
Threat Actor Profile: Molerats
Much like mole rats create an intricate network of underground tunnels, the cyber threat group known as Molerats has expertly burrowed its way through the digital defenses of its targets. Since its detection in 2012, this Arabic-speaking faction has honed its craft in cyber espionage, focusing on political and military targets throughout the Middle East. Employing a mix of phishing, malware, and social engineering, Molerats adeptly navigates through cyber defenses, gathering sensitive information while remaining largely undetected.
Who is Molerats?
Molerats, also known as the Gaza Hackers Team, Gaza Cybergang, ALUMINUM SARATOGA, and Extreme Jackal, is a politically motivated Advanced Persistent Threat (APT) group that has been active since at least 2012. This group primarily targets entities within the Middle East, North Africa, and the U.S., focusing on governmental, telecommunications, and media organizations. However, their activities have also been observed affecting various sectors across the globe, demonstrating their expansive reach and the non-discriminatory nature of their cyber espionage campaigns.

Illustration of Molerats generated by using DALL-E 3
Characteristically, Molerats leverages social engineering tactics, spear phishing campaigns, and malware deployment to infiltrate their targets. The group is known for its evolving toolkit, which includes a range of custom-developed backdoors such as Spark and publicly available malware tools that have facilitated their espionage activities. Molerats has been associated with several high-profile campaigns, including Operation Parliament, highlighting their ongoing focus on gathering intelligence aligned with regional geopolitical interests.
Their operations are notable not only for the breadth of industries targeted but also for their strategic evolution in response to cyber defense advancements. This adaptability underscores the persistent threat posed by Molerats in the landscape of global cybersecurity.
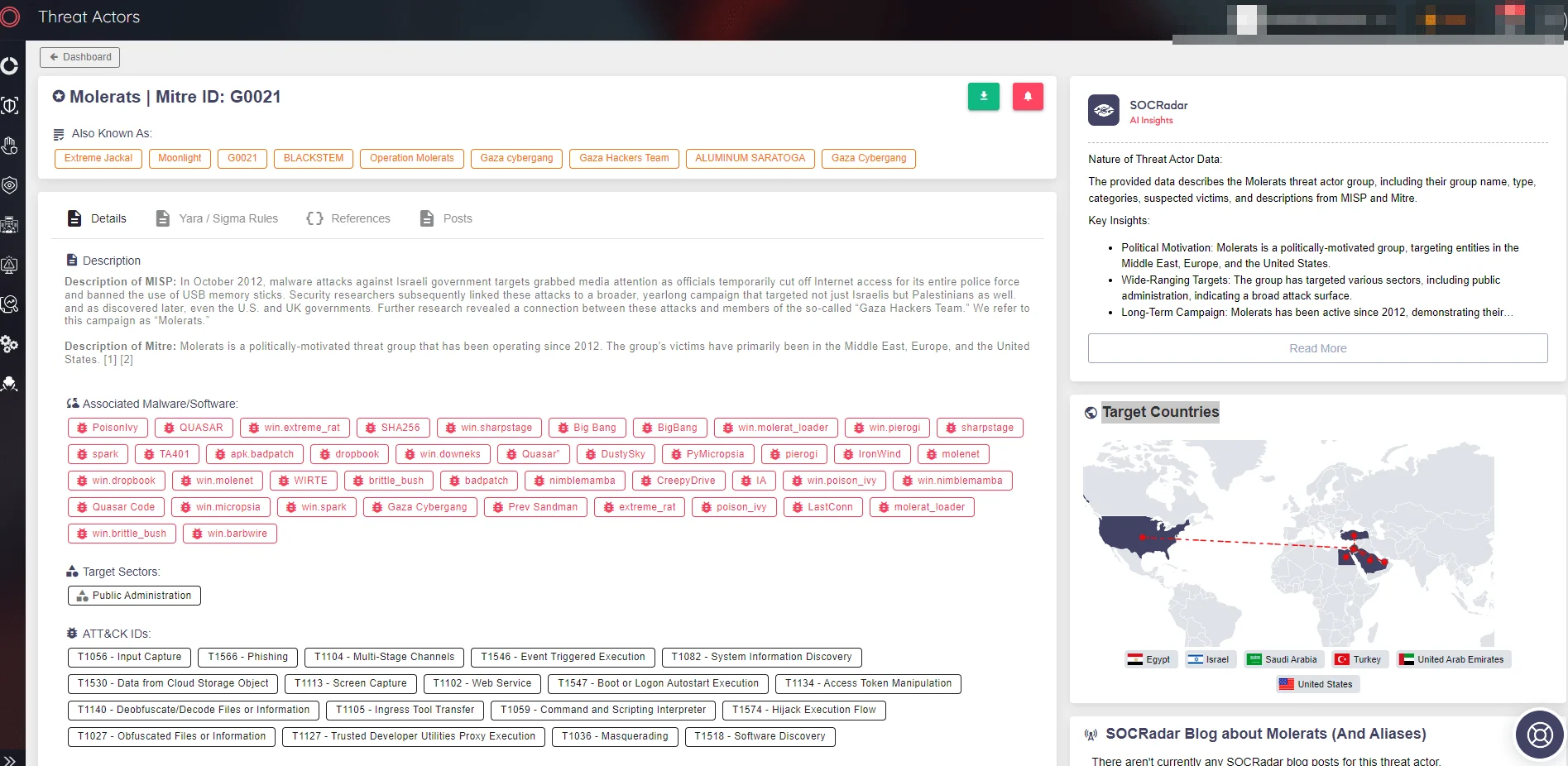
Threat Actor information page of Molerats (Source: SOCRadar)
How Does Molerats Attack?
Molerats employs a sophisticated array of techniques and tools to conduct its cyber espionage operations, focusing predominantly on social engineering and malware to compromise their targets. Their attacks typically follow a structured methodology that allows them to remain stealthy and effectively achieve their objectives. Here’s an overview of their common attack vectors:
Spear-Phishing Emails: At the core of Molerats’ strategy are spear-phishing campaigns. These emails are meticulously crafted to appear legitimate, often mimicking the communication styles of trusted organizations or individuals. The emails might include urgent requests or enticing documents that prompt the recipient to take action, such as enabling macros or downloading attachments.
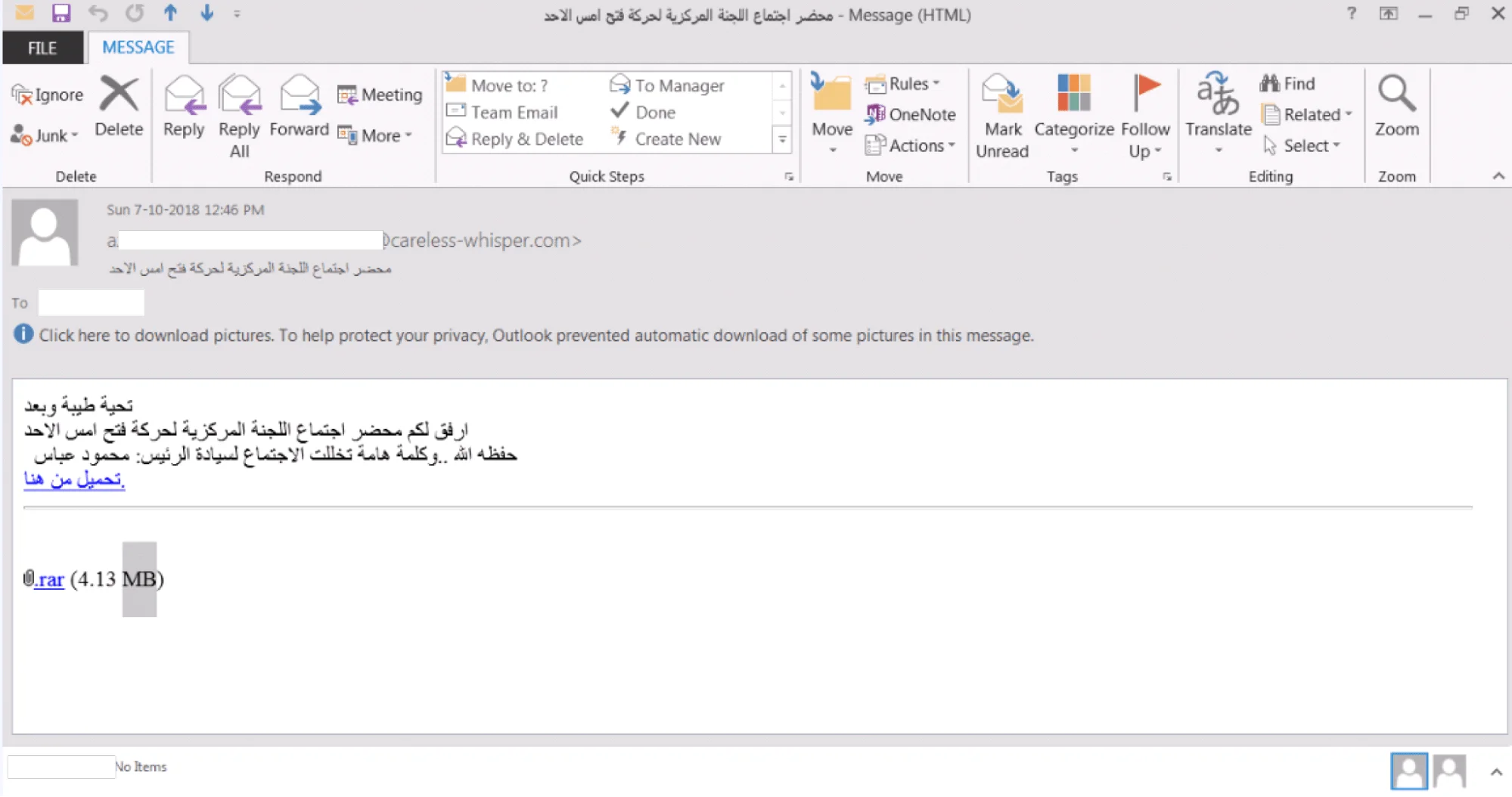
The image is a screenshot of an email interface showing a phishing attempt with a malicious RAR file attachment. (Source: Kaspersky)
Malicious Attachments and Links: The spear-phishing emails usually contain attachments or links that lead to malicious payloads. These attachments often appear as benign documents with names relevant to ongoing events or internal matters of the target organization, enhancing the likelihood of the recipient opening them.
Use of Legitimate Services for Malware Delivery: To evade detection by security systems, Molerats frequently utilizes legitimate cloud services like Google Drive, Dropbox, and GitHub to host their malware. This approach helps mask their malicious traffic within allowed and common network traffic, making detection more challenging.
Deployment of Custom and Commercial Malware: Once initial access is gained, Molerats deploys a variety of tools. These include custom-developed backdoors such as Spark, as well as commercially available RATs (Remote Access Trojans) and info stealers. This arsenal allows them to maintain persistent access, execute commands remotely, and exfiltrate sensitive information.
Evasion Techniques: Molerats shows a keen adaptiveness in its operations, employing various evasion techniques to avoid detection. This includes encrypting command and control communications, using obfuscated code, and deploying malware only capable of executing in specific environments (e.g., systems with an Arabic keyboard layout).
Data Exfiltration: After successfully infiltrating a system, the group focuses on data exfiltration. The stolen data typically includes documents, credentials, emails, and other sensitive information that can be used to further penetrate the victim’s network or to fulfill their intelligence-gathering objectives.
Through these methods, Molerats has consistently updated and adapted its tactics to counter cybersecurity measures, making it a persistent and evolving threat in the region and beyond. Their ability to blend into legitimate traffic and effectively use spear-phishing techniques underscores the need for continual advancements in cybersecurity awareness and defenses.
What are the Targets of Molerats?
Molerats’ cyber espionage activities are predominantly concentrated in the Middle East and North Africa (MENA) region, with notable operations also reaching into Turkiye and the USA. The choice of these specific geographic regions is strategic, aligning with the group’s interest in sensitive political, military, and economic information that can influence regional and global power dynamics. Here’s a detailed look at their targeted sectors within these regions:
Governmental and Diplomatic Institutions: Molerats places a high priority on infiltrating governmental bodies, ministries, and diplomatic institutions, including embassies. These targets are rich sources of political and strategic intelligence that can provide insights into internal and foreign policy decisions, diplomatic communications, and state secrets.
Aerospace and Defense Industries: Companies operating in the aerospace and defense sectors are critical targets due to the sensitive nature of their work, which often involves national security and advanced technology. Gaining access to proprietary designs, defense plans, and upcoming military projects offers significant strategic advantages.
Financial Institutions: The financial sector’s targeting encompasses banks and financial services firms, which hold critical economic data and can provide economic intelligence and potential leverage over national and private financial resources.
Journalists and Media Outlets: Journalists are targeted not only as a source of sensitive insider information but also to potentially manipulate the media narrative to influence public perception or gain advance warning of investigative exposures.
Software Developers: By targeting software developers and technology firms, Molerats can potentially access a wide array of proprietary software tools and products, which could be used to facilitate further intrusions or develop capabilities that aid in their cyber espionage efforts.
Insurance and Retail: Molerats targeted the insurance and retail sectors, expanding their focus beyond their traditional governmental and telecommunications targets as seen in the TopHat campaign initiated in late 2019.
What are the Notable Operations of Molerats?
Molerats has been involved in several high-profile cyber espionage operations over the years, utilizing a sophisticated array of custom-developed malware. These operations typically reflect the group’s strategic interests in gathering intelligence from targeted sectors. Below is an overview of some of their most notable campaigns and the specific malware tools they employed:
Operation Molerats, initially uncovered in 2012, illustrates the group’s extensive cyber espionage efforts, targeting entities not only in Israel and Palestine but expanding to the US and UK. Initially favoring the widely accessible XtremeRAT, Molerats diversified their malware toolkit over time, notably incorporating Poison Ivy, which broadened their operational capabilities.
Their tactics have been characterized by the use of geopolitically themed phishing emails, leveraging regional crises to entice targets to open malicious attachments. This strategic use of contextually relevant lures highlights Molerats’ adaptability and persistent threat to global security.
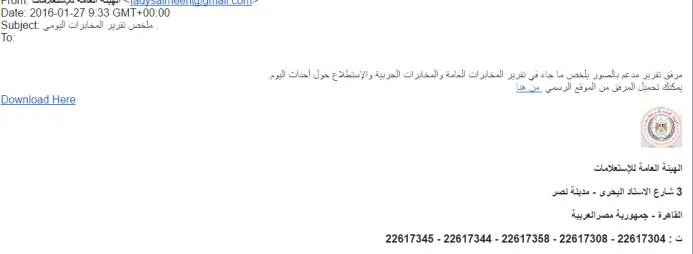
Email targeting Arabic speakers used in the DustySky campaign (Source: ClearSky)
Operation DustySky was a significant cyber espionage initiative by the Molerats group, leveraging a sophisticated malware known as DustySky. First observed in May 2015, DustySky is a multi-stage malware designed specifically for intelligence gathering. It targeted various high-value sectors including governmental and diplomatic institutions, aerospace and defense industries, financial sectors, journalists, and software developers.
The campaign involved sending targeted emails, crafted in Hebrew, Arabic, or English, equipped with malicious attachments to infect the systems of selected victims across the Middle East (Saudi Arabia, United Arab Emirates, Egypt, Iraq and Israel), with operations extending to the US and Europe.
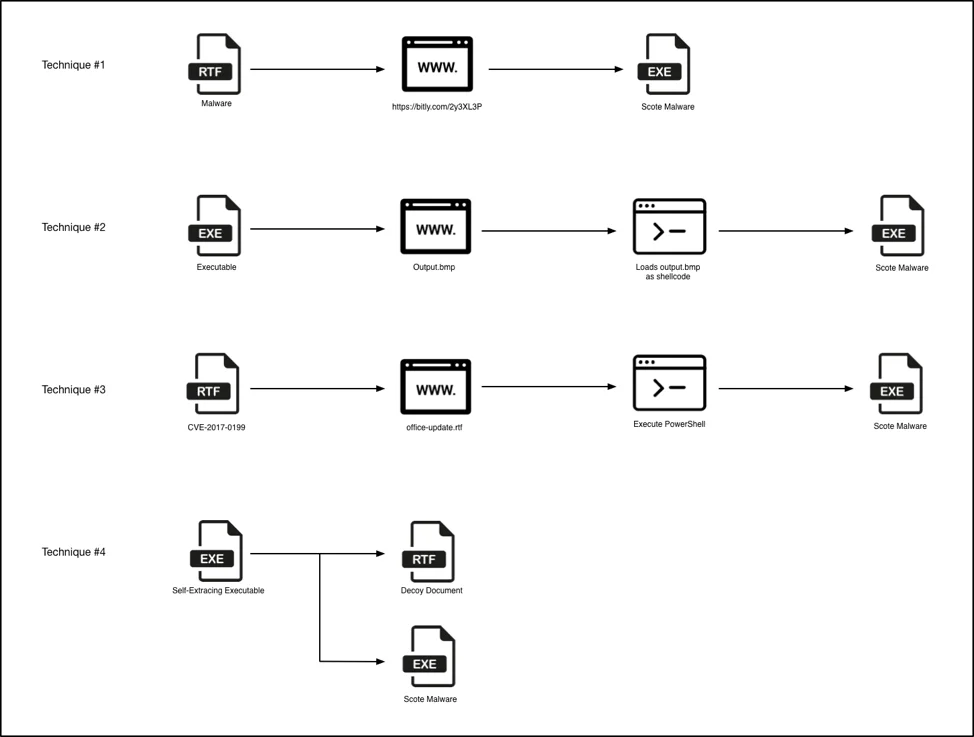
Malware delivery techniques of TopHat campaign (Source: Unit42)
TopHat, initiated in late 2019, marked a strategic evolution for Molerats as they expanded their targeting beyond the usual governmental and telecommunications sectors to include industries like insurance and retail. This extension into less typical targets indicated a potential exploration of new intelligence-gathering avenues or perhaps a testing of their cyberattack techniques in varied environments.
Spear-phishing remained their attack vector of choice, using emails that employed social engineering tactics, including coercion with threats of exposing sensitive information to trick recipients into activating malicious payloads. The primary malware used was the Spark backdoor, which allowed the attackers to control compromised systems remotely, demonstrating Molerats’ continued evolution and adaptability in cyber espionage.
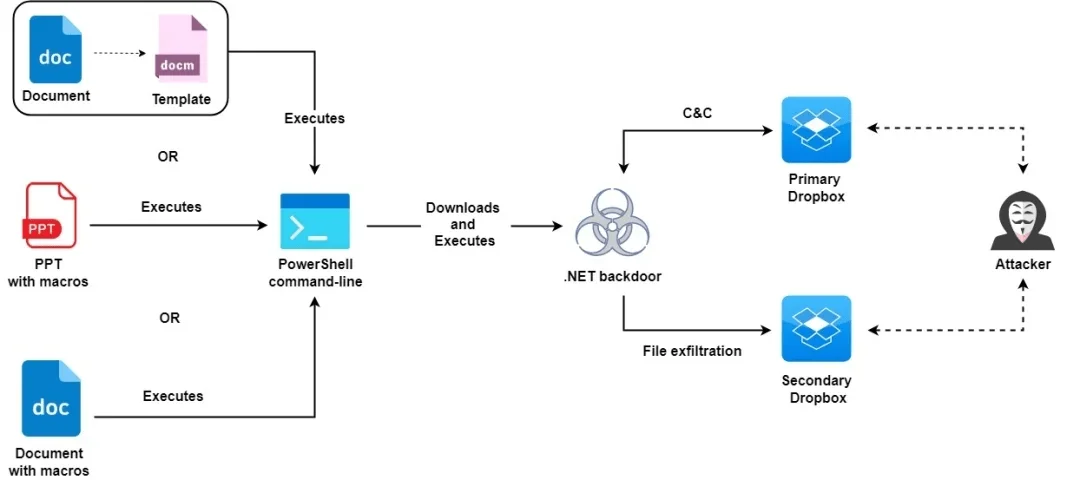
Attack chain of the campaign detected in 2021(Source Zscaler)
Molerats’ latest notable campaign, identified in late 2021, showcased the group’s continued evolution in cyber espionage amidst ongoing geopolitical tensions in the Middle East. This operation involved macro-based MS Office files embedded with decoys related to the Israel-Hamas conflict, specifically targeting influential individuals in Palestine’s banking sector, political figures, as well as activists and journalists in Turkiye.
The campaign featured a refined .NET backdoor, enhanced for better evasion. Molerats employed sophisticated packing tools such as ConfuserEx and Themida for obfuscation and utilized legitimate cloud services like Dropbox for command and control communications, effectively blending malicious operations within legitimate traffic to complicate detection.
Conclusion
In summary, Molerats has proven to be a formidable force in the landscape of cyber espionage. Originating from the Middle East, this politically motivated group has shown a deep capability for sophisticated cyber attacks targeting various sectors and regions. Utilizing custom malware, spear-phishing, and social engineering tactics, Molerats has demonstrated remarkable adaptability and technical expertise. Their involvement in significant operations such as TopHat and the deployment of malware like Spark and DustySky highlights their strategic intent and mastery in digital espionage.
Security Recommendations Against Molerats
To defend against Molerats and other sophisticated cyber threat actors, organizations should adopt a multi-layered approach to cybersecurity that includes:
Advanced Email Security Protocols: Given Molerats’ frequent use of spear-phishing, it is crucial for organizations to implement advanced email filtering solutions. These should include capabilities for phishing detection and sandboxing technology to inspect email attachments and links for malicious content.
SOCRadar Labs, Email Threat Analyzer
Email Threat Analyzer is a security tool that quickly assesses emails to determine if they are scams. It provides real-time analysis, helping organizations identify and respond to email threats promptly to enhance their cybersecurity measures.
Ongoing Cybersecurity Training: It is essential to educate staff and users about the risks associated with spear-phishing and other forms of social engineering attacks. Conducting regular training sessions can significantly decrease the likelihood of employees falling prey to such tactics.
Comprehensive Endpoint Security: Deploy comprehensive endpoint security solutions that provide real-time monitoring and defense against various forms of malware, including those specifically crafted and zero-day threats. Ensuring that all endpoints are regularly updated and patched is crucial for maintaining strong security.
Strategic Network Segmentation: By segmenting networks, organizations can limit the spread of intrusions. Implement strict access control measures and adhere to the principle of least privilege to minimize user and application access rights to essential functions only.
Prepared Incident Response Framework: Maintain a well-defined incident response plan that outlines procedures for detecting, containing, eradicating, and recovering from cyber attacks. This plan should also include protocols for communicating with relevant stakeholders during an incident.
Routine Security Evaluations: Periodically conduct security audits and penetration tests to identify and address vulnerabilities within the IT infrastructure, enhancing the organization’s defense against potential breaches.
Monitoring and Logging: Implement thorough logging and monitoring solutions to continuously review logs for unusual activities, particularly those involving access to sensitive data and critical systems.
Continuous Intelligence Sharing and Collaboration: Stay current with the latest cyber threat intelligence and actively participate in community and governmental information-sharing initiatives to enhance your defensive posture against emerging threats.
MITRE ATT&CK TTPs of Molerats
| ID | Name | Use | |
| T1547 | .001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | Molerats saved malicious files within the AppData and Startup folders to maintain persistence.[3 |
| T1059 | .001 | Command and Scripting Interpreter: PowerShell | Molerats used PowerShell implants on target machines. |
| .005 | Command and Scripting Interpreter: Visual Basic | Molerats used various implants, including those built with VBScript, on target machines. | |
| .007 | Command and Scripting Interpreter: JavaScript | Molerats used various implants, including those built with JS, on target machines. | |
| T1555 | .003 | Credentials from Password Stores: Credentials from Web Browsers | Molerats used the public tool BrowserPasswordDump10 to dump passwords saved in browsers on victims. |
| T1140 | Deobfuscate/Decode Files or Information | Molerats decompresses ZIP files once on the victim machine. | |
| T1105 | Ingress Tool Transfer | Molerats used executables to download malicious files from different sources. | |
| T1027 | Obfuscated Files or Information | Molerats has delivered compressed executables within ZIP files to victims. | |
| T1566 | .001 | Phishing: Spearphishing Attachment | Molerats has sent phishing emails with malicious Microsoft Word and PDF attachments. |
| .002 | Phishing: Spearphishing Link | Molerats has sent phishing emails with malicious links included. | |
| T1057 | Process Discovery | Molerats actors obtained a list of active processes on the victim and sent them to C2 servers. | |
| T1053 | .005 | Scheduled Task/Job: Scheduled Task | Molerats has created scheduled tasks to persistently run VBScripts. |
| T1553 | .002 | Subvert Trust Controls: Code Signing | Molerats has used forged Microsoft code-signing certificates on malware. |
| T1218 | .007 | System Binary Proxy Execution: Msiexec | Molerats has used msiexec.exe to execute an MSI payload. |
| T1204 | .001 | User Execution: Malicious Link | Molerats has sent malicious links via email trick users into opening a RAR archive and running an executable. |
| .002 | User Execution: Malicious File | Molerats has sent malicious files via email that tricked users into clicking Enable Content to run an embedded macro and to download malicious archives. | |



































