
Major Cyber Attacks in Review: October 2024
October 2024 brought a wave of high-profile cyber incidents across various sectors, highlighting the ongoing challenges in digital security. Financial institutions, tech companies, and critical infrastructure faced major breaches.
For instance, Interbank in Peru saw the exposure of over 3 million customers’ sensitive data, while Free, a prominent French ISP, confirmed a breach affecting over 19 million users. Another striking incident involved the massive healthcare data breach at Change Healthcare, impacting the records of 100 million individuals in the U.S.
Dive into our monthly review to understand the latest tactics employed by threat actors and how organizations can strengthen their defenses. Read on for a deeper look at October’s major cybersecurity breaches.
Interbank Breach Exposed Data of Over 3 Million Customers
In June 2024, Interbank, one of Peru’s top financial institutions, confirmed a significant data breach that exposed sensitive information of customers. The breach came to light after a hacker, using the alias “kzoldyck,” leaked portions of the stolen data on multiple hacking forums.
The attacker claimed to have obtained internal API credentials and over 3.7 TB of data from Interbank’s systems. They revealed 3 million customer’s information in the post, and also noted failed extortion attempts with the bank’s management prior to the leak.
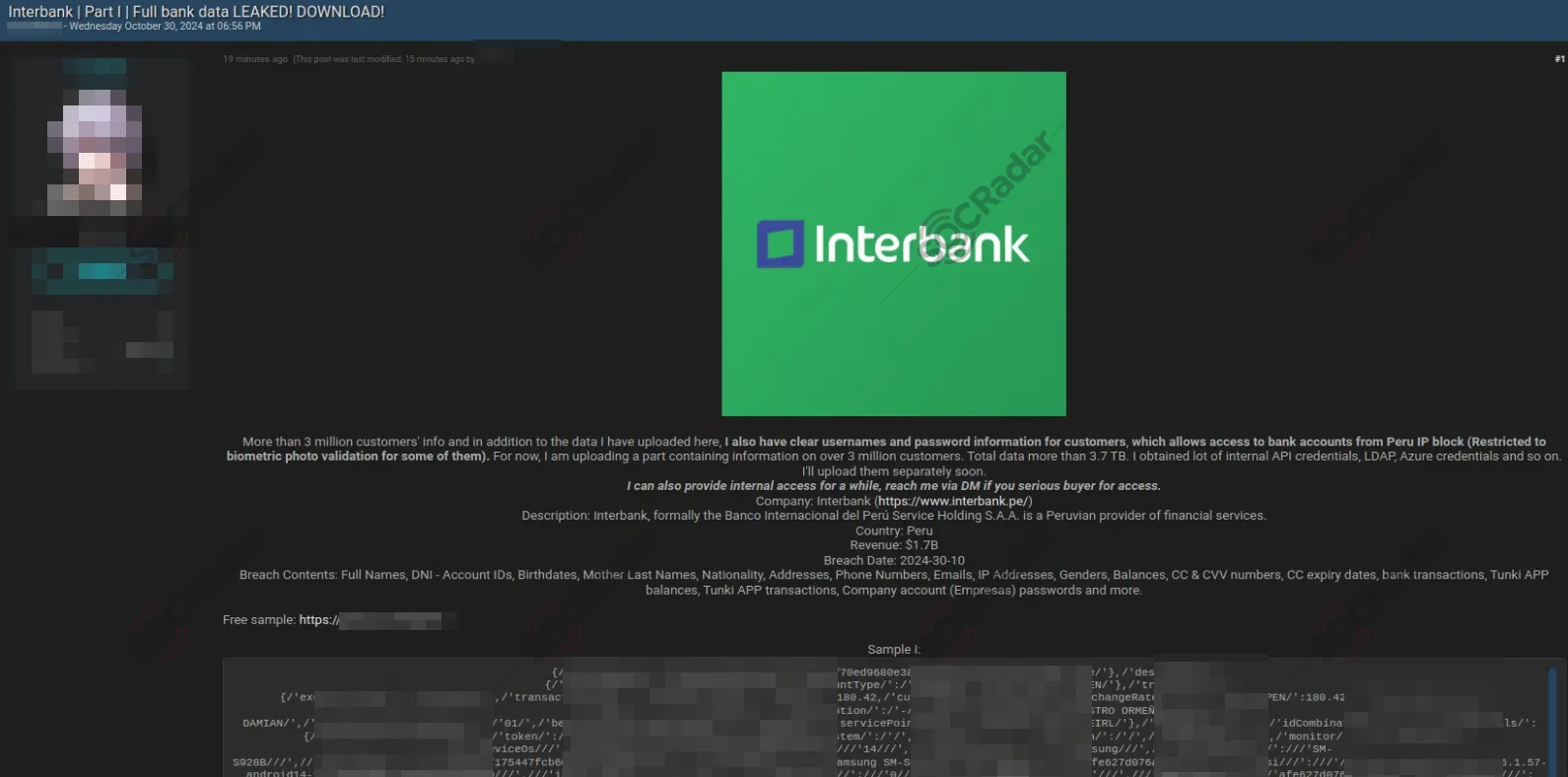
Interbank data breach post (Source: SOCRadar Dark Web News)
The compromised data reportedly includes customer names, account IDs, addresses, phone numbers, email addresses, and sensitive financial details such as credit card numbers, CVVs, and even plaintext credentials.
Free ISP Breach Exposed Data of Over 19 Million French Subscribers
On October 26, 2024, Free, a prominent French ISP under Iliad Group, confirmed a significant data breach affecting over 19 million subscribers. The breach came to public attention when a hacker posted samples of stolen data, including IBANs, names, phone numbers, and addresses, for sale on BreachForums.
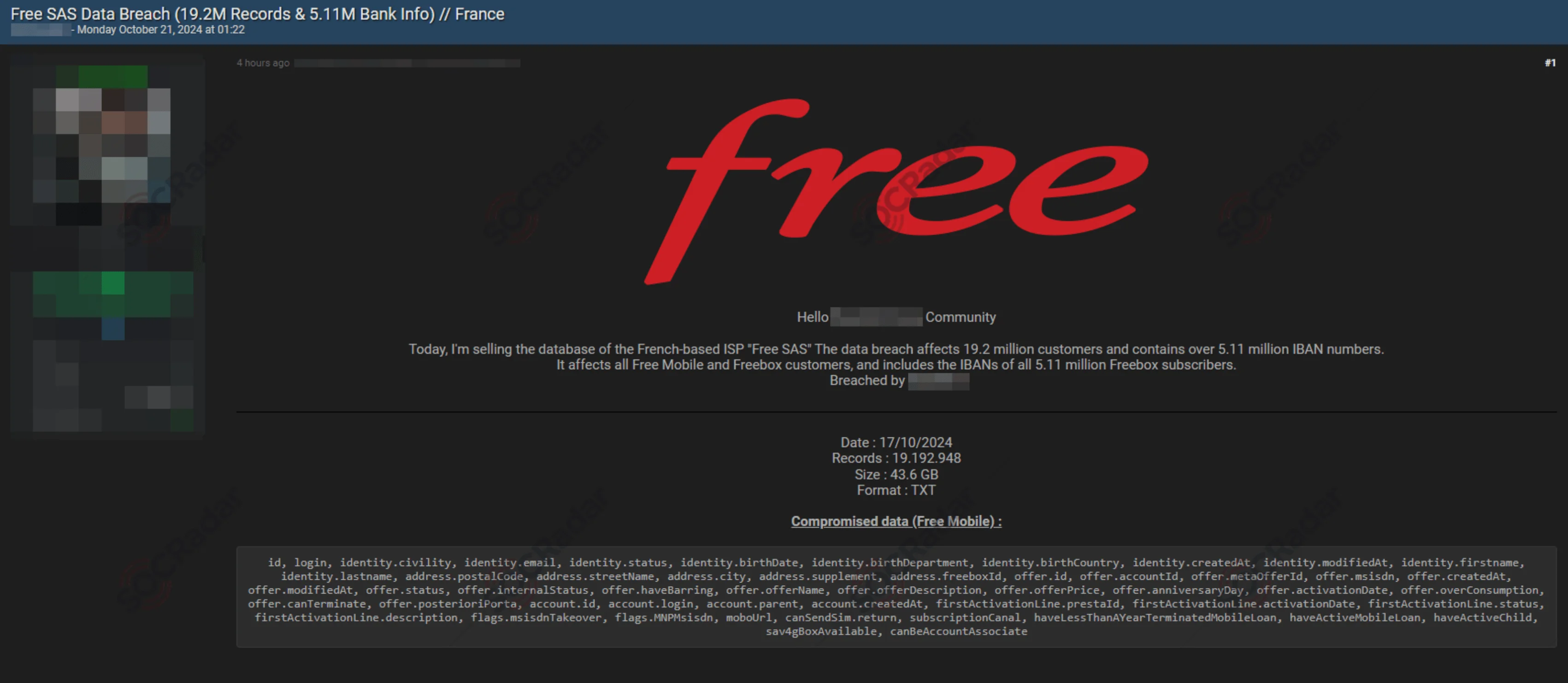
Free ISP data breach post (Source: SOCRadar Dark Web News)
The breach reportedly targeted Free’s internal management system, affecting both Free Mobile and Freebox customers. While Free assured that passwords, bank card details, and communications were not compromised, the exposed IBANs and personal information still pose privacy risks, raising potential for phishing and fraud.
Moreover, the attacker threatened further exposure by releasing 100,000 lines of customer IBANs on the day of the company’s disclosure, demanding over $70,000 to prevent a wider release.
This breach underscores security vulnerabilities in France’s telecom sector, amplifying concerns over critical infrastructure amid recent high-profile cyber incidents.
Find more details about this incident in our blog post: Free ISP Breach Compromises Millions, Threat Actor Threatens Data Leak.
Change Healthcare Ransomware Attack Exposed Data of 100 Million Patients
UnitedHealth confirmed that the February ransomware attack on its subsidiary, Change Healthcare, compromised the personal and healthcare information of over 100 million individuals. Conducted by the BlackCat (ALPHV) ransomware gang, the attack became one of the largest healthcare data breaches in recent history.

SOCRadar threat actor card for BlackCat ransomware
The attackers exploited weak Citrix remote access without multi-factor authentication, using stolen credentials to steal 6 TB of sensitive data before encrypting systems.
UnitedHealth reportedly paid an initial ransom of $22 million, yet data leaks persisted after a second extortion by an affiliate, RansomHub. The financial toll from the attack has surged to approximately $2.45 billion in losses by Q3 2024, marking significant operational and reputational damage.
Utilize SOCRadar’s Breach Datasets feature – under the Cyber Threat Intelligence module – to track exposed information across the Dark Web. By continuously monitoring compromised datasets, your organization can swiftly identify breaches and mitigate risks associated with stolen credentials and other sensitive data.
Monitor Breach Datasets and Combolists through hacker channels to prevent exposure to threats (SOCRadar XTI)
IntelBroker Breached Cisco DevHub, Claimed Access to Sensitive Data for 12 Days
On October 14, 2024, IntelBroker, the admin of BreachForums, claimed a successful breach of Cisco Systems, targeting the company’s DevHub environment. The threat actor alleged access to sensitive materials, including source codes, certificates, API tokens, and customer Secure Remote Connections (SRCs). IntelBroker also claimed access to data linked to major corporations like Microsoft, AT&T, and Bank of America, posting screenshots on the forum as proof.
Cisco responded swiftly, stating that the exposed data originated from its public-facing DevHub and that its core systems remained secure. On October 18, Cisco confirmed revoking IntelBroker’s access and temporarily disabled DevHub to prevent further exploitation.
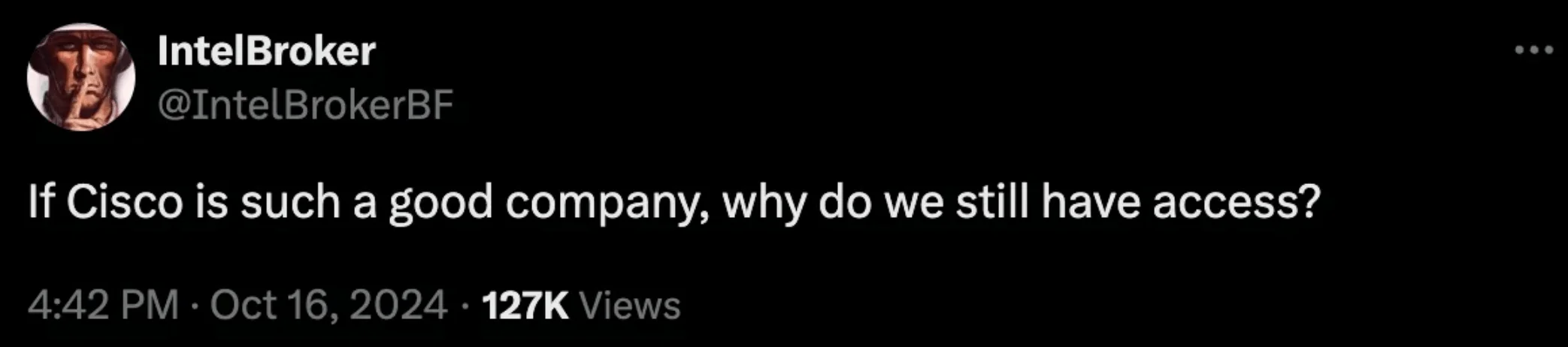
In an October 16 tweet, IntelBroker stated that they still had access to Cisco’s systems
Despite Cisco’s reassurances, IntelBroker maintained their breach claims on social media, underscoring the reputational impact for Cisco and emphasizing IntelBroker’s perceived resilience within the cybercriminal community.
Read more about the Cisco incident and IntelBroker’s claims: IntelBroker’s Alleged Cisco Breach.
Game Freak Confirmed Cyberattack Leaked Employee Data and Game Source Code – Pokemon Breach
Japanese video game developer Game Freak, co-owner of the Pokémon series, confirmed a cyberattack in August 2024 that compromised personal data of 2,606 employees and exposed sensitive game information.
The breach, which targeted the company’s servers, resulted in the theft of employee names and company email addresses. Additionally, the attackers accessed source code for past Pokémon titles and files from an in-development game, codenamed “Synapse.”
Game Freak acknowledged the incident on its website, detailing its response to affected employees and efforts to strengthen server security. This breach underscores the risks facing prominent gaming studios and raises concerns over safeguarding intellectual property in the gaming industry.

The breach notice was published in the news page of Game Freak’s official site
Casio Ransomware Attack Compromised Personal Data of Employees, Customers, and Partners
Casio confirmed that it suffered a ransomware attack in early October 2024, which led to the theft of sensitive data affecting employees, job applicants, customers, and business partners.
The attack, attributed to the Underground ransomware group, resulted in unauthorized access to Casio’s network and subsequent data leaks, including employee information, business partner details, and financial documents.
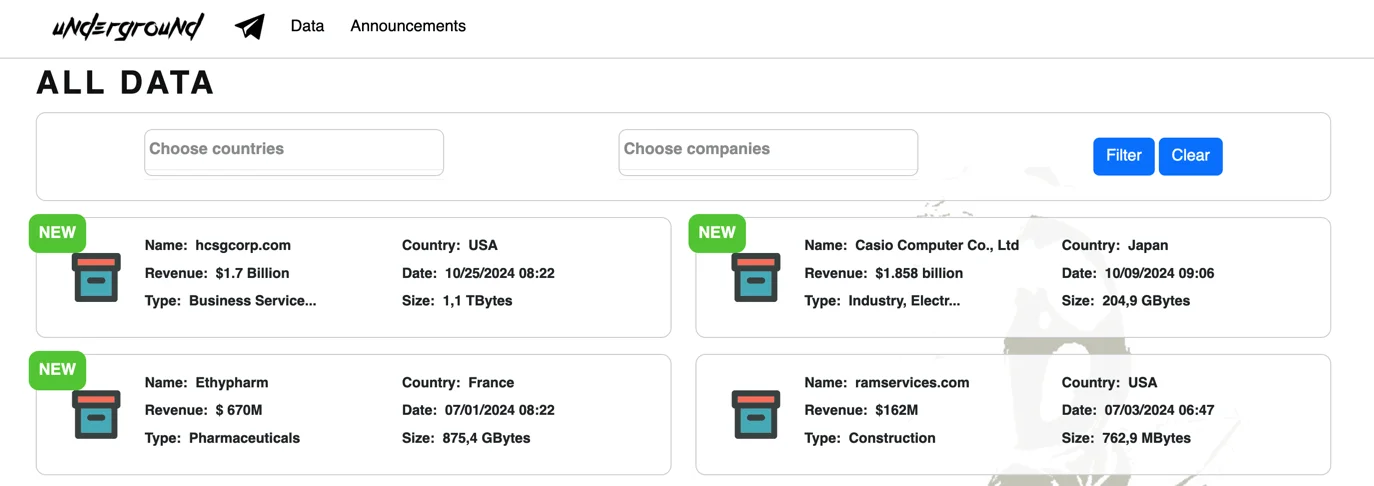
Latest breach listings by Underground ransomware, including Casio
Casio’s disclosure listed compromised data such as personal information of employees and job candidates, customer details, and business contracts, though it clarified that credit card information remained unaffected. Key services like CASIO ID and ClassPad.net were also reportedly unaffected, as they operate on separate servers.
SOCRadar’s Dark Web Monitoring and Dark Web News modules deliver critical insights into threat actor activities, helping organizations stay ahead of potential data breaches and cyber threats. By continuously monitoring Dark Web forums, marketplaces, and other underground channels, these tools provide early access to intelligence on potential data leaks and threat actor plans targeting specific industries, regions, or even your own organization.
SOCRadar’s Dark Web Monitoring – Monitor Black Market, Botnet Data, PII Exposure, and more
With in-depth threat intelligence reports and profiles, SOCRadar’s Threat Actor Intelligence also offers visibility into specific threat groups, tactics, and Indicators of Compromise (IoCs) linked to recent breaches. This critical data empowers your organization to identify patterns in Dark Web activity, manage vulnerabilities, and ensure sensitive data remains protected from unauthorized access or sale.
Internet Archive Breach Exposed Data of 31 Million Users, API Keys, and Source Code
In October 2024, the Internet Archive confirmed a major data breach that compromised personal information for 31 million users, including email addresses, bcrypt-hashed passwords, and screen names.
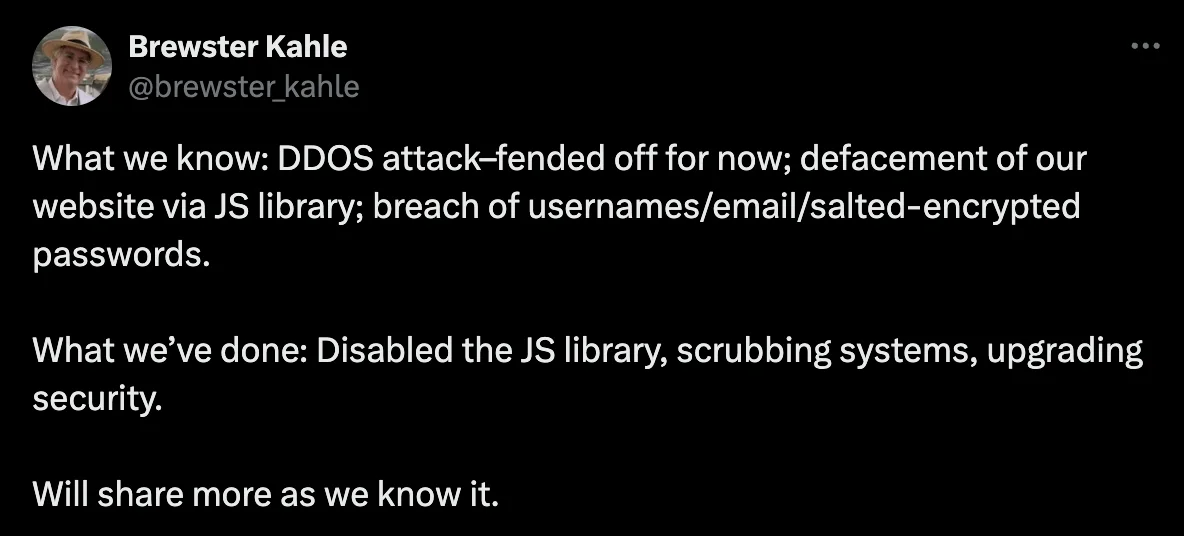
Tweet by Brewster Kahle, regarding the breach incident and DDoS attacks (X)
The breach, traced to an exposed GitLab configuration file, allowed a threat actor to access API keys and source code for the Archive’s platforms. Following this breach, the popular Wayback Machine and related services experienced widespread outages due to persistent Distributed Denial-of-Service (DDoS) attacks by the hacktivist group BlackMeta.
The Internet Archive, known for its role in preserving online content, responded by taking affected services offline to prioritize security and prevent further exploitation. BlackMeta’s DDoS attacks, reportedly politically motivated, compounded the challenges facing the Archive, disrupting access for users globally.
The Archive’s response included disabling compromised JavaScript libraries and securing its Zendesk server after attackers leaked sensitive user information dating back to 2018.
For a detailed timeline of the Internet Archive breach and the latest updates, see the below article:
Internet Archive Data Breach and DDoS Attacks: What You Need to Know
LEGO Website Breach Used to Promote Fake Cryptocurrency Scam
On October 5, 2024, LEGO’s official website was breached by hackers who displayed fraudulent advertisements for a non-existent “LEGO Coin.”
The hackers replaced the home page ads with a scam promoting a fake digital coin, encouraging visitors to “Buy the new LEGO Coin today and unlock secret rewards!” The fake ad, captured by a LEGO Reddit moderator, led some buyers to fall victim, with estimated losses in the low hundreds of dollars.

Fake advertisement for the LEGO Coin (Source: Reddit)
LEGO quickly removed the unauthorized banner and confirmed that no user accounts or sensitive customer data were compromised. The company stated that it has identified the breach’s cause and is implementing enhanced security measures to prevent future incidents.
American Water Cyberattack Disrupted Systems and Customer Services
American Water, the largest publicly traded U.S. water and wastewater utility, experienced a cyberattack leading to a shutdown of several systems, including its online customer portal, MyWater. The company, serving over 14 million people across 14 states, immediately engaged third-party cybersecurity experts and reported the breach to law enforcement to assess and contain the impact.
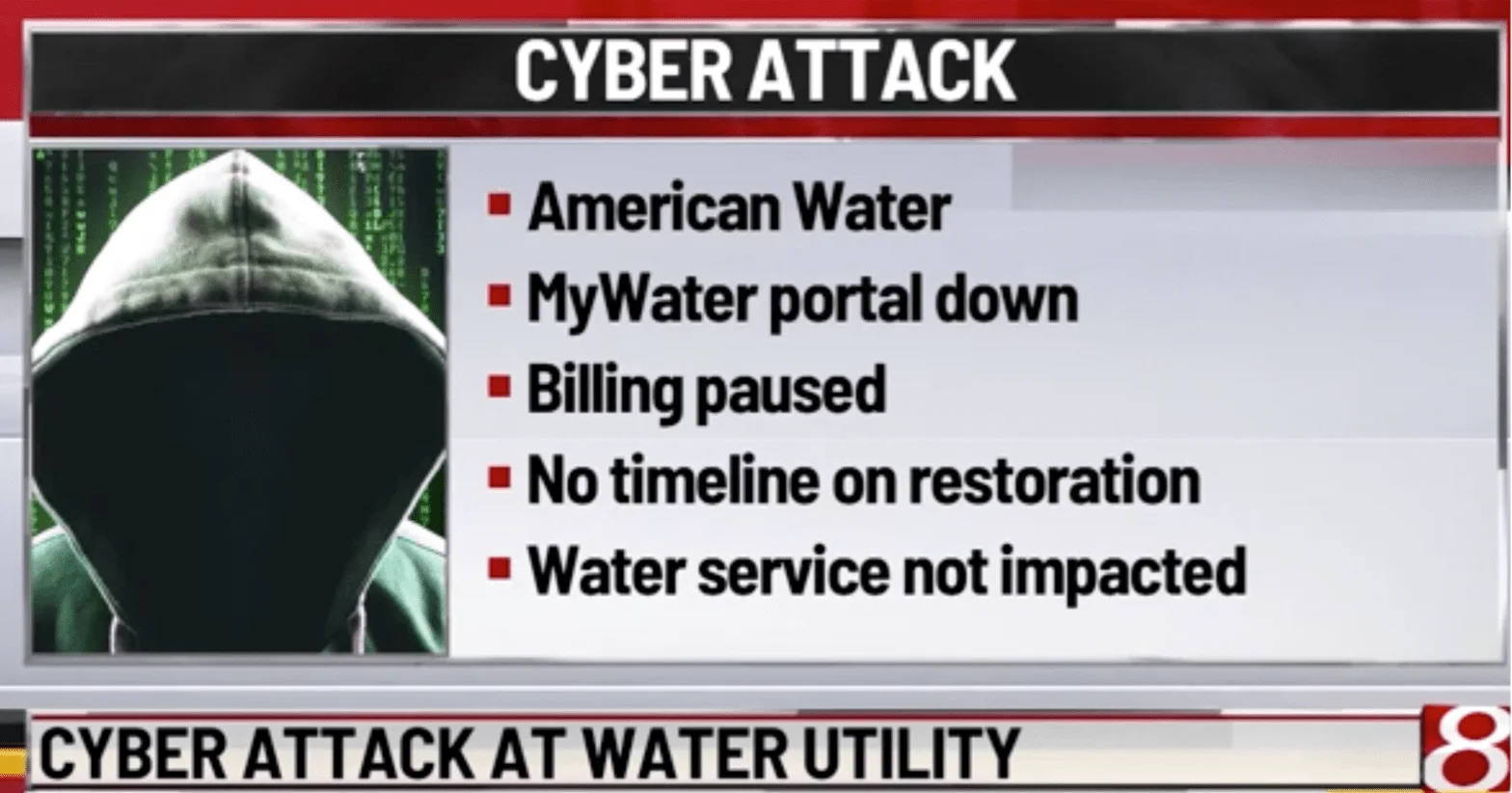
News on the American Water cyber attack (Source: Wishtv)
In a SEC filing, American Water disclosed that they have taken preventive measures by disconnecting certain systems, and reassured customers that no late fees will apply while services remain offline.
FBCS Data Breach Exposed Information of Over 4 Million, Including Comcast and Truist Customers
It was revealed that in February 2024, Financial Business and Consumer Solutions (FBCS), a U.S.-based debt collection agency, experienced a data breach affecting over 4 million individuals. Cybercriminals accessed sensitive data within FBCS’s systems between February 14 and February 26, impacting clients like Comcast Cable Communications and Truist Bank, which have since notified affected customers.
Data breach notification by Comcast (Source: maine.gov)
Initially thought to affect 1.9 million individuals, the scope widened to 4.2 million by July. Exposed data varied by individual and included names, addresses, Social Security numbers, and medical information, increasing the risk of identity theft. Comcast later confirmed ransomware involvement in the attack, offering affected customers a year of free credit monitoring.
Truist Bank began notifying its customers in September, including those impacted by other breaches, and has provided additional guidance and monitoring solutions.
For more details, read SOCRadar’s full coverage blog post:FBCS Breach Exposes Millions, Including Comcast and Truist Bank.
Cloudflare Mitigated Record-Breaking 3.8 Tbps DDoS Attack Targeting Financial and Telecom Sectors
Cloudflare mitigated a record-breaking DDoS attack that reached a peak of 3.8 Tbps, marking one of the largest on record.
The 65-second hyper-volumetric L3/4 attack was part of a broader DDoS campaign targeting clients in finance, internet, and telecom sectors, with over 100 similar attacks reported in September, many exceeding 2 Bpps and 3 Tbps.
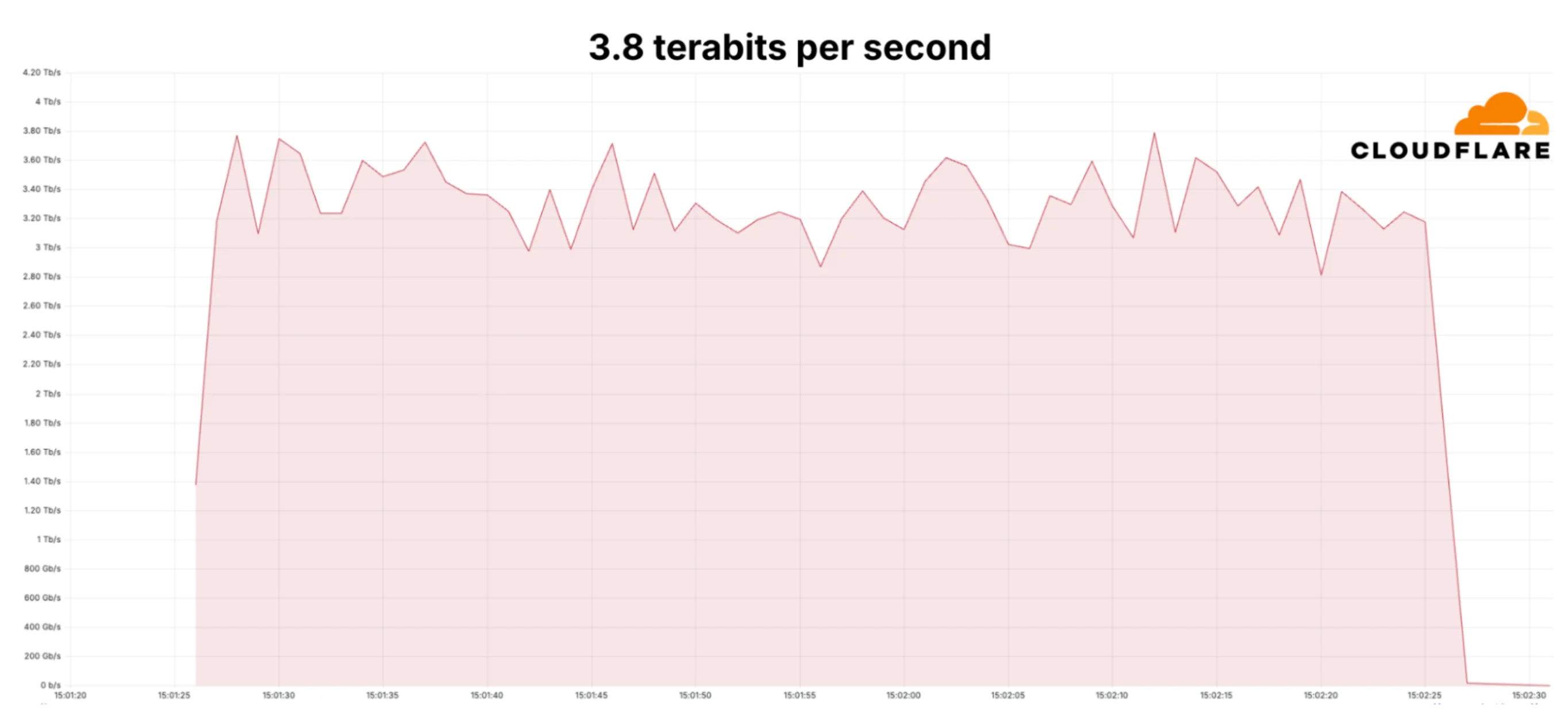
Diagram of the DDoS attack (Source: Cloudflare)
The attack exploited a critical vulnerability (CVE-2024-3080) in ASUS routers, impacting over 157,000 devices across regions like the U.S., Russia, and Vietnam. Cloudflare’s response required precise filtering to handle the flood of malicious packets without taxing CPU resources, ensuring continued service for legitimate users.



































