
New on Dark Web: Epic Games Recruitment Post, Poseidon Stealer, Coinbase Phishing Kit
The SOCRadar Dark Web Team has discovered several new cyber threats over the last week. Notable dark web posts include a job posting aimed at Epic Games employees, an Israeli chemical manufacturing company’s unauthorized network access sale, the sale of the Poseidon Stealer, and the release of a new Coinbase phishing kit. In addition, credit card numbers from the United States are being sold.
Receive a Free Dark Web Report for Your Organization:
An Alleged Unauthorized Network Access Sale is Detected for an Israeli Chemical Manufacturing Company
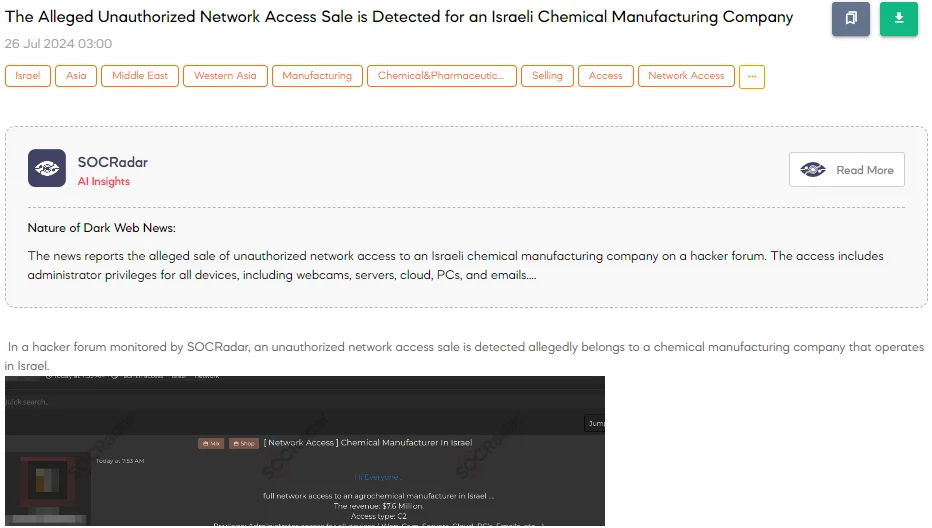
The SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to have unauthorized network access to an Israeli chemical manufacturing company. In the post, the threat actor alleges that they have gained full network access to an agrochemical manufacturer based in Israel. They emphasize that the company has a reported revenue of $7.6 million, suggesting a significant potential impact.
The access type is described as Command and Control (C2), which indicates a high level of control over the compromised network. Moreover, the threat actor claims to possess administrator privileges for all devices within the network, including web interfaces, cameras, servers, cloud services, PCs, and emails. The post concludes with an invitation for potential buyers to message the threat actor to negotiate a deal.
Poseidon Stealer is Allegedly on Sale
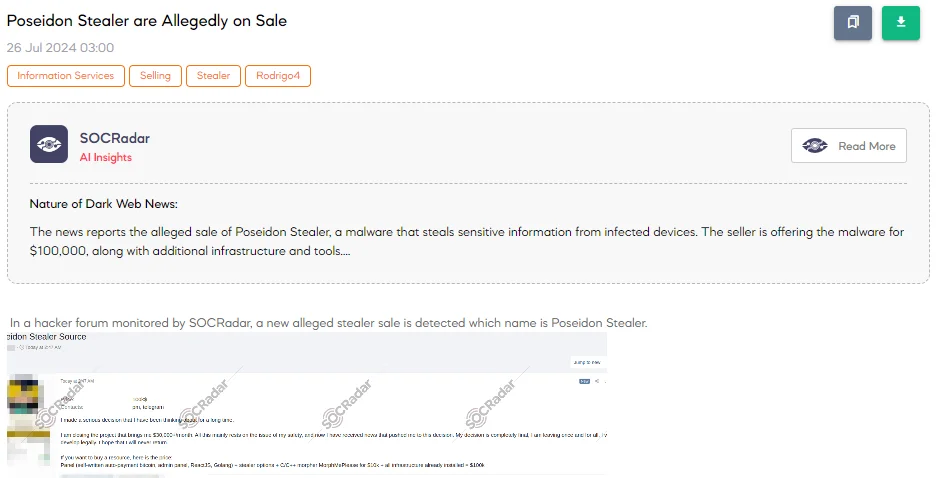
The SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor is selling a stealer called Poseidon Stealer for $100,000. In the post, the actor explains that they have made a serious decision to close the project, which has been generating over $30,000 per month, primarily due to concerns for their safety. The sale includes the Poseidon Stealer panel with a self-written auto-payment Bitcoin system, admin panel, ReactJS, Golang, stealer options, and the C/C++ morpher MorphMePlease.
A New Coinbase Phishing Kit is Leaked
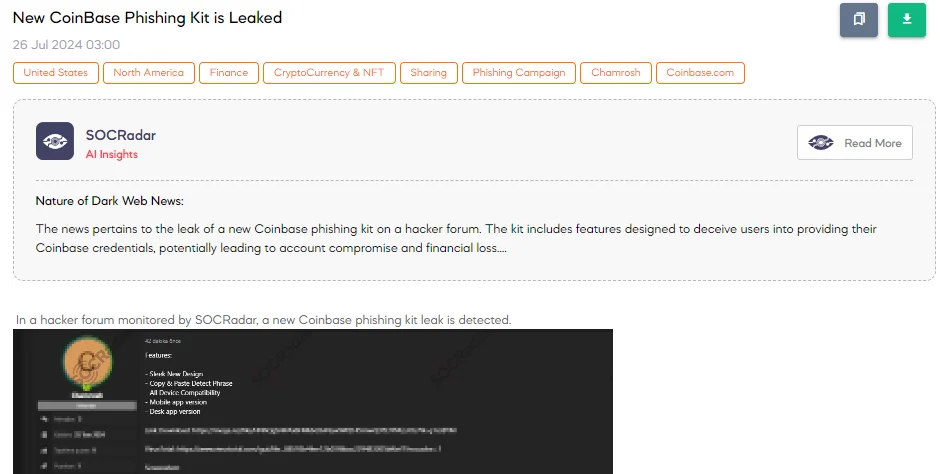
The SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor has leaked a new Coinbase phishing kit. According to the threat actor, this phishing kit includes several advanced features: a sleek new design that closely mimics the legitimate Coinbase website, a copy & paste detect phrase to prevent users from copying and pasting their passwords, and compatibility with all devices, ensuring effectiveness across smartphones, tablets, and desktop computers. Additionally, the kit includes dedicated versions for both mobile and desktop applications, allowing seamless execution of the phishing attack on any platform.
140K Credit Cards Belonging to the United States are on Sale
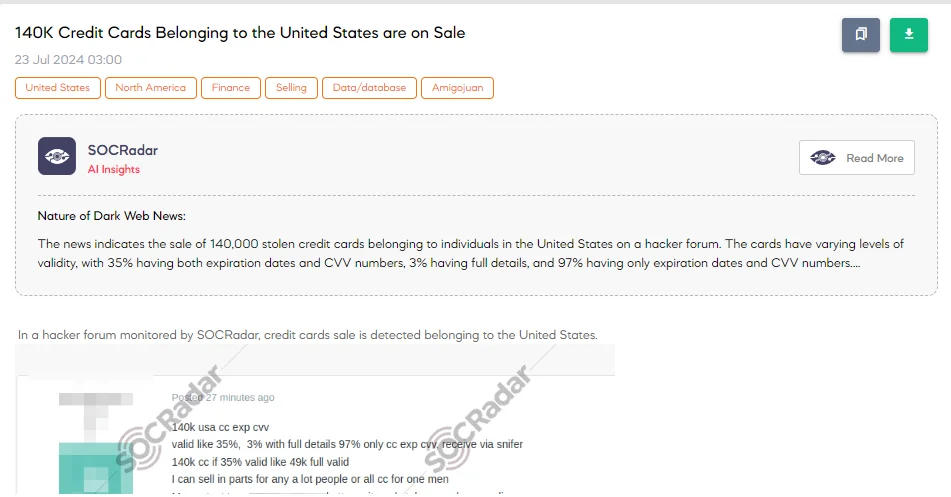
The SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claimed to be selling credit card details belonging to individuals in the United States. The post advertises a sale of 140,000 credit card numbers, with an asserted validity rate of 35%, equating to approximately 49,000 fully valid cards. The threat actor states that 3% of these cards come with complete details, while the remaining 97% include only the card number, expiration date, and CVV.
According to the post, these details were obtained using a sniffer. The starting price for the entire batch is $28,000, with bids increasing in increments of $1,000, and an instant purchase option available for $33,000. The seller indicates a willingness to sell the cards in smaller lots or as a whole and prefers to be contacted via Telegram, claiming to be always online and fluent in both Russian and English. This post highlights the ongoing threat of credit card fraud and the sophisticated techniques employed by cybercriminals to monetize stolen data.
New Recruitment Post is Detected for Employees of Epic Games
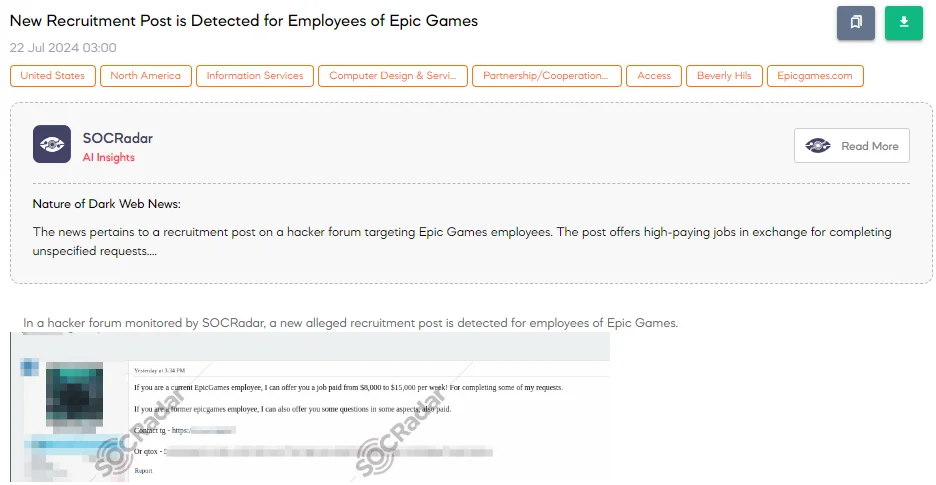
The SOCRadar Dark Web Team detected a post on a hacker forum where a new alleged recruitment post targets employees of Epic Games. The threat actor is offering a job to current Epic Games employees with payments ranging from $8,000 to $15,000 per week for completing certain requests. Additionally, former employees are also being targeted with paid inquiries related to specific aspects of their previous employment. C
Contact methods provided include Telegram and qTox, which are often used for secure and anonymous communication. This post specifically aims to recruit both current and former employees, suggesting tasks that likely involve sensitive or potentially illegal activities related to Epic Games’ internal operations or data. The high payment offered indicates the significant value placed on the expected information or actions.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































