
Navigating the Shadowy Depths of the Migo Malware Campaign
The Migo malware campaign emerged as a formidable adversary, targeting Redis servers with novel system-weakening techniques aimed at cryptojacking.

An AI illustration of the Migo Malware Campaign
This campaign not only highlights the sophistication of modern cyber attacks but also underscores the imperative need for robust, proactive cybersecurity measures.
Redis, a popular in-memory data store system, now finds itself at the crossroads of innovation and vulnerability. The Migo malware, leveraging Redis for initial access, employs a Golang ELF binary with compile-time obfuscation and user-mode rootkit capabilities to mine cryptocurrency, all while staying under the radar.

Command to disable protected mode, observed by a Redis honeypot sensor
The intricacies of Migo – from its initial access strategies disabling protected modes and exploiting system vulnerabilities to its persistence mechanisms ensuring continual operation – present a complex challenge.
Defending Against Migo Malware and Further Cyber Threats
SOCRadar’s comprehensive threat intelligence platform serves as an indispensable tool for organizations aiming to preemptively address threats such as Migo Malware. Providing real-time insights and actionable intelligence, it empowers users to identify potential vulnerabilities, understand attacker tactics, and fortify their defenses against sophisticated attacks like Migo.
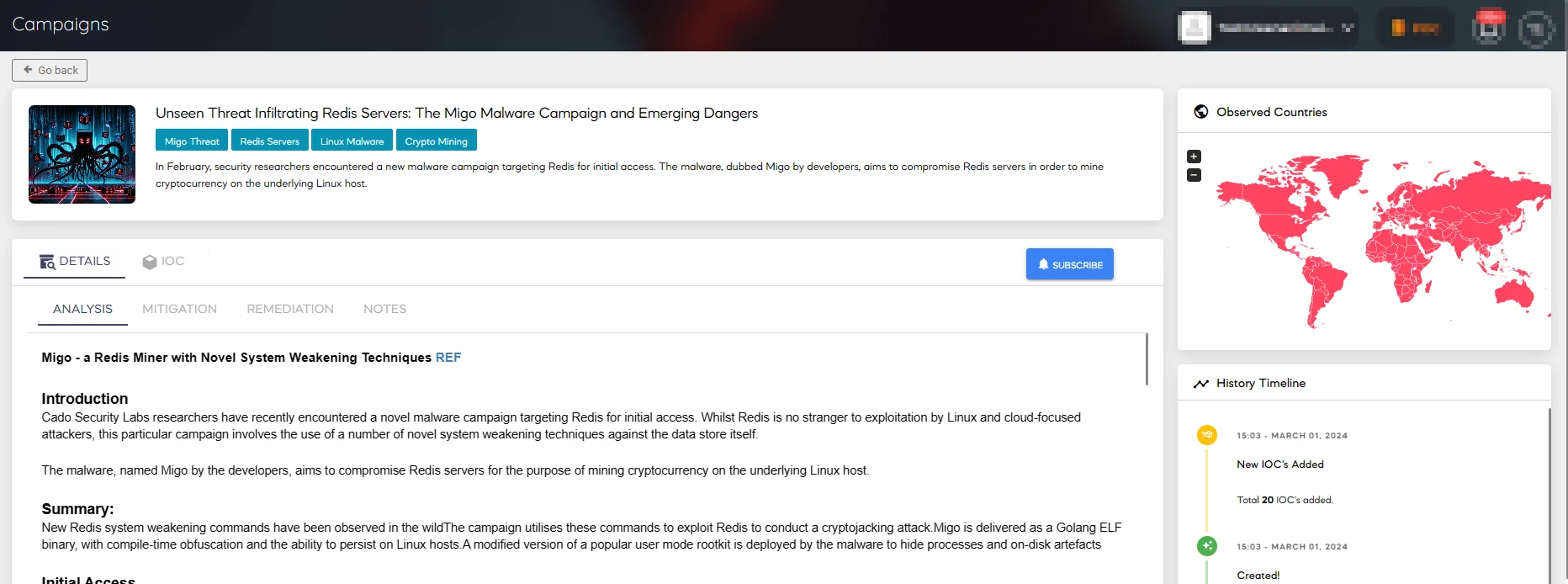
Learn more about the Migo Malware campaign on SOCRadar Campaigns
By leveraging SOCRadar, organizations can not only enhance their incident response capabilities but also adopt a more strategic, informed approach to cybersecurity. SOCRadar ensures not just a reaction to immediate threats, but also a strong resilience against the complexities of tomorrow’s cyber threat landscape through Threat Actor/Malware monitoring.
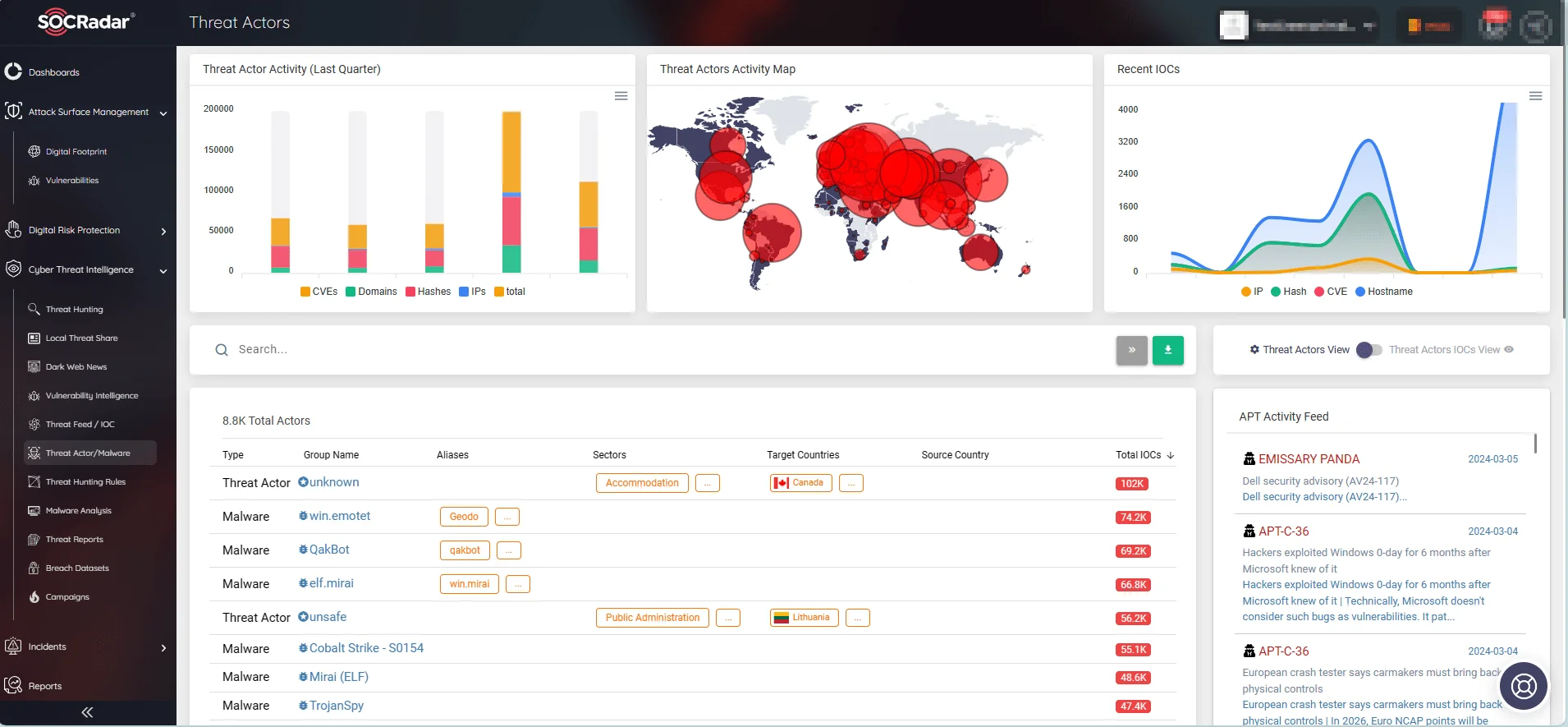
SOCRadar’s Threat Actor/Malware monitoring page
In conclusion, the Migo malware campaign is a stark reminder of the continuous need for advanced cybersecurity solutions. SOCRadar, with its deep insights and proactive stance, stands ready to guide and protect organizations through these digital battlegrounds.
To learn more about the tactics, techniques, and procedures of the threat actor(s) behind the campaign, Migo Malware, visit the campaign page on SOCRadar platform. Discover how SOCRadar can illuminate the path to cybersecurity excellence for your organization by exploring our Cyber Threat Intelligence module.




































