LockBit’s New Regulations Sets Minimum For Ransom Demands
Recently, the notorious LockBit ransomware group has initiated a significant discussion among its affiliates regarding potential changes to their ransom payment policies. The group has expressed growing frustration with ransomware negotiators and their handling of payment demands. Currently, LockBit affiliates have carte blanche in determining the ransom amounts for targeted companies, leading to a lack of consistency in their demands. To address this issue, Lockbit is contemplating the introduction of new regulations on ransom demands.
The Dilemma
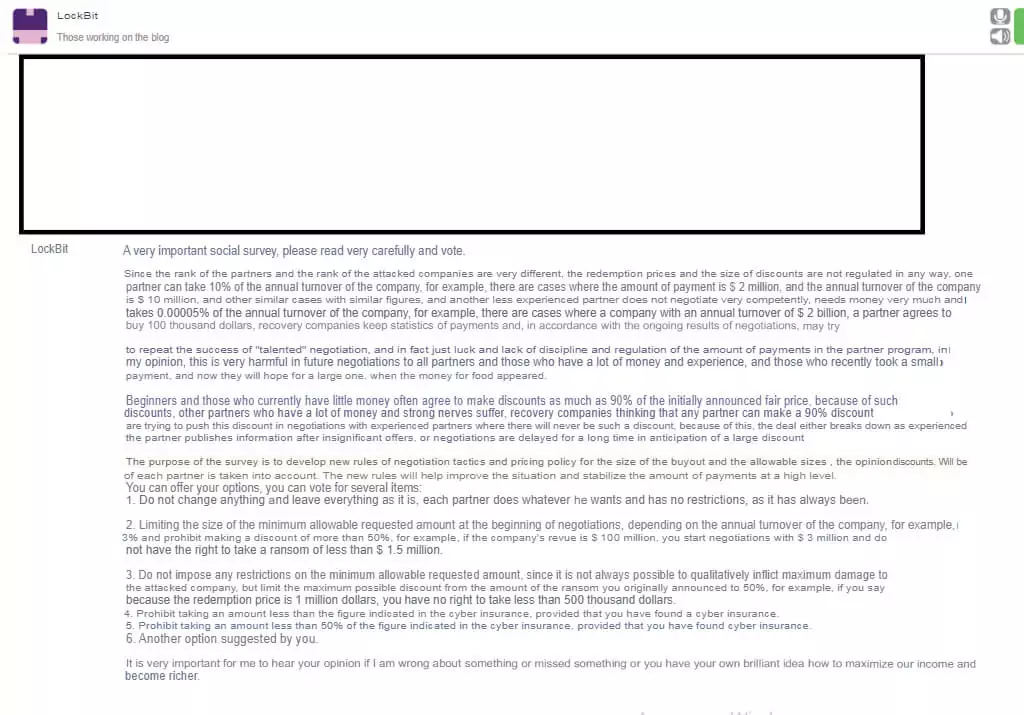
LockBit ransomware group faces a dilemma as they observe varying approaches among their affiliates. On the one hand, newer affiliates offer substantial discounts to victimized companies out of desperation to secure quick payments. On the other hand, more seasoned affiliates maintain a steadfast stance and do not readily acquiesce to negotiators’ proposed payment terms. This disparity in approach has prompted LockBit to consider implementing rules to standardize ransom demands.
The administrative team of LockBit has presented several options for regulating ransom payments. These options are as follows:
- Maintain the Status Quo: LockBit could choose to maintain its current policy of not imposing any specific rules on ransom payment amounts. This approach would leave payment decisions entirely to the discretion of individual affiliates.
- Set a Minimum Payment: LockBit is deliberating on introducing rules that would mandate a minimum payment equivalent to 3% of the victim company’s annual revenue. Affiliates would have the option to offer a 50% discount, reducing the payment to 1.5% of the annual revenue.
- Cap Discount Percentage: Another proposal is to restrict affiliates from granting a discount greater than 50% of the originally demanded ransom amount.
- Ransom Insurance Policy: LockBit could require that the ransom payment not fall below the victim’s maximum ransomware insurance policy as a minimum threshold.
- Minimum Payment Based on Insurance: Alternatively, LockBit could establish a rule requiring a minimum payment of 50% of the victim’s ransomware insurance policy.
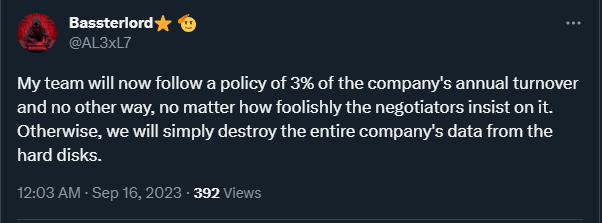
National Hazard Agency’s Stance
In response to this internal debate, the National Hazard Agency, a subdivision of the LockBit ransomware group, has taken a decisive stance. They have announced that they will no longer entertain ransom offers below 3% of the targeted company’s annual revenue. Any negotiator who approaches them with a payment offer below this threshold will face immediate retaliation, resulting in the complete destruction of the victim company’s data.
Internal Struggles and the Future Possibilities
LockBit, which dominated the ransomware landscape throughout the past year, experienced a temporary setback, yielding its leadership position to Cl0p for a month. Moreover, LockBit faced challenges regarding their ability to substantiate their claims regarding data leaks, though they countered these allegations by simultaneously releasing numerous data breaches.
Once again, LockBit found itself in the spotlight due to internal changes, a recurring issue inherent to its Ransomware-as-a-Service (RaaS) model. While democratic decisions may be made, some affiliates could harbor discomfort, potentially leading to operational disruptions. Conversely, the introduced standardization may enhance their profit margins, potentially transforming LockBit into a more formidable long-term threat in the ransomware landscape.
For a deeper understanding of LockBit’s operations, you can refer to our LockBit interview post.
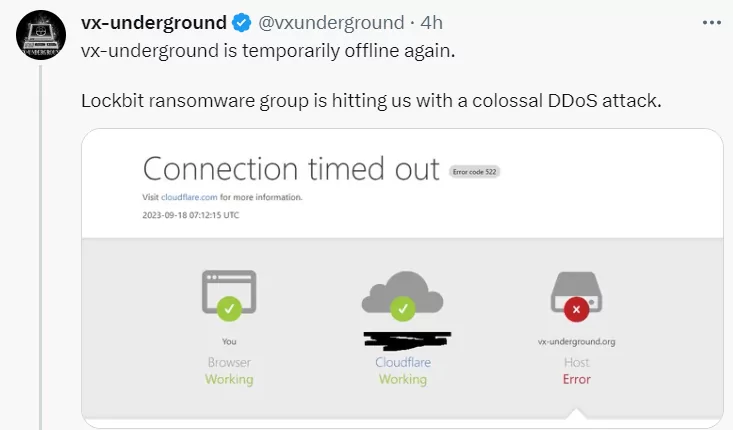
Another incident is that LockBit has a botnet and is testing it on vx-underground’s website. Even if this incident is not an immediate threat for now, it shows that LockBit has increased its capabilities, and it seems that ransomware groups have strengthened their arsenal with attack methods other than encryption and extortion.
Conclusion
LockBit ransomware group is at a crossroads, grappling with the need to bring uniformity to its ransom demands. The internal discussion among affiliates has led to a range of proposed options, each with its own implications for the future of the group’s operations. The stance taken by the National Hazard Agency underscores the seriousness of this debate and the potential consequences for those who fail to comply with the proposed changes. As this story unfolds, ransomware continues to evolve, posing new challenges and risks to organizations. In fact, despite these internal struggles, they continue to make many victim announcements and leaks. LockBit has disclosed 20+ fresh victims via its leak blog throughout this weekend. Furthermore, the group has opted to publicly release the compromised data, signaling their unsuccessful negotiations.
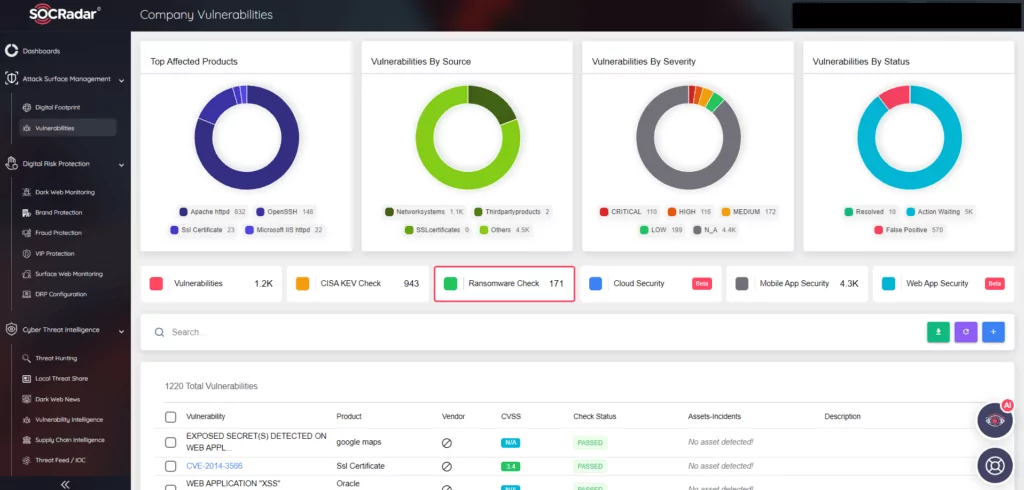
SOCRadar is dedicated to continuously surveilling threat actors, focusing on ransomware groups like LockBit. We aim to furnish our users with actionable intelligence. In this vein, we introduce the Vulnerability-Ransomware Check, a newly integrated feature within our Attack Surface Management module. This feature thoroughly scans our users’ assets, factoring in the security vulnerabilities often exploited by ransomware groups, and presents the findings.