
Julian Assange Released, But the Leak and Extortion Era Began Long Ago
WikiLeaks founder Julian Assange has been freed in the UK after serving over five years in Belmarsh prison for what the U.S. government described as the “largest compromises of classified information” in its history.
In 2019, U.S. authorities charged Assange with 18 criminal counts for conspiring with former US Army intelligence analyst Chelsea Manning to obtain and publish classified information. He has been in a British prison for the last five years, fighting extradition to the US.
Assange agreed to plead guilty to one charge, and in return, U.S. authorities agreed not to demand his extradition. Assange, who spent several years hiding in the Ecuadorian embassy before being transferred to a London prison, was accused of orchestrating one of the most significant leaks of classified documents in American history.
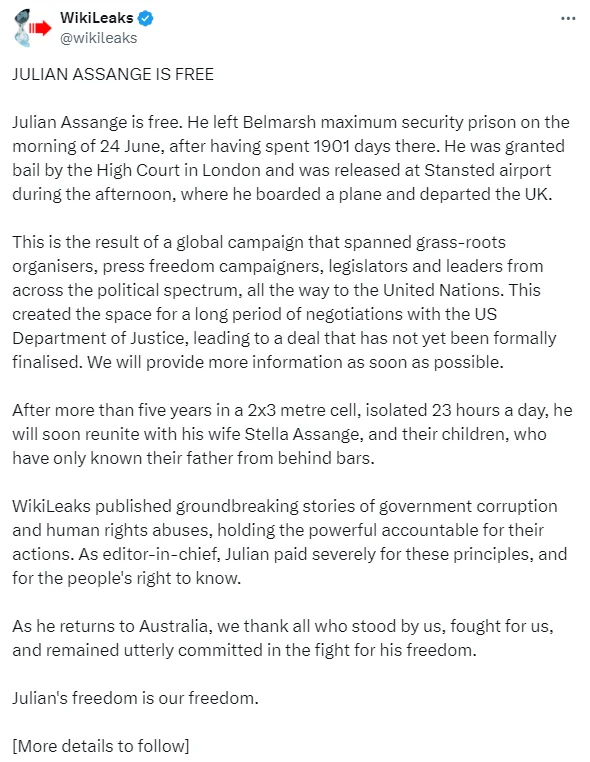
WikiLeaks post on X
“After more than five years in a 2×3 metre cell, isolated 23 hours a day, he will soon reunite with his wife Stella Assange, and their children, who have only known their father from behind bars.” WikiLeaks on X wrote.
So, what kind of mark has Julian Assange left on the cyber world and cybersecurity? And what’s the story with extortion in this context? Let’s explore these questions further.
The Impact of Julian Assange and WikiLeaks on the Cyber World
Julian Assange, the controversial founder of WikiLeaks, has profoundly influenced the intersection of cybersecurity, politics, and journalism. We could even speculate that Assange will remain pivotal in discussions about transparency, data security, and cyber threats. However, before diving deeper, let’s take a retrospective view.
The Genesis and Mission of WikiLeaks
Founded in 2006, WikiLeaks quickly gained notoriety for publishing confidential documents that exposed corruption, government malfeasance, and human rights abuses. Significant early leaks included files on Kenyan corruption, Tibetan unrest, and drone strikes in Yemen. However, the site’s most impactful disclosures came in 2010 and 2011, when Assange orchestrated the release of thousands of classified military documents provided by former US Army intelligence analyst Chelsea Manning. These revelations, detailing civilian casualties in Afghanistan and Iraq, prompted widespread debate about the ethics and implications of whistleblowing in the digital age.
The Legal Saga and Extradition Battles
Assange’s legal troubles began in earnest when he sought refuge in the Ecuadorian embassy in London in 2012 to avoid extradition to Sweden over sexual assault allegations and to the US for the WikiLeaks disclosures. His asylum ended dramatically in April 2019, leading to his imprisonment in the UK and an ongoing battle against extradition to the US, where he faces 18 criminal counts, including hacking into military databases.
The Cybersecurity Landscape Post-WikiLeaks
As stated in an article, The 2017 release of Vault 7 documents detailing CIA hacking capabilities may have underscored the vulnerabilities in global cybersecurity frameworks. Although not immediately disruptive as other leaks, Vault 7 could have provided a blueprint for state and non-state actors to enhance their cyber warfare techniques.
One of the key lessons from the WikiLeaks saga is the significant threat posed by insiders. Chelsea Manning’s role in the original leaks demonstrated how insiders with access to sensitive information could inflict substantial damage. This has led to increased awareness and measures within organizations to mitigate insider threats, although challenges remain.
Furthermore, Hacktivist attacks, often in support of WikiLeaks, have also become a critical concern. Notable incidents include the 2010 Distributed Denial of Service (DDoS) attack on PayPal by WikiLeaks supporters after the company ceased processing donations to the organization. Such events underscore the evolving nature of cyber threats, where political activism and cybercrime increasingly intersect.
Till this day, despite his incarceration, Assange’s influence persisted. In 2024, an interesting group, WikiLeaksV2, emerged, mirroring the original WikiLeaks’ mission of exposing sensitive information. This group, created in the lead-up to Assange’s latest extradition appeal, has already begun publishing data allegedly sourced from ransomware groups, signaling a new phase in the cyber war over transparency and information control.
WikiLeaksV2: A More Aggressive Approach
In the days leading up to Assange’s extradition appeal at the UK’s Royal Courts of Justice, a minor group, WikiLeaksV2 was established, expressing solidarity with Assange and his mission. This new platform aims to continue the work of exposing critical information, claiming to possess significant data and encouraging whistleblowers to submit information. Unlike the original, WikiLeaksV2 includes a focus on healthcare data, reflecting evolving concerns in data security and public interest.

WikiLeaksV2’s recent post about alleged data breach of Synnovis
Sharing samples from the data leaked by Qilin Ransomware, the group comments harshly on the UK and healthcare managers and concludes their post as follows:
“In summary, having analyzed this archive, we consider the hacker attack on Pathology services provider Synnovis to be rather a boon for the healthcare system in London and the whole UK. We encourage journalists and law enforcement agencies to take the opportunity to explore the dark side of Synnovis and draw their own conclusions.”
They also share samples from the leaked data. For detailed information on Qilin and the Synnovis incident, check out our blog post on Qilin.
So, while the main goal of this group is activism, WikiLeaksV2 also serves as a platform for amplifying the threat actor’s voice and as a means to distribute data, potentially benefiting a threat actor motivated by financial gain.
Age of Extortion
When examining the current landscape of “Ransomware,” it’s evident that the threat persists. Security forces have inflicted great damage on ransomware giants with successful operations, and over the past year, huge ransomware operations such as LockBit, ALPHV, and previously Hive have suffered major blows.
However, despite LockBit’s significant setback, numerous large and small groups persist in utilizing LockBit’s leaked builder to launch attacks. Conversely, emerging threat groups adopt a different approach by not necessarily encrypting data with ransomware; instead, they threaten organizations by exposing sensitive data.
While recent years might have been characterized as the “Age of Ransomware,” it’s increasingly clear that we’ve transitioned into the “Age of Extortion.” While some perpetrators justify their actions based on their beliefs, others are straightforward about their financial motives.
The case of the financially motivated Qilin Ransomware group is particularly intriguing, given their assertion that their recent attack was politically motivated against Synnovis. This ambiguity in motives highlights the ongoing threat posed by the potential leakage of millions of sensitive data, driven by a variety of reasons.
Therefore, it could be said that Julian Assange and WikiLeaks stand as pivotal figures in the cyber realm. Their actions have undeniably shaped the proliferation of the extortion trend, as seen in the case of WikiLeaksV2, with some groups supporting Assange ideas by offering support to ransomware groups or promoting them.
In the end, one thing is clear, data is an extremely valuable resource and threat actors also know this very well.
The Future of Cybersecurity and Data Protection
While some experts argue that WikiLeaks’ impact on cybersecurity has been overstated, the organization has undeniably spurred significant changes in how governments and corporations handle sensitive information. Efforts to improve whistleblower protections and enhance cybersecurity measures are direct responses to the vulnerabilities exposed by WikiLeaks.
Looking ahead, the continued relevance of WikiLeaks, or entities like WikiLeaksV2, hinges on the delicate balance between transparency and security. As Assange’s legal battle seems to be concluded, the cybersecurity world watched closely, knowing that the outcomes could influence the future of data security, government accountability, and the right to information in the digital age.
In conclusion, Julian Assange and WikiLeaks have left an indelible mark on the cyber world. Their legacy is a complex tapestry of advocacy for transparency, unintended consequences for cybersecurity, and an ongoing dialogue about the role of whistleblowers in a connected world. As new threats and challenges emerge, the lessons from WikiLeaks will remain crucial in navigating the intersection of technology, security, and human rights.
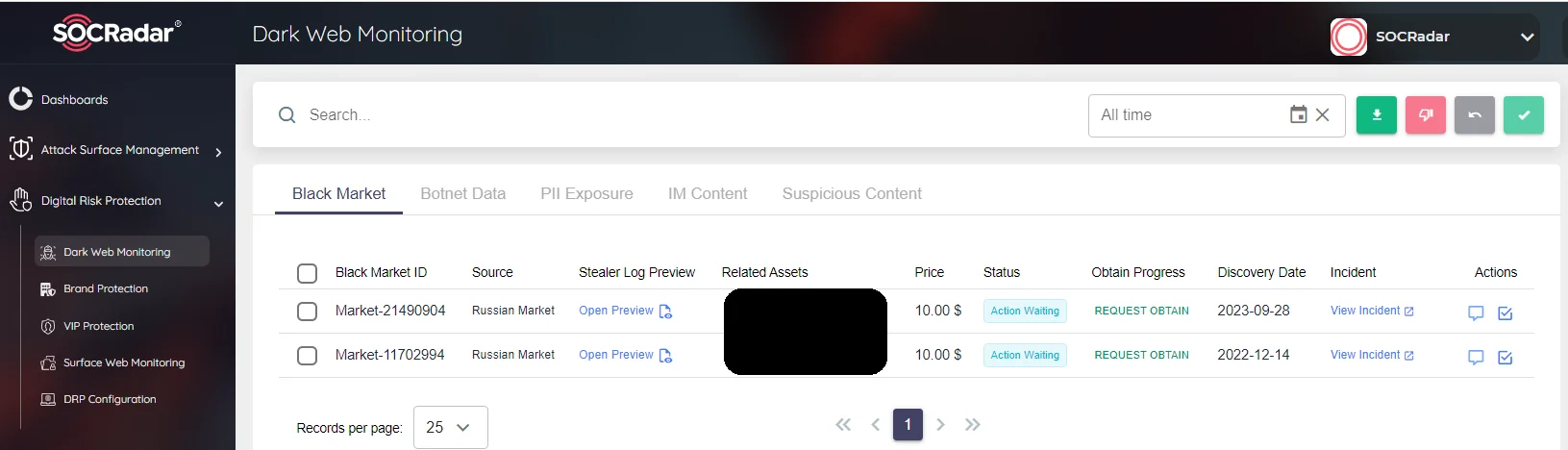
Credentials & Data Leak Detection by SOCRadar
SOCRadar may be your guide in these dark corridors. SOCRadar leverages an expanding dataset, utilizing advanced analytics algorithms and a skilled team of analysts to assist organizations in identifying potential compromises such as employee email addresses, credit card information, or customer login details. For example, given the frequent trading of credit card information on the Internet, particularly in the dark web, SOCRadar’s Credit Card Leakage monitoring module and real-time alerts empower proactive measures against fraud.
SOCRadar, Dark Web Monitoring




































