
Fortifying the Digital Frontier: Australia’s Pioneering Cyber Shields Strategy
In 2022, Following the Medibank breach in November, Australia’s Cyber Security Minister Clare O’Neil highlighted the country’s stance against ransom payments. She further announced the formation of a new task force, merging the capabilities of the Australian Federal Police with the nation’s cyber intelligence agency to initiate a “hack the hackers” campaign against cybercriminals targeting Australia. This pioneering task force embarked on a comprehensive counter-attack strategy, representing a novel approach in Australia’s cyber defense efforts.
Again in November, but in 2023, Australia’s journey to fortify its defenses once again came to the forefront through the “Six Cyber Shields” strategy. Aimed at transforming the nation into a global cybersecurity leader by 2030, this comprehensive plan underscores the critical importance of safeguarding digital infrastructure, enhancing public awareness, and fostering international collaborations to counteract the ever-evolving cyber threats. Lastly, the blog post of ISACA on January 31, 2024, shared expert insights.
Let’s delve into the origins of this situation and further analyze the strategy adopted.
What are the Six Cyber Shields
Australia saw a significant surge in cybersecurity incidents, with a reported increase of over 80% in the period between July 2021 and June 2022, indicating a heightened level of interest from cyber threat actors. As stated above, a later pivotal event in the escalation of cybersecurity threats in Australia involved a major breach at Medibank, one of the country’s largest private health insurers, in October 2022.
The incident, executed by a ransomware group linked to the now-defunct REvil gang, resulted in the theft of details for approximately 9.7 million customers, impacting nearly 500,000 individuals. This breach marked a significant moment in the evolution of cybersecurity awareness and response in Australia. In this context, task forces were established, plans were made, and Australia is drawing a cyber security road map until 2030 and will follow the 6 principles.
Most basically, the “Six Cyber Shields” strategy is a plan to safeguard Australia’s digital landscape.
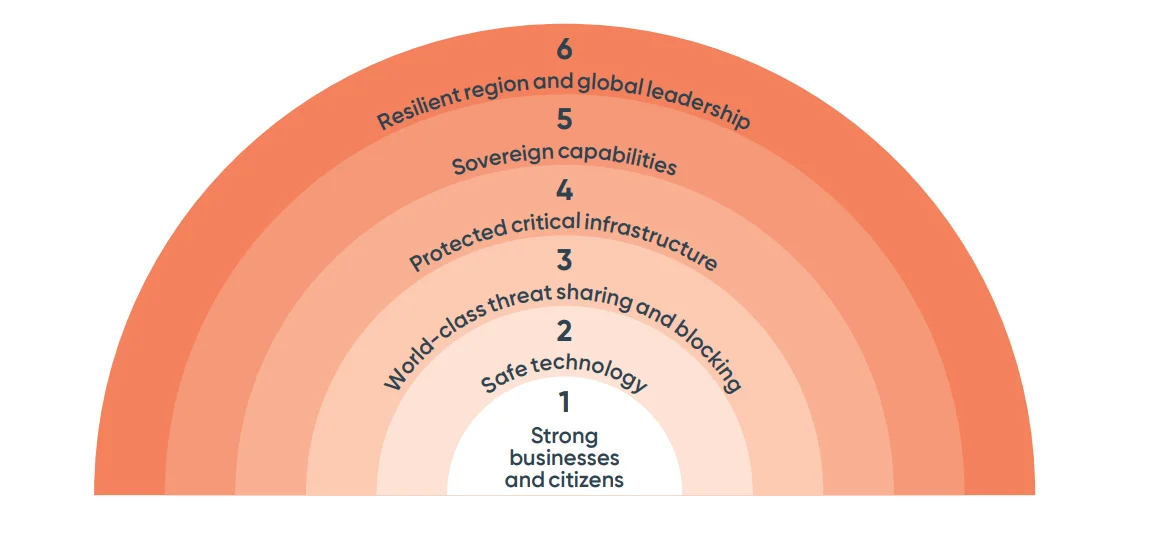
Layers of Cyber Shield. (Source)
As stated in ISACA, it includes:
- Education and Awareness: Enhancing public understanding of cyber threats.
- Safe Technology Standards: Setting safety standards for digital products.
- Real-Time Threat Intelligence Sharing: Facilitating the immediate blocking and sharing of cyber threats.
- Protection of Critical Infrastructure: Ensuring essential services are secure from cyber-attacks.
- Development of Sovereign Capabilities: Building Australia’s own cybersecurity capabilities.
- International Collaboration: Strengthening global partnerships for regional cybersecurity resilience.
Further Details
Although the 6-layer strategy we mentioned is a framework that covers every topic in a broad sense, there are other details that should be highlighted.
- Pacific Cyber Force: As Clare O’Neil states “We want to remain the security partner of choice for nations in the Pacific family. We’ve consulted closely with our regional partners to understand their unique cyber challenges. We’ve heard from Pacific Islands that digitisation and connectivity are key parts of their economic development strategies, but also increase the cyber risks they face as nations. “
Therefore, increasing regional cyber security capacity by supporting the threat sharing layer is a development that may lead to a collaborative Pacific Isles solidarity against Russian, Chinese, and North Korean threat actors.
- Roadmap: Australia’s 2030 vision will unfold in three stages. As stated in the document:
- First Stage (2023-2025): Their initial focus will be on solidifying their base by addressing crucial vulnerabilities in cyber defenses, enhancing protection for the most at-risk individuals and businesses, and fostering an increase in cyber security proficiency throughout the region.
- Second Stage (2026-2028): During this period, Australia aims to broaden cyber security expertise across the entire economy. They plan to escalate investments within the wider cyber ecosystem, expand the cyber security sector, and cultivate a varied cyber security workforce.
- Final Stage (2029-2030): In the concluding phase, the goal is to become pioneers in cyber security on a global scale. Australia will spearhead the creation of state-of-the-art cyber technologies designed to adapt to evolving risks and opportunities within the cyber domain.
- Cooperation with the Industry: Under the first stage, they will collaborate with the industry to jointly develop a comprehensive set of legislative reforms aimed at enhancing cyber defenses. This initiative will consider introducing new cyber responsibilities, simplifying reporting mechanisms, refining incident response strategies, and facilitating more effective sharing of insights following cyber incidents.
Designed to reduce regulatory impact, this package will be crafted with a focus on incorporating expert recommendations and addressing the needs of all Australians. To ensure these adjustments are well-informed and inclusive, a focused co-design process will be initiated before implementing these changes.
For full details remember to check the official documentary.
Is It Enough?
Australia’s Six Cyber Shields strategy is a forward-thinking approach, showcasing their commitment to cybersecurity. This initiative stands out for its comprehensive coverage, from public education to international collaboration.
However, its success hinges on effectively addressing challenges like rapidly evolving cyber threats. Although it is good to set baseline plans and starting points, 6 layers and a premade plan can hinder providing the necessary flexibility.
For example, even before Six Cyber Shields has fully exited the planning stage, articles are being written stating new ideas and needs. An Australian technology news site suggests Data Science as the 7th shield and states that the 2030 targets can be achieved in this way.
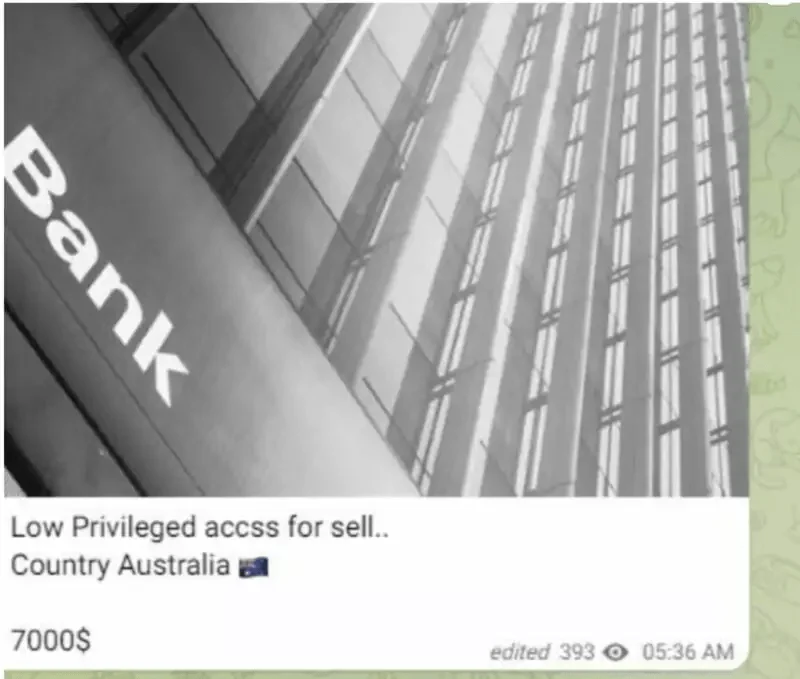
Before the Medibank incident, an access was sold on Telegram channels. Therefore a better cyber threat intelligence service could have stopped the breach.
The good thing is that Australia may actually be the perfect example in this context. The hack the hackers initiative, which we mentioned in the Introduction, was a perfect example of proactive security, and it could potentially be one of the nations that showed the most proactive stance possible.
So, in this project, where they created a national cyber security framework, focusing on issues such as expanding and sharing Threat Intelligence capacity could enable them to react before incidents occur. Thus, they may need to make the necessary flexible moves without being fanatically stuck in these plans.
Conclusion
Australia’s Six Cyber Shields strategy marks a step towards securing a safer digital future, emphasizing the nation’s proactive approach to cybersecurity. By addressing key areas from public awareness to global collaboration, it sets a comprehensive framework aimed at mitigating cyber threats.
This initiative not only reflects Australia’s dedication to protecting its digital borders but also contributes to the global effort against cybercrime, offering a model for others to follow in the pursuit of a more secure digital world.
SOCRadar, with its extensive capabilities in Digital Risk Protection and Threat Intelligence, could play a pivotal role in enhancing cybersecurity posture. By offering real-time threat detection, Attack Surface Management, and intelligence, SOCRadar can aid in the early identification of potential cyber threats, thereby enabling quicker response times and reducing the likelihood of successful attacks. Its ability to monitor a wide range of digital channels for threat indicators complements many security postures, including Australia’s strategy, especially in terms of real-time threat intelligence sharing and proactive security.
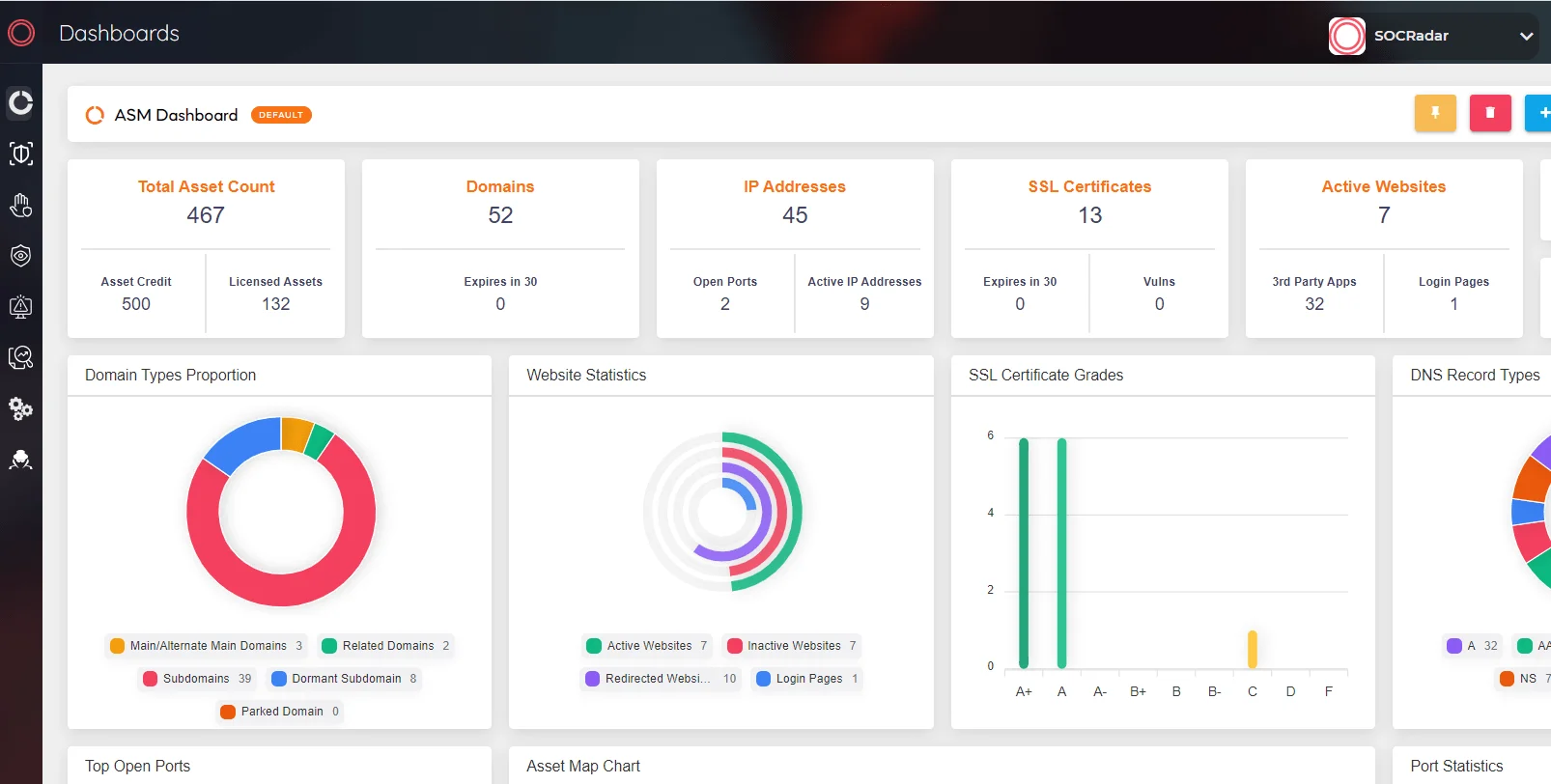
SOCRadar Attack Surface Management




































