
How to Integrate Vulnerability Intelligence Into SDLC Pipelines?
The Software Development Lifecycle (SDLC) is a systematic process utilized by development teams to design, create, and deliver top-notch software. Its primary aim is to mitigate project risks with thorough planning, ensuring customer expectations are met from conception to maintenance. Thus, integrating security measures across the SDLC stages is critical to ward off potential attacks and ensure the software’s effectiveness.
Securing the SDLC pipelines requires directly integrating security measures into it; developers must ensure that they are coding with potential vulnerabilities in mind.
One of the best practices for securing your SDLC pipelines is continuous monitoring, a common procedure in many business operations. Integrating vulnerability intelligence into SDLC pipelines can also significantly enhance software security throughout its development lifecycle.
By integrating automated security testing into the SDLC pipelines, you can ensure that your product has fewer security flaws and vulnerabilities for attackers to exploit. This prevents security issues from making it into production and ensures existing vulnerabilities are triaged timely.
This article touches on simple steps for integrating vulnerability intelligence into your development processes, as well as how it can be easily automated to improve security.
Ensure Security of SDLC Pipelines with Automated Vulnerability Detection and Management
SOCRadar maintains a comprehensive inventory of organizational digital assets and continuously monitors them. This proactive approach triggers alerts to customers in the event of a security incident, empowering them to react promptly and effectively. While it’s convenient to make swift decisions when a platform or service is already proficiently monitoring for you, it’s undeniable that further automation in SDLC pipelines simplifies the process even more.
Automated procedures can be deployed to halt the pipeline if a security vulnerability emerges in the environment, paving the way for a more secure development setting.
Beyond merely halting the pipeline, these procedures can also automatically create bug tickets, send notifications via email or messaging systems, and even trigger additional security scans, ensuring that relevant parties are promptly informed and corrective actions are initiated efficiently.
For instance, consider an organization that uses Jenkins to automate its pipeline, outlining its workflows and steps. The process of detecting vulnerabilities at different development stages can be automated using a dependency checker tool.
However, addressing the vulnerabilities discovered necessitates a dependable and continuously updated knowledge base for vulnerability information. Here, SOCRadar’s Vulnerability Intelligence comes to the fore. You can seamlessly integrate its capabilities into your SDLC pipelines using the API, providing a robust solution for vulnerability management and ensuring the security of your digital assets.
Why Automation?
The integration of automated security measures, such as vulnerability detection, into the Software Development Life Cycle (SDLC) pipelines is essential for several compelling reasons:
- Efficiency and Time-Saving: Automated vulnerability management tools can swiftly scan and evaluate multiple software and systems, saving valuable time and resources compared to manual methods.
- Comprehensive Coverage: Manual security testing is constrained by the tester’s knowledge and time, which can lead to overlooked vulnerabilities. In contrast, automated tools can test for thousands of potential security flaws, ensuring a more exhaustive examination.
- Consistency and Reduction of Human Error: Automation streamlines security operations and minimizes the risk of human error, which is crucial for maintaining consistent security practices. This consistency is vital for detecting and responding to security incidents effectively.
- Real-time Detection and Response: Automated systems can monitor networks and systems around the clock, detecting and responding to threats in real time, which is not feasible with manual processes.
- Improved Software Quality: Integrating security into the SDLC pipelines from the outset results in more reliable and less error-prone software.
Many data breaches result from attackers exploiting a known vulnerability that could have been identified and patched with automated vulnerability management, potentially preventing the breach.
Recent statistics underscore the importance of automated security in the SDLC pipelines. A report with Google highlights regional statistics, demonstrating that vulnerability exploitation has risen as a primary intrusion vector. In the Americas, an exploit was the cause of intrusion in 41% of cases. The ratio is 39% for JAPAC and 37% for EMEA.
In essence, automating security measures in the SDLC is not just a best practice – it is a necessity. It enhances efficiency, coverage, consistency, and software quality while enabling real-time detection and response to threats. It can significantly reduce the risk of data breaches by preventing known vulnerabilities from being exploited.
Using OWASP Dependency-Check to Find Security Gaps Throughout SDLC Pipelines
There are varying ways to integrate – and automate – vulnerability intelligence within your SDLC pipelines. For this article, we used a Groovy script on a Jenkins pipeline to pull a vulnerable repository for testing purposes.
Our demonstration utilizes the OWASP Mutillidae II project from GitHub, an open-source, purposefully vulnerable web application, serving as a platform for web-security learners. Following this, we integrated the OWASP Dependency-Check plugin.
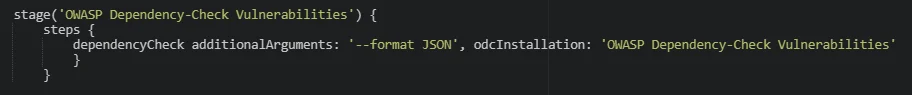
Invoking OWASP’s Dependency Check within a Jenkins pipeline stage
The OWASP Dependency-Check harnesses both public and private vulnerability databases, enabling us to identify known vulnerabilities in project dependencies. The plugin’s compatibility with various programming languages and package managers makes it an optimal choice for our testing scenario.
Building such a pipeline is also achievable by creating a ‘freestyle’ project on Jenkins. By configuring your development pipeline’s source code repository and invoking the dependency check in the build steps, it is possible to construct the same test case without directly utilizing Groovy.
Results from the Vulnerable Project
We can examine the results after the code repository is pulled and scanned with the dependency checker.
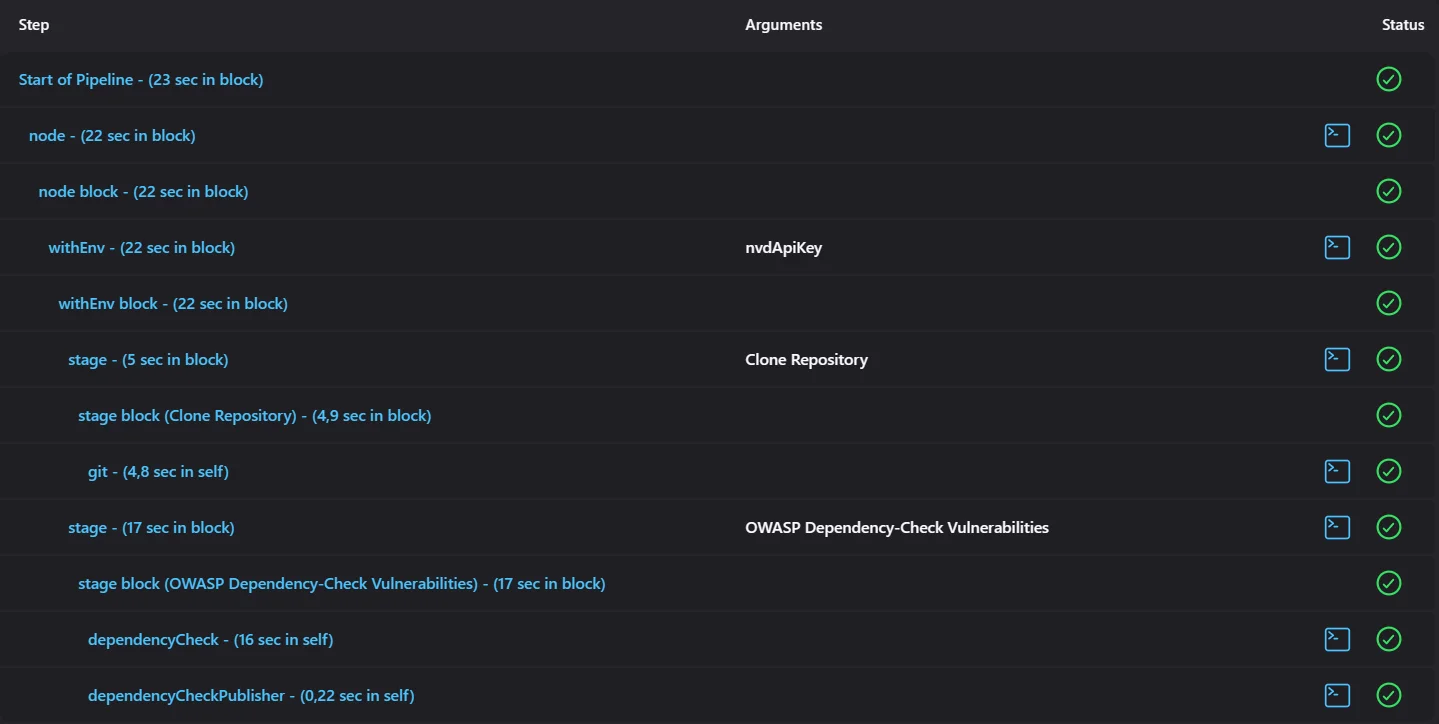
In quick steps, the pipeline pulls the repository and scans it using the dependency check plugin
The Common Platform Enumeration (CPE) information of the potentially vulnerable components is available in the resulting JSON file, and further down, we can find the identified CVEs.
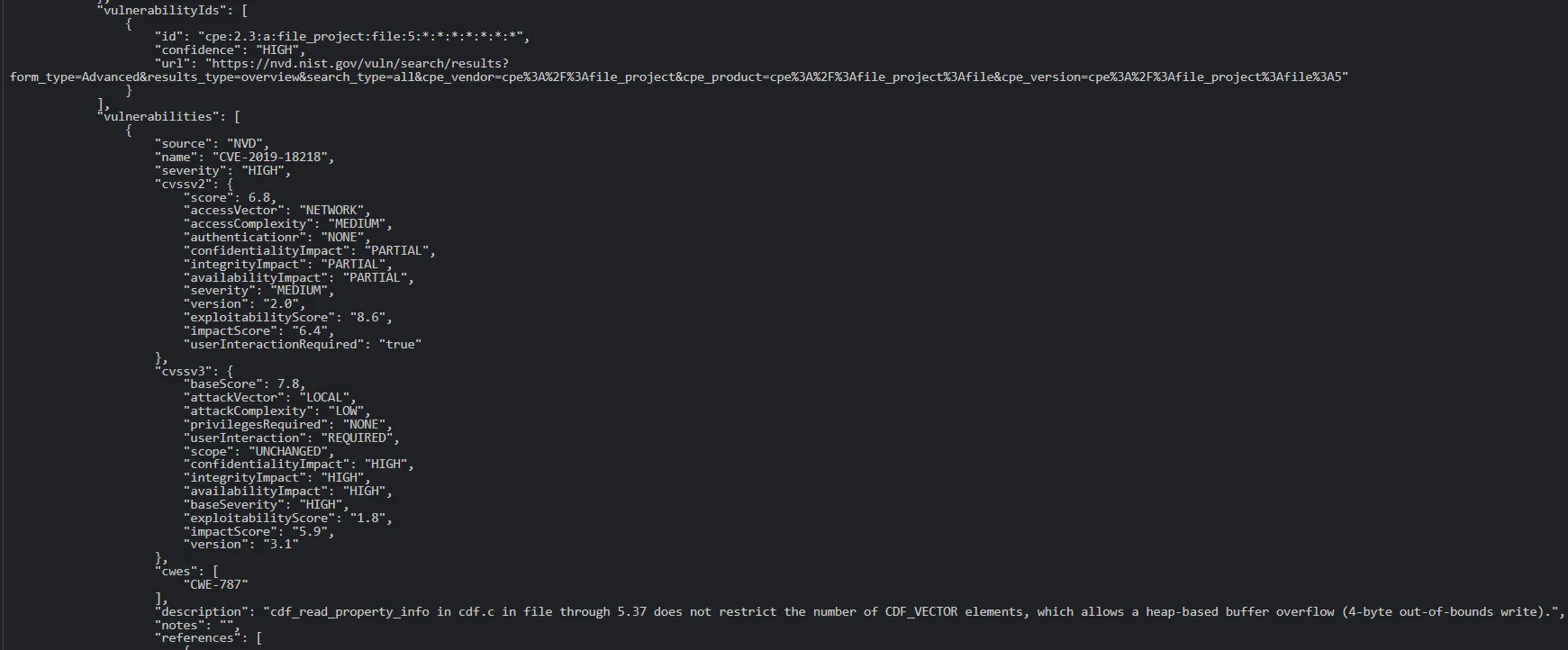
A view of CVEs in the JSON output
Numerous CVEs exist within the test application. For instance, we highlighted CVE-2019-18218 in the image above – a high severity Out-of-Bounds Write vulnerability in ‘file’, a utility for determining file types.
An HTML view of the dependency check report is also available:
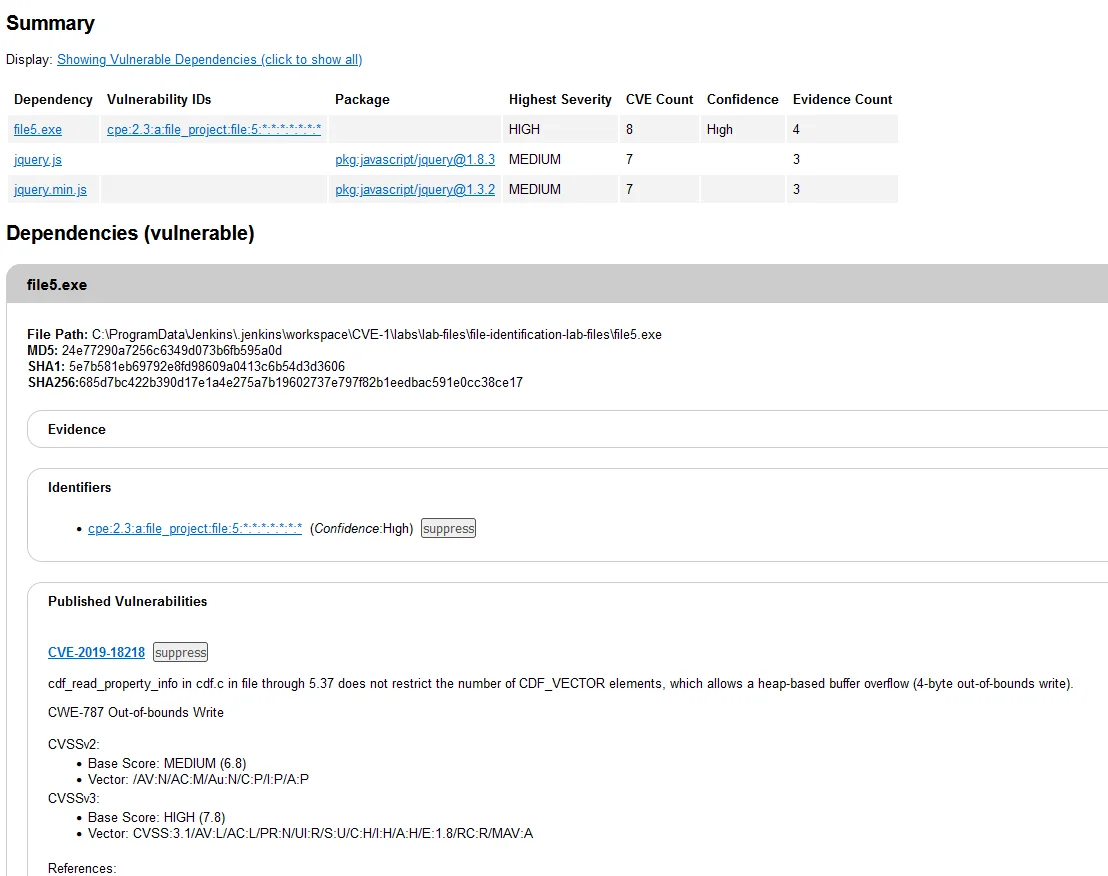
HTML view of the dependency check report
When we searched for the vulnerability on the SOCRadar platform, we found that exploits for this vulnerability were already available.
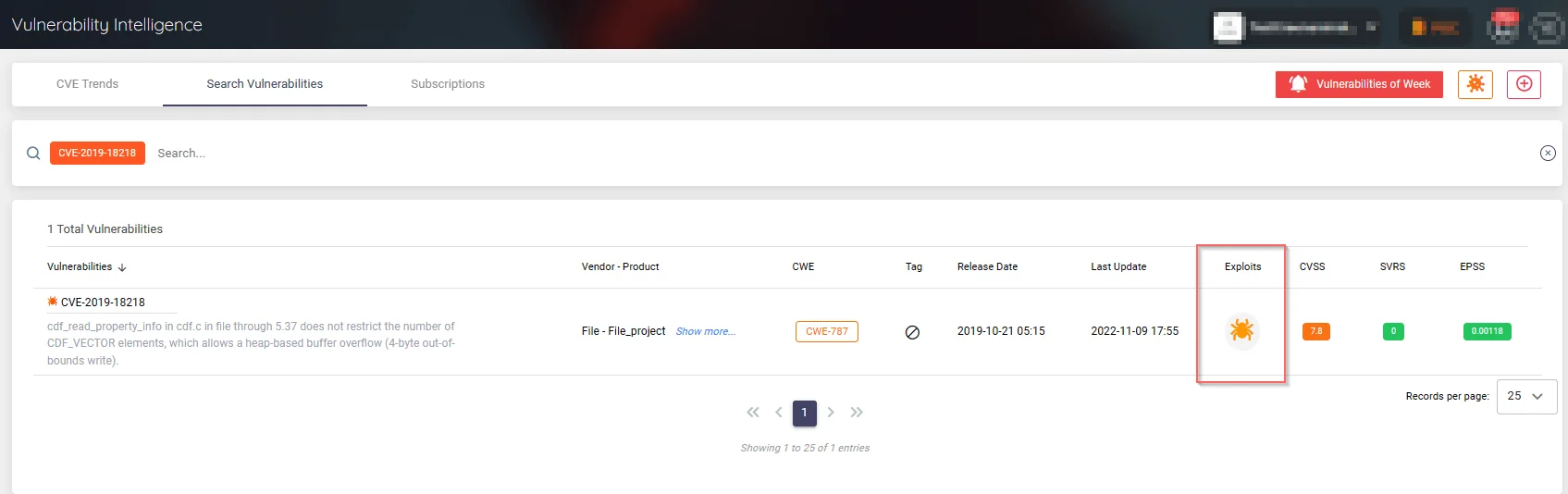
Searching for the vulnerability on SOCRadar’s Vulnerability Intelligence service
However, we can fully automate this search process, allowing the pipeline to determine this and decide on a quick action for rapid and enhanced protection against vulnerabilities.
This is where SOCRadar’s CTI Vulnerability API comes into play. With this API, you can obtain information and take action over vulnerabilities emerging in your assets.
We can extract the CVE identifiers from the JSON file with a short script. This script can be added to the previous Jenkins Workspace and run from there, or it can be added as a separate job. We added it as a separate job.
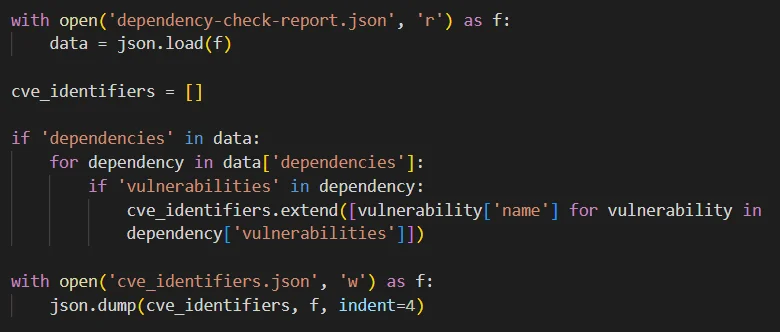
A simple script to extract CVE identifiers from the dependency check report
The script that is used initializes an empty list to store CVE identifiers. It checks if the JSON data contains the key ‘dependencies’ and iterates over each item under this key.
For each dependency, it checks if the key ‘vulnerabilities’ exists. If it does, the code extracts CVE identifiers from each vulnerability item and adds them to the list.
Finally, it writes the collected CVE identifiers to a new JSON file. We will use this last JSON file to make requests to the API and collect related vulnerability information.
Using the SOCRadar API to Gather Details About the Found Vulnerabilities
Once the CVE identifiers are extracted from the JSON file, they can be iterated through the SOCRadar API.
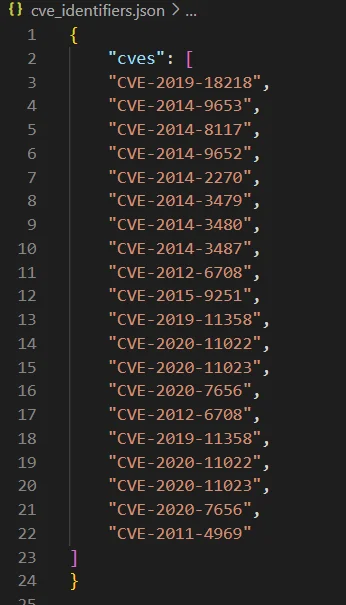
The JSON file for extracted CVE identifiers
We can parse the CVE list from JSON as text and send automated curl requests for each CVE. This can be done in a Jenkins stage with a script snippet, the output of which can be seen in separate JSON response files.
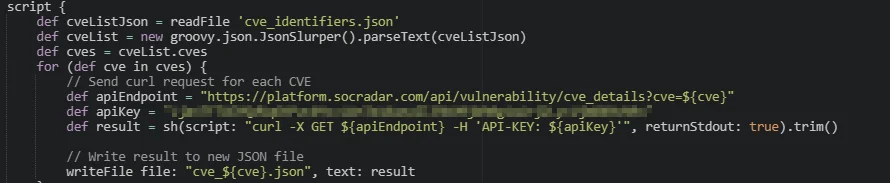
Integrating the script for successive API requests into the Jenkins pipeline
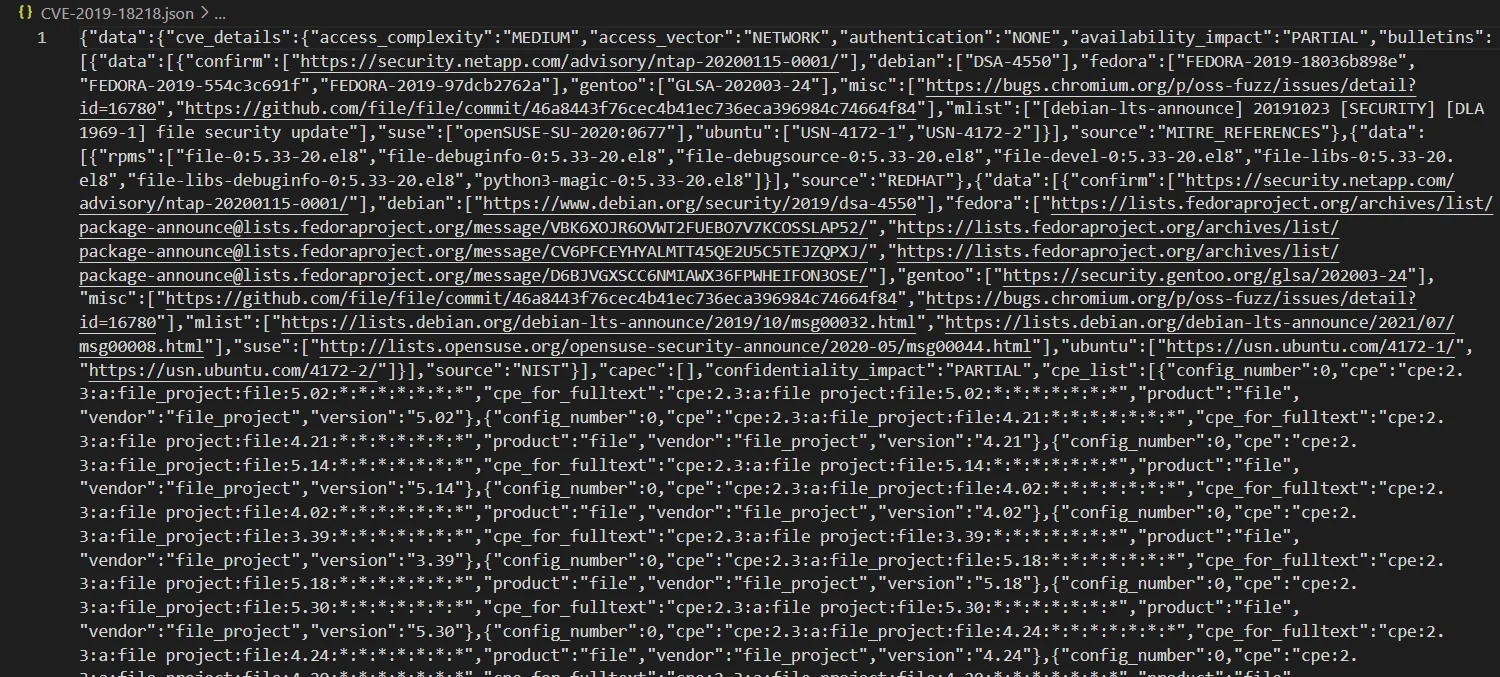
The SOCRadar CTI Vulnerability API returned the following JSON for one of the vulnerabilities
We aim to check if a vulnerability is exploited or a public exploit exists for the vulnerability, since attackers often utilize these in real-world attacks shortly after their emergence. To achieve this, we can filter all files using ‘jq’, a powerful command-line tool for parsing, filtering, and manipulating JSON data.
We use ‘jq’ to search a JSON file to find instances of “event_type”: “EXPLOITED”.
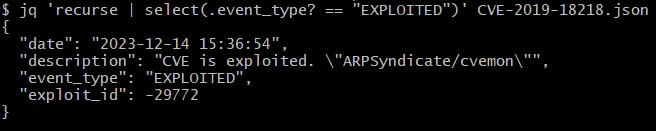
Filtering certain occurrences from a JSON file using jq
These event types accompany each update in the vulnerability’s lifecycle provided on SOCRadar’s Vulnerability Intelligence, and the event type “EXPLOITED” is used when an attacker exploits the vulnerability or when an exploit code becomes publicly available.
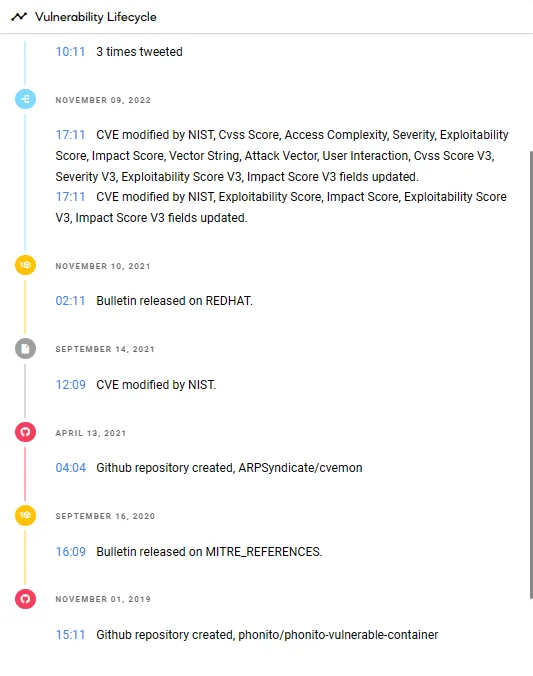
Vulnerability lifecycle view for CVE-2019-18218 from SOCRadar’s Vulnerability Intelligence
To iterate this process through all the JSON files for the identified and extracted vulnerabilities, a Bash script similar to the following can be used:
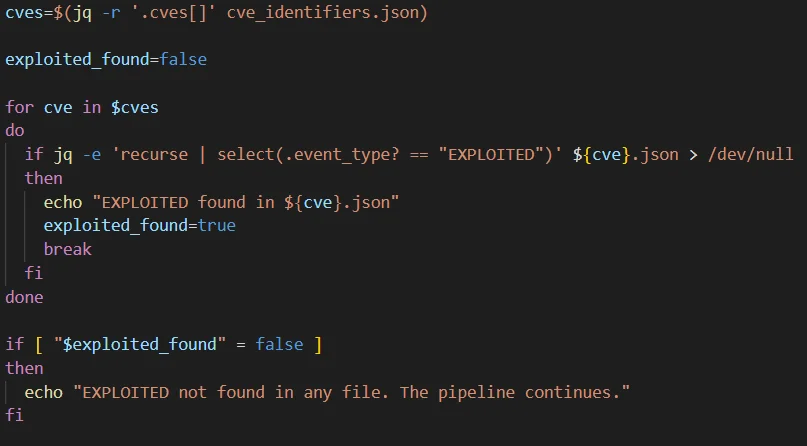
A script to find the exploit occurrences through all the CVE JSON files
This script reads the JSON file containing the CVE identifiers, iterating over each to locate the “EXPLOITED” event type within corresponding JSON files. If “EXPLOITED” is found in any of the JSON files, it prints a message indicating its presence. If not, it outputs a message stating so. Although this does not end the pipeline; it only terminates our loop. To exit the pipeline completely, you can append an exit code.
This Bash script can be run in a Jenkins pipeline by including it in a stage, or the logic can be used in any development automation tool. This allows for the connection of cases to a pipeline failure or resumption, thereby automating the process of identifying and acting upon vulnerabilities within used components.
What Are the Benefits of SOCRadar API Integrations?
This article highlights our utilization of the CTI Vulnerability API, one of the many API services offered by SOCRadar. The advantages of integrating with SOCRadar’s APIs are numerous and significantly contribute to cybersecurity and operational efficiency. The key benefits include:
- Increased Efficiency and Productivity: SOCRadar API integrations automate routine tasks, boosting team efficiency and productivity by allowing staff to focus on more strategic work rather than mundane manual tasks. Real-time monitoring of assets and alerting mechanisms via email or API enables faster response and helps maintain an up-to-date asset inventory.
- Proactive Vulnerability Management: API integration helps swiftly detect and remediate unknown assets or vulnerabilities that adversaries could exploit, reducing the risk of intellectual property theft.
- Compliance and Brand Protection: By making tracking of CEO fraud, business email compromise, and credential stuffing attacks easier, SOCRadar API integrations help protect the brand reputation and avoid regulatory penalties.
- Data Silo Elimination and Data Quality Improvement: API integrations break data silos, allowing for a unified view of data across systems, which improves data quality and prevents human errors.
- Security and Flexibility: Purposeful, actionable, and secure API integrations, such as SOCRadar’s, align with business goals and use cases, offering insights into various security threats and supporting asset management, threat tracking, and incident response.
- Ease of Management and Expert Support: SOCRadar’s API integrations are designed to be simple and easy to manage, with the option to speak with experts to evaluate the right APIs for a business’s specific needs.
Conclusion
By meticulously navigating each stage of the SDLC pipelines, development teams strive to minimize project risks and ensure that customer expectations are not only met but exceeded. A critical aspect of this process is the comprehensive integration of security measures, which plays a very important role in safeguarding against potential breaches and vulnerabilities.
Detecting and addressing vulnerabilities at each stage of development is essential for maintaining the integrity and security of the software. However, manual vulnerability detection processes are often time-consuming and prone to human error, leaving gaps that attackers can exploit. This is where automation emerges as a game-changer, offering a more efficient and effective approach to vulnerability management within SDLC pipelines.
With its extensive set of API endpoints, SOCRadar offers capabilities to improve security across development stages. From vulnerability intelligence to threat tracking, it equips organizations with the necessary tools to proactively identify and mitigate risks.
SOCRadar Integrations page – API references
Those looking for more information on securing SDLC pipelines can check out our previous article, “Implementing Cyber Threat Intelligence in Software Development Lifecycle (SDLC) Pipelines,” which contains additional practical tips and best practices for fortifying SDLC pipelines against evolving cyber threats.
Sign up for the Free Edition to test SOCRadar XTI now:

































