
Threat-Informed Defense (TID): A Threat Intelligence Perspective
Cyberattacks are increasing in frequency worldwide, posing significant challenges for organizations as they strive to protect their cyber assets from persistent and advanced threat actors. While vulnerability assessments, penetration testing and red teaming, play a crucial role in testing your environment and provide a better understanding and fortification of your security posture, they do not fully represent the actual threats that organizations may encounter. To assess and enhance cybersecurity effectively, organizations need to adopt a discipline centered around cyber threat intelligence (CTI), which involves investigating, modeling, and executing cyber adversary tactics, techniques, and procedures (TTPs).
A noteworthy approach in this regard is Threat-Informed Defense (TID), which offers a holistic security strategy by providing a different perspective on security perception. According to MITRE ATT&CK, Threat-Informed Defense leverages a deep understanding of adversary tradecraft and technology to safeguard against, detect, and mitigate cyberattacks. This approach encompasses investments in cybersecurity involving people, processes, and technology that can be effectively incorporated into security plans. Moreover, it promotes a community-based approach to tackle the global challenge.
Why is TID essential? What are the characteristics?
While understanding vulnerabilities is crucial, companies should adopt a Threat-Informed Defense (TID) approach to assess, organize, and optimize their security strategy. By systematically applying a deep understanding of adversary tradecraft and technology and viewing the enterprise through the lens of an adversary, a security team gains critical insights on how to prioritize security operations and investments. This shift in perspective helps the team clearly see how sophisticated adversaries could exploit the company’s assets.
Collaboration and data sharing are also vital tools for reducing security control failures and building a threat-based defense. Traditional security team structures employ threat-focused red teams and defense-focused blue teams to test security controls sequentially. However, security teams often work in silos, and these exercises are typically conducted only once or twice a year, which is insufficient given the rapidly evolving threat landscape. Purple teams, which possess knowledge and expertise on both sides, should adopt a threat-based security approach and play an active role for threat detection exploring the true-positive spectrum and mitigating their impact in a timely manner.
Currently, there is a significant shortage in the hiring of cybersecurity analysts and penetration testing positions. This means that every log or alert reviewed, and every test performed must explicitly contribute to improving an organization’s ability to mitigate, detect, and respond to the known techniques used by the most likely threat actors. Offensive security efforts should always align with the desired outcome to ensure the effective utilization of these limited resources. Threat Intelligence-based adversary emulation can provide the most value in enhancing a security program.
What is the relationship between TID and MITRE ATT&CK?
The ATT&CK knowledge serves as a critical component of Threat-Informed Defense, providing a common language to describe adversary behaviors. However, it is just the starting point. The true value of Threat-Informed Defense lies in relating these behaviors in ATT&CK to an enterprise’s overall security context. This context includes various aspects, such as the specific threat groups that target similar organizations, the existing defenses, the effectiveness of those defenses based on testing, and even specific vulnerabilities that enable adversary behaviors. Therefore, it is crucial to establish a connection between relevant adversary behaviors and the existing defenses in order to effectively detect and respond to them.
Organizations that aim to successfully implement a Threat-Informed Defense should prioritize the use of Breach-and-Attack Simulation (BAS) systems at the core of their cybersecurity strategy. A robust BAS platform utilizes the MITRE ATT&CK framework to enhance, assess, and test threat detection and hunting efforts by simulating real-world behaviors. By continuously testing and validating security controls and analyzing performance data, CISOs and their teams gain visibility into the effectiveness of their cybersecurity program and can provide accurate reports to the board. Data-driven insights play a crucial role in making informed business decisions. These platforms allow organizations to meet the evolving challenges of the threat landscape by constantly testing and validating their security controls.
Validation efforts function as ongoing fire drills for an organization’s defenses, simulating adversary behavior and evolving defenses to adapt to the demands of a modern threat landscape. The goal is to create a comprehensive and resilient cybersecurity strategy that is rooted in evidence-based security. SOCRadar actively leverages the MITRE ATT&CK framework to track emerging cyber actors that frequently change names and forms, enabling the identification of common patterns in the evolution and transformation of TTPs and threat actors.
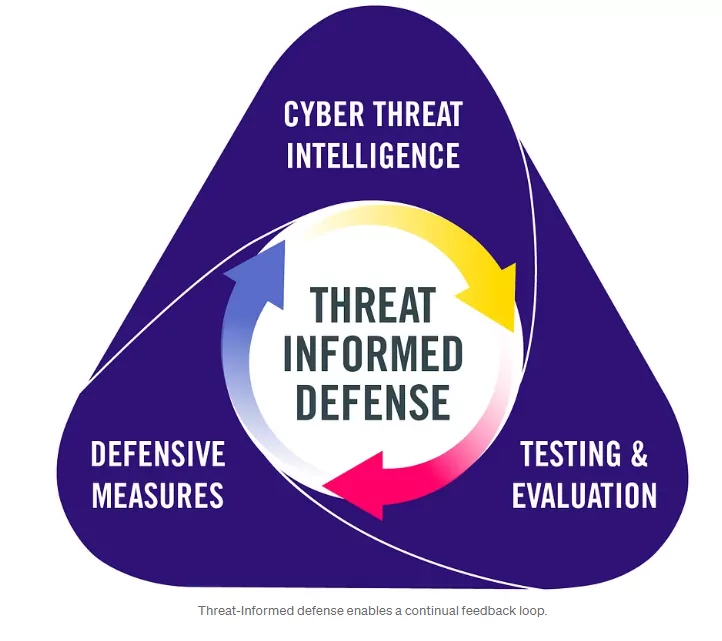
What are the key benefits of Threat-Informed Defense for organizations?
- Leveraging a Threat-Informed Defense can provide valuable insights into the current security posture of an enterprise. By analyzing known adversary behaviors, it becomes easier to identify significant gaps in enterprise defenses compared to relying solely on compliance approaches. The relatively small number of adversary behaviors allows mapping them to the team’s set of mitigating controls in frameworks such as NIST 800-53, CIS, or CMMC, as well as the protection, detection, and response capabilities provided by the cybersecurity tools deployed by the team.
- A Threat-Informed Defense approach enables clear benchmarks for evaluating existing controls and capabilities. With increased visibility into specific adversary behaviors, the team now has a roadmap for assessing the ability of its defenses to protect against, detect, and respond to those behaviors. Ideally, the team can establish a continuous testing program to automatically verify that company defenses consistently function as expected.
- While Threat-Informed Defense can significantly improve an enterprise’s security posture relative to the resources invested, it does not replace good cyber hygiene practices. Organizations still need to identify their assets,manage their configurations, and patch exploitable vulnerabilities in their systems. Threat-Informed Defense does not eliminate the need for these foundational activities but provides a critical means of assessing, prioritizing, and measuring their effectiveness. When systematically applied within an enterprise, Threat-Informed Defense enhances visibility into the effectiveness of deployed defenses and offers a clear roadmap for ongoing improvement.
- To counter these sophisticated threats, utilizing automation tocontinuously and at scale test organizations’ security controls is key to implementing a Threat-Informed Defense. Automated security control validation can leverage new threat intelligence on adversary tactics, techniques, and procedures (TTPs) through knowledge-based frameworks such as MITRE ATT&CK. This strategy allows for the deployment of assessments and adversary emulations against security controls at scale, enhancing visibility by continuously monitoring performance data and enabling organizations to assess the effectiveness of their security program.
- A relatively new security team structure is purple teaming, where testing aligns with a shared understanding of the threat landscape and the systems to be defended. Purple teaming combines red and blue teams to conduct adversary testing against an organization’s most critical controls, focusing on those most likely to impact operations. Successful purple teaming aims to share performance data after exercises, transforming traditionally siloed structures into collaborative efforts, breaking down operational barriers, and increasing cybersecurity effectiveness.
How can Threat-Informed Defense be implemented into Cyber Threat Intelligence practice?
Threat actors often require business and personal identities to launch their attacks, yet defenders have a prominent blind spot regarding the attack surface associated with employees’ and contractors’ identities. While most organizations focus on securing work identities, this fails to address a significant portion of the digital attack surface, particularly for high-value targets. Additionally, considering the large number of compromised passwords sold and shared on dark web marketplaces, a substantial proportion of these can be linked to personal identities. Therefore, it is crucial to carefully monitor this personal data, disclosed along with verified and comprehensible intelligence information.
Cyber Threat Intelligence can be combined with fragmented data to provide the necessary insights into the human attack surface, allowing for the prioritization of defenses. For instance, if a specific threat actor is conducting a social engineering campaign and you know which employees are at risk and why based on their digital footprint, you can adjust your defenses accordingly, such as implementing enhanced Multi-Factor Authentication (MFA) controls for their accounts. Similarly, if a threat actor is leveraging compromised passwords from personal accounts of employees and contractors for initial access, and you have complete visibility into your users’ compromised credentials in breach repositories, you can proactively trigger password changes and prevent their reuse.
Whether responding to social engineering attacks or other personal and sensitive data leaks, an effective defense against cyberattacks must manage the digital attack surface in conjunction with the personal attack surface. Assessing intelligence on the tactics, techniques, and procedures (TTPs) of threat actors active in your sector, along with intelligence on high-value employees within your organization (such as C-suite executives targeted by BEC (Business Email Compromise) attacks, individuals with privileged technical and financial access, and those with a high level of personal data disclosure, is essential for a threat-informed defense approach.
Combining threat intelligence with MITRE ATT&CK can offer the following benefits to cybersecurity teams as they work towards implementing threat-informed defenses:
- Identify key global threat actors targeting your industry.
- Obtain actionable information about adversaries’ operational behavior and analyze its impact on your security posture.
- Strengthen your blue and red teams by enabling a purple team approach, incorporating threat-informed defenses across all aspects of your security organization.
How can SOCRadar help your organization?
Uncovering potential threats within your digital attack surface and aligning them with your existing threat intelligence can be a time-consuming and resource-intensive process, particularly for large organizations with complex systems and multiple access points. Establishing clear boundaries for your attack surface and integrating effective vulnerability management processes is quintessential. The SOCRadar EASM (External Attack Surface Management) module addresses these challenges by discovering your digital assets, assessing your cybersecurity risks, and reducing the likelihood and impact of a successful cyber-attack. This service offers a unified view of your cyber assets, providing complete visibility into your expanding attack surface. It helps identify potential vulnerabilities by incorporating a more comprehensive and effective cybersecurity program and utilizing an attacker’s perspective to automatically identify threat signals and instances of sensitive data disclosure.
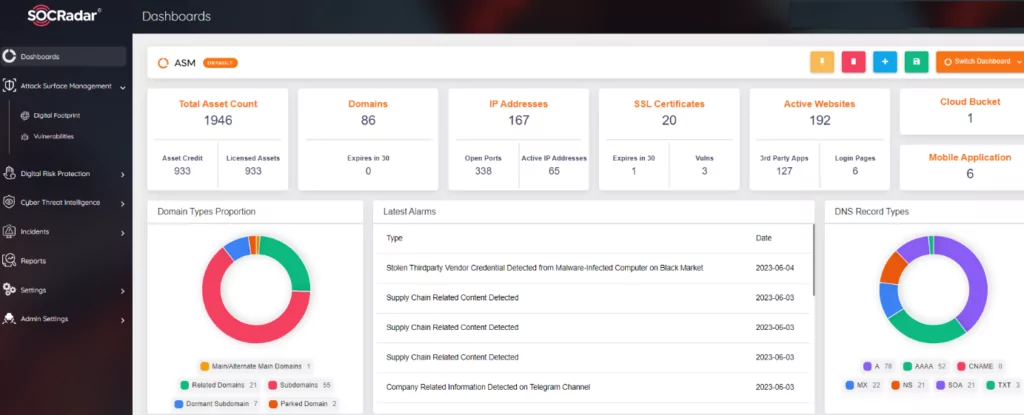
SOCRadar also offers a solution that seamlessly combines external threat intelligence with human risk mapping, empowering defenders to prioritize and mitigate corporate and individual risks. The Digital Risk Protection (DRPS) service discovers and maps your digital assets, matches them with verified intelligence from the dark web and open sources, and assists in mitigating cyber risks through services like brand protection, fraud protection, and VIP protection.
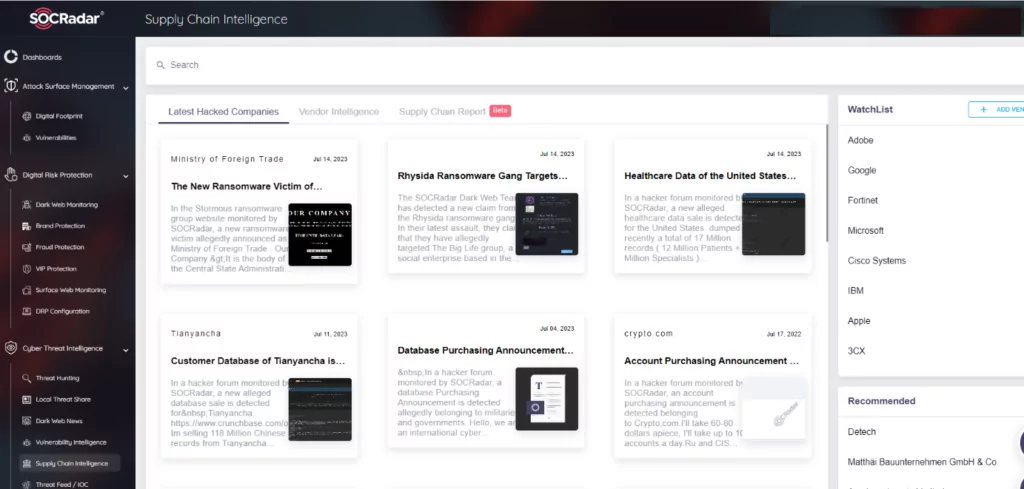
As stated in the Verizon 2023 Data Breach Investigations Report, threat actors will undoubtedly continue to exploit the human element and personal data to infiltrate organizations. SOCRadar provides a comprehensive layer of prediction and prevention against attacks that target the corporate domain and supply chain contractors. The SOCRadar Supply Chain Intelligence module can alert you to companies currently exposed to cyber-attacks and extract actionable intelligence from manufacturers’ historical cyber incidents and data breaches. Consequently, with a Threat-Informed Defense approach, companies can enhance their security, resilience, and resistance against cyber-attacks.
Conclusion
Threat-Informed Defense provides a comprehensive understanding of adversary toolkits and technologies to safeguard against, detect, and mitigate cyberattacks. While vulnerability assessments such as penetration testing and red teaming are valuable for specific use cases, they do not fully represent the actual threats an organization may encounter.
To assess and enhance cybersecurity effectively, it is necessary to employ threat intelligence-driven adversary emulation. This approach involves searching, modeling, and executing cyber adversary tactics, techniques, and procedures (TTPs).
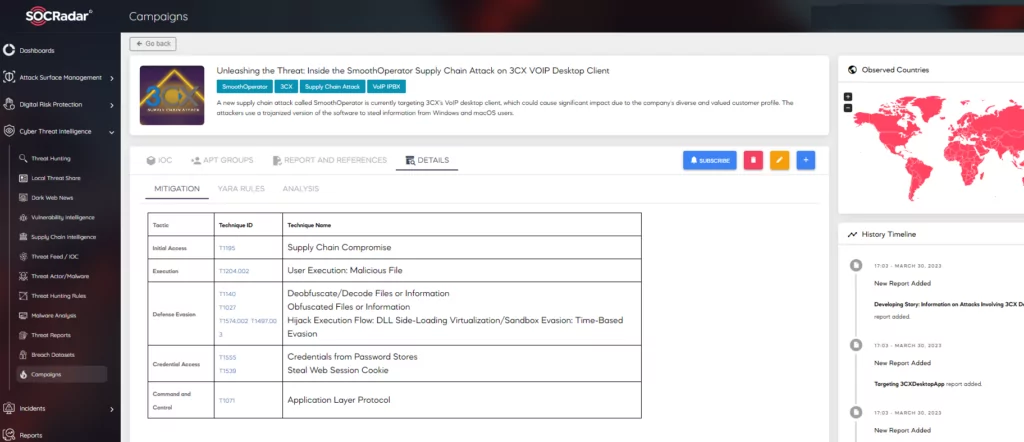
SOCRadar Campaign page is designed in line with the MITRE Campaign motivation and serves the customers. The campaigns page, which is enriched with dark web intelligence information about recent malicious campaigns, includes a group of unauthorized intrusion activities carried out over a period of time with common goals and objectives. The typical characteristic of these activities may not be directly and individually linked to a specific threat actor. Consequently, you can follow these types of real-world threat risks, which are spread over the entire cyberspace.
By combining threat intelligence with the MITRE ATT&CK framework, organizations can transition from a reactive to a proactive cybersecurity program. Adopting a Threat-Informed Defense approach enables cybersecurity teams to accurately identify the specific threats that the organization is more likelyto face. Consequently, they can implement appropriate and effective defense measures to mitigate those threats.


































