
LockBit Hacked: 60,000 Bitcoin Addresses Leaked
The LockBit ransomware group, one of the most well-known cybercrime gangs, has been hacked. The attackers defaced LockBit’s Dark Web panel and leaked nearly 60,000 Bitcoin addresses, along with a database full of internal data.
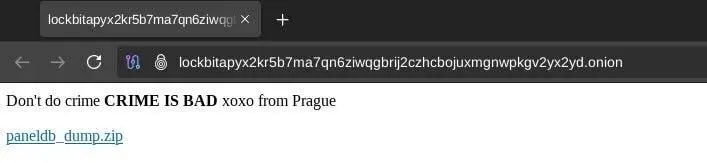
The hacked site displayed a message that read: “Don’t do crime. CRIME IS BAD xoxo from Prague.”
It also included a link to download a file called paneldb_dump.zip, which turned out to be a MySQL database dump of LockBit’s backend system.
With SOCRadar’s Threat Hunting feature, users can search and access this content, available in the SOCRadar Free Edition
What is Inside The LockBit Panel Leak?
Although nearly 60,000 Bitcoin addresses were leaked, a LockBit representative claimed that no private keys or sensitive data were compromised.
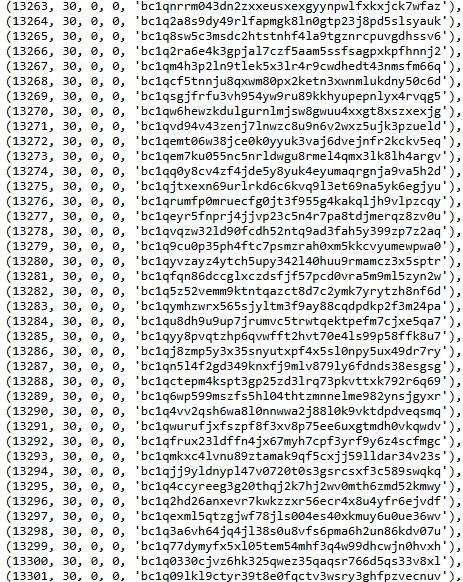
A sample from Bitcoin addresses
During a Tox chat with Rey, the LockBit operator ‘LockBitSupp’ acknowledged the breach and said that no private keys or data had been compromised:
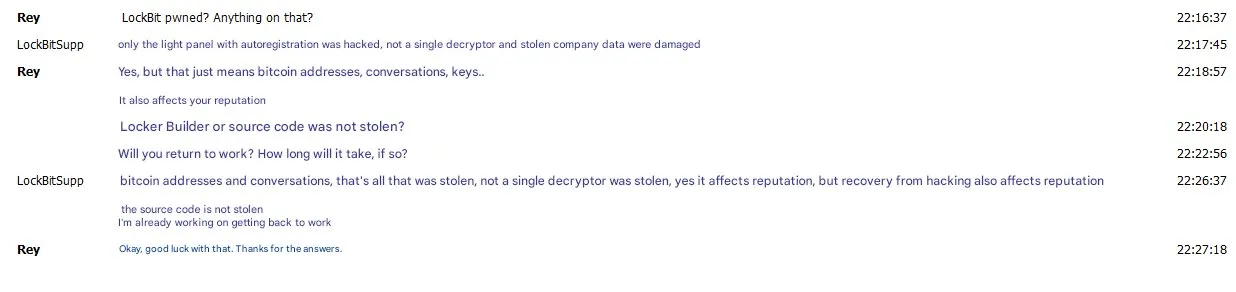
A post on X by ReyXBF shows a conversation with LockBitSupp.
According to an initial analysis from BleepingComputer, the leaked database had 20 tables:
- A table with 59,975 unique Bitcoin addresses used for ransom payments.
- A “builds” table showing custom ransomware builds, some listing the names of companies targeted.
- A “chats” table with 4,442 negotiation messages between victims and LockBit, from December 2024 to April 2025.
- A user table with 75 affiliates and admins, including usernames and plaintext passwords like “Weekendlover69” and “MovingBricks69420”.
Importantly, no private Bitcoin keys were leaked so the addresses can be studied but not accessed.
What is Inside The LockBit Chat Logs
As part of the breach, over 4,000 timestamped chat messages between LockBit operators and victims were leaked. These logs cover a period from December 2024 to April 2025, revealing how the group handled negotiations over time. The conversations took place via LockBit’s affiliate panel and included direct discussions on pricing, file recovery, and payment methods.
Key Takeaways from the Chat Logs
- Ransom Demands Vary Widely: Prices ranged from a few thousand dollars to over $150,000, often based on the victim’s perceived ability to pay.
- Bitcoin Wallets and Payments: Several Bitcoin addresses and confirmed transactions were included, helping trace funds.
- Negotiation Was Common: Victims regularly pleaded for lower payments, with some receiving discounts or installment options.
- Technical Support Promised: LockBit provided decryptors and instructions, especially for Windows and ESXi systems.
- Victim Desperation: Many messages showed victims in distress, fearing job loss or begging for leniency.
- Scripted Responses: Repeated, copy-pasted instructions suggest LockBit used automated or templated replies for efficiency.
How Did It Happen?
It’s not clear who carried out the attack, but there’s some evidence the breach might be connected to a similar hack on the Everest Ransomware. In both cases, the same message was used to deface the sites.
One possible way in was a known vulnerability in PHP 8.1.2 (CVE-2024-4577), which LockBit’s server was running. This flaw allows hackers to run code on the server remotely, making it a likely point of entry.
Why It Matters
This breach gives law enforcement and blockchain analysts new clues to track how LockBit moved ransom money. Each Bitcoin address can now be analyzed on the blockchain, potentially linking payments to real-world identities.
The hack also comes not long after Operation Cronos in 2024, when international authorities took down parts of LockBit’s infrastructure, including servers and 1,000 decryption keys. LockBit came back online afterward, but this latest hit damages their already shaky reputation.
In Conclusion
Whether this is the end of LockBit isn’t clear(it’s not), but it’s definitely a serious blow to LockBit’s reputation and their operation. It also shows that even ransomware gangs aren’t immune to sloppy security like using outdated software or storing passwords in plain text. A similar case to BreachForums’ recent fate.
SOCRadar’s Advanced Dark Web Monitoring, Dark Web Search Engine
Either way, the researchers who’ve been tracking LockBit now have more data to work with. SOCRadar notifies the relevant users referenced in the logs with the necessary alerts.


































