Ivanti Avalanche Critical Buffer Overflow Vulnerabilities: CVE-2023-32560
Two critical vulnerabilities, collectively identified as CVE-2023-32560, have been discovered within Ivanti Avalanche, an enterprise mobility management (EMM) solution responsible for managing, monitoring, and securing various mobile devices.
The flaws have been classified as critical (CVSS v3: 9.8) and can be exploited remotely without requiring user authentication. This potentially enables malicious actors to execute arbitrary code on the targeted system.
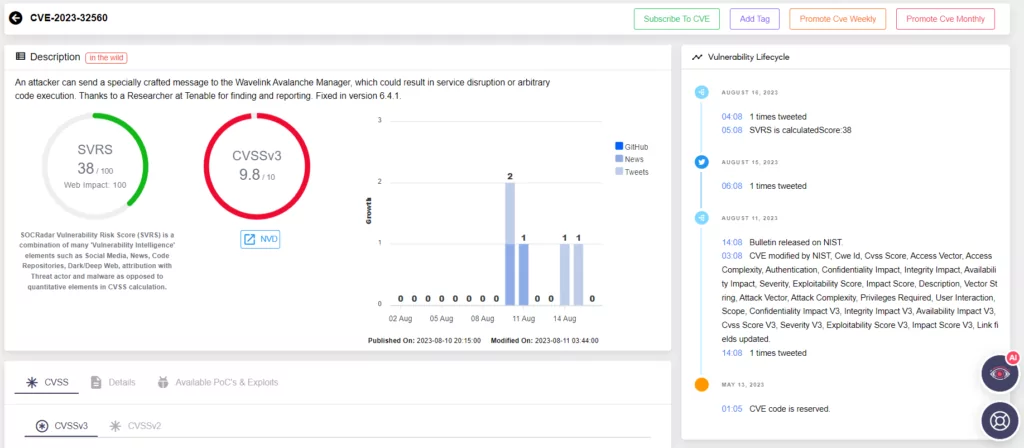
Affected Versions and Exploitation of Ivanti Avalanche Vulnerabilities
The vulnerability specifically impacts version 6.4.0.0 and earlier of WLAvalancheService[.]exe, which is communicated through TCP port 1777.
The exploitation involves attackers sending specially crafted data packets containing either hex strings (type 3) or a list of decimal strings separated by semicolons (type 9).
For data type 3, the executable WLAvalancheService[.]exe employs a stack-based buffer of fixed size to hold converted binary data from a hex string. An unauthenticated remote attacker can cause a buffer overflow by inputting a long hex string.
Similarly, with data type 9, WLAvalancheService[.]exe uses a fixed-size stack-based buffer to store user-provided data, which is then converted to an integer using atol().
Ivanti Avalanche Security Update: Patching Multiple Vulnerabilities
Researchers identified these vulnerabilities and notified Ivanti on April 4, 2023. Subsequently, a proof-of-concept was shared with the vendor on April 13, 2023.
After extending the disclosure timeline to grant Ivanti more time to address the issue, a security update was released on August 3, 2023, introducing Avalanche version 6.4.1.
Avalanche version 6.4.1 not only resolves CVE-2023-32560 but also addresses several other vulnerabilities:
- CVE-2023-32561 (Ivanti Avalanche dumpHeap Incorrect Permission Assignment Authentication Bypass Vulnerability)
- CVE-2023-32562 (Ivanti Avalanche FileStoreConfig Arbitrary File Upload Remote Code Execution Vulnerability)
- CVE-2023-32563 (Ivanti Avalanche updateSkin Directory Traversal Remote Code Execution Vulnerability)
- CVE-2023-32564 (Ivanti Avalanche FileStoreConfig Arbitrary File Upload Remote Code Execution Vulnerability)
- CVE-2023-32565 (Ivanti Avalanche SecureFilter Content-Type Authentication Bypass Vulnerability)
- CVE-2023-32566 (Ivanti Avalanche SecureFilter allowPassThrough Authentication Bypass Vulnerability)
The Ongoing Threat Landscape Surrounding Ivanti
Given Ivanti’s deployment in critical systems and environments, the constant hunt for severe vulnerabilities by threat actors underscores the potential for these vulnerabilities to serve as gateways for malicious activities.
Additionally, hackers recently exploited a zero-day authentication bypass vulnerability (CVE-2023-35078) in Ivanti Endpoint Manager Mobile (EPMM). This flaw enabled unauthorized access to a platform utilized by multiple ministries of the Norwegian government, potentially compromising sensitive and classified information. You can read our blog post about vulnerability here to learn more.
Enhancing Vulnerability Management and Digital Asset Protection with SOCRadar
At SOCRadar, we’ve designed our Vulnerability Intelligence to give you full support in effectively managing vulnerability issues and prioritizing essential patches. Our platform lets you easily search for and access detailed information about vulnerabilities, helping you stay ahead of potential threats.
Furthermore, our External Attack Surface Management (EASM) is a key player in safeguarding your digital assets. Through this advanced system, we carefully discover and monitor your digital landscape. We’ll quickly let you know if any issues arise that might pose a security risk. With SOCRadar, you can trust that we’re here to provide proactive protection for your online presence.