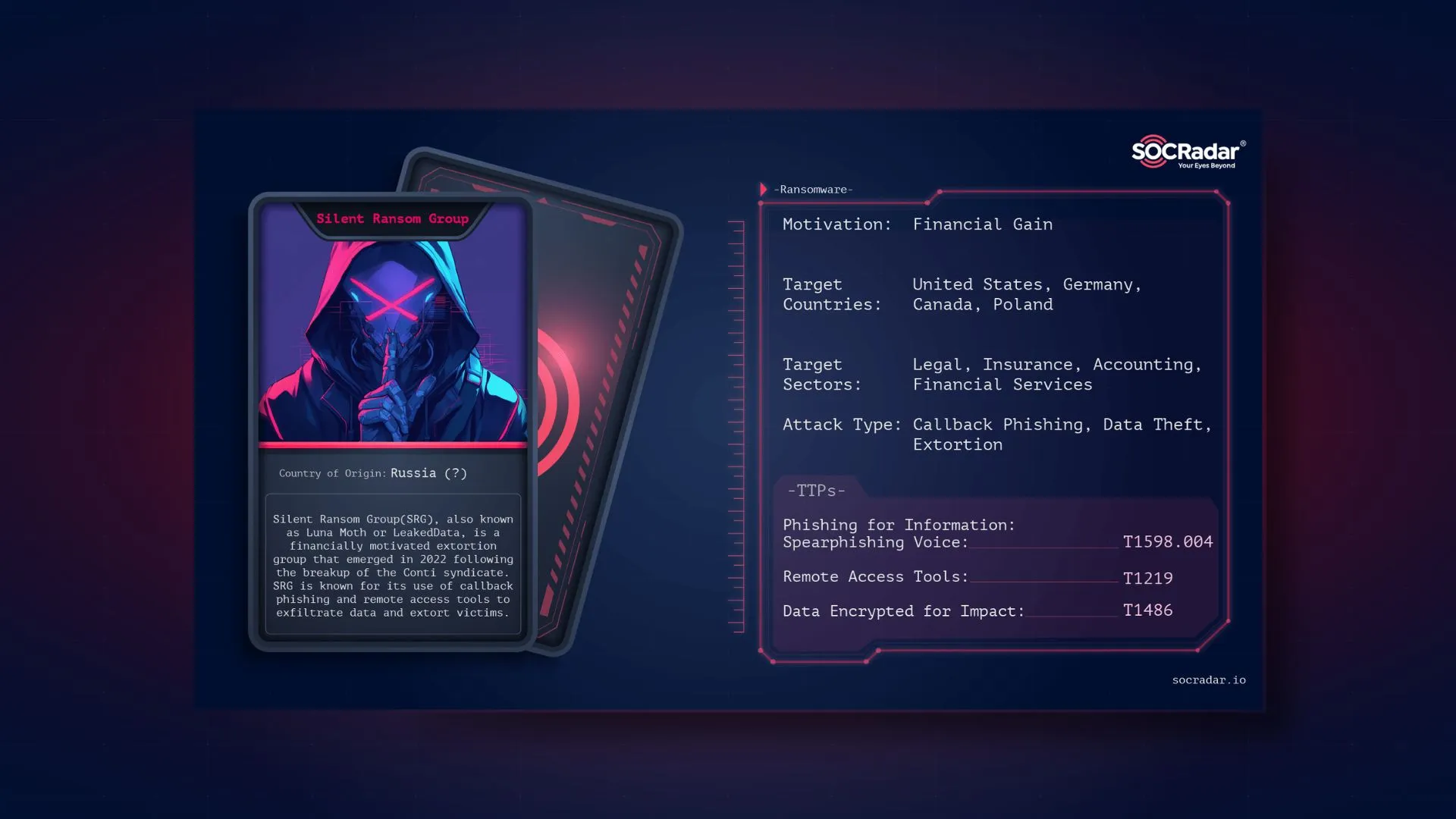
National Credit Union Administration and GTA 5 Leaks, Craxs RAT, New Windows Stealer
The SOCRadar Dark Web Team has detected critical events, including the alleged Grand Theft Auto V source code leak and the compromise of sensitive financial data from the US National Credit Union Administration. Additionally, sophisticated a Android RAT malware and a new Windows data stealer are being sold, posing severe cybersecurity risks. A hacking service announcement advertises unauthorized access to social media and messaging platforms, underscoring the urgent need for robust security measures in today’s interconnected online environment.
Get your free Dark Web Report and find out if your data has been compromised.
Source Code of Grand Theft Auto V is Leaked
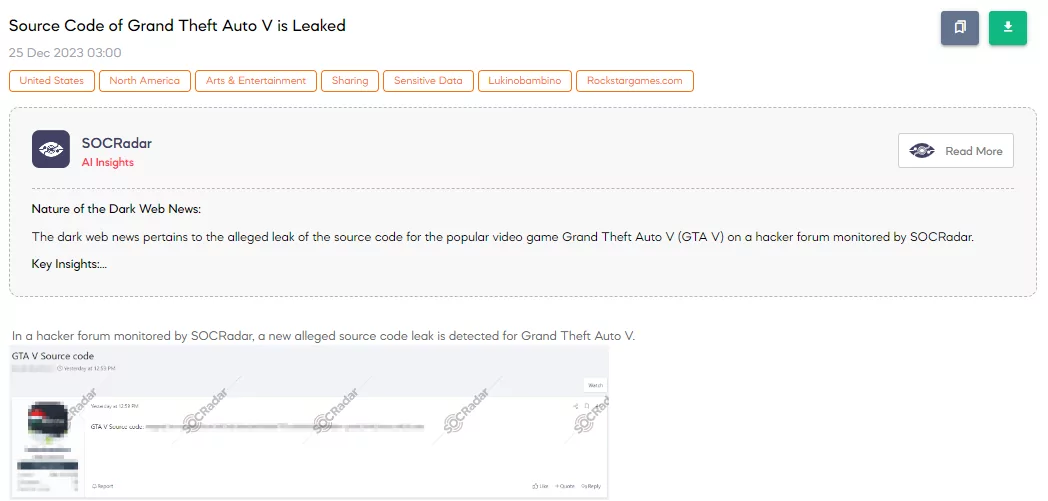
The SOCRadar Dark Web Team has detected a post on a hacker forum indicating a new, alleged leak of the source code for Grand Theft Auto V. The leak of GTA V’s source code poses significant risks, including potential exploitation of vulnerabilities, unauthorized reverse engineering, and an increased threat of cyberattacks targeting players and the game’s server. This event highlights the critical need for stringent security in protecting digital assets.
Data of United States National Credit Union Administration is Leaked
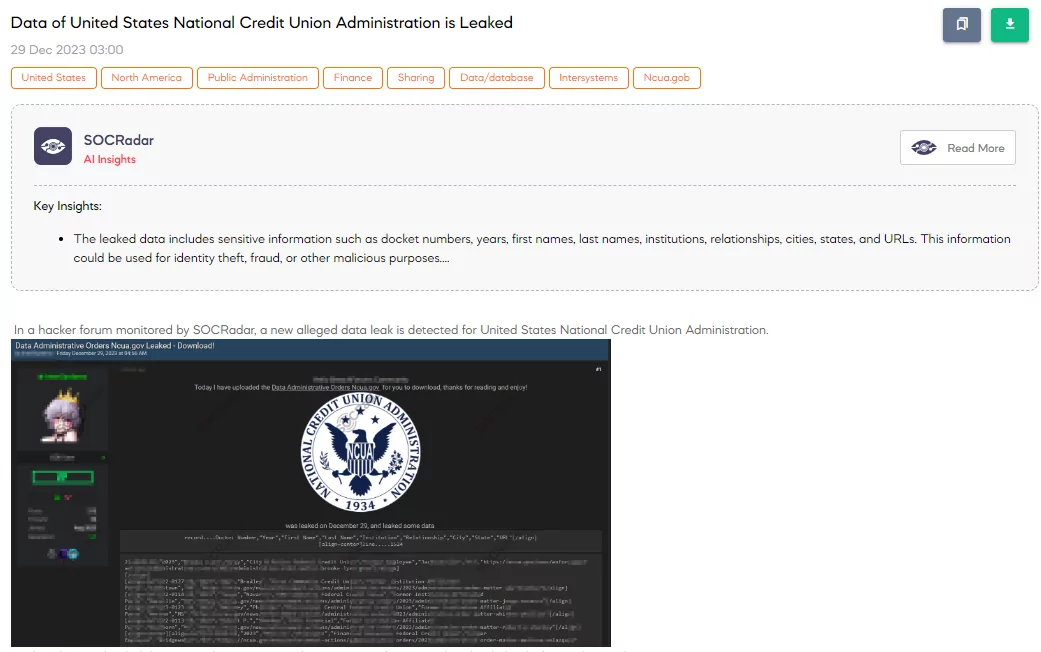
On December 29, 2023, A SOCRadar Dark Web Analyst identified a post on a hacker forum claiming the data leak from the United States National Credit Union Administration (NCUA). The threat actor announces the availability of administrative order data from NCUA’s website for download, including sensitive information such as docket numbers, years, first and last names, institution details, relationships, location information, and associated URLs. The data was allegedly leaked on December 29, highlighting a significant breach of sensitive financial regulatory information.
Craxs Android RAT Malware is on Sale
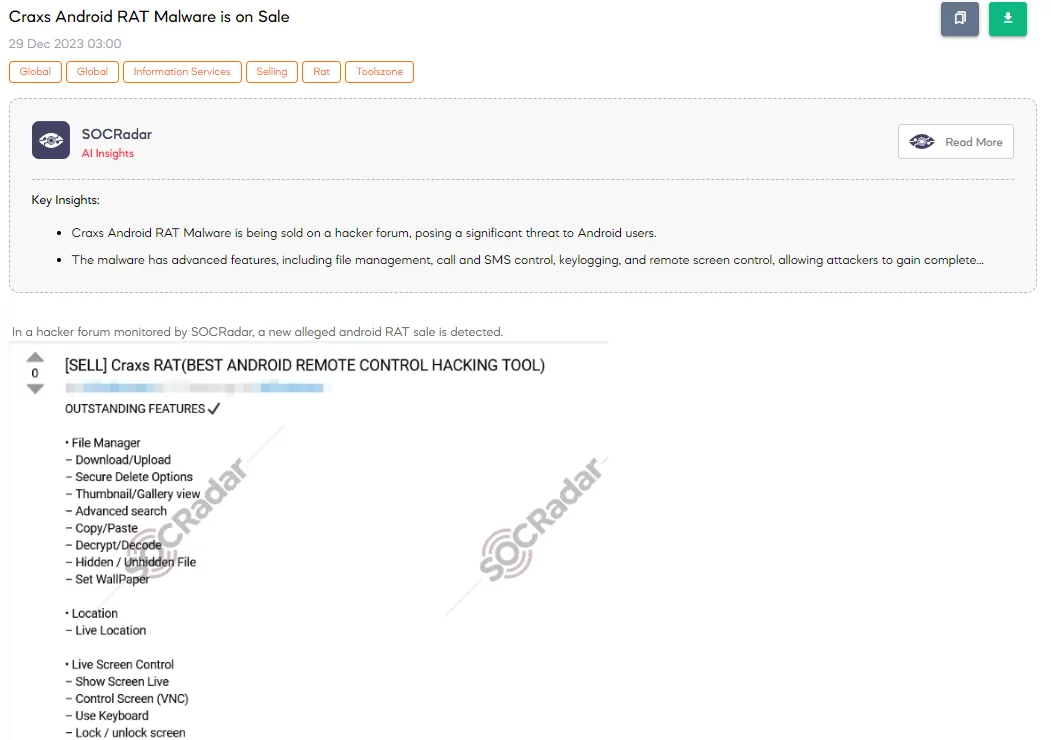
A threat actor on a hacker forum is selling Craxs RAT, a sophisticated Android remote control hacking tool. The threat actor claims it offers extensive features like live location tracking, screen control, file management, keylogging, and various stealth modes for evading detection and maintaining persistence. The tool actively manages calls, SMS, applications, and device settings and provides access to microphones and cameras. The threat actor promotes the tool as a comprehensive solution for unauthorized remote access and surveillance, targeting Android devices with detailed customization and evasion techniques.
A New Windows Stealer is on Sale
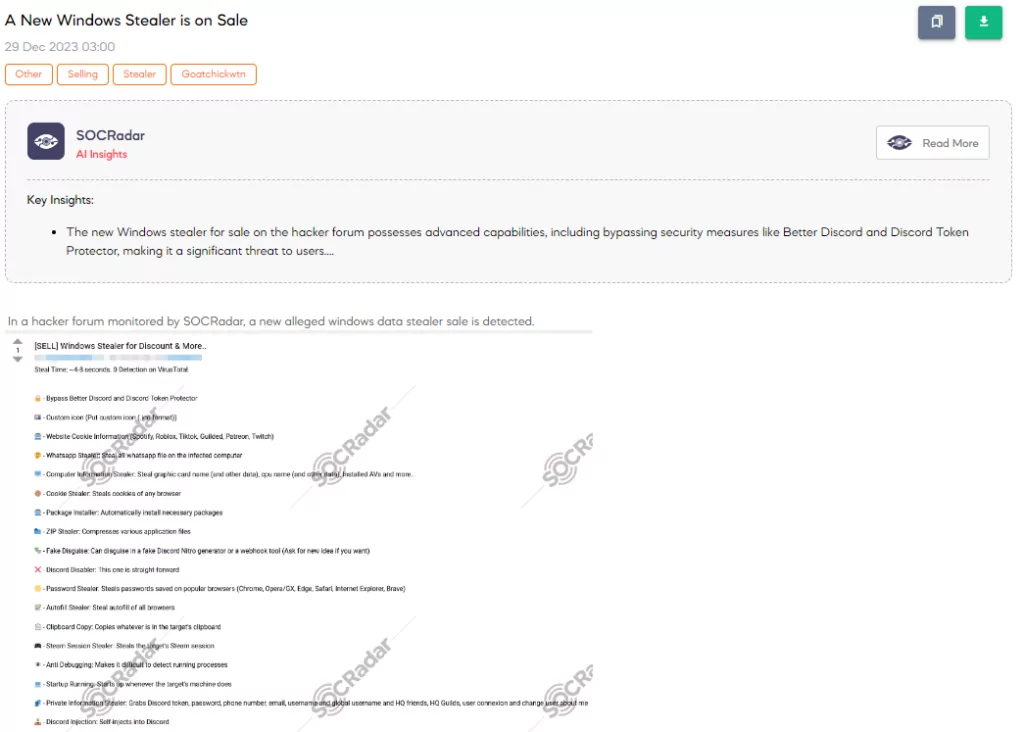
As detected by SOCRadar, a new alleged Windows data stealer is being advertised on a hacker forum. The threat actor claims the tool can steal data in about 4-8 seconds with zero detection on VirusTotal. It reportedly bypasses Better Discord and Discord Token Protector and can steal cookies from the websites of platforms such as Spotify, Roblox, TikTok, Guilded, Patreon, and Twitch.
The tool also claims to have capabilities for WhatsApp data extraction, gathering detailed computer information, stealing browser cookies and passwords, and copying clipboard contents. It boasts additional features like auto-installing necessary packages, compressing files, disguising as fake apps, disabling Discord, and stealing Steam sessions. The stealer also includes anti-debugging and automatic startup and can extract sensitive files, take screenshots, and even cause a Windows Blue Screen of Death.
Hacking Service Announcement is Detected for Social Media and Messaging App Access
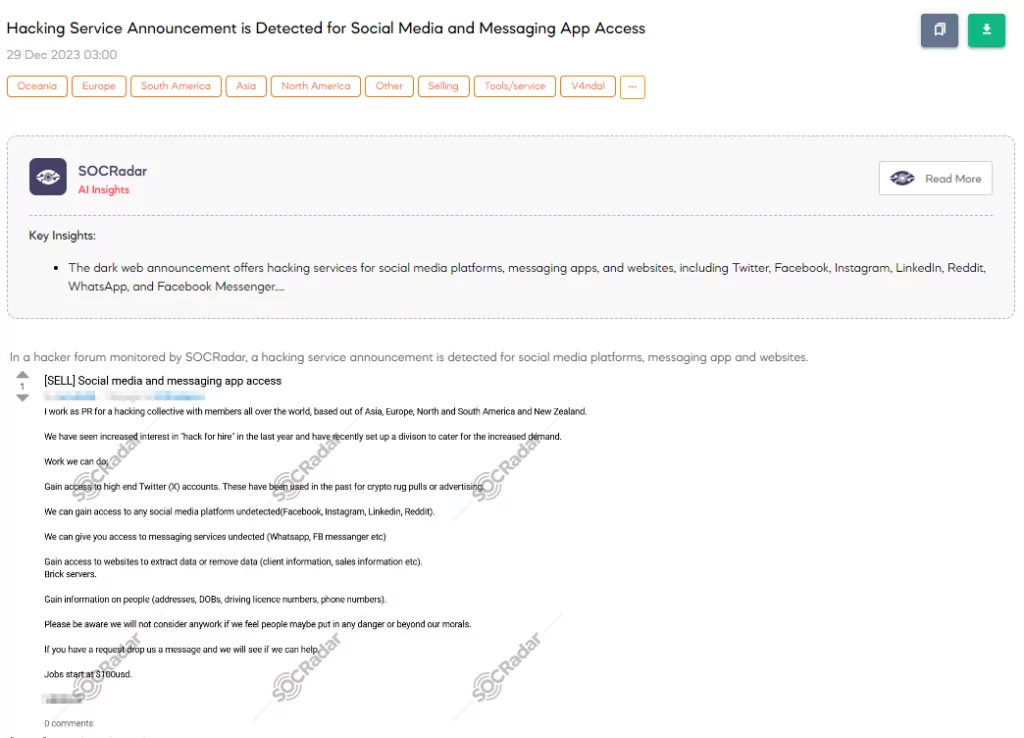
On December 29, 2023, the SOCRadar Dark Web Team identified a hacking service announcement on a hacker forum, offering unauthorized access to various social media platforms, messaging apps, and websites. The threat actor, claiming to represent a global hacking collective with members across Asia, Europe, the Americas, and New Zealand, highlighted their recent division formation to meet the growing demand for “hack for hire” services.
The services advertised include:
- Gaining access to high-profile X (Twitter) accounts previously used for cryptocurrency scams and advertising purposes.
- Undetected access to major social media platforms like Facebook, Instagram, LinkedIn, and Reddit.
- Access to messaging services like WhatsApp and Facebook Messenger without detection.
- Extracting or removing data from websites, including client and sales information.
- Obtaining personal information such as addresses, dates of birth, driving license numbers, and phone numbers.
The threat actor emphasizes their ethical boundaries, stating they will refuse work that could endanger individuals or go against their morals. Starting at $100, they invite interested parties to contact them for potential jobs. The starting price for their hacking services is stated to be $100.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.