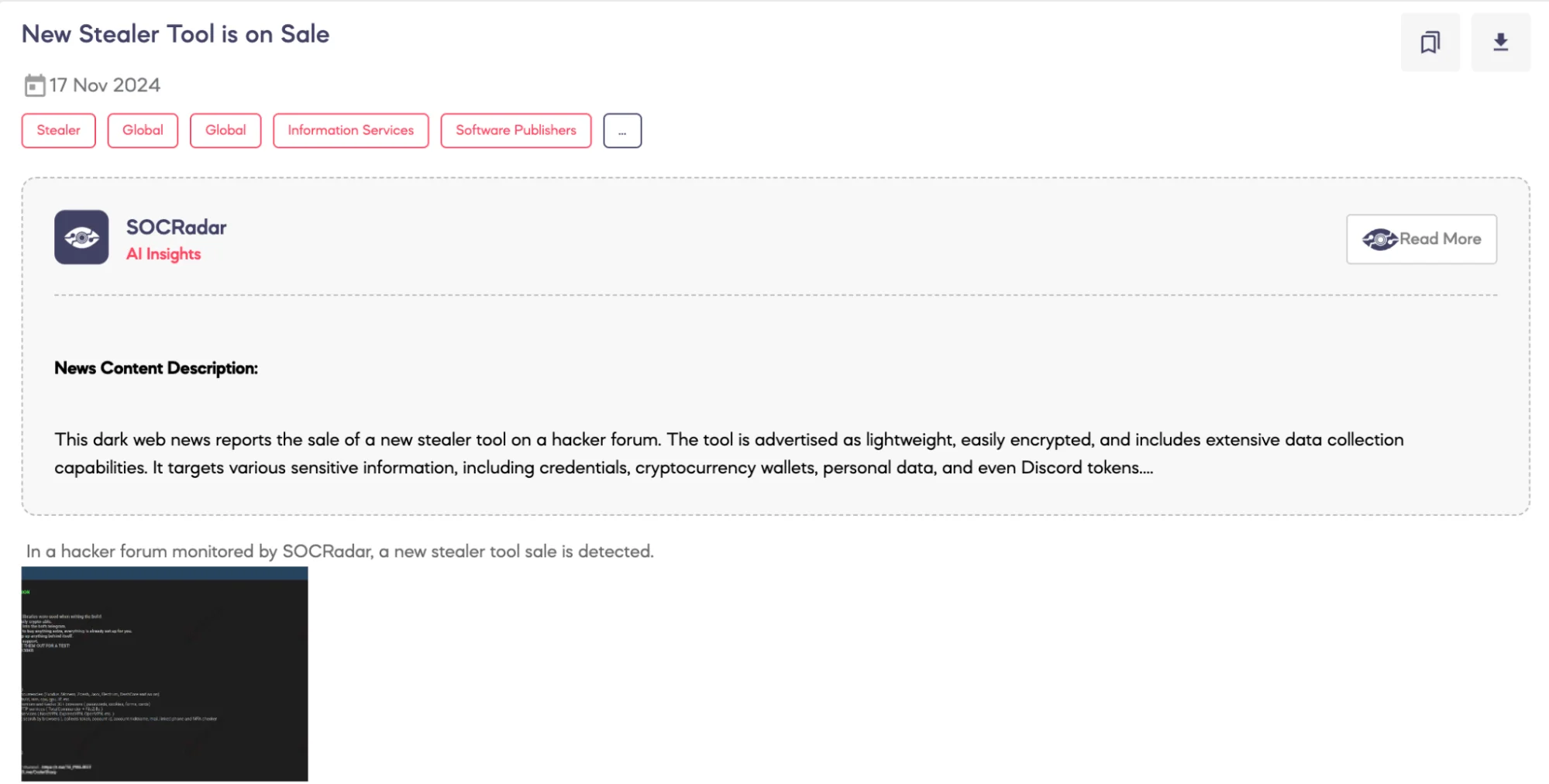
SOCRadar Dark Web team detected a post published on a hacker forum where a threat actor advertised a new stealer malware for sale. According to the threat actor’s claims, the malware operates without external libraries and supports Chrome v129+ browsers. It logs data directly to a bot’s Telegram account and includes features for collecting information such as PC details, browser credentials, cryptocurrency wallets, VPN data, Discord tokens, and Steam account information. Pricing for the malware is advertised as $20 for one month, $40 for three months, and $100 for lifetime access.
A New Hacking Service is Detected
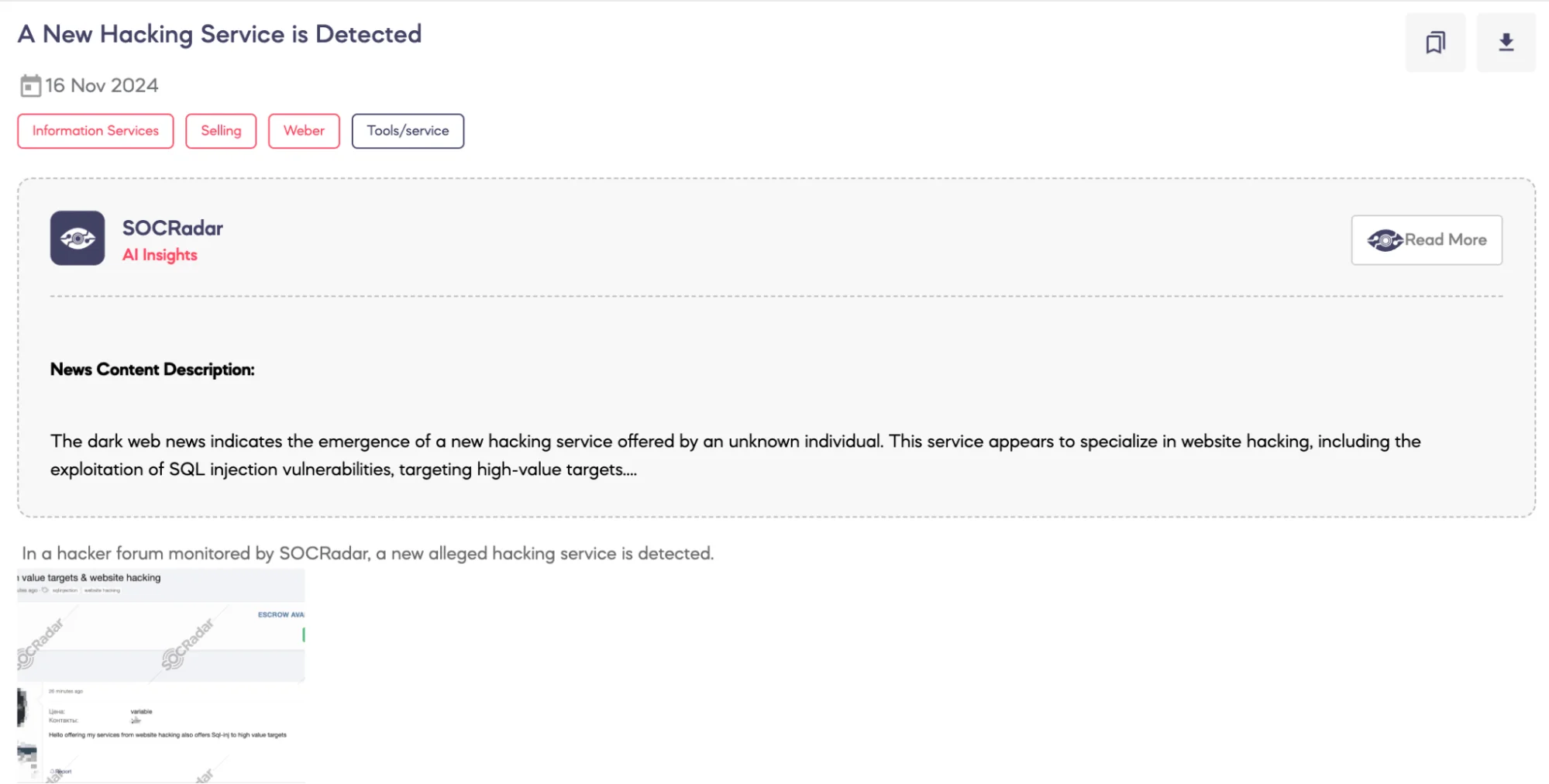
SOCRadar Dark Web team detected a post on a hacker forum where a threat actor advertised a new hacking service. According to the threat actor’s claims, the service includes website hacking and SQL injection attacks targeting high-value entities. This post highlights the ongoing threat posed by cybercriminals offering tailored attack services on underground forums.
Customer Data Purchasing Announcement is Detected for the Bank of France
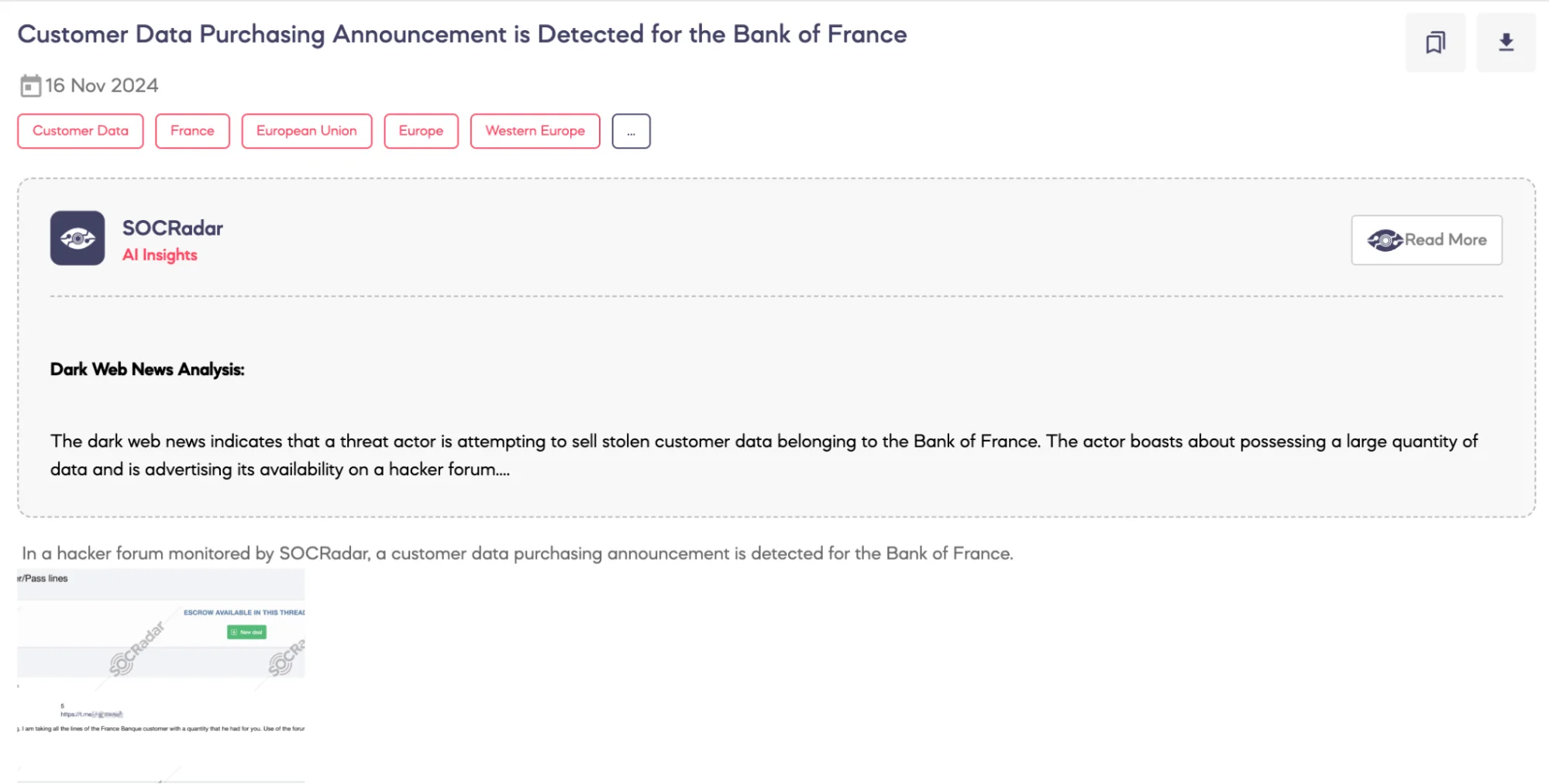
SOCRadar Dark Web team detected a post on a hacker forum where a threat actor announced an intent to purchase login credentials associated with the Bank of France. The actor expressed interest in acquiring login credentials from forum members and encouraged them to share relevant data. However, specific details about the type or volume of data requested were not disclosed.
Alleged Database of German Federal Statistical Office is Leaked
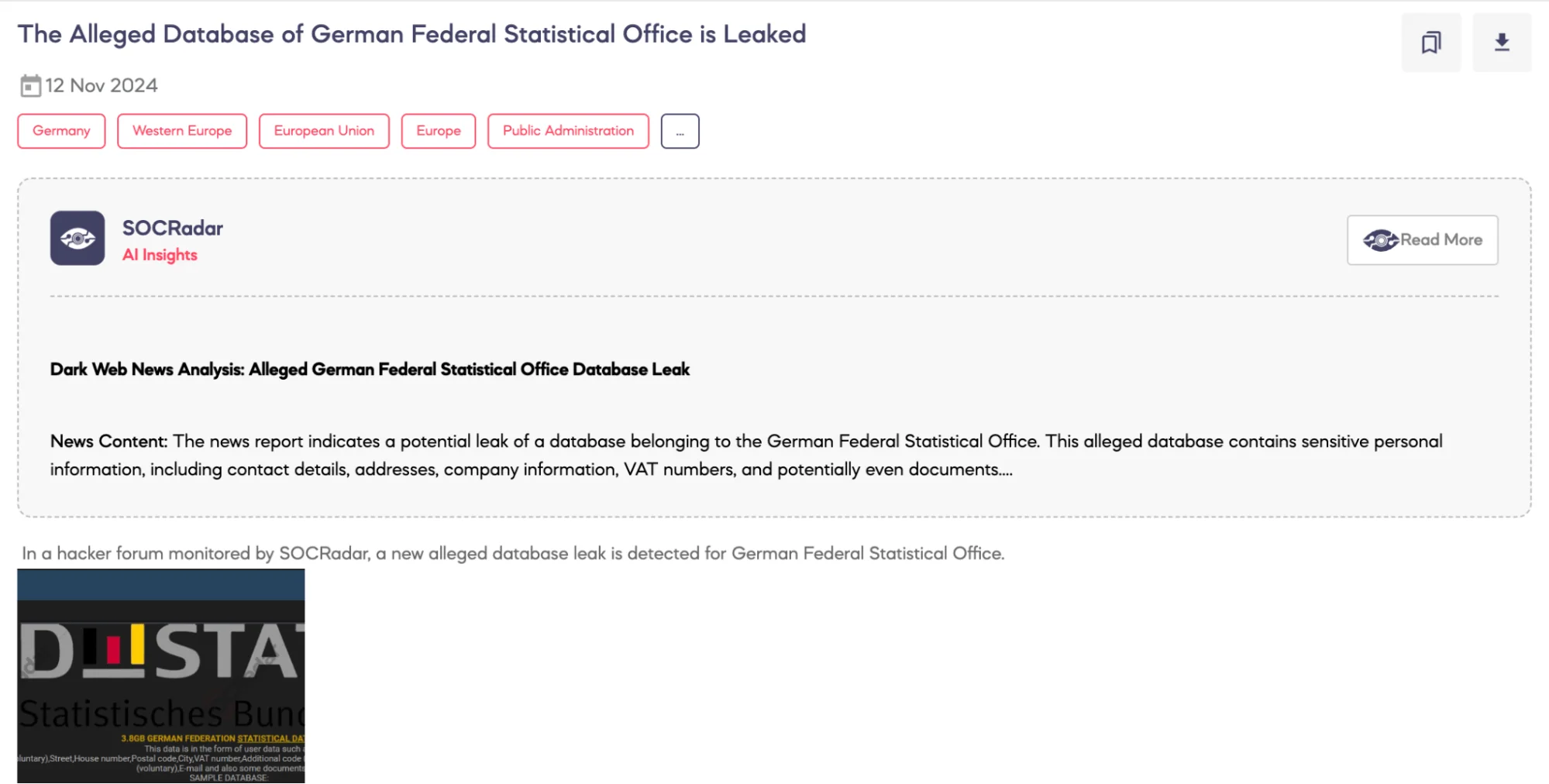
SOCRadar Dark Web team identified a post on a hacker forum indicating an alleged database leak involving the German Federal Statistical Office.
The threat actor claims that the leaked database, amounting to 3.8 GB, includes comprehensive user data fields. These allegedly comprise contact information, physical addresses, company names, departmental details, street names, house numbers, postal codes, city names, VAT numbers, and state-specific tax office information. Additionally, the database is said to include optional fields such as academic or professional titles, first names, supplementary codes, and certain documents.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































