Global Malverposting Campaign Infecting Over 500,000 Devices
A global malverposting campaign that has been ongoing for the past three months has been traced back to a Vietnamese threat actor.
Malverposting is the practice of distributing malware to a large number of people through promoted social media posts on platforms like Facebook, Twitter, and Instagram. During the campaign, the threat actor distributed information stealer variants such as SYS01 Stealer on social media platforms, infecting over 500,000 devices.
Attack Scheme
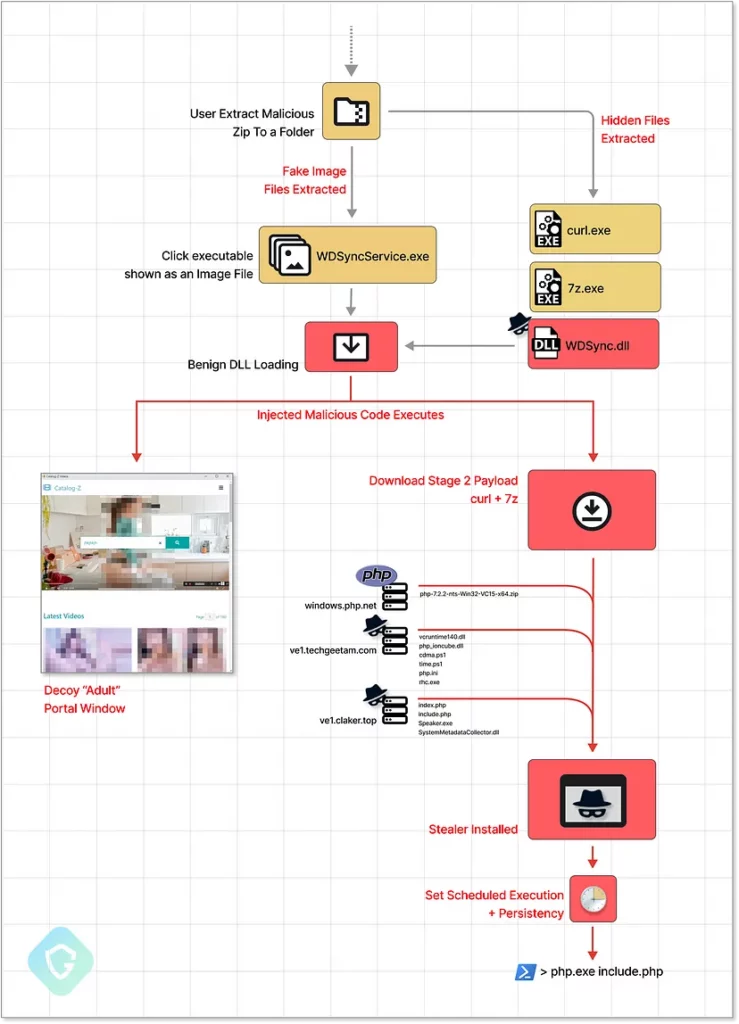
The campaign involves altering a sideloaded DLL to include obfuscated code that triggers the malicious activity. In one instance, the attacker had access to the source code of a Seagate Toolkit executable, allowing them to recompile the specific DLL with their malicious payload.
The threat actor hijacked popular accounts and also created new business accounts to use in malverposting attacks. Through these accounts, they served sponsored posts that offered free downloads of adult-rated photo albums in ZIP format. However, the ZIP file contains executable files that trigger an infection chain when opened. The Stealer malware is then downloaded dynamically from C2 servers using curl and 7zip binaries, which are hidden inside the original ZIP payload. The malware can steal sensitive information, including session cookies and account data.
Malverposting Campaign Leverages Stolen Data to Create Facebook Bots
What makes the attack chain particularly potent is that the attacker uses the stolen data to create additional Facebook bot accounts, which they use to push more sponsored posts and scale the scheme further. This enables the attackers to distribute millions of copies daily, giving them the time to conduct their malicious activities undetected.
The malicious payload used in the attack is also sophisticated and distinctive, utilizing methods commonly seen in Advanced Persistent Threats (APTs)
The newest version of the payload has different variations, all of which begin the infection chain using a seemingly harmless executable file. The attacker used regular system tools associated with well-known Hard-Drive manufacturers such as Seagate and WesternDigital, which could make the attack appear benign and evade detection by antivirus and endpoint security software.
The PHP-based stealer is deployed using a constantly evolving method incorporating more features to avoid detection. This indicates that the threat actor continuously improves tactics in response to public disclosures.
Researchers have uncovered a phishing operation that targets Facebook users. The attackers trick users into entering their login credentials on fake copycat websites that are designed to steal their account information and gain control over their profiles.
The threat actor has been discovered to create new business profiles and claim them to be photographer accounts in order to avoid being detected by Facebook.
The infections caused by this technique have mainly been reported in Australia, Canada, India, the U.K., and the U.S.
You can find IoCs in Guardio’s Medium post.
Discover Campaigns on SOCRadar
The SOCRadar Labs Campaigns page provides up-to-date information on the latest campaigns carried out by threat actors. By visiting the page, users can easily track the timeline, associated threat actors, and indicators of compromise (IoC) for each campaign and stay informed of the ongoing campaigns that threaten various industries.