New Bulletin by CISA on Rising Vulnerabilities: Apache, BIG-IP, IBM, VMware, WordPress, and More
The Cybersecurity and Infrastructure Security Agency (CISA) released a summary of new vulnerabilities with a bulletin on October 30, 2023. These vulnerabilities were added to the National Institute of Standards and Technology (NIST), and to the CISA-sponsored National Vulnerability Database (NVD) within the past week.
In this blog post, we highlight critical and high-severity vulnerabilities featured in the CISA bulletin that may impact the cybersecurity community. Some of these vulnerabilities have already garnered attention from various media outlets and are likely to attract the interest of threat actors.
Understanding the current trend in vulnerabilities and addressing them proactively allows you to stay one step ahead of potential threats. Without further delay, let’s explore the details of these vulnerabilities.
An Overview of Critical and High-Severity Vulnerabilities in the Bulletin
Apache HTTP Server
The Apache HTTP Server Project is an open-source cross-platform web server software, designed for modern operating systems, such as UNIX and Windows.
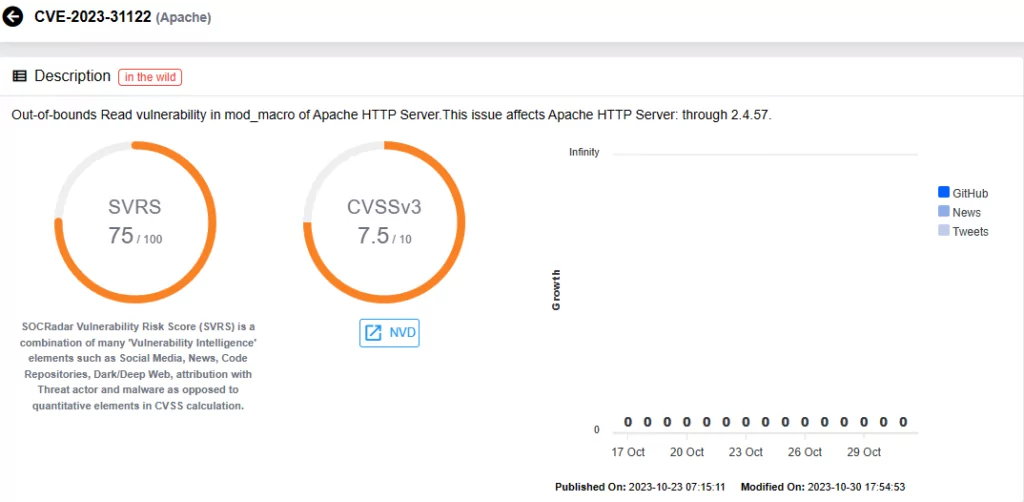
- The vulnerability found within Apache HTTP Server is tracked as CVE-2023-31122, with a CVSS score of 7.5. This vulnerability presents itself as an Out-of-bounds Read vulnerability located in mod_macro and impacts versions up to 2.4.57.
F5 BIG-IP
F5 Networks’ BIG-IP is a suite of hardware platforms and software solutions, designed to enhance application performance with a primary focus on ensuring application availability and security.
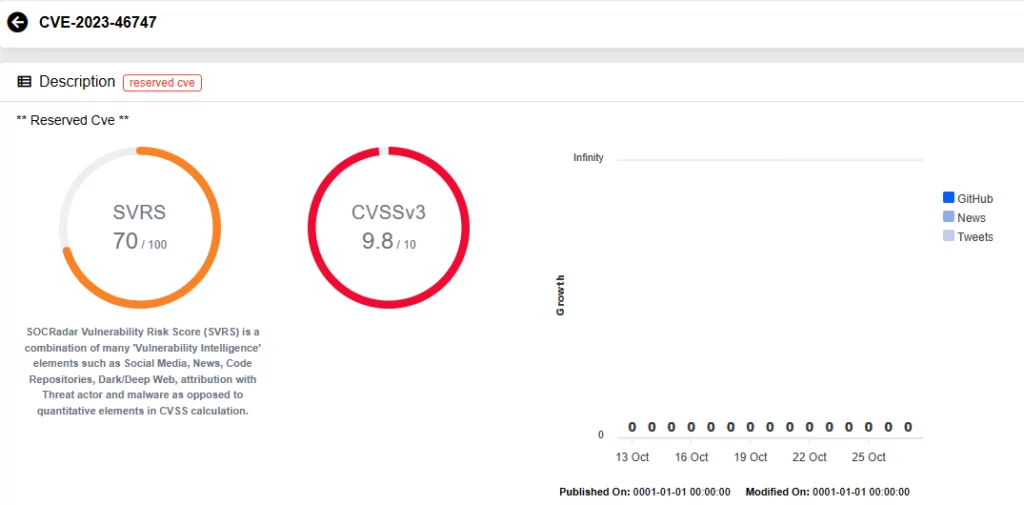
Recent scrutiny of F5 BIG-IP products unearthed two critical vulnerabilities. The first of these vulnerabilities, identified as CVE-2023-46747, permits unauthenticated remote code execution.
- CVE-2023-46747 (CVSS Score: 9.8): It allows undisclosed requests to bypass configuration utility authentication, granting an attacker with network access to the BIG-IP system through the management port and/or self IP addresses the ability to execute arbitrary system commands.
For detailed information regarding this vulnerability, refer to the linked blog post:
Another vulnerability CISA has listed in the bulletin concerning F5 BIG-IP is CVE-2023-46748.
- CVE-2023-46748 (CVSS Score: 8.8): This authenticated SQL injection vulnerability exists within the BIG-IP Configuration utility. It may allow an authenticated attacker with network access to the Configuration utility through the BIG-IP management port and/or self IP addresses to execute arbitrary system commands.
IBM Cognos Dashboards, Security Verify Governance, Sterling Partner Engagement Manager
IBM has identified several critical vulnerabilities in its software solutions:
IBM Cognos Dashboards on Cloud Pak for Data 4.7.0:
- CVE-2023-38275 (CVSS Score: 7.5): Exposes sensitive information in container images, potentially leading to system attacks.
- CVE-2023-38276 (CVSS Score: 7.5): Exposes sensitive information in environment variables, aiding possible system attacks.
IBM Security Verify Governance 10.0:
- CVE-2022-22466 (CVSS Score: 9.8): Contains hard-coded credentials used for various security functions, such as a password or cryptographic key.
- CVE-2023-33839 (CVSS Score: 8.8): Allows remote authenticated attackers to execute arbitrary commands through specially crafted requests.
- CVE-2023-33837 (CVSS Score: 7.5): Fails to encrypt sensitive information during storage or transmission.
IBM Sterling Partner Engagement Manager:
- CVE-2023-43045 (CVSS Score: 7.5): The vulnerability resides in versions 6.1.2, 6.2.0, and 6.2.2, and could allow remote unauthorized actions due to improper authentication.
QNAP QUSBCam2
QNAP QUSBCam2, a software enabling USB webcams to function as remotely-manageable IP (ONVIF) cameras, is vulnerable to:
- CVE-2023-23373 (CVSS Score: 8.8): An OS command injection vulnerability. Exploitation of this vulnerability could permit users to execute commands through a network.
VMware Fusion
VMware Fusion, a suite of Desktop Hypervisor products catering to application developers, IT professionals, and virtual machine enthusiasts, is afflicted by the following vulnerabilities in versions prior to 13.5:
CVE-2023-34045 (CVSS Score: 7.8): A local privilege escalation vulnerability, most notably occurring during installations for the first time or when upgrading. This flaw allows a malicious entity with local, non-administrative user privileges to exploit the system and elevate their privileges to root.
CVE-2023-34046 (CVSS Score: 7.0): VMware Fusion is susceptible to a TOCTOU (Time-of-check Time-of-use) vulnerability during the installation for the first time or when upgrading. A local user with non-administrative privileges can potentially harness this vulnerability to escalate their system privileges to root.
Zscaler Client Connector
Zscaler Client Connector (formerly Zscaler App/Z App) is an application deployed on end-user devices, automatically routing all user traffic through the Zscaler Zero Trust Exchange to enforce policies, access controls, and enhance performance.
The product is affected by several vulnerabilities, with the most critical being a privilege escalation vulnerability, tracked as CVE-2023-28805.
- CVE-2023-28805 (CVSS Score: 9.8): This critical vulnerability is identified in Zscaler Client Connector on Linux due to improper input validation, impacting versions prior to 1.4.0.105.
In addition, the product has two vulnerabilities that affect its Windows installers and uninstallers:
- The vulnerabilities are present in the Zscaler Client Connector Installer and Uninstaller for Windows versions before 3.6. One of them is an unquoted search path issue (CVE-2021-26735, CVSS Score: 7.8) that potentially allows local adversaries to execute code with SYSTEM privileges, while the other vulnerability (CVE-2021-26736, CVSS Score: 7.8) enables the execution of binaries from low-privileged paths, granting local adversaries code execution with SYSTEM privileges.
Furthermore, a vulnerability specific to macOS was identified:
- CVE-2021-26738 (CVSS Score: 7.8): Zscaler Client Connector for macOS versions before 3.7 contains an unquoted search path vulnerability via the PATH variable, potentially allowing a local adversary to execute code with root privileges.
Lastly, there are several vulnerabilities impacting versions before 1.3.1.6 on Linux:
- CVE-2023-28793 (CVSS Score: 7.8): A buffer overflow vulnerability in the signelf library used by Zscaler Client Connector on Linux allows code injection.
- CVE-2023-28795 (CVSS Score: 7.8): An Origin Validation Error vulnerability in Zscaler Client Connector on Linux allows the inclusion of code in an existing process, impacting versions before 1.3.1.6.
- CVE-2023-28796 (CVSS Score: 7.8): A vulnerability related to improper verification of cryptographic signatures, potentially leads to code injection.
Additionally, a Windows-specific vulnerability:
- CVE-2023-28797 (CVSS Score: 7.3): Versions prior to 4.1 writes/deletes configuration files within specific folders on the disk. Malicious users can replace the folder, executing code as a privileged user.
WordPress
The bulletin by CISA also includes a multitude of critical and high-severity vulnerabilities in WordPress. These vulnerabilities affect various services and plugins, such as Ad Inserter, Jetpack CRM, Brizy, Security & Malware scan by CleanTalk, Cyr to Lat, Horizontal scrolling announcement, Dropbox Folder Share, Icegram Express, ImageMagick Engine, PluginEver WC Serial Numbers, BEAR, Qwerty23 Rocket Font, Fancy Product Designer, Simple:Press – WordPress Forum Plugin, Soisy Pagamento Rateale, and Essential Blocks.
Most critical of the vulnerabilities in WordPress are CVE-2023-4488, CVE-2020-36706, CVE-2023-4402, and CVE-2023-5576:
- CVE-2023-4488 (CVSS Score: 9.8): Dropbox Folder Share for WordPress (up to and including version 1.9.7) has a Local File Inclusion vulnerability via editor-view.php, allowing unauthenticated attackers to execute arbitrary PHP files. This could bypass access controls, gain sensitive data, and enable code execution.
- CVE-2020-36706 (CVSS Score: 9.8): Simple:Press – WordPress Forum Plugin (up to and including version 6.6.0) permits arbitrary file uploads, lacking proper file type validation, potentially leading to remote code execution.
- CVE-2023-4402 (CVSS Score: 9.8): Essential Blocks plugin for WordPress (up to and including version 4.2.0) is vulnerable to PHP Object Injection due to untrusted input deserialization, enabling unauthenticated attackers to inject a PHP Object. A presence of a POP chain via other plugins or themes may facilitate file deletion, data retrieval, or code execution.
- CVE-2023-5576 (CVSS Score: 9.3): Migration, Backup, Staging – WPvivid plugin for WordPress (up to and including version 0.9.91) exposes Google Drive API secrets in plaintext within its public source, potentially allowing unauthenticated attackers to impersonate the WPVivid Google Drive account through social engineering.
To see all the vulnerabilities featured in the bulletin, refer to the official website of CISA.
Utilize SOCRadar XTI to Effectively Combat Security Vulnerabilities
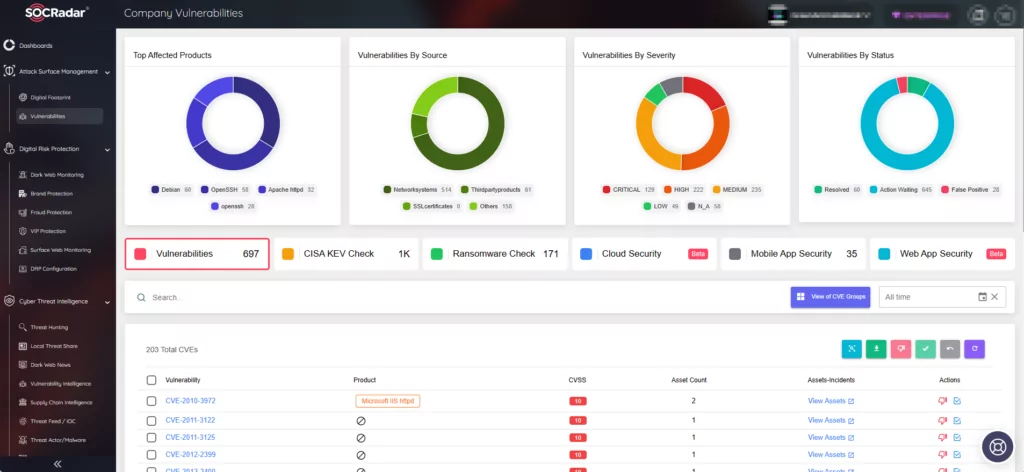
With the Attack Surface Management (ASM) module, proactively monitor emerging vulnerabilities across your digital assets, receive timely threat alerts, and better manage patching efforts to enhance your security posture.
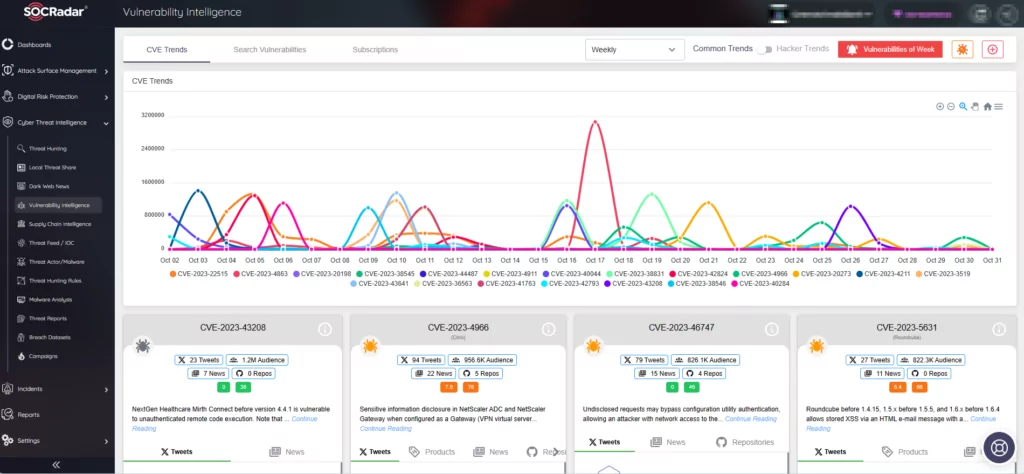
For further insights, updates, and hacker trends related to identified vulnerabilities, leverage SOCRadar’s Vulnerability Intelligence. The module provides specific details about vulnerabilities and their SOCRadar Vulnerability Risk Score (SVRS), offering a better understanding of their popularity and potential for exploitation.