
Is Lapsus$ Extortion Group “Officially Back from Vacation”?
The Lapsus$ group announced that they would be on vacation until March 30 after the notorious Okta attack. In the early hours of yesterday morning, the threat actor announced that they were “officially back from vacation” in a post on the group’s Telegram channel.
Lapsus$ has shared a 70GB data leak that it claims is customers’ source code from Luxembourg-based global software company Globant. It seems they will continue their attack despite the arrests of alleged group members in the United Kingdom on March 24.
What’s in the Leak?
Lapsus$’s post on the Telegram channel, which has been regularly monitored by SOCRadar analysts, shows the group leaked 70GB of data allegedly belonging to Globant clients.
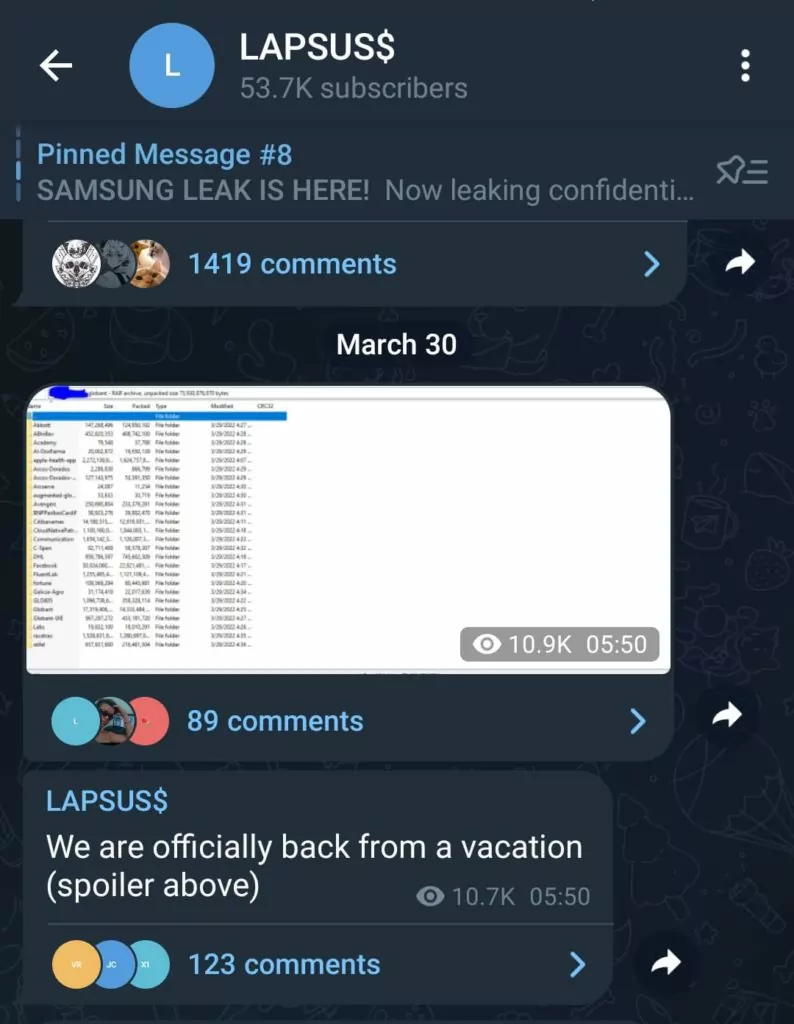
In the screenshots, the leak files show the names of “Facebook,” “apple-health-app,” and giant companies such as DHL, Citibank BNP Paribas. Cybersecurity researchers have yet to decide whether these files evidence customer data exposure.
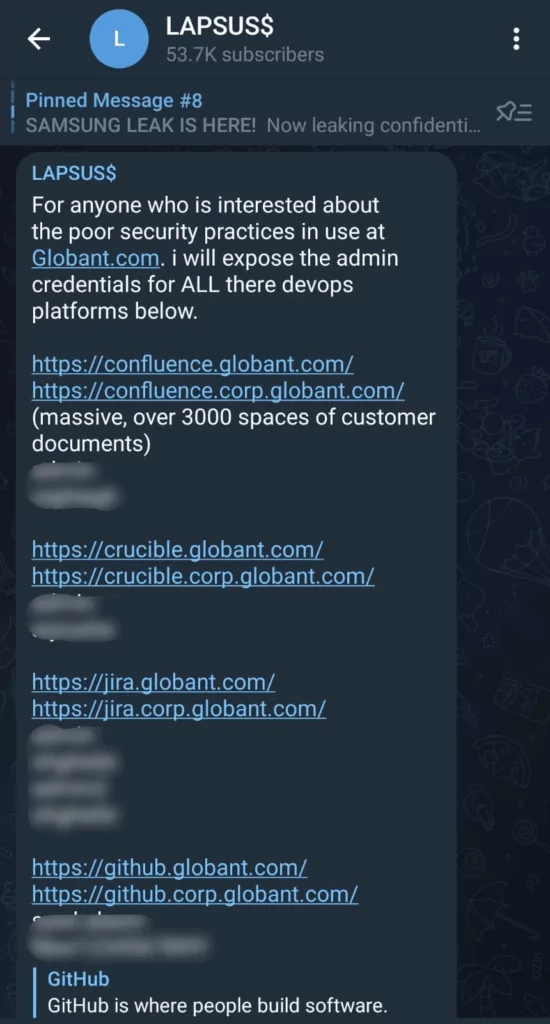
Another message shared by the threat actor, credentials of the system admins, is exposed. The group appears to have revamped the method in the Okta attack. Capturing credentials and accessing the tools used by the victim through them is considered the modus operandi of Lapsus$.
What Happened Before?
Lapsus$ has only made headlines for its attacks in the past few months. The group responsible for the data breaches of Samsung, NVIDIA, Microsoft, and Okta also attracted attention by using a different technique than ransomware gangs.
Although the threat actors leak data, they do not use ransomware. They prefer to capture data and demand ransom rather than encrypt it. Among the ransomware groups where the double extortion method is widely accepted, there is growing consensus that Lapsus$ is having different working and income model.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access.



































