Nitrogen: A Malware Campaign Leveraging Search Ads
Researchers have uncovered a new initial access malware campaign dubbed “Nitrogen”. This campaign employs Google and Bing search ads to promote fake software sites.
The primary objective of the Nitrogen malware is to provide threat actors with initial access to corporate networks. This is accomplished through the use of fake sites, infecting unsuspecting users with Cobalt Strike and ransomware payloads. As part of the campaign, threat actors can engage in data theft and cyberespionage, and eventually deploy the BlackCat (ALPHV) ransomware.
How Does Nitrogen Malware Infect Networks?
The Nitrogen malware campaign begins when a user searches for various popular software applications, such as AnyDesk, Cisco AnyConnect VPN, TreeSize Free, and WinSCP, on Google or Bing. The attackers use these well-known software products as a masquerade to infiltrate victim networks.
Trend Micro was the first to document activity related to Nitrogen malware, observing WinSCP ads leading to BlackCat ransomware infections.
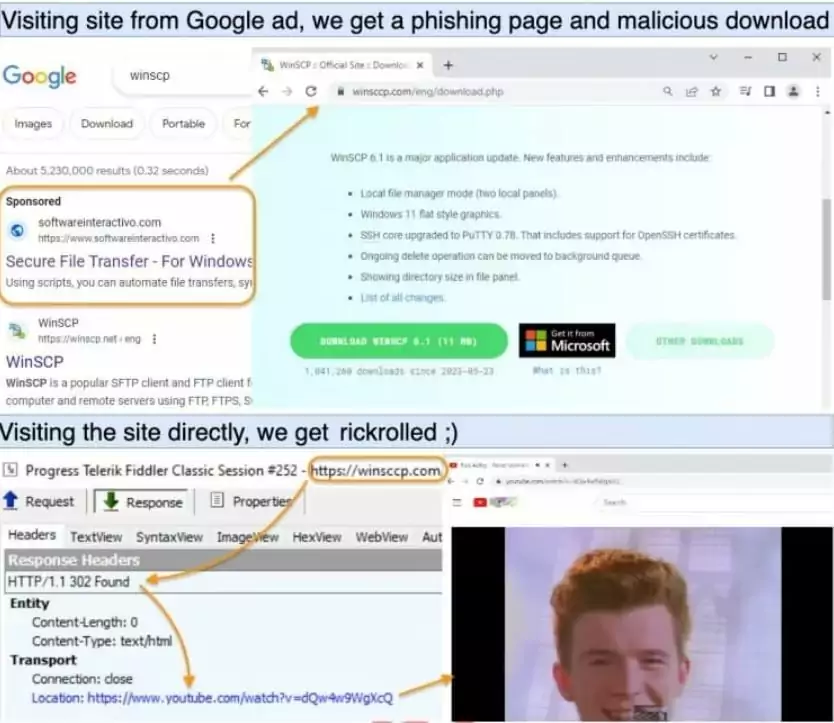
The search engine displays an advertisement for a phishing page promoting the software that was searched for. Phishing sites are exclusively presented to visitors from specific geographic regions, and when they click the link, they are redirected to compromised WordPress hosting pages that look like legitimate software download sites.
A recent report by Sophos revealed that Nitrogen campaign’s main targets are technology and non-profit organizations in North America. Visitors who click the fake URLs directly, and not visit it via Google/Bing ads promoted in the target region, are redirected to rick-rolling YouTube videos (an internet prank involving Rick Astley’s “Never Gonna Give You Up” music video).
Users accessing the fake sites unknowingly download trojanized ISO installers, which sideload a malicious DLL file named msi.dll. The msi.dll serves as the installer for the Nitrogen initial access malware, called “NitrogenInstaller.” It installs a promised app and a malicious Python package to avoid suspicion.
For persistence, the NitrogenInstaller creates a registry run key named “Python,” pointing to a malicious binary (“pythonw[.]exe”), which runs every five minutes.
The Python component runs “NitrogenStager” (“python.311.dll”) to communicate with the threat actor’s C2, launching a Meterpreter shell and Cobalt Strike Beacons on the victim’s system.
In some cases, attackers perform manual commands to get additional ZIP files and Python 3 environments for executing Cobalt Strike in memory. Because, NitrogenStager cannot run Python scripts.
The threat actor’s goal remains unknown, but the infection chain suggests they may stage compromised systems forransomware deployment. In at least one case, this attack chain led to the deployment of the BlackCat ransomware, as reported by Trend Micro.
Recommendations
This campaign is not the first instance of ransomware gangs exploiting search engine ads for initial access to corporate networks. Users are advised to avoid clicking on “promoted” search results when downloading software and instead only download from the developer’s official site.
Additionally, users should be cautious with software distributed using ISO files, as this is an uncommon method for legitimate Windows software distribution (usually .exe or .zip archives).
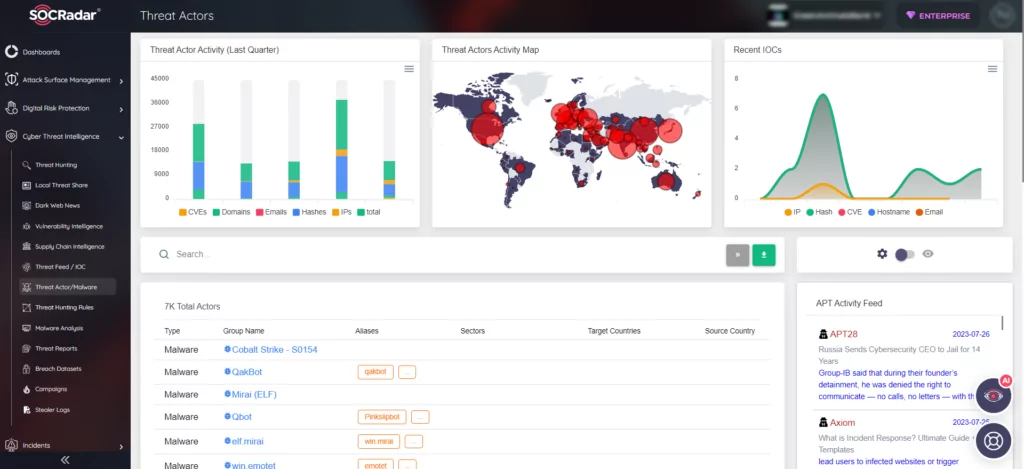
Stay Ahead of Adversaries: SOCRadar’s Threat Actor & Malware Tracking
Threat actors and advanced persistent threat (APT) groups utilize a diverse array of tools and strategies to achieve their objectives. Gaining a comprehensive understanding of these adversaries and dynamically monitoring their activities can offer invaluable insights into their current tactics, techniques, and procedures (TTPs).
At SOCRadar, we utilize automated data collection, classification, and AI-driven analysis across various sources on the surface, deep, and dark web. By doing so, we keep you constantly informed and alerted about the activities of APT groups. Armed with this critical information, you can develop more effective use cases to detect and prevent their malicious activities.
Our Threat Actor & Malware panel is continuously updated, ensuring you have access to the latest information about threat actors and malwares. With the capability for in-depth examination and analysis, SOCRadar empowers you to stay ahead and proactively protect your organization against potential threats.