
Joint Advisory Warns of Truebot Malware Variants Infecting US and Canadian Networks
Today, a joint Cybersecurity Advisory (CSA) was released by several organizations, including the Cybersecurity and Infrastructure Security Agency (CISA), Federal Bureau of Investigations (FBI), the Multi-State Information Sharing and Analysis Center (MS-ISAC), and the Canadian Centre for Cyber Security (CCCS).
The advisory sheds light on the emergence of newly identified Truebot malware variants that are targeting networks in the United States and Canada.
The joint advisory confirms that cyber threat actors have been leveraging Truebot malware variants to infiltrate organizations’ networks. These variants, also known as Silence.Downloader, have gained attention due to their usage by malicious cyber groups such as the CL0P Ransomware Gang.
The malware is primarily spread through phishing campaigns, where recipients are tricked into clicking malicious hyperlinks that execute the malware. The attackers have also been observed using software update notifications disguised as email attachments to deliver Truebot malware. The phishing approach aims to deceive users into interacting with the attachments, leading to a redirection to a malicious web domain where the malware is deployed.

What makes the Truebot malware particularly concerning is the newer versions that allow cyber threat actors to gain initial access by exploiting a known vulnerability.
Specifically, the attackers have been taking advantage of a remote code execution vulnerability (CVE-2022-31199) in the Netwrix Auditor application.
By exploiting this vulnerability, the attackers can execute the malware at scale within compromised environments. This demonstrates the need for organizations to promptly patch vulnerable systems and applications to reduce the risk of exploitation.
Previous Research on Truebot’s Origin
Cisco’s December 2022 research revealed a surge in Truebot malware infections. Truebot, identified in 2017, is linked to the Silence Group, hence its alternative name Silence.Downloader.
The researchers believe the Silence Group is associated with the prominent threat actor Evil Corp (TA505), given that one of the subsequent payloads deployed by Truebot is the Grace malware (aka FlawedGrace, GraceWire), which is attributed to Evil Corp.
During the second half of 2022, the Truebot attacks targeted the remote code execution vulnerability in the Netwrix auditor, followed by an upsurge of attacks using Raspberry Robin. Researchers state that the threat actors behind these Truebot infections were able to create a botnet of more than 1,000 systems worldwide, primarily through Raspberry Robin attacks, and have started employing new distribution methods as of November 2022.
Truebot Malware Post-Compromise Activity
After gaining access, the attackers engaged in post-compromise activities such as data theft and the deployment of Clop ransomware. During the investigation of one such attack, researchers uncovered a sophisticated custom data exfiltration tool, named Teleport.
Once the systems are compromised by Truebot, the attackers proceed to evaluate potentially interesting systems for further analysis and deploy additional malware to facilitate this process.
According to Cisco researchers, a typical post-infection scenario involving Truebot malware follows these steps:
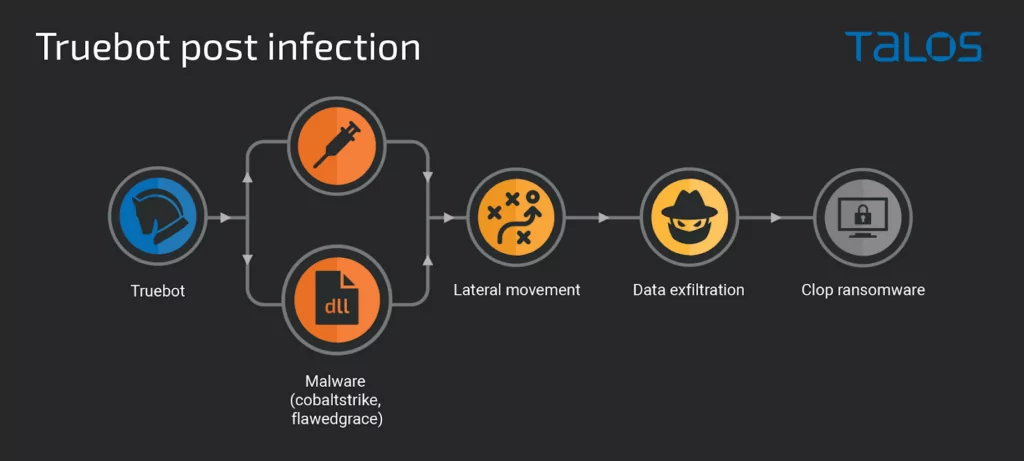
The research highlights two distinct Truebot botnets. The first botnet is widely distributed, with a specific focus on Mexico, Pakistan, and Brazil, while the second, more recent botnet appears to target the United States.
Truebot Mitigations and Reporting
To mitigate the impact of Truebot malware and other related ransomware incidents, it is crucial for organizations to implement the recommended mitigations outlined in the joint advisory. This includes applying patches for CVE-2022-31199 to address the vulnerability exploited by the malware.
Additionally, organizations are encouraged to report any incidents and anomalous activities to the appropriate authorities, such as CISA, the FBI, or the MS-ISAC, depending on the nature of the incident.
For more comprehensive technical details, indicators of compromise (IOCs), and in-depth information on Truebot malware variants, refer to the official joint advisory.
The advisory provides valuable insights and actionable recommendations to enhance cybersecurity defenses and protect against this evolving threat.
The emergence of Truebot malware variants targeting organizations in the United States and Canada shows the ongoing challenges posed by cyber threats.
By staying informed, implementing recommended mitigations, and promptly addressing vulnerabilities, organizations can bolster their cybersecurity posture and reduce the risk of falling victim to Truebot and other similar malware.
It is crucial to continuously monitor for updates from trusted sources, collaborate with relevant authorities, and follow best practices to ensure a robust defense against evolving cyber threats.
Enhancing Vulnerability Management with SOCRadar’s Vulnerability Intelligence Module
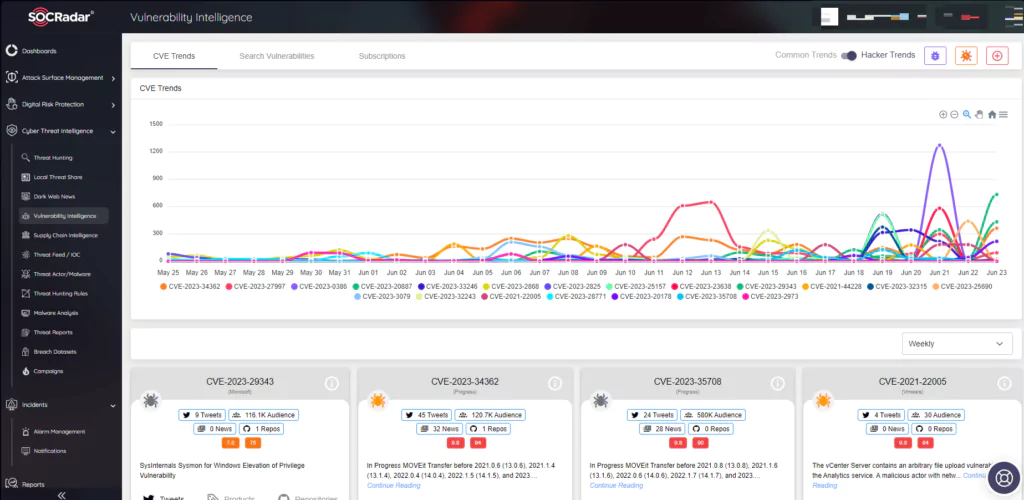
SOCRadar’s Vulnerability Intelligence Module is a valuable tool to combat the risks posed by vulnerabilities like CVE-2022-3199. It aids in monitoring and identifying emerging vulnerabilities that threat actors may exploit to compromise your business.
By leveraging this module, you receive timely alerts whenever critical vulnerabilities or exploits are discovered for the specific product components and technologies associated with your digital footprint.
This allows you to stay informed about the vulnerabilities being targeted by threat actors and gain actionable insights and contextual information to facilitate faster assessment and verification processes. By using SOCRadar’s Vulnerability Intelligence Module, you can enhance your defense against potential attacks and safeguard your business.




































