Network Devices Under Threat: Mustang Panda Targets TP-Link Routers, Critical Teltonika Vulnerabilities
The attacks targeting European foreign affairs entities since January 2023 have been attributed to a Chinese cyber espionage group, Mustang Panda. The attackers use a TP-Link firmware implant that contains a backdoor malware called “Horse Shell.” This custom firmware enables attackers to launch attacks from residential networks, not just sensitive networks.
Researchers from CheckPoint discovered the Horse Shell TP-Link firmware implant in January 2023 and reported that the attacks specifically focus on regular residential and home networks. Although attributed to Mustang Panda due to significant overlap, researchers also name the activity separately as “Camaro Dragon.”
MustangPanda: A Persistent Threat Targeting American and European Entities
Since at least 2012, the threat group known as Mustang Panda (also referred to as Camaro Dragon, RedDelta, or Bronze President) has targeted American and European organizations.
Their previous campaigns also focused on Asian countries like Taiwan, Hong Kong, Mongolia, Tibet, and Myanmar. In 2022, they used European Union and Ukrainian government reports as bait to initiate malware infection by malicious files.
The Mustang Panda attribution was based on several factors, including server IP addresses, requests with hardcoded HTTP headers on Chinese websites, typing errors in the binary code suggesting a non-native English speaker, and functional similarities to the APT31 “Pakdoor” router implant.
TP-Link Routers Hacked with Horse Shell Backdoor
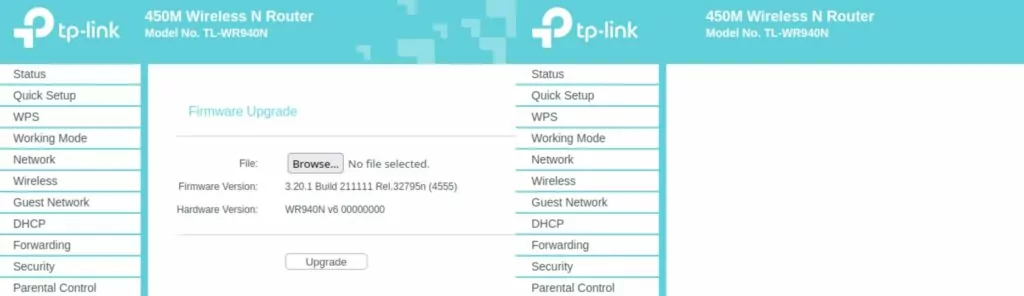
It is currently unclear how the attackers infect TP-Link routers with the malicious firmware image. According to the researchers, threat actors may be exploiting a vulnerability or brute-forcing the administrator’s credentials; once an attacker gains admin access to the management interface, they can remotely update the device with the custom firmware image.
In the most recent attacks, the threat actors used a custom firmware implant designed specifically for TP-Link routers.
The implant includes a custom backdoor called “Horse Shell” that allows attackers to maintain persistence, build anonymous infrastructure, and move laterally in compromised networks. Because of its firmware-agnostic design, the Horse Shell backdoor can be used to target different vendors’ firmware.
When the Horse Shell backdoor implant is activated, it alters the operating system’s behavior. It ensures that its process remains active even when commands like SIGPIPE, SIGINT, or SIGABRT are issued and starts operating in the background.
After activation, the backdoor establishes a connection with the command and control (C2) server. It sends a range of information, including the user name, OS version, time, device details, IP address, MAC address, and supported features of the implant.
The backdoor then waits for commands, which enable an attacker to do the following:
- Remotely execute arbitrary shell commands on the infected router.
- Transfer files to and from the infected router.
- Use SOCKS tunneling to obfuscate the origin and destination of network traffic and hide the C2 address.
The firmware also hides the version upgrade form on the TP-Link router’s management web interface. SoftwareUpgradeRpm.htm contains a web form for uploading new firmware. However, a CSS property (display:none) was added inline to the HTML form in the modified version of the firmware, which hides the form when a user enters the page. This does not remove the form or the feature from the HTML, but it makes performing the upgrade or even knowing that this feature exists more difficult.
Critical Vulnerabilities in Teltonika Networks Products Could Allow Remote Attacks
Several network equipment of another firm has been found vulnerable as well. Researchers discovered eight vulnerabilities in Teltonika Network’s routers. Three of the vulnerabilities are rated as critical, with one vulnerability being assigned the maximum CVSSv3 score of 10.0.
Which Teltonika Networks Products are Affected?
Teltonika Networks is a Lithuanian company that manufactures networking products used in a variety of industries globally. Researchers discovered the security vulnerabilities in Teltonika’s RUT241 and RUT955 cellular routers, as well as the Teltonika Remote Management System (RMS).
Affected Teltonika Networks product versions are listed below:
- Remote Management System (RMS) versions prior to 4.14.0
- RUT routers version 00.07.00-00.07.03.4
Critical Vulnerabilities in Teltonika Networks RUT Routers and Remote Management System
CVE-2023-32347 (CVSS score: 10.0): Teltonika’s RMS versions prior to 4.10.0 use device serial numbers and MAC addresses to identify devices for device claiming and authentication from both the user and device perspectives. If an attacker obtains this information, they can authenticate as that device, steal its communication credentials, and execute arbitrary commands as root.
CVE-2023-32348 (CVSS score: 9.3): Prior to 4.10.0, Teltonika’s RMS versions included an OpenVPN-based VPN hub feature for cross-device communication, allowing new devices to communicate with Teltonika devices connected to the VPN. OpenVPN server enables users to route their traffic; an attacker could elevate this to route a connection to a remote server, gaining access to data on other Teltonika devices.
CVE-2023-2586 (CVSS score: 9.0): The vulnerability affects Teltonika’s RMS version 4.14.0, allowing an unauthorized attacker to register previously unregistered devices via the RMS platform. If the user has not disabled the RMS management feature, which is enabled by default, an attacker could register that device to themselves and perform remote code execution (RCE) with root privileges via RMS’s Task Manager feature.
Teltonika has patched all its products, it is advised to refer to the vendor for updates. For more information about the Teltonika Networks vulnerabilities, visit the Cybersecurity and Infrastructure Security Agency’s (CISA) detailed advisory, which you can find here.
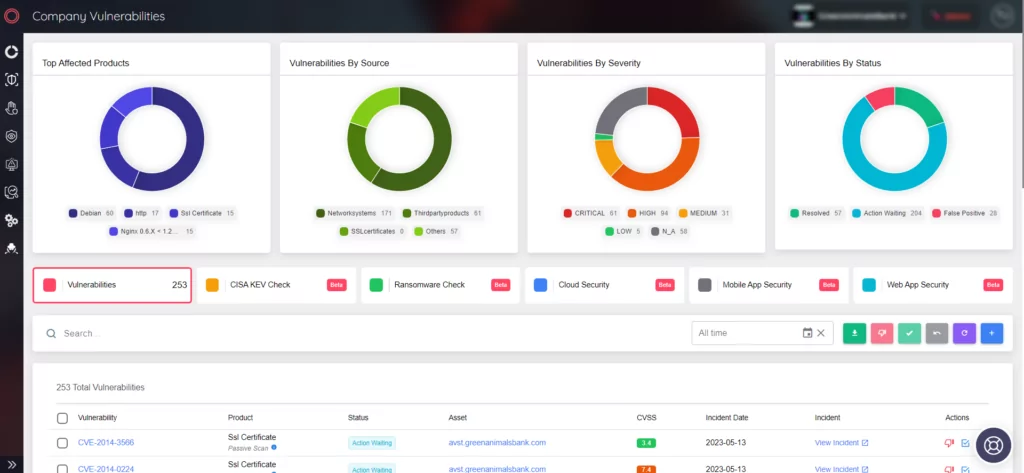
Real-time Insights: Track Vulnerabilities with SOCRadar’s Attack Surface Management
SOCRadar’s Vulnerability Intelligenceoffers valuable support in effectively managing vulnerability concerns and determining patch priorities. The platform provides the ability to search for and access comprehensive details about vulnerabilities.
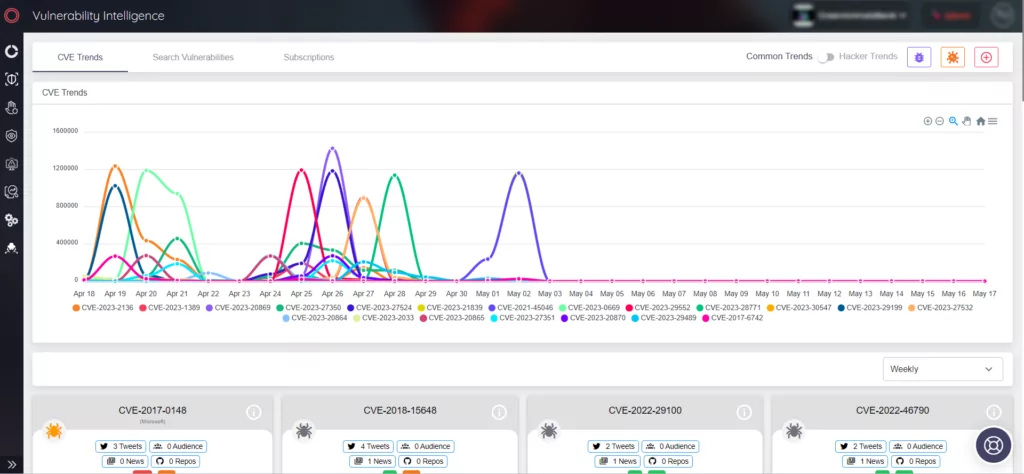
Also, with SOCRadar’s Attack Surface Management, organizations can track vulnerabilities in their digital footprint’s automatically identified products, gaining real-time insights. This proactive approach empowers security teams to prioritize vulnerabilities by leveraging contextual intelligence.