
Major Cyber Attacks in Review: March 2025
March 2025 was marked by a wave of significant cyber incidents affecting cloud platforms, developer ecosystems, blockchain networks, and telecom providers. From a hacker claiming access to millions of Oracle Cloud records to a sophisticated supply chain attack on GitHub Actions, this month illustrated how threat actors continue to exploit both legacy vulnerabilities and emerging opportunities in CI/CD and authentication infrastructure.
This review recaps the most impactful cyber attacks observed in March 2025, outlining the methods, targets, and evolving tactics behind each breach.
Hacker Claimed Oracle Cloud Breach Exposed 6 Million Records
In March 2025, a threat actor known as “rose87168” claimed to have breached Oracle Cloud, allegedly stealing 6 million records containing encrypted SSO and LDAP credentials, Java KeyStore files, and other key authentication data. The actor began selling the data on BreachForums while attempting to extort affected organizations, reportedly impacting over 140,000 Oracle Cloud tenants worldwide.
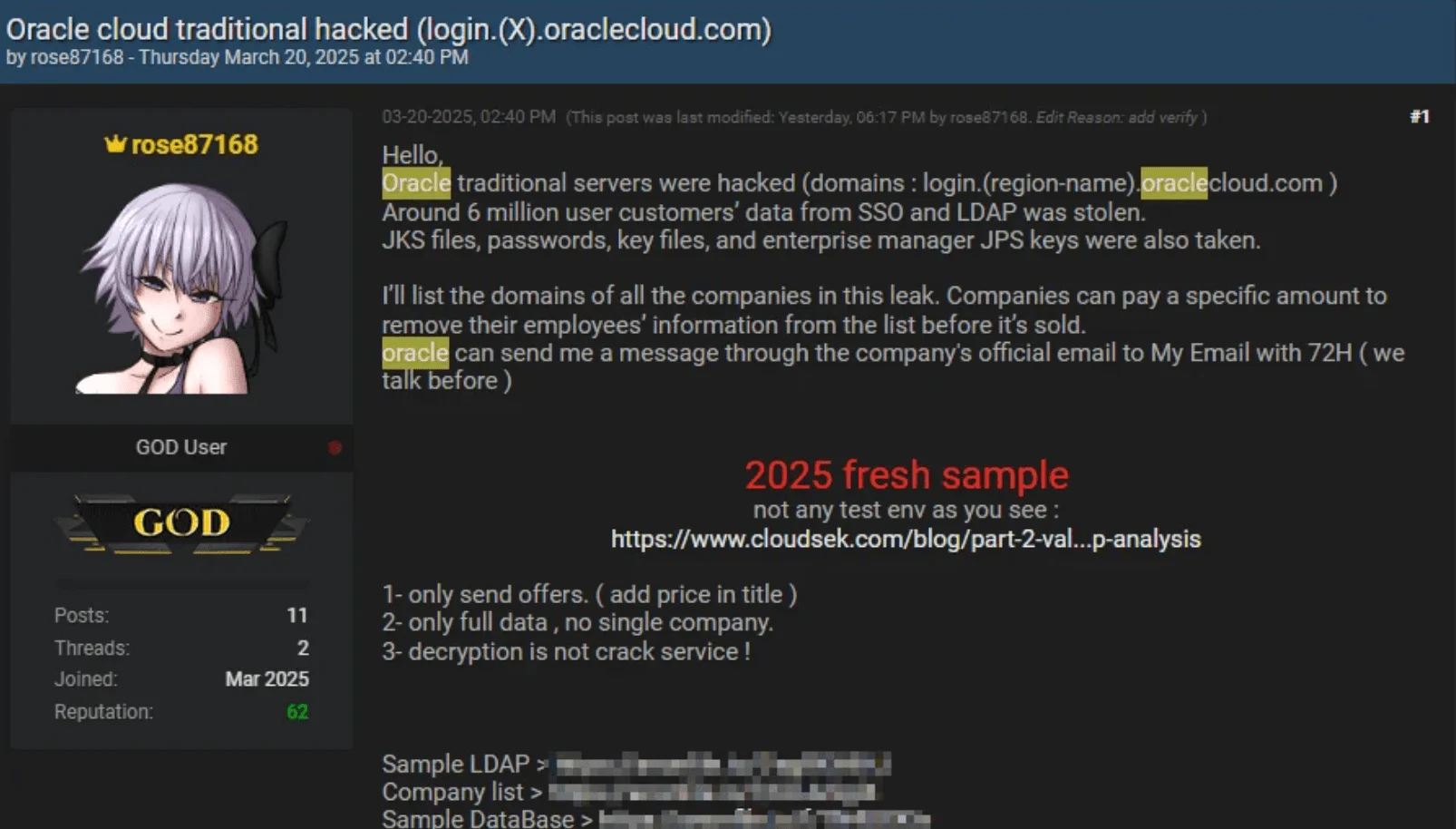
Threat actor claims a breach of Oracle
The threat actor provided samples, including files uploaded to an Oracle Cloud subdomain, archived on the Wayback Machine, as proof of access. Oracle initially denied any breach, stating that the credentials were not linked to Oracle Cloud systems. However, by early April, the company had reportedly begun notifying affected customers, while attributing the stolen data to outdated, unused systems – an explanation that drew skepticism.
The breach was believed to involve CVE-2021-35587, a known RCE vulnerability in Oracle Fusion Middleware. The hacker initially demanded $20 million in exchange for technical details but was rebuffed by Oracle. Meanwhile, Oracle faced a second breach affecting its healthcare division, further raising questions about its cloud security posture.
For a detailed breakdown of the incident, visit our full coverage at “Everything You Need to Know About Oracle Cloud Security Incident by rose87168”.
GitHub Actions Breach Exposed CI/CD Secrets in Supply Chain Attack
In March 2025, a cascading supply chain attack targeting GitHub Actions exposed CI/CD secrets from at least 218 repositories across over 4,000 organizations. The breach began with the compromise of reviewdog/action-setup@v1, which was modified to dump secrets into GitHub workflow logs. This poisoned action was later used in tj-actions/eslint-changed-files, enabling attackers to steal a Personal Access Token (PAT).
With this token, threat actors injected malicious code into tj-actions/changed-files, an action used by 23,000+ projects.
While only a fraction of those repositories ran vulnerable workflows during the attack window, high-profile names, including Coinbase, were affected. According to reports, Coinbase’s agentkit was explicitly targeted, although no damage was ultimately reported.

The breach highlighted how one compromised action can trigger downstream infections and how mutable version tags like @v1 can enable widespread abuse. Most exposed secrets were short-lived tokens, but some included high-risk credentials for services like AWS and npm. Overall, the incident underscores the growing threat of supply chain compromises within CI/CD pipelines.
WEMIX Lost $6.1M in Tokens After Authentication Key Theft
On February 28, 2025, blockchain gaming platform WEMIX was breached in a cyber attack that resulted in the theft of 8.65 million WEMIX tokens, valued at approximately $6.1 million.

The attackers reportedly gained access through stolen authentication keys tied to the platform’s NFT service, NILE, which had been exposed in a shared developer repository. After two months of planning, the threat actors executed 15 withdrawal attempts, 13 of which succeeded, and laundered the stolen funds via cryptocurrency exchanges.
WEMIX CEO Kim Seok-Hwan confirmed the breach during a March press conference, stating that disclosure was delayed to prevent further exposure and market disruption. The compromised server was immediately shut down, and a criminal complaint was filed with South Korea’s cybercrime unit the same day.
As a result of the incident, all blockchain infrastructure was taken offline for migration to a more secure environment, and a full service restoration was conducted in late March.
X Disrupted by DDoS Attack, Dark Storm Claimed Responsibility
In March 2025, social platform X suffered a large-scale DDoS attack that caused global outages. Elon Musk attributed the attack to IP addresses in Ukraine and suggested it was the work of a nation-state or large coordinated group.
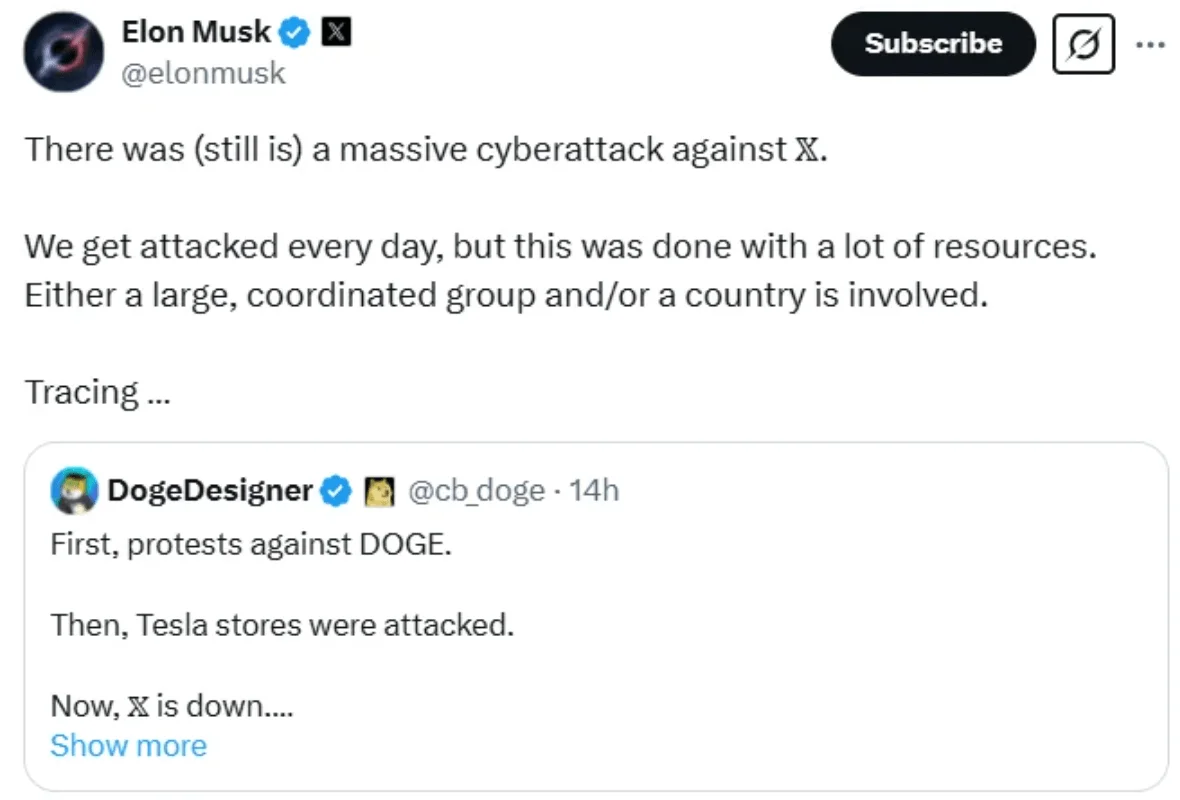
Tweet by Elon Musk, about DDoS attacks on X
However, the pro-Palestinian and pro-Russian group Dark Storm Team claimed responsibility via Telegram, posting screenshots to support their claim.
While the group has a history of targeting social media platforms, experts caution that such claims often lack verification and may serve promotional purposes. X responded by reinforcing its defenses with support from Cloudflare.
More details about this incident can be found on the SOCRadar blog: “X Faces Cyberattack – Dark Storm Team Takes Credit, Musk Blames Ukraine”.
NTT Communications Breach Exposed Data of Nearly 18,000 Corporate Clients
NTT Communications Corporation, a major Japanese telecommunications provider, confirmed in March that a cyberattack led to the unauthorized access and potential leakage of corporate customer information. The breach, initially discovered on February 5, 2025, affected nearly 18,000 corporate entities through NTT’s ‘Order Information Distribution System.’
Press release by NTT, auto-translated. Read the full version here.
The stolen data may include company names, representative names, contract numbers, email addresses, and service usage information. While NTT acted quickly to block initial access, further investigation revealed the attackers had pivoted to another internal device, prompting additional containment measures.
Although the company stated that the threat has been neutralized, it opted not to notify affected customers individually, instead relying solely on a public disclosure.
Nearly One Million Devices Targeted in Global Malvertising Campaign
Microsoft Threat Intelligence revealed that they uncovered a large-scale malvertising campaign in December 2024, which compromised nearly one million consumer and enterprise devices worldwide.
The attack, attributed to the threat cluster Storm-0408, originated from illegal streaming sites that redirected users through a multi-layered chain to GitHub-hosted payloads. These GitHub repositories hosted malware that initiated a four-stage infection chain involving infostealers like Lumma and remote access tools such as NetSupport RAT.
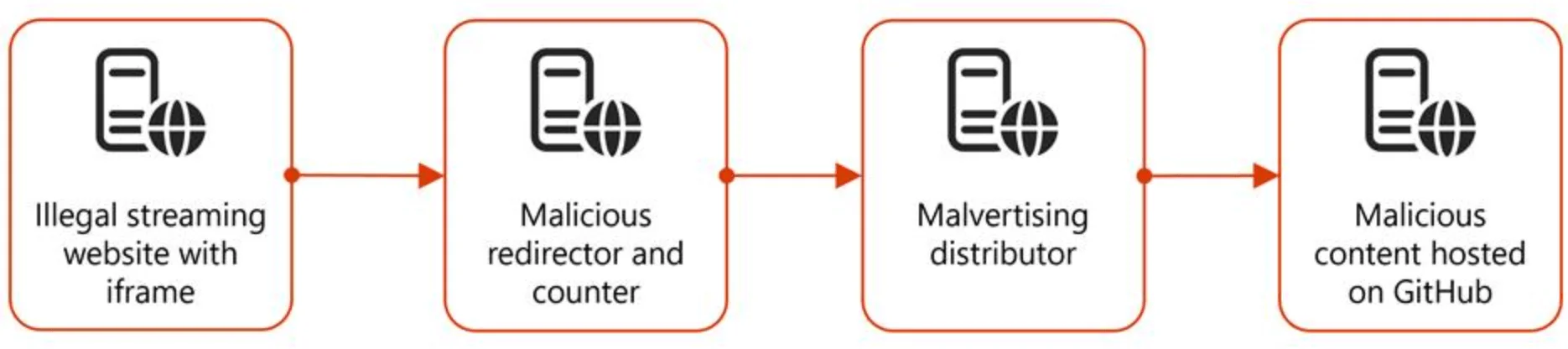
Redirection chain used in the malvertising campaign (Microsoft)
Once downloaded, the payloads performed system discovery, credential harvesting, data exfiltration, and established persistence through Windows registry keys and startup folder shortcuts. Additional payloads were delivered using PowerShell, VBScript, and AutoIT scripts, with some variants targeting cryptocurrency wallets and browser credential stores.
Although GitHub, Discord, and Dropbox were used as hosting points for various stages, GitHub played a central role in distributing the initial malware droppers. Microsoft worked with GitHub to promptly remove the malicious content.
Tata Technologies Data Leak Tied to Hunters International
In March, the ransomware group Hunters International leaked over 1.4 TB of data allegedly stolen from Tata Technologies, including 730,000+ files containing employee details, purchase orders, and contracts. The breach followed a ransomware attack confirmed by Tata in late January, which the company initially downplayed as impacting only a few internal IT assets.
Hunters International, a rebrand of the Hive ransomware gang, claimed responsibility and published the data on its leak site. The group has reportedly begun pivoting to exfiltration-only attacks, targeting global firms in industries such as aerospace, real estate, and energy. Its new strategy involves directly pressuring company executives while avoiding traditional encryption methods to evade detection.
The Tata breach highlights the ongoing risks posed by RaaS groups adapting their extortion models in response to law enforcement pressure.

Threat actor card of Hunters International
For more insights into the group’s operations, visit our Dark Web profile on Hunters International, where you will find detailed intelligence on their evolving tactics and victimology.
To reduce exposure to similar threats, organizations can rely on SOCRadar’s integrated capabilities, such as:
- Advanced Dark Web Monitoring: Tracks leak sites, breach forums, and encrypted channels in real-time.
- Cyber Threat Intelligence (CTI): Provides context-rich insights into vulnerabilities, threat actors, campaigns, and IOCs.
- Attack Surface Management (ASM): Continuously maps exposed digital assets to help security teams identify risks before attackers do.
- Proactive Alerting: Notifies you of brand mentions, stolen data, or exposed credentials.
SOCRadar’s ASM module, Digital Footprint
By combining deep visibility with actionable intelligence, SOCRadar helps organizations identify risks early and respond before damage occurs.




































