
Latest Dark Web Leaks: Disney Slack, U.S. Credit Cards, 1TX Vendor Database
The SOCRadar Dark Web Team has identified several significant data breaches and cyber threats involving prominent organizations and large-scale databases. Notable incidents include the alleged leak of Disney’s internal Slack data, a massive database of the Romanian population, and the sale of 1,000 U.S. credit cards.
Receive a Free Dark Web Report for Your Organization:
Alleged Internal Slack Data of Disney is Leaked
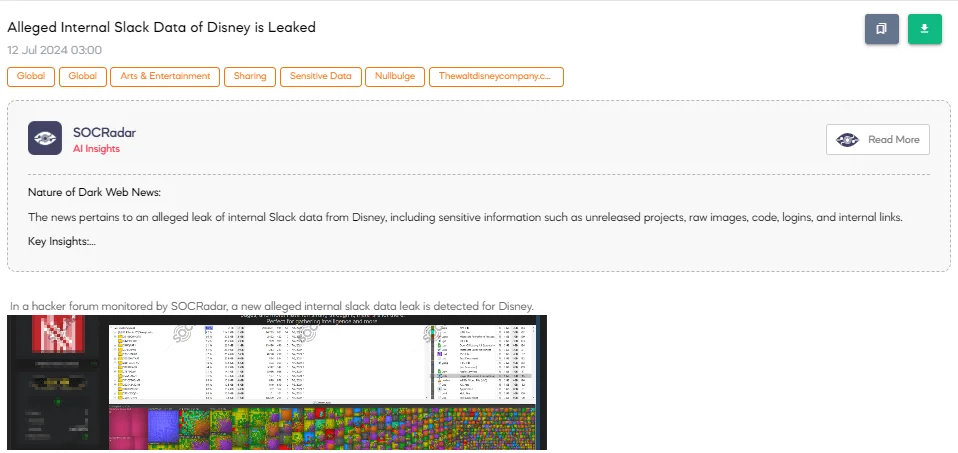
The SOCRadar Dark Web Team detected a post in a hacker forum that a threat actor claims to have leaked internal Slack data of Disney. The alleged leak includes 1.1TiB of data from almost 10,000 channels, encompassing every message and file possible. This data purportedly contains unreleased projects, raw images and code, some logins, links to internal APIs and web pages, and more. The threat actor described the leak as a rich source for gathering intelligence.
Alleged Database of Romanian Population is on Sale
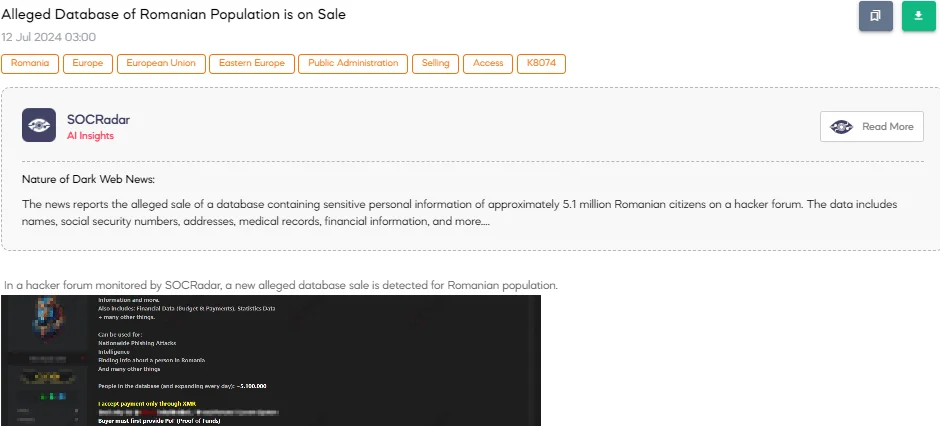
The SOCRadar Dark Web Team detected a post in a hacker forum that a threat actor claims to have a new alleged database of the Romanian population for sale.
The database allegedly includes sensitive information such as full names, SSNs (PIN/CNP), dates of birth, physical addresses, email addresses, phone numbers, ID data, workplace history, medical information, relatives’ information, financial data, and more. The threat actor suggests that this data can be used for nationwide phishing attacks, intelligence gathering, and finding information about individuals in Romania.
The database allegedly contains information on approximately 5.1 million individuals and is expanding daily. The threat actor accepts payment only through XMR, with a minimum purchase of $100 for smaller batches of data, while the starting bid for the entire database is $15,000.
1000 Credit Cards Belonging to the United States are Allegedly on Sale
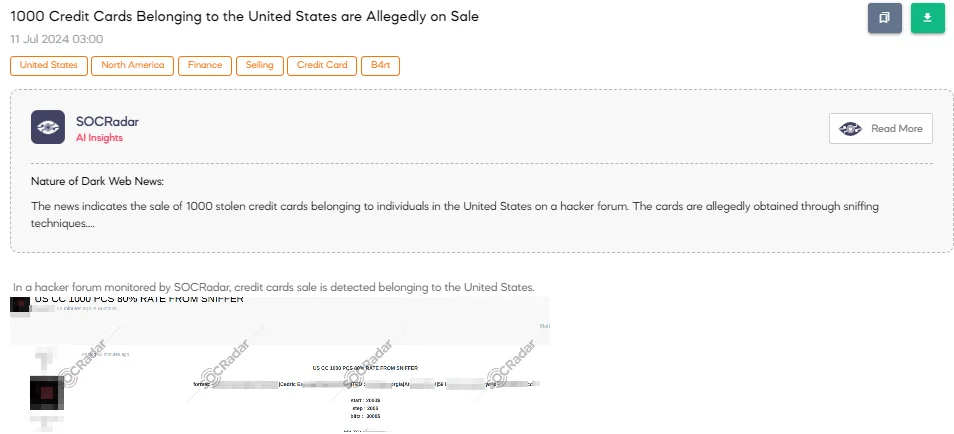
The SOCRadar Dark Web Team detected a post in a hacker forum that a threat actor is allegedly selling 1,000 credit cards belonging to individuals in the United States. The threat actor claims that the cards were obtained through a sniffer, with an 80% validity rate. The data format includes credit card number, expiration date, name, CVV, address, and email.
The Alleged New MacOS Stealer is on Sale
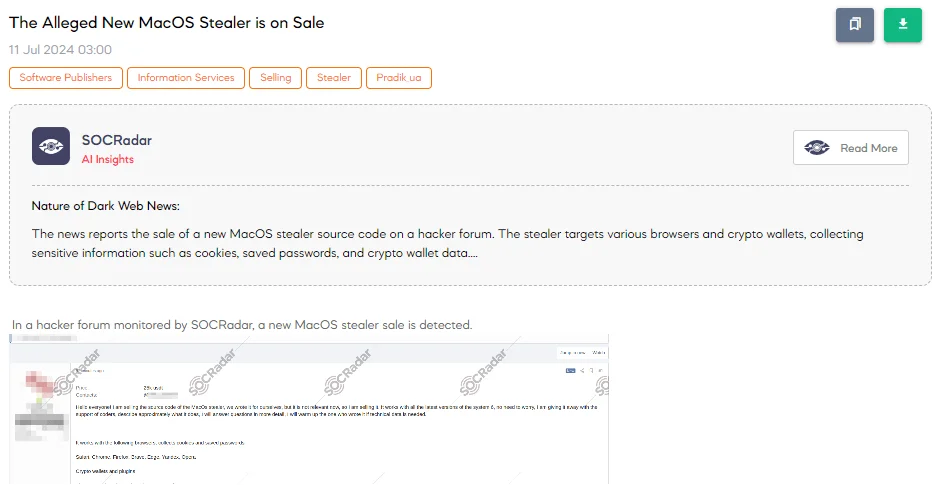
The SOCRadar Dark Web Team detected a post in a hacker forum that a new MacOS stealer is up for sale. The threat actor claims to be selling the source code of this MacOS stealer for 25,000 USDT, along with coder support. USDT stands for Tether, a type of cryptocurrency that is pegged to the US dollar.
The stealer allegedly works with all the latest versions of MacOS and targets multiple browsers including Safari, Chrome, Firefox, Brave, Edge, Yandex, and Opera. It is designed to collect cookies and saved passwords. Additionally, it can target crypto wallets and plugins such as Electrum, Coinomi, Exodus, Binance, and Atomic. The threat actor also mentioned that log management is available via a Telegram panel.
Alleged New 0-Day Exploit for Mozilla is on Sale
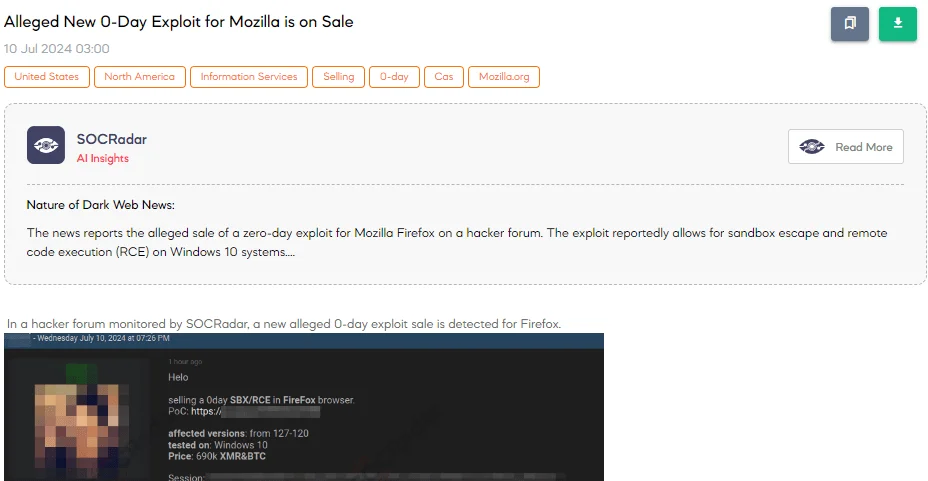
The SOCRadar Dark Web Team detected a post in a hacker forum that a new alleged 0-day exploit for Firefox is on sale. The threat actor claims to be selling a 0-day Sandbox Escape (SBX) and Remote Code Execution (RCE) exploit in the Firefox browser. According to the post, the exploit affects versions from 127 to 120 and has been tested on Windows 10. The asking price is 690k Monero (XMR) and Bitcoin (BTC).
Alleged Leak of 1TX’s Vendor Database
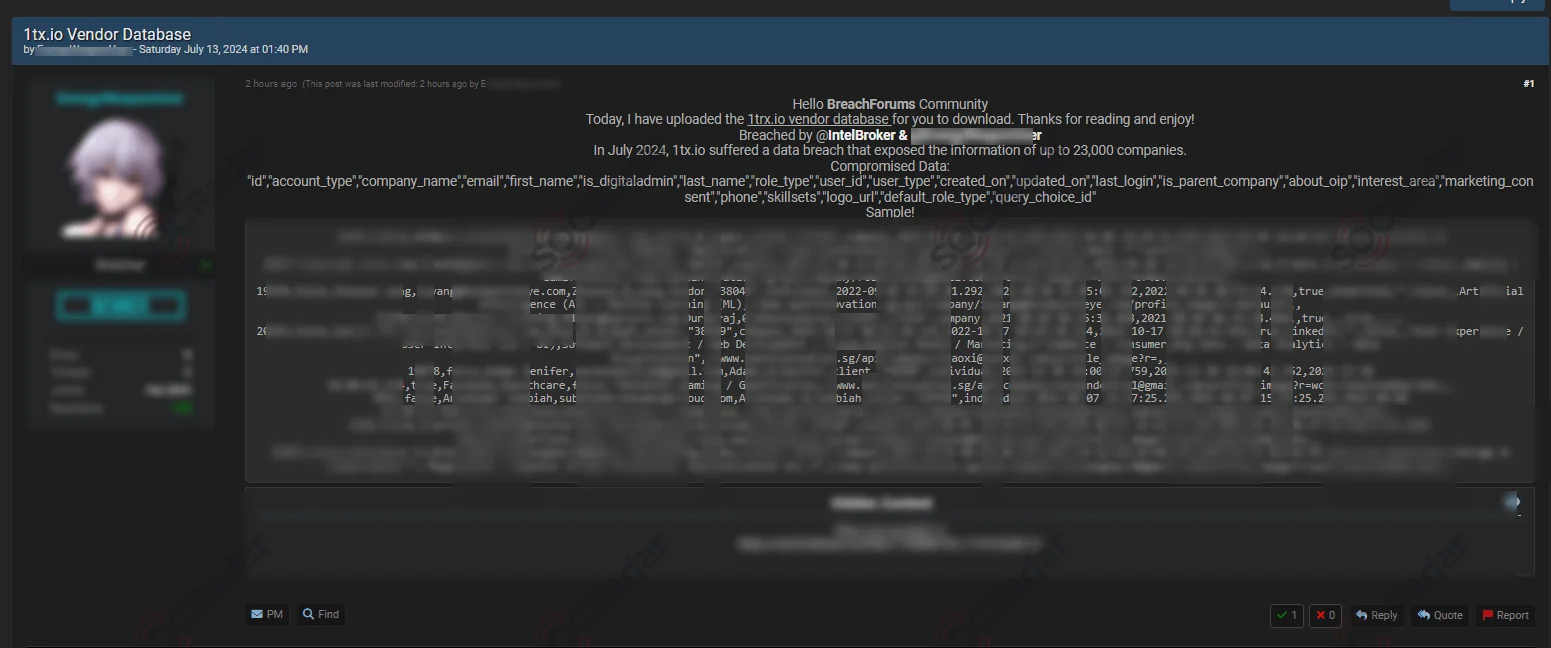
The SOCRadar Dark Web Team detected a post in a hacker forum that a threat actor, IntelBroker, in collaboration with another threat actor, has purportedly leaked 1TX’s vendor database. The leak allegedly exposes sensitive information from approximately 23,000 companies. The compromised data includes company names, email addresses, first and last names, digital admin details, phone numbers, roles, and other critical information.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































