
How to Detect BEC Attacks?
1- What is a BEC attack?
A Business Email Compromise (BEC) attack is a cyberattack involving the hijacking, spoofing, or impersonation of a business email address. The victim of a BEC attack receives an email that appears to be from a trusted business firm. While the email may appear genuine, it often contains a phishing link, a malicious attachment, or a money transfer request to the attacker.
According to the statistics from the FBI’s 2020 Internet Crime Report; the FBI’s Internet Crime Complaints Center (IC3) received nearly 20,000 complaints about the BEC, and reported losses due to the BEC increased from $1.29 billion in 2018 to $1.86 billion in 2020. In addition to that,
According to the BEC Report of 2021 that was prepared by the GreatHorn (security provider);
- Spoofing – 71% of BEC attacks use a fake email account or website to provide credibility. Attacks can be made with a known name and surname, a similar domain name, or a compromised email account.
- Spear Phishing – 69% of BEC attacks use spear phishing to increase their chances of reaching the right people in an organization who have an impact on money transfer. According to the report, 57% of the attacks target the finance department, 22% target the CEOs, and 20% target the IT department.
- Malware – 24% of BEC attacks still use malware. Despite the decrease in the malware attack, it has been determined that the attackers’ continuation of such attacks is the motivation to gain more by attacking other companies through the victim company by using the data obtained through various techniques (authorization, gaining internal access, etc.).
According to the report, 71% of the organizations which was investigated by GreatHorn, stated that their users were ready to identify a phishing email, and 43% of the same organizations had experienced a security incident in the last 12 months. In short, a BEC attack is likely a speared phishing attack that uses very specific social engineering tactics to gain the buyer’s trust and participate in some financial transactions. Furthermore, according to Verizon’s 2021 Data Breach Investigation Report (DBIR), a BEC attack is the second most common type of social engineering attack. As stated in the Verizon report, it is sometimes sufficient for the attackers to send an email containing “CEO@…com” without even needing a business email, to be successful in the attack.
Agari, a contributor to the Anti-Phishing Working Group (APWG), found that BEC scams have become more costly for some victims. Average wire transfer demand in BEC hacks increased from $48,000 in Q3 2020 to $85,000 in Q1 2021. Agari has detected a new method used by BEC scammers, the “Report Aging” phishing attack.
Common BEC Attack
It has been determined that the cases are concentrated in four attack types.
- Imitation of Third-Party Firm: Attackers carry out their attacks by impersonating the representative of the collaborating company.
- Manager Behavior: Attackers use social engineering (usually high-ranking) to create a fake message on behalf of a manager within the company. Gift card distribution has also been an increasing offensive content.
- Legal Correspondence Messages are usually sent on behalf of a lawyer or law firm, as most situations that require an immediate and confidential response are legal.
- Hijacking Corporate Email, it is the most dangerous method since the attacker reaches the emails within the company. Because it can easily imitate the communication style of the employee.
According to Symantec’s 2019 Internet Security Threat Report (ISTR), the top five subject lines used for BEC attacks are:
- Emergency
- Request
- Important
- Payment
- Attention
Stages of BEC Attack
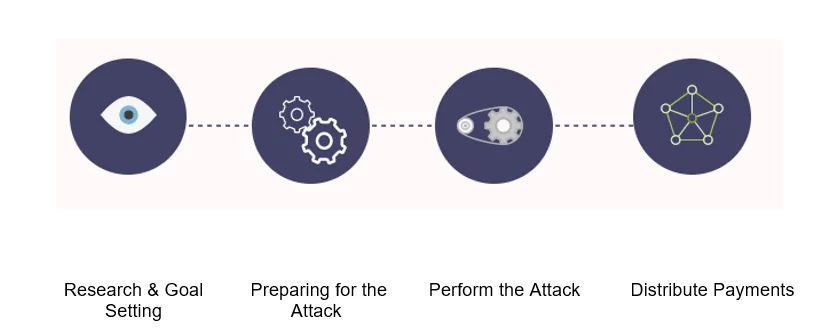
- Research & Set Goals
Attackers focus on their victims by doing research for days or weeks, searching company information (employee, manager profiles, organizational structure, etc.), contact data from websites, social media, and Dark & Deep Web, creating a profile of the targets. Common BEC targets include CEOs, lawyers, and personnel who can transfer funds on behalf of the organization.
- Prepare to Attack
Attackers prepare for an attack by creating fake domain names and email addresses, impersonating a trusted vendor/company, or hijacking the victim’s manager or colleague’s email account.
- The Attack Has Happened
A BEC attack can occur in an email or an entire conversation, depending on the vulnerability of the attacker. Uses urgent, persuasive sentences. Provides electronic instructions to send money to the victim’s fake account.
- Distribute Payments
Once the money is transferred to the attacker, it is quickly collected and distributed across multiple accounts to reduce traceability and the chance of recovery.
As with most cybersecurity incidents, Fast response times are critical to BEC attacks. If organizations are slow to detect a successful BEC attack, the money is unlikely to be recovered.
2-Recent BEC Attacks
CEO of FACC fired after firm was hit by BEC attack
On January 19, 2016, the Austrian aviation parts manufacturer FACC, whose customers include Airbus and Boeing, was attacked by the BEC. In an email, the attackers pretended to be CEO Walter Stephan, asking an employee to transfer money to a fake account for a fake bogus acquisition project.

Source: FACC, hit by cyber fraud
In the BEC attack, known as the “”fake president incident” attack, the FACC defrauded €42 million ($47 million). The company said it was only able to prevent the transfer of €10.9 million.
The firm’s supervisory board decided at a 14-hour meeting to dismiss CEO Walter Stephan with “immediate effect”. The fraud pushed FACC to an operating loss of 23.4 million euros in its 2015/16 financial year versus a loss of 4.5 million a year earlier.
Google and Facebook Suffered from BEC Attack Costing $100M
Google and Facebook were hit by a BEC attack that started with a single BEC email and ended with more than $100 million in lost money between 2013 and 2015. The attacker, Valdas Rimasauskas, posed as a Taiwan-based hardware company and defrauded Google and Facebook with a series of fake invoices sent to companies.

Source: Google and Facebook Fraudster Pleads Guilty to $100 million Scam
3- How to Prevent BEC Attacks
Threat actors use various technical tricks and social engineering methods to carry out BEC attacks.
In addition, the following steps help prevent BEC attacks:
- Customize your anti-spam settings properly and use powerful spam filters: You need powerful spam filters that can prevent files containing malware, phishing domain links etc. from reaching users.
- Do not open suspicious-looking attachments: This explanation does not only apply to messages sent by people you do not know. It also applies to senders you believe are your acquaintances. The vast majority of BEC attacks that originate from phishing are the result of obtaining the credentials of administrator-level employees.
- Avoid giving out personal information: Attackers may aim to send a phishing email in preparation for the attack, and they need to get your information from somewhere. They can obtain it using OSINT techniques by reviewing your social media posts or public profiles for important information.
- Use the Show File Extensions feature: This is useful when scammers are trying to use a confusing technique where a file appears to have two or more extensions.
- Authenticate email users: You should also use technologies such as SPF, DMARC, and DKIM to prevent malicious people from using email spoofing techniques.
- Install a browser plugin to block pop-ups: Pop-ups act as a common entry point for attackers to launch ransomware attacks. That’s why you should look into installing browser add-ons to stop pop-ups in their tracks.
- Periodically train employees against social engineering. By providing a workshop and/or simulation environment, training of employees on BEC attacks can be provided.
- Block known malicious Tor IP addresses
4- How to Use SOCRadar for Detecting BEC Attacks Earlier?
With the SOCRadar Unified Threat Intelligence Service, SOCRadar protects from BEC attacks with the following items.
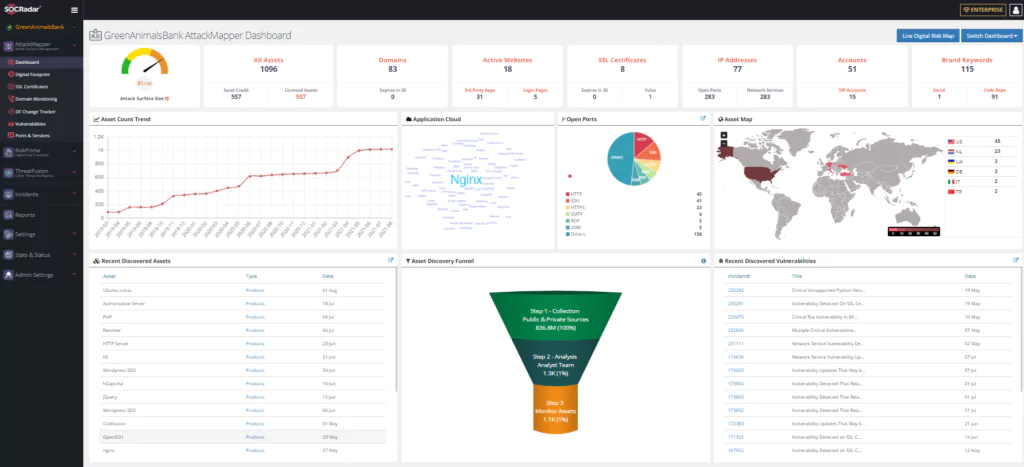
SOCRadar AttackMapper module prevents and quickly detects ransomware attacks by discovering and tracking your assets on the internet:
- Making an inventory of digital assets open to the Internet,
- Searching the e-mail accounts of your employees on the Dark & Deep Web via your MX registered domains and reporting the disclosure of your company employees’ e-mail accounts and the seizure of their passwords.
- Investigation of private e-mails of VIP and critical personnel (finance, developer, information security, Legal department, etc.) on Dark & Deep Web and reporting the situation of their passwords being compromised.
- With the DLP identifiers feature, your company’s Credit card, Critical personnel information (Identity Number, Telephone Number) etc. are searched on the Dark & Deep Web and the disclosure situation is reported.
- Provides SPF, DMARC, and DKIM control on your MX registered domains used to prevent email spoofing techniques.
SOCRadar RiskPrime Module provides the detection of intelligence information about your assets and your company:
● Creating alarms in possible situations by automatically tracking company domains in Dark and Deep web environments,
● The HUMINT ability of SOCRadar dark web analysts provide your company to communicate with the threat actor for confirmation of the accuracy of up-to-date information and remove postings for increasing the company’s reputation when necessary
● Creating alarms in possible situations by automatically following the 3rd party companies providing services to your company in Dark and Deep web environments,
SOCRadar ThreatFusion Module provides intelligence on current cyber events:
● Vulnerability Tracking with internal/external systems and/or applications for vulnerabilities notifications,
● Integration of IOCs used by threat actors into security devices,
● Integration to detect and block phishing domains for phishing/BEC attack purposes,
● Active monitoring of threat actors,
● Threat sharing about BEC attacks actively informs security personnel.
● Analyzing suspicious files with the Threat Analysis module.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free


































