
Beyond the Click: Understanding Zero-Click Exploits and Their Impact
A zero-click exploit is a sophisticated type of cyberattack that operates without requiring any direct interaction from the target user. Unlike traditional exploits, where a user might be tricked into clicking on a malicious link or downloading a suspicious file, zero-click exploits are designed to execute malicious code autonomously. Zero-click exploits primarily target vulnerabilities in applications that handle and process data from untrusted sources, such as SMS platforms, email apps, and phone applications.
For instance, when a smartphone receives an SMS or email, it often displays notifications based on the content of the message, even before the user opens it. If a vulnerability exists in the data processing code of these applications, a well-crafted malicious message can exploit it, leading to unauthorized code execution. The malicious code can then install malware, erase its traces, and even suppress notifications, leaving the user completely unaware of the breach. Expanding on zero-click exploits, particularly in the context of the growing prevalence of artificial intelligence in workflows, it is essential to recognize such risks are escalating. For instance, imagine a personal assistant LLM given access to an individual’s email. While convenient, it opens doors to vulnerabilities, like indirect prompt injection attacks, where a malicious email could manipulate the LLM into sending spam from the user’s inbox.
The significance of zero-click exploits lies in their stealthy nature and high success rate. Traditional cyberattacks provide a window of opportunity for the target to detect and possibly counteract the threat. In contrast, zero-click exploits can compromise a device subtly, sometimes only leaving behind a missed call notification from an unknown number. This covert operation makes them highly valuable assets in the arsenal of cyber threat actors, including advanced persistent threats (APTs) and nation-states.
Such exploits are often employed to deploy spyware, enabling covert surveillance and data collection on individuals deemed significant by governments or other entities. This was also one of the focal points of Edward Snowden’s actions back in the 2010s, as he emphasized smartphones can be hacked into with just one text message and then used to spy on their owners. This situation bears resemblance to a more recent vulnerability, disclosed in September 2022 by WhatsApp (CVE-2022-36934). An attacker only needed to send a specially crafted video call to exploit the vulnerability, subsequently gaining the ability to execute code by chaining it with another vulnerability.
Zerodium, a company that specializes in acquiring vulnerabilities, currently offers substantial rewards for such security vulnerabilities. They offer up to $1 million for WhatsApp exploits that enable remote code execution and local privilege escalation, increasing to $1.5 million if it involves zero-click exploits, as seen in the case of CVE-2022-36934, underscoring their growing significance. Likewise, the bounty for zero-click exploits for iOS FCP and Android FCP go higher, up to $2.5 million.
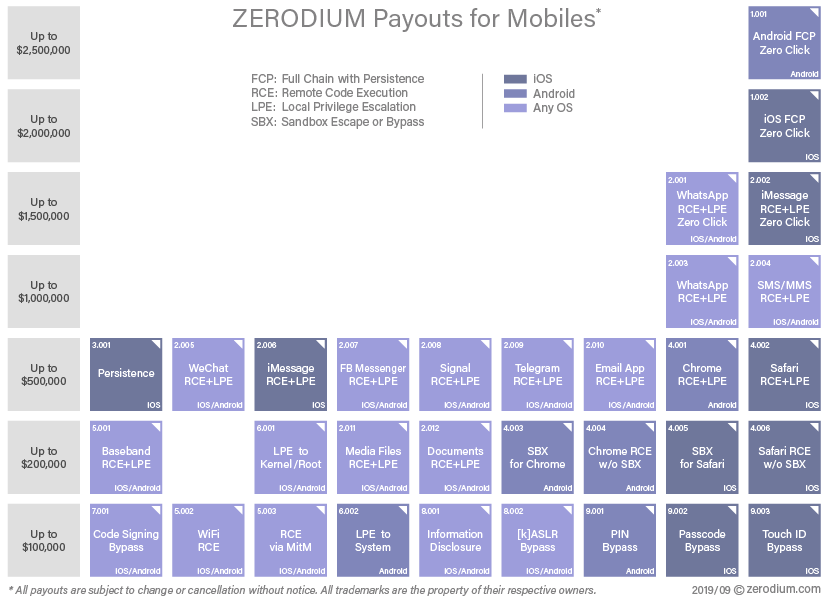
How Do Zero-Click Exploits Work?
Zero-click exploits operate in a stealthy and sophisticated manner, often leaving little to no trace of their intrusion. Here’s a hypothetical scenario to illustrate their modus operandi:
- Identification of Vulnerability: The first step involves cybercriminals pinpointing a vulnerability, often in popular e-mail or messaging applications.
- Crafting the Attack: Once the vulnerability is identified, attackers craft a specific message, e-mail, or call tailored to exploit this weakness.
- Remote Infection: The vulnerability might, for instance, allow hackers to remotely compromise a device through e-mails that consume an excessive amount of memory. This means that merely receiving such an email or message can lead to an infection.
- Stealthy Operation: Interestingly, the malicious e-mail, message, or call used to initiate the exploit doesn’t necessarily persist on the victim’s device. It can be designed to delete itself after successful execution, further obscuring the attack’s origin.
- Access and Control: As a consequence of the exploit, cybercriminals can gain extensive control over the compromised device. This includes the ability to read, modify, leak, or even delete messages.
It is worth noting that the vector of the attack can vary widely. Whether it is a series of network packets, authentication requests, text messages, MMS, voicemails, video conferencing sessions, phone calls, or messages over platforms like Skype, Telegram, or WhatsApp, the primary objective remains the same: to exploit a vulnerability in an application’s code responsible for processing the data.
For instance, the ShellShock vulnerability (CVE-2014-6271), a historical example of such exploitation, allowed attackers to execute arbitrary code on a target system without the need for direct user interaction, through network interaction, showcasing the wide range of potential attack vectors. While ShellShock is not typically categorized as a ‘zero-click’ exploit, it exemplifies vulnerabilities that extend beyond user interaction, as attackers could exploit the vulnerability through network interactions or other means.
In the modern context, the capabilities of a spyware named ‘Pegasus’ serve as a testament to how attackers leverage such vulnerabilities to conduct malicious activities. A brief illustration of the capabilities of Pegasus spyware can be seen below.
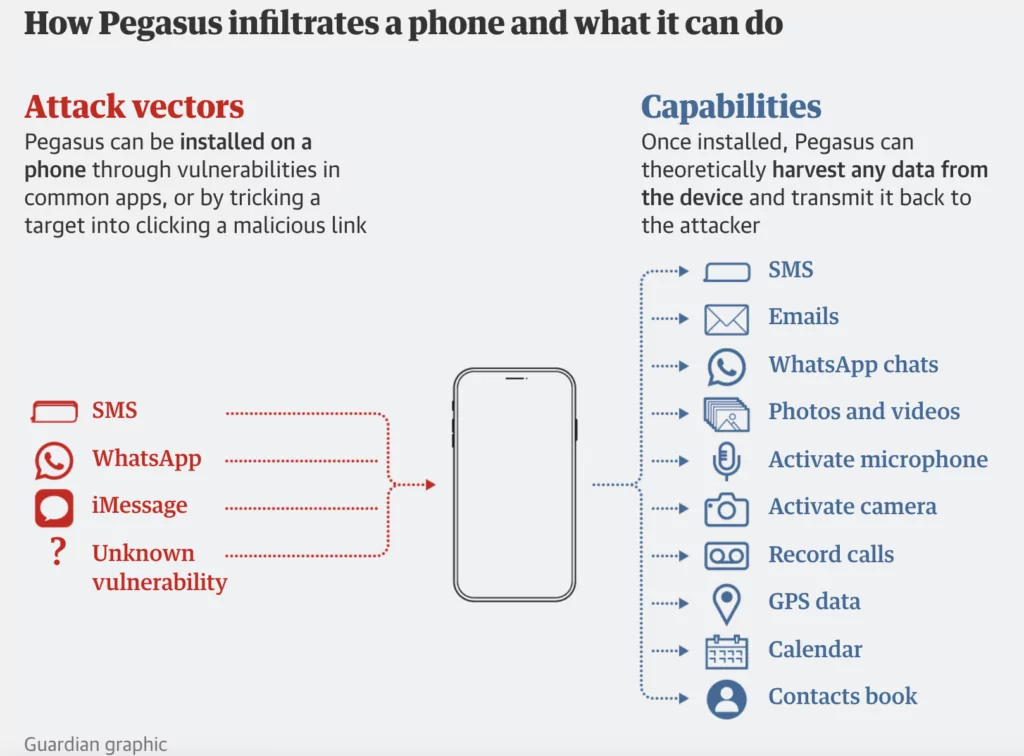
Who Leverages Which Applications with Zero-Click Exploits?
Smartphones stand out as the primary targets for zero-click exploits. Given their ubiquity and the plethora of communication apps they support – from SMS, phone calls, and messaging apps to social media platforms – they offer a vast attack surface for cybercriminals.
Popular smartphone brands, notably Apple, and widely used apps like WhatsApp are frequently in the crosshairs of such attacks. A notable instance of this was the 2019 WhatsApp exploit. During this incident, a vulnerability within WhatsApp was manipulated by attackers to discreetly install spyware on victims’ phones. The exploit operated through a VoIP call, where a specially designed series of packets were hidden within the connection. This attack was particularly alarming as it targeted high-profile activists and political dissidents. The incident was later brought to light in court by Meta (previously known as Facebook), the parent company of WhatsApp.
The NSO Group, an Israeli firm, emerges as one of the most prominent providers of zero-click exploits. Specializing in selling surveillance software to governments and law enforcement agencies, the company has been implicated in distributing exploits that target widely used messaging apps, including WhatsApp. Their flagship product, the Pegasus Spyware, has allegedly been at the forefront of numerous covert surveillance operations since its creation. This powerful tool is designed for remote zero-click surveillance of smartphones, making it a potent weapon in the hands of its users.
Furthermore, NSO Group’s exploits have not been limited to messaging apps. In 2021, the company was implicated in a significant breach targeting nine Bahraini activists. This attack leveraged a previously undisclosed zero-click vulnerability in Apple’s iMessage. The exploit was used to bypass iOS security measures, underscoring the company’s capability to target even the most secure platforms.
How Can You Mitigate Zero-Click Exploits?
- Restart Your iPhone Periodically: For iPhone users, a simple yet effective measure is to periodically restart the device. Experts at Amnesty have demonstrated that this action can potentially disrupt the functioning of spyware like Pegasus on iOS, at least temporarily. Restarting has the benefit of halting any non-persistent code in its tracks. However, a potential downside is that this action might erase traces of an infection, making it challenging for researchers to ascertain if a device was targeted by a zero-click attack.
Zero-click exploits can frequently leverage buffer overflow vulnerabilities, as was the case with the Pegasus spyware (in BLASTPASS exploits). Given that buffers primarily reside in RAM, malicious code will be erased from memory upon a reset, unless additional persistence measures are taken.
- Avoid Jailbreaking Devices: Jailbreaking removes certain built-in security controls from the device’s firmware. Moreover, jailbroken devices can install unverified software, making them susceptible to vulnerable code that could be exploited by zero-click attacks.
- Segregate Data for High-Profile Targets: Individuals at higher risk should consider using a dedicated device solely for sensitive communications. It’s advisable to store minimal information on their phones. Utilizing features like disappearing messages can be beneficial. Additionally, for utmost privacy, it’s recommended to keep phones out of the room during crucial face-to-face discussions.
- Heed Warnings from Tech Companies: Both Apple and WhatsApp have, on numerous occasions, alerted users who might have been on the receiving end of zero-click attacks. If you receive such a notification, it’s imperative to take prompt action.
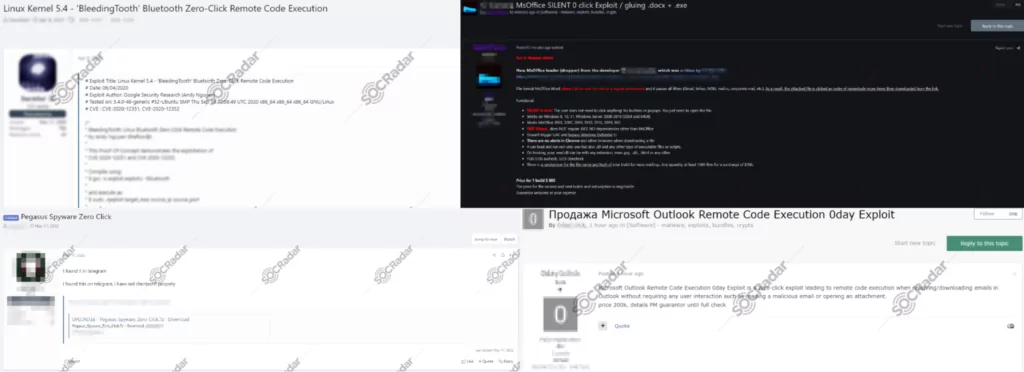
- Stay Updated with SOCRadar: SOCRadar constantly monitors the dark web for potential threats. Its surveillance often detects the sharing and sale of zero-click exploits. By staying updated with SOCRadar, users can receive timely alerts if any post related to zero-click exploits is detected, as illustrated in the graphic below, picturing the sale/share of zero-click exploits.
Conclusion
In today’s rapidly evolving digital landscape, zero-click exploits have emerged as one of the most covert and potent tools for cyber espionage. These sophisticated attacks, which require no user interaction, target vulnerabilities in widely used applications, especially on smartphones. High-profile incidents, such as the 2019 WhatsApp exploit, highlight the real-world implications and the stealthy nature of these breaches.
While companies like the NSO Group have been instrumental in developing and distributing these exploits, their actions have raised significant ethical and security concerns. Mitigating the risks posed by zero-click exploits is challenging, but adopting best practices, staying informed, and being vigilant can offer a layer of protection against these stealthy cyber threats. With tools like SOCRadar’s Dark Web News module, you can at least get a grip on the zero-click exploits.
Additional References:
- What is a Zero Click Attack? | Check Point Software
- Zero-Click Exploits | Kaspersky
- The Pernicious Invisibility Of Zero-Click Mobile Attacks | Forbes
- Forensic Methodology Report: How to catch NSO Group’s Pegasus | Amnesty International
- Zero-click attacks explained, and why they are so dangerous | CSO Online



































