
How to Protect Against Digital Risks in Three Steps
threats to an organization’s digital assets are constantly evolving, cybercriminals are no longer solely focused on breaching your internal network; they are also looking for the most vulnerable link in your extended digital ecosystem. This often includes partners, suppliers, and third-party vendors who are integral to your operations but may inadvertently become gateways for cyberattacks. As such, protecting against digital risks now requires looking far beyond your organization’s immediate perimeter. To stay ahead of these threats, companies must adopt a comprehensive, proactive security strategy—and that’s where Digital Risk Protection (DRP) comes into play.

DALL-E illustration of DRP
Digital Risk Protection provides the external threat intelligence and continuous monitoring needed to mitigate third-party cyber risks. By understanding the vulnerabilities introduced by your digital supply chain, embracing global best practices, and implementing a well-structured DRP program, you can enhance your overall security posture. The following sections will guide you through the essentials of DRP, its role in combatting third-party cyber threats, and the steps to successfully integrate DRP into your existing security framework.
How DRP Addresses Third-Party Cyber Threats
In an increasingly interconnected digital ecosystem, organizations depend on a wide variety of third-party vendors, suppliers, and partners. While these relationships drive innovation and growth, they also introduce complex cyber risks that can compromise sensitive data, disrupt operations, and damage reputation. Digital Risk Protection (DRP) emerges as a pivotal solution for managing and mitigating these risks. By continuously monitoring and analyzing potential threats beyond the organization’s direct perimeter, DRP solutions help maintain the integrity of digital assets, protect customers, and uphold compliance standards. DRP’s proactive stance enables businesses to address risks before they escalate, ensuring a more resilient security posture in the face of an ever-evolving threat landscape.
1. Understanding Third-Party Cyber Risks: Why Your Organization Needs DRP
Third-party cyber risks stem from vulnerabilities, breaches, and malicious activities originating outside of your company’s direct control. These risks can emerge from vendors with inadequate security measures, subcontractors with compromised credentials, or suppliers unknowingly harboring malware. The potential impacts are substantial—ranging from data exposure and financial fraud to operational downtime and regulatory fines. For instance, a logistics partner could be targeted by a ransomware attack, halting critical supply chain processes and triggering a cascade of disruptions across your entire operation.
DRP solutions address these concerns by proactively scanning external digital ecosystems—websites, social media platforms, cloud environments, dark web forums, and more—to identify suspicious activities and vulnerabilities associated with third-party entities. This early detection not only prevents threats from infiltrating your organization through external links, APIs, or shared tools but also helps maintain trust among stakeholders. In essence, organizations that implement DRP are better equipped to anticipate, identify, and respond to digital threats stemming from their broader business ecosystems, ensuring that even when working with numerous partners, the integrity of their data and operations remains uncompromised.
2. Impact on Global Cybersecurity Practices
The rise of DRP solutions is reshaping how organizations approach cybersecurity on a global scale. Traditional security measures often focus narrowly on an organization’s internal networks and endpoints, inadvertently leaving gaps that attackers can exploit through the organization’s many interconnected partners. DRP extends the boundary of cybersecurity strategies, reinforcing them with extensive intelligence-gathering capabilities, external vulnerability assessments, and automated alerting systems.
Globally, this shift has encouraged a more holistic view of cybersecurity. Instead of treating external risks as an afterthought, leading organizations now view them as integral components of their overall defense strategy. As a result, new best practices include continuous external threat monitoring, establishing detailed risk profiles for third parties, and adopting frameworks like Zero Trust at a more granular scale. In turn, DRP solutions have inspired international standards and guidelines, pushing vendors, suppliers, and partners to strengthen their security measures. By fostering an environment in which all stakeholders recognize their shared responsibility for cybersecurity, DRP helps create a more resilient and secure global digital landscape.
3. Implementing a DRP Strategy to Enhance Cybersecurity Resilience
To integrate DRP into your cybersecurity framework effectively, consider the following steps:
- Identify Your Third-Party Landscape:
Begin by mapping out your entire network of external partners, suppliers, and service providers. Understanding the breadth and depth of these relationships ensures that your DRP strategy targets the right areas. - Define Clear Security Criteria for Vendors:
Establish baseline security requirements that vendors must meet. These can include adherence to specific compliance standards, regular penetration testing, and maintaining updated certifications. DRP tools can help verify compliance and alert you to any deviations. - Select DRP Tools and Services:
Evaluate specialized DRP platforms or managed security services that offer continuous external threat intelligence, brand protection, dark web monitoring, and vulnerability scanning for partner ecosystems. Consider solutions that integrate with existing SIEM or SOAR tools for streamlined workflows. - Integrate DRP with Existing Cybersecurity Protocols:
Incorporate DRP alerts and insights into your Security Operations Center (SOC) processes. When a third-party risk is detected, ensure the proper escalation paths are in place for rapid incident response and remediation. - Regularly Review and Update Your DRP Strategy:
The digital landscape is dynamic, and so are the risks. Continuously refine your DRP approach by analyzing past incidents, reviewing vendor performance, and staying informed about emerging threat trends.
By embedding DRP into your cybersecurity framework, you strengthen your organization’s overall resilience. Proactive intelligence gathering and continuous external monitoring reduce the likelihood of devastating breaches, data leaks, and costly downtime. With a robust DRP strategy in place, your organization can confidently navigate the complexities of digital business relationships, maintaining a competitive edge, safeguarding sensitive information, and fostering trust among customers, investors, and partners alike.
Uncover Digital Risks with SOCRadar’s Advanced DRP Solution
Protecting against third-party cyber threats necessitates proactive monitoring and full visibility into your digital ecosystem. SOCRadar’s Digital Risk Protection (DRP) module enables businesses to protect their digital assets effectively.
From detecting vulnerabilities and impersonation attempts to monitoring dark web activity and external-facing assets, SOCRadar DRP provides real-time insights to mitigate risks before they become critical. Your organization can keep up with evolving cyber threats thanks to an intuitive interface, streamlined alerts, and actionable threat intelligence.
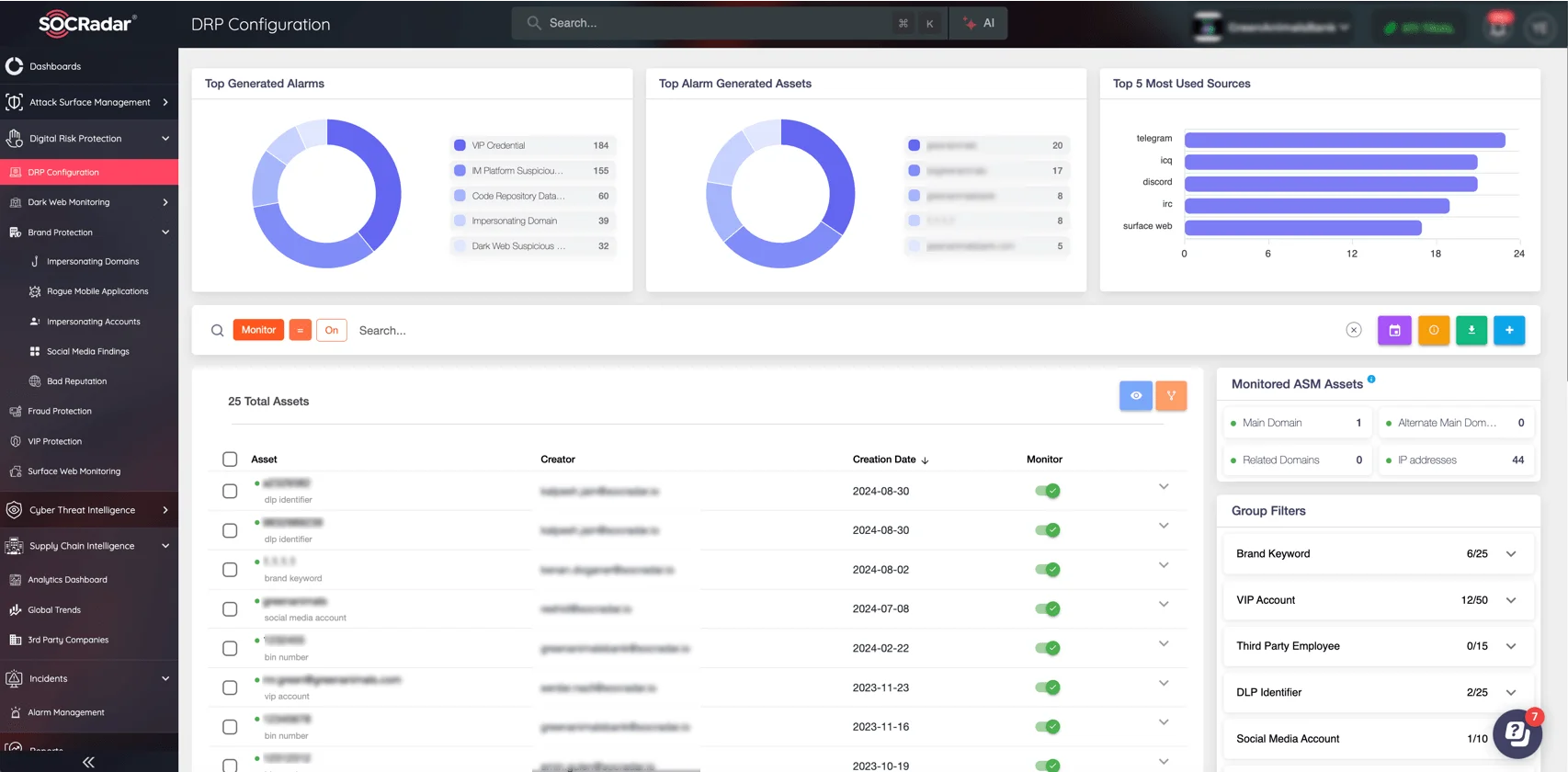
SOCRadar DRP Dashboard: Real-time insights into alarms, assets, and external threats
Improve your cybersecurity strategy today with SOCRadar’s DRP module—because protecting your organization necessitates thinking beyond the perimeter.


































