
How Credit Cards Get Stolen and Abused on the Deep & Dark Web
According to the latest Nilson report from 2019, the cost of payment card fraud was $28 billion worldwide in 2019. Similarly, the Federal Trade Commission reports the majority of the fraud losses reported to them (a total of almost 2 billion Dollars) were due to credit card fraud, which tops their list of identity theft fraud.
How do the fraudsters obtain credit cards?
Fraudsters can access credit cards in several ways. In the old days, credit cards were physically copied with the use of embedded devices as people used them in card readers to do their shopping. New cards were created using this skimmed information to be used later for fraudulent purchases. With the advent of chip cards, this type of fraud significantly decreased.
New methods to skim credit cards
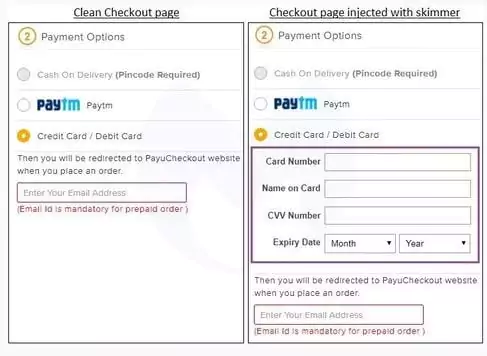
Today a significant portion of credit card transactions take place online without a card present. This makes online shopping sites an appealing target for cybercriminals. The Magecart group is one of the well-known crime groups that successfully attacked many websites, including British Airways and Ticketmaster, to collect payment card data along with PII. Threat actors insert malicious code either into the third-party payment processors or directly into the websites that copy all the information entered on a form. Such pages are monitored by SOCRadar against code injection in the Attack Surface Management.
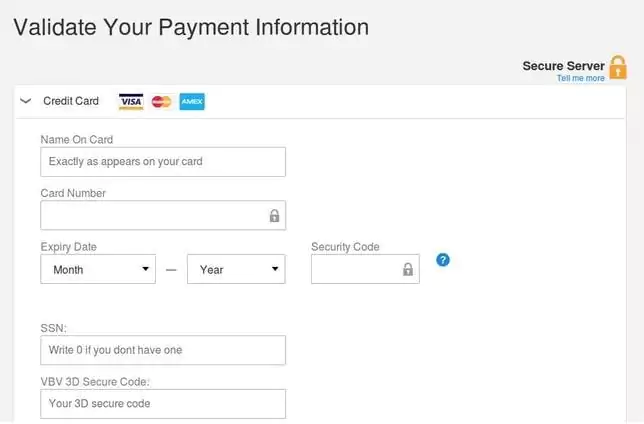
Social engineering is another popular method to collect credit card information. We are used to seeing phishing pages harvest login credentials but credit card collection using phishing links is just as common. They can also credit card information by pretending to be a shopping site or a fake support site. They can also simply call the victims and pretend to be an authority or a vendor while they ask for payment card details.
Another popular method is to infect user computers with info stealers or keyloggers and then collect credit card details as they are entered into the forms by the victim.
How are the stolen credit cards used?
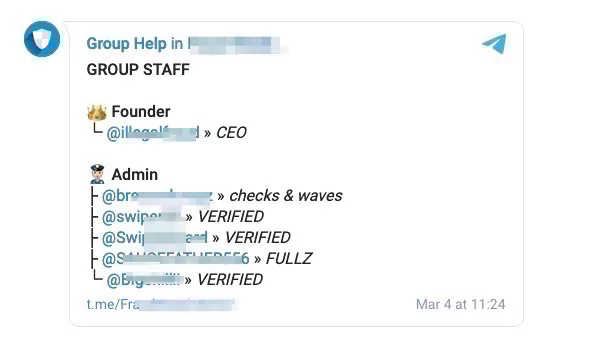
Threat actors seldom use the cards they collected for their shopping. These cards are put up for sale in underground carding forums such as Joker’s Stash or in private chat channels, such as IRC channels or Telegram, along with other illicit services and goods. Threat actors also use other well-known social media outlets such as twitter to advertise their goods.
There are several actors involved in the life cycle of stolen credit cards such as sellers, buyers, and mules. The information traded ranges from just card information to full user information (aka “fullz”) that enables more fraud capabilities. The prices range depending on the level of information offered and the type of the card.
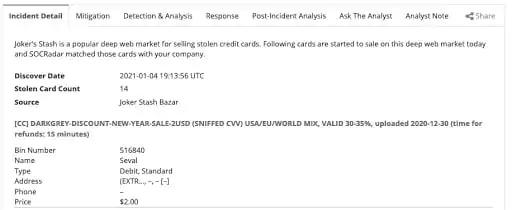
Monitoring deep and dark web for stolen credit cards
Given the size of losses from payment card fraud, credit card monitoring in the deep and dark web is an indispensable service for financial organizations. Using a combination of human analysts and automated monitoring, SOCRadar will detect any payment card information exposed or for sale for its customers. By simply adding your financial institution’s BIN numbers to the AttackMapper module, you can receive automated alerts if a card in your organization is offered for sale.

Discover SOCRadar® Community Edition for free
With SOCRadar® Community Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
References
[1] Hackers Steal Payment Card Data Using Rogue Iframe Phishing, Bleeping Computer
Cover image by CardMapr on Unsplash



































