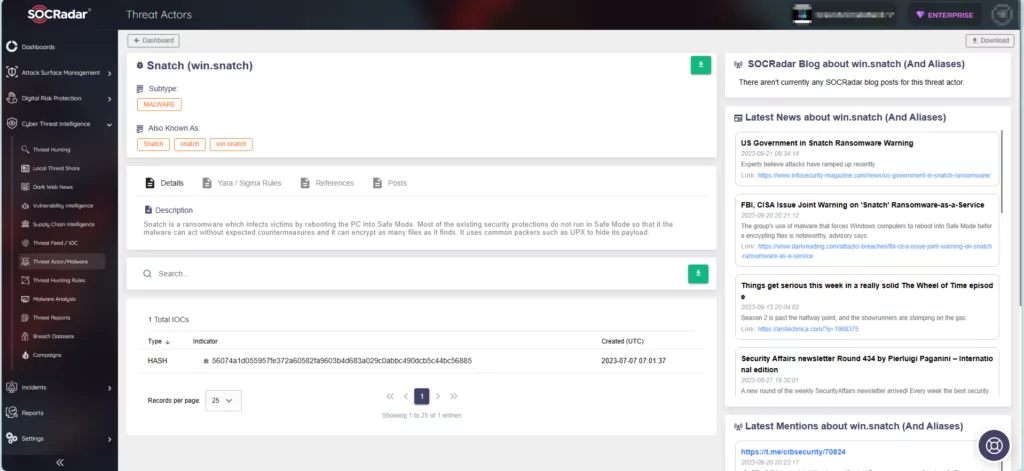
Joint Advisory by CISA and FBI: Snatch Ransomware
The FBI and CISA have recently issued a joint cybersecurity advisory (CSA) concerning the Snatch ransomware variant. The advisory provides comprehensive insights into Snatch ransomware operations, encompassing its Indicators of Compromise (IoCs) and Tactics, Techniques, and Procedures (TTPs).
Within the advisory, it is mentioned that the Snatch ransomware variant was identified through FBI investigations as recently as June 1, 2023, and is involved in data theft and extortion activities.
In this blog post, we will summarize the key points in the advisory, outline the operations of Snatch ransomware, and explore the latest attacks.
What is the Origin of Snatch Ransomware?
The Snatch ransomware variant first appeared in 2018, employing a Ransomware-as-a-Service (RaaS) model. The group is reported to have claimed their first victim in the United States in 2019 and refined their tactics since mid-2021.
Their targets encompass a wide array of critical infrastructure industries, including the Defense Industrial Base (DIB), Food and Agriculture, and Information Technology.
The advisory mentions that the Snatch ransomware group was originally known as “Team Truniger,” after a key group member named “Truniger,” who previously worked as an affiliate of GandCrab.
Snatch Ransomware’s Extortion Tactic
Snatch threat actors actively engage in data exfiltration, employing the double extortion tactic wherein they leak victim data if the demanded ransom remains unpaid. Notably, these threat actors have been observed acquiring previously stolen data from other ransomware variants, with the aim of pressuring victims to pay a ransom in order to prevent the release of their data on Snatch’s extortion blog.
CISA’s advisory highlights that, since November 2021, an extortion site operating under the name Snatch has been available on both Clearnet and TOR, hosted by a bulletproof hosting service. It is further noted that individuals claiming association with the blog asserted that the blog had no connection to Snatch ransomware, despite the presence of confirmed Snatch victims’ data on the blog, alongside victims associated with other ransomware groups, Nokoyawa and Conti.
How Does the Snatch Ransomware Attack?
To infiltrate victim networks, they exploit Remote Desktop Protocol (RDP) vulnerabilities and occasionally acquire compromised credentials from cybercriminal forums. They establish persistence on victims’ networks via administrator account compromise, connecting to a command and control (C2) server on a Russian bulletproof hosting service through port 443, and initiating RDP connections.
Data discovery and lateral movement are facilitated using the “sc[.]exe” command, as well as tools such as Metasploit and Cobalt Strike. Before deploying ransomware, they dedicate up to three months to exploit victim networks, moving laterally and searching for files to exfiltrate, followed by the actual exfiltration of data.
During deployment, Snatch actors try to disable antivirus software and execute a file named “safe[.]exe.” In recent attacks, the ransomware executable’s name consists of a string of hexadecimal characters matching the SHA-256 hash of the file, aiming to evade rule-based detection.
Furthermore, it is reported that Snatch ransomware actors utilize a customized variant known for its ability to reboot devices into Safe Mode, effectively evading antivirus and endpoint protection before encryption of files.
After execution, the ransomware payload modifies registry keys, utilizes native Windows tools for enumeration, creates processes to execute specific batch (.bat) files, and subsequently deletes volume shadow copies. Once the batch files have been executed, the ransomware executable removes them from the victim’s file system.
Encrypted files receive unique hexadecimal appendages, specific to each infection, accompanied by a “HOW TO RESTORE YOUR FILES.TXT” text file in each folder.
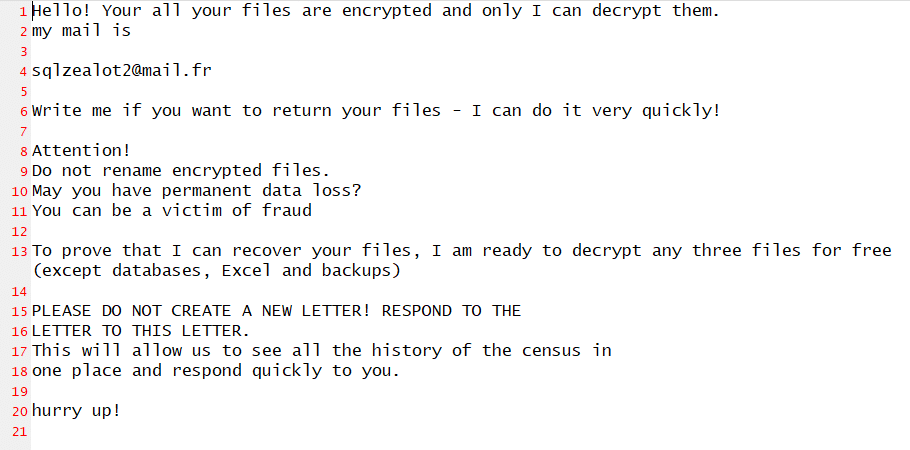
How Do Snatch Threat Actors Contact Victims Post-Exfiltration?
Snatch threat actors use email and Tox chat for communication. However, some victims have reported contact via spoofed calls since 2021, leading them to Snatch’s extortion site. Interestingly, some victims receive ransom notes from Snatch even when affected by other ransomware, resulting in data postings on both the respective ransomware blogs and Snatch ransomware’s extortion blog.
The advisory lists some of the mailing domains used by Snatch threat actors; while these email addresses are random, they typically originate from one of the following domains:
- sezname[.]cz
- cock[.]li
- airmail[.]cc
- tutanota[.]com / tutamail[.]com / tuta[.]io
- mail[.]fr
- keemail[.]me
- protonmail[.]com / proton[.]me
- swisscows[.]email
The domains, with the exception of the first three, are legitimate email domains that provide encrypted email services.
Recent Attacks by Snatch Ransomware
Department of Defence South Africa (DARPA):
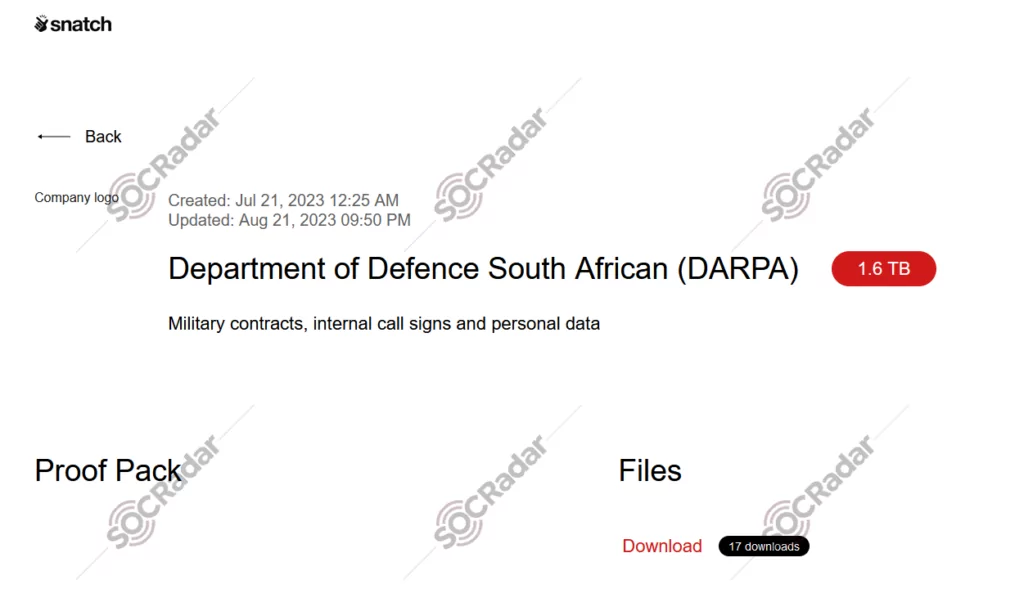
On August 21, 2023, the Snatch ransomware leaked data of the South African Department of Defence (DARPA) on their extortion site. The leaked data totaled at 1.6TB, and allegedly contained military contracts, internal call signs, and personal information.
Telcoset.com.tr:
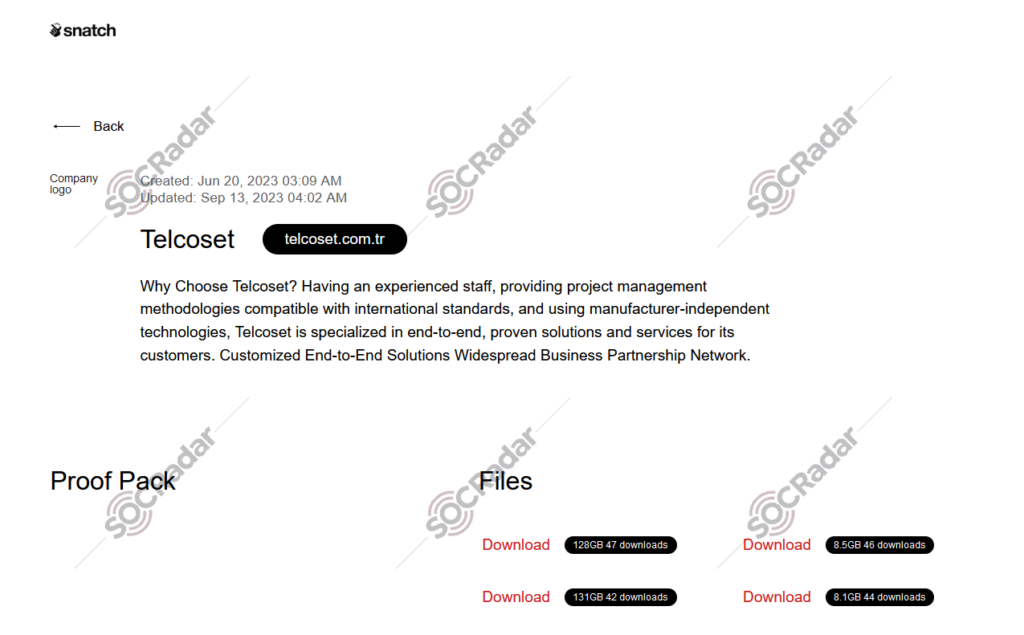
On September 13, 2023, the Snatch ransomware gang leaked the data of a technology company in Turkey, named Telcoset.
ZILLI, Florida Department of Veterans’ Affairs, and CEFCO:

On September 19, 2023, the data of three new victims were leaked by the gang. The victims are Zilli.com, a clothing company based in France, Florida Department of Veterans’ Affairs, and CEFCO, a US-based fuel company.
Recommendations
Against the Snatch variant, as for other ransomware infections, it is always advisable to maintain offline backups of your data. Having backups in place helps prevent disruptions to your organization’s workflow and the loss of critical data.
Additionally, it is recommended to enable and enforce phishing-resistant multifactor authentication (MFA) measures while monitoring Remote Desktop Protocol (RDP) usage. You can achieve this by conducting network audits to identify systems using RDP, closing unused RDP ports, logging RDP login attempts, and implementing account lockouts after a certain number of attempts.

Further details, recommendations, and an extensive list of the Indicators of Compromise (IoCs), and the MITRE ATT&CK TTPs are available on the official advisory on CISA.
Stay Ahead of Cyber Threats with SOCRadar
SOCRadar takes a proactive approach by constantly monitoring threat actors and malware, providing you with real-time intelligence to strengthen your organization’s defenses. On the platform, you can search for specific threat actors and access comprehensive details such as their targeted vulnerabilities, affiliations with other actors, and indicators of compromise. This empowers you to effectively stay ahead of malicious actors who seek to exploit vulnerabilities within your organization.