GoAnywhere MFT Vulnerability Contributes to 91% Increase in Ransomware Attacks
[May 4, 2023] Update: Brightline, a mental health provider, was among the organizations targeted by the Clop ransomware group in March. Read the subheading “Data Breach of Brightline Impacts Over 780K Patients.”
The Department of Health and Human Services (HHS) Cybersecurity Coordination Center has cautioned healthcare providers in the U.S. about ransomware attacks carried out by the Cl0p (Clop) and LockBit groups. There is a significant risk that cybercriminals will continue to target the healthcare sector.
These attacks exploit a high-severity vulnerability in the GoAnywhere MFT (Managed File Transfer) product of Fortra, tracked as CVE-2023-0669, and two other vulnerabilities in PaperCut’s MF/NG software (CVE-2023-27350 and CVE-2023-27350).
About the Fortra GoAnywhere MFT Vulnerability (CVE-2023-0669)
Fortra announced on February 1, 2023, that their GoAnywhere MFT product contains a zero-day vulnerability, identified as CVE-2023-0669 (CVSS score: 7.2, High severity).
Successful exploitation of CVE-2023-0669 allows for remote code execution (RCE), and initial suspicious activity related to it was detected on January 18. The vulnerability can only be exploited by gaining access to the application’s administrative console, which is typically restricted to a private company network, through VPN, or by specific IP addresses in an allow list.
Since the zero-day RCE vulnerability in Fortra’s GoAnywhere MFT was made public, malicious actors have attempted to exploit it.
459 Attacks Related to GoAnywhere MFT Vulnerability Recorded in March
According to an alert from the Health Sector Cybersecurity Coordination Center (HC3), the Cl0p Ransomware group has historically targeted the healthcare industry, with 129 organizations being targeted in March.
The latest reports show that the exploitation of the Fortra GoAnywhere MFT vulnerability has resulted in a significant increase in ransomware attacks in March, with a 91% rise compared to February and 459 attacks recorded during the month. It was also found later that the BlackCat (ALPHV) ransomware group had taken advantage of the CVE-2023-0669 vulnerability.
Data Breach of Brightline Impacts Over 780K Patients
Brightline, a pediatric mental health provider offering virtual counseling, confirmed that protected health information was stolen from its GoAnywhere MFT service. The Cl0p ransomware group was responsible for the data breach, which affected 783,606 people.
The provider was listed on Cl0p’s extortion site on March 16, indicating that it was one of the 129 companies compromised by the threat actor in March.
The stolen data included personal information such as full names, physical addresses, dates of birth, member identification numbers, dates of health plan coverage, and employer names. Brightline stated that it has taken steps to mitigate the impact and employed additional security measures.
According to the most recent update, the Cl0p ransomware group has deleted Brightline’s data from their leak site. However, it is uncertain whether the threat actor still has possession of the data or not.
Recommendations
It is critical to apply patches for all actively exploited vulnerabilities as soon as possible. Upgrade GoAnywhere MFT to version 7.1.2 or higher to avoid exploitation of CVE-2023-0669.
Master encryption modification and credential reset is also advised for the Fortra GoAnywhere MFT vulnerability, CVE-2023-0669.
In early February, security researcher Florian Hauser published a proof-of-concept (PoC) for the exploitation of the CVE-2023-0669 vulnerability, which you can find here.
Stay Ahead of Attackers with SOCRadar
SOCRadar’s Attack Surface Management (ASM) module facilitates tracking your organization’s exposure and identifying security threats affecting your assets.
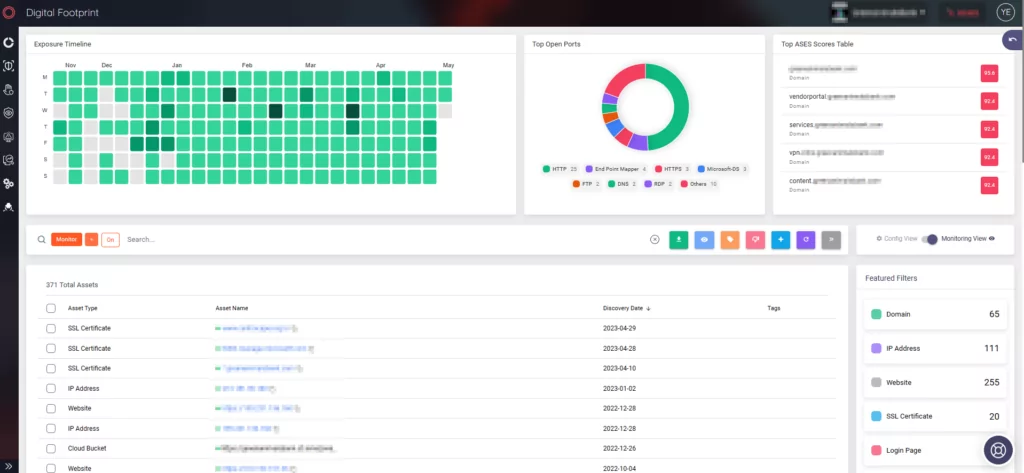
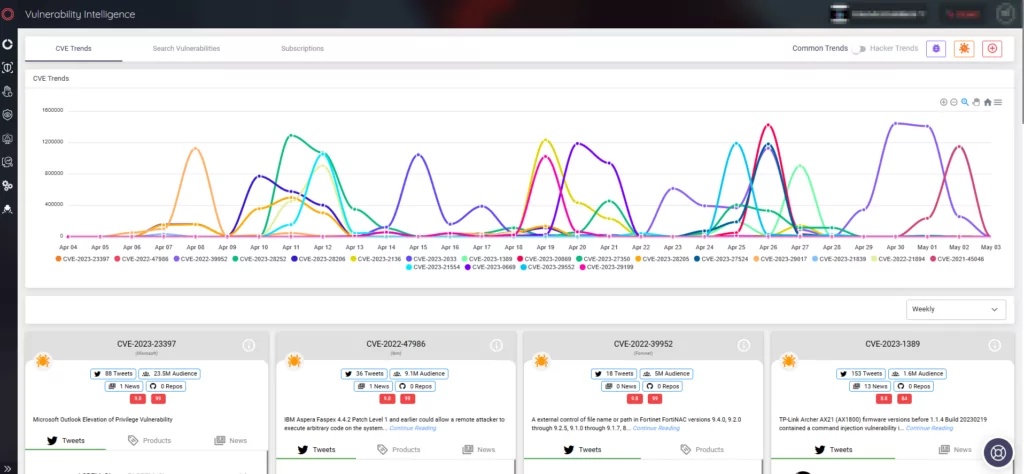
The Digital Footprint tab enables users to monitor their assets, while the Company Vulnerabilities tab allows them to take quick actions on vulnerabilities.
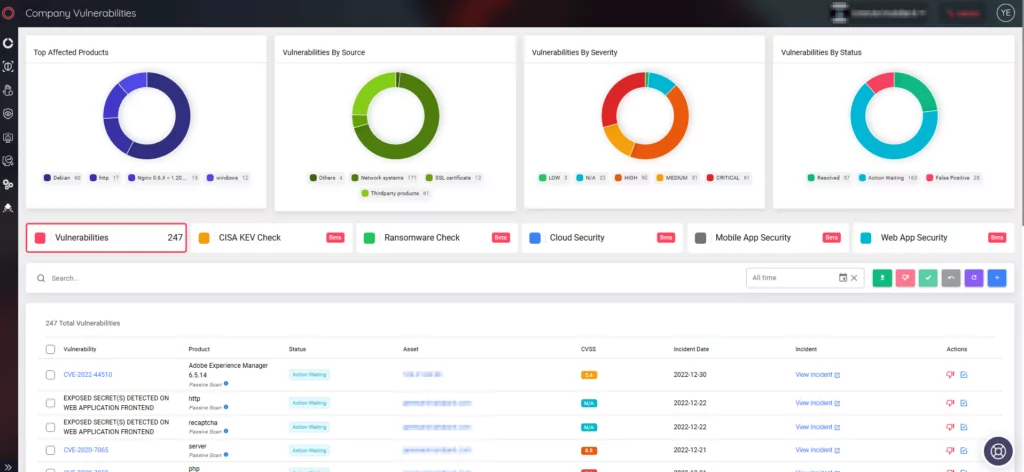
You can search for comprehensive information on vulnerabilities, including relevant updates and proof-of-concept exploits, on the Vulnerability Intelligence tab. Vulnerability Intelligence also provides insight into the latest vulnerability trends among hackers.