Inside the Mind of a Ransomware Boss: An Interview with the LockBit Administrator
As the effectiveness of ransomware attacks continues to escalate, they have emerged as the most significant challenge in today’s digital landscape. Despite ongoing efforts by the Cyber Security community to combat these malicious activities, threat actors persist with their diverse methods. However, the reactive measures employed against these known adversaries merely help to mitigate the risk rather than eradicate it entirely. Consequently, it becomes imperative for the cyber security industry and its authorities to enhance their analysis of adversaries and adopt proactive measures to counter the ever-evolving threat landscape.
In this blog post, we delve into an interview conducted by vx-underground, where they had the chance to converse with LB0, the leader of the LockBit, the most active ransomware group. The interview offers a deep dive into the operations of the LockBit, uncovering their tactics and offering valuable perspectives on the cybersecurity landscape. This insightful interview provides a unique opportunity to gain insights into the mindset of a ransomware leader. We will analyze the interview while considering the potential falsehood of the information shared.
An analysis of the interview
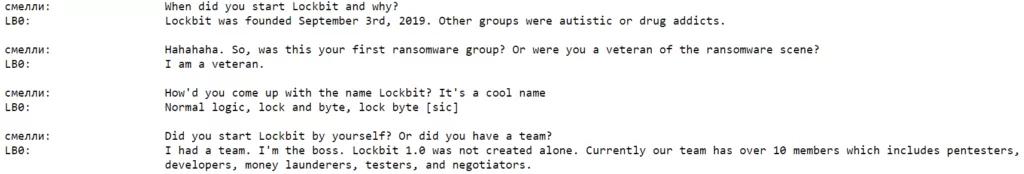
The interview begins by referencing LockBit’s origins and revisiting well-known topics. As expected, it has been reiterated that the threat actor behind LockBit is a seasoned ransomware operator. Their humiliating accusations against other groups may also reveal the rivalry, perhaps hostility, between existing threat groups. They mention that the group staff is ten people. Even if this claim is accepted as valid, it should not be surprising that the group that has made the most attacks in the last year has few members because LockBit, as the most active RaaS group, can use affiliates alongside its staff and shift the burden of infiltrating a system to others.
Fewer people – more effect, a win-win model of ransomware affiliation
In recent years, the RaaS (Ransomware-as-a-Service) model has gained significant popularity among ransomware operators. Instead of deploying their own ransomware through their intrusion operations, these groups opt to lease numerous affiliates, often numbering in the tens or even hundreds, and share profits based on a percentage arrangement. Collaborating with such an extensive network of partners significantly enhances their operational capabilities, leading to a highly lucrative collaboration for both ransomware groups and other hackers involved. As a result, the core staff of ransomware groups remains more diminutive, but this has the dual effect of increasing the profit margin per person and bolstering operational security.
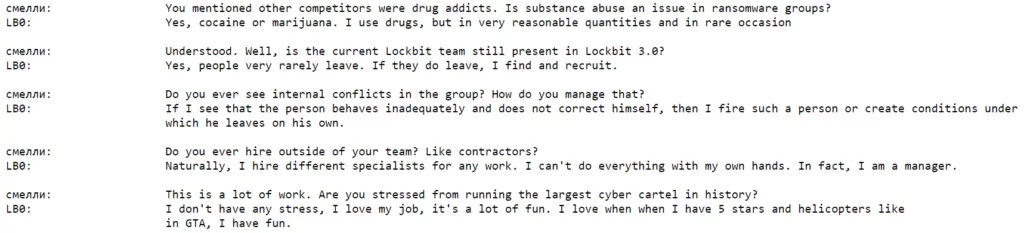
The claim that drug use is common among ransomware operators may be one of the true claims. In the Dark Web Market research conducted by SOCRadar, we have seen that the primary source of income for these illegal environments is the drug trade. In fact, 80% of the sales in these black markets were on drugs, and in this context, it is not surprising that drug use is common among threat actors. Apart from that, they talk about in-group dynamics, and we see that employees who are not well-behaved are fired or forced to resign. It is not known how to get word of confidentiality from the members who leave the group, but the information leaked by someone inside can be one of the most important leads for the authorities. The cessation of Conti‘s operations was also due to an internal conflict. In June 2023, US Justice Department arrested and charged a Russian national with LockBit affiliation last month. Such developments may be the steps that will bring the inevitable end of the LockBit. To give an example from another group, the US State Department announced rewards of up to $10 million for information that would disrupt the Cl0p ransomware operation. Again, it can be said that these actions aims to destroy such groups from within.
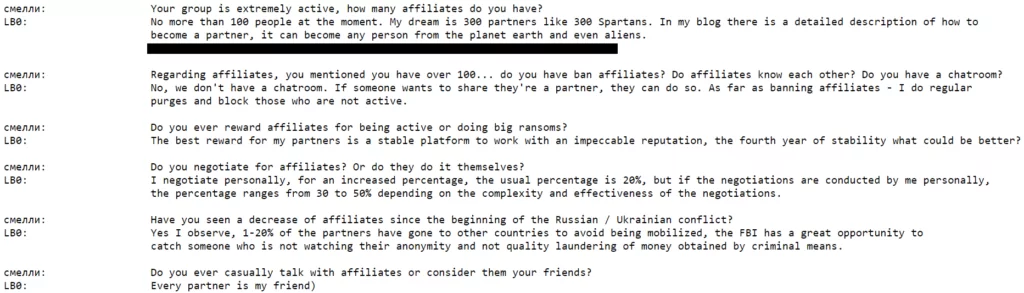
As we mentioned above, they say that while they have ten members, they have over a hundred affiliates and talk about their intention to increase. An increase in this number may indicate that the number of victims of LockBit will increase. Another interesting point in these dialogues is the claims of not using chat rooms; considering that the leaks in Conti started with the leaking of Rocket Chat conversations, it can be said that they act more cautiously in this context.

Toward the end of the interview, cashing out is mentioned. The LockBit admin says this is easy and tells about the alleged method. He/she says s/he first exchanged ransom money through Chinese exchangers. This is actually a good example of how Russian and Chinese threat actors support each other in illegal operations. It is claimed that when money is circulated on exchangers and different cards for a while, it is withdrawn from ATMs via couriers called “mules” and delivered to the LockBit admin in person. Even if the couriers don’t know who they are delivering the money to, it can be considered as an important lead for the authorities. Another interesting point is that this cash is transferred to restaurants, which are legal businesses that the LockBit admin claims they own, for further laundry. Even if the allegations are not 100% reliable, they talk about the location of the restaurants, and this information can be considered an important lead in identifying the restaurants that can be connected to the same person and the admin of LockBit.
Check out the vx-underground’s original interview for a few other random fun questions.
LockBit Interview in Summary
This interview offers crucial perspectives on the thought processes of a ransomware boss. Similar to any malicious actor, their drive to satisfy their ego and generate profits can be observed. Consequently, gaining insights into the inner workings of ransomware groups can enhance our understanding of the adversary and enable us to better comprehend their tactics, techniques, and procedures (TTPs). While the interview may not directly provide actionable clues for organizations, it holds potential for evaluation by authorities and cyber threat intelligence firms.
SOCRadar is also working to continuously monitor threat actors, primarily ransomware groups like LockBit, to provide usable intelligence data to their users. In this context, Vulnerability-Ransomware Check, one of our most recently added features in our Attack Surface Management module, scans the assets of our users and presents them to you, taking into account the security vulnerabilities frequently exploited by Ransomware groups.