
Massive OpenAI Leak, WordPress Admin Exploit, Inkafarma Data Breach
SOCRadar’s Dark Web Team has detected a wave of cyber threats on hacker forums this week, including an alleged leak of millions of OpenAI user accounts. Meanwhile, a WordPress admin exploit script, WPU 2.0, is being sold, offering features to bypass security measures and manipulate websites. Additionally, unauthorized VPN access to a U.S. oil and gas company is up for sale, while U.S. credit cards are being offered. In Peru, pharmaceutical company Inkafarma has reportedly suffered a breach, with customer records now on the Dark Web. These incidents highlight ongoing risks across industries and platforms.
Receive a Free Dark Web Report for Your Organization:
Alleged Script of WordPress Checker is on Sale
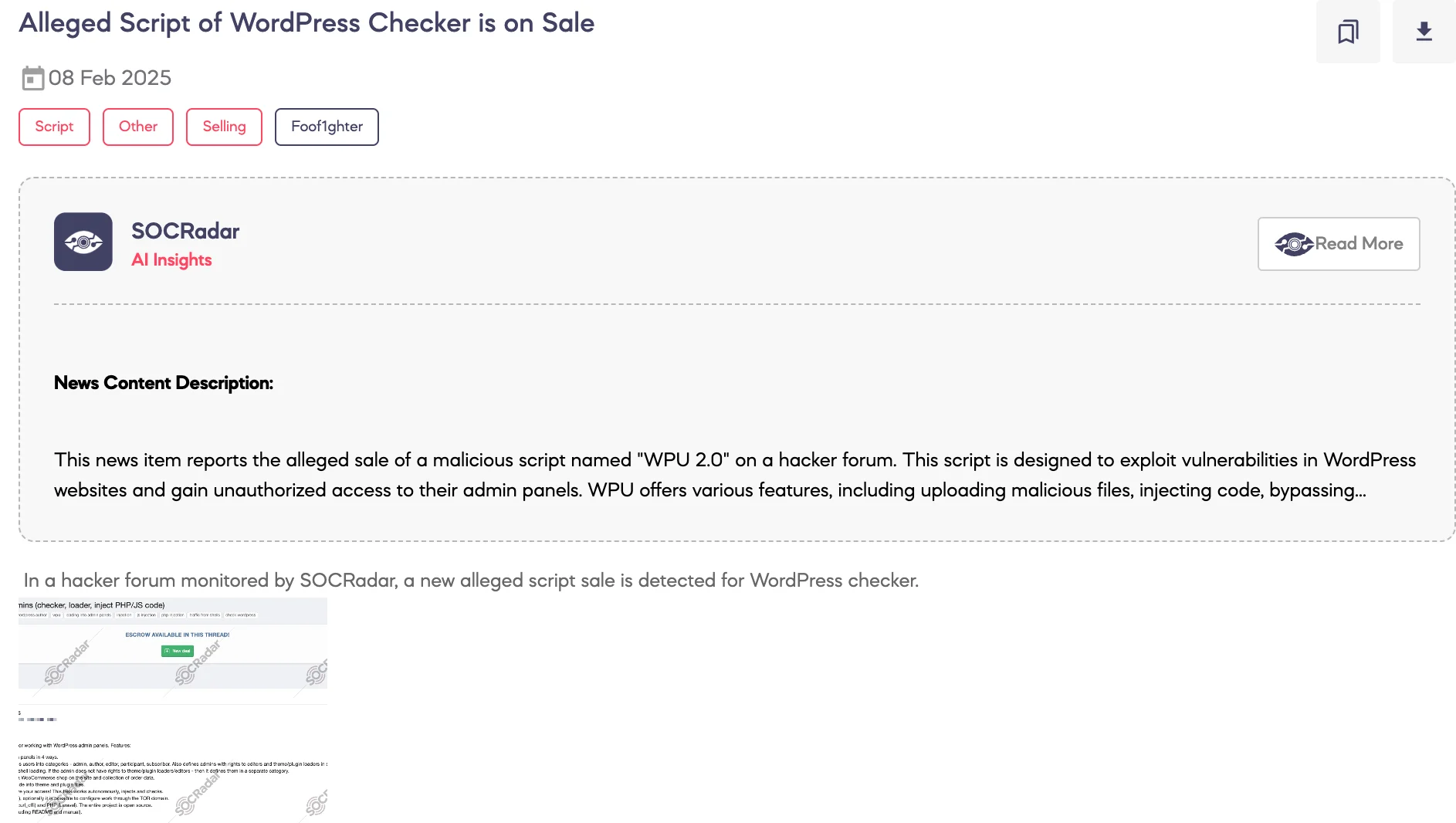
SOCRadar Dark Web Team detected a post on a hacker forum advertising the sale of an alleged script named WPU 2.0, designed for unauthorized activities targeting WordPress admin panels. According to the threat actor, the script is priced at $2,000, with a one-year update plan included. It offers extensive functionalities, including PHP file uploads, access rights checking, JavaScript and PHP code injection, WooCommerce data collection, and the ability to bypass Web Application Firewalls (WAFs) like Cloudflare and Imunify360.
The threat actor also claims that the script is written in Python PHP , and includes features such as captcha-solving, proxy management, disabling popular security plugins, and autonomous re-uploading of injected code. It also supports integration with TOR networks for increased anonymity.
Alleged Account Codes of OpenAI are Leaked
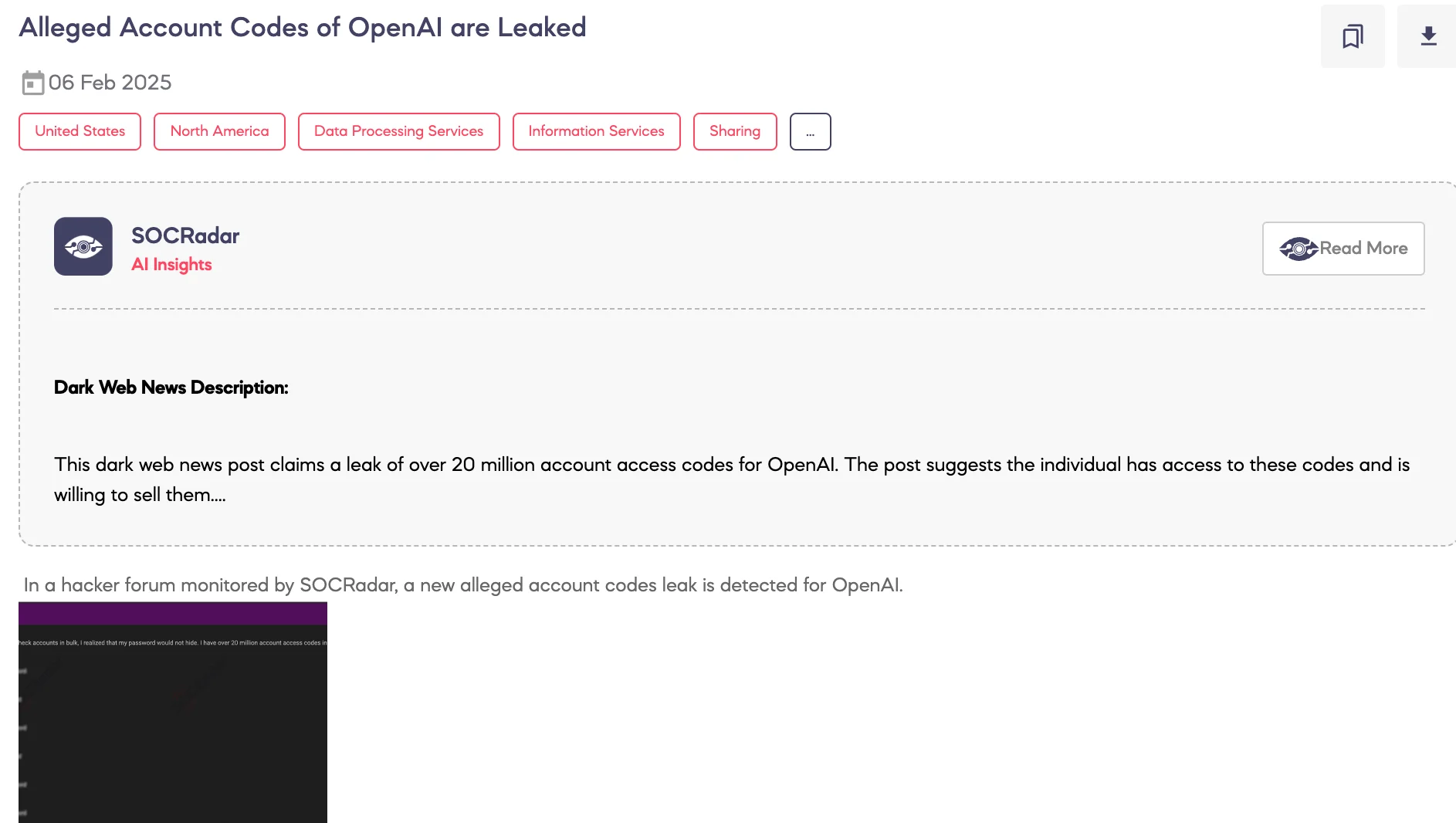
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to have leaked over 20 million user authentication credentials allegedly associated with OpenAI accounts. The threat actor alleges that these credentials were obtained by exploiting vulnerabilities related to OpenAI’s bulk account verification processes. The dataset is described as highly valuable, with the actor inviting interested parties to establish contact for further details.
Alleged 1,000 Credit Cards Belonging to the United States are on Sale
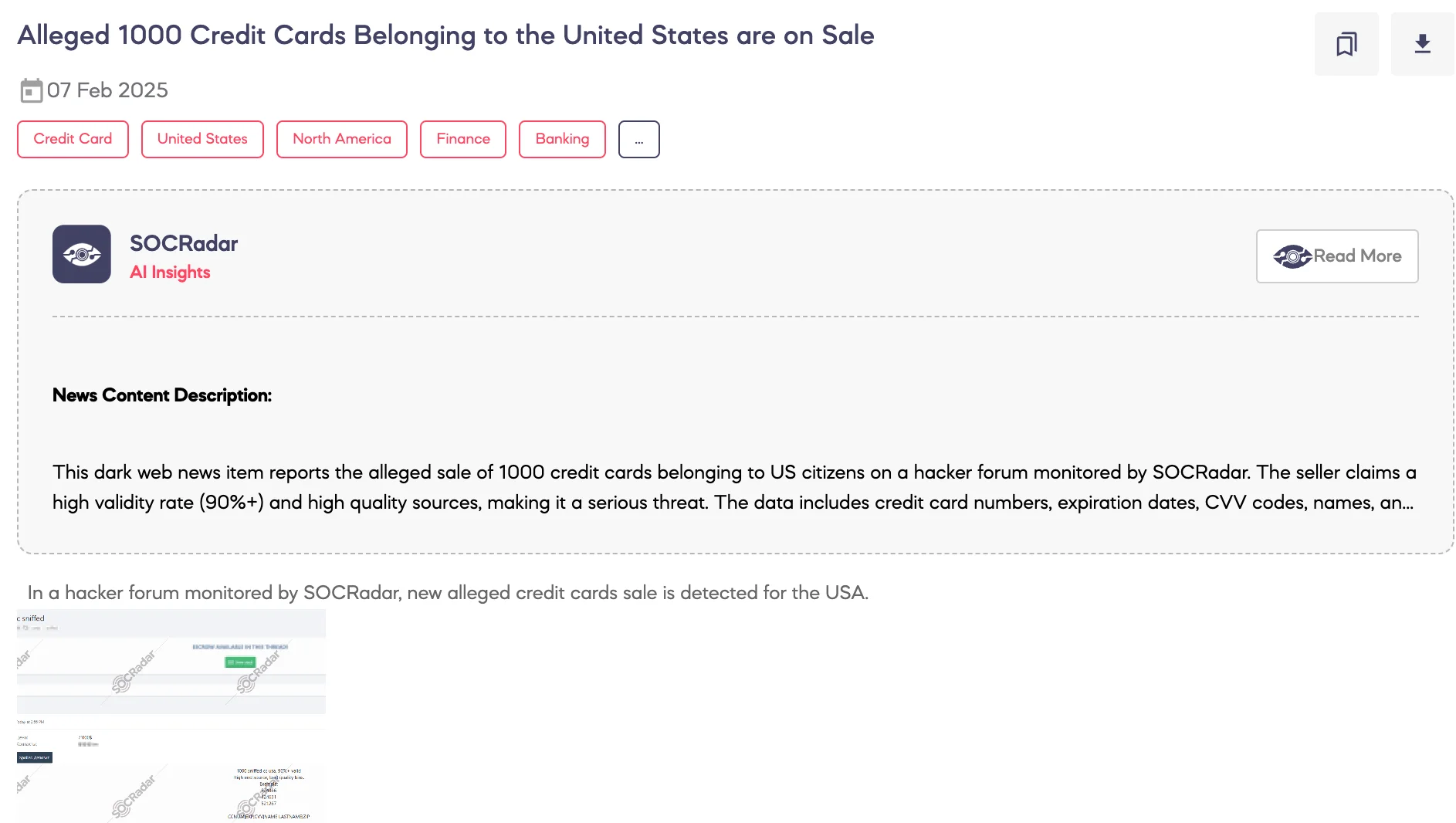
SOCRadar Dark Web Team detected a post on a hacker forum in which a threat actor claims to be offering for sale 1,000 allegedly compromised credit card records associated with individuals in the United States. The threat actor asserts that the data was obtained through sniffing techniques and claims a validity rate exceeding 90%. The dataset reportedly includes credit card numbers, expiration dates, CVV codes, cardholder names, and ZIP codes. The asking price for the dataset is $7,000.
Alleged Customer Database of Inkafarma is on Sale
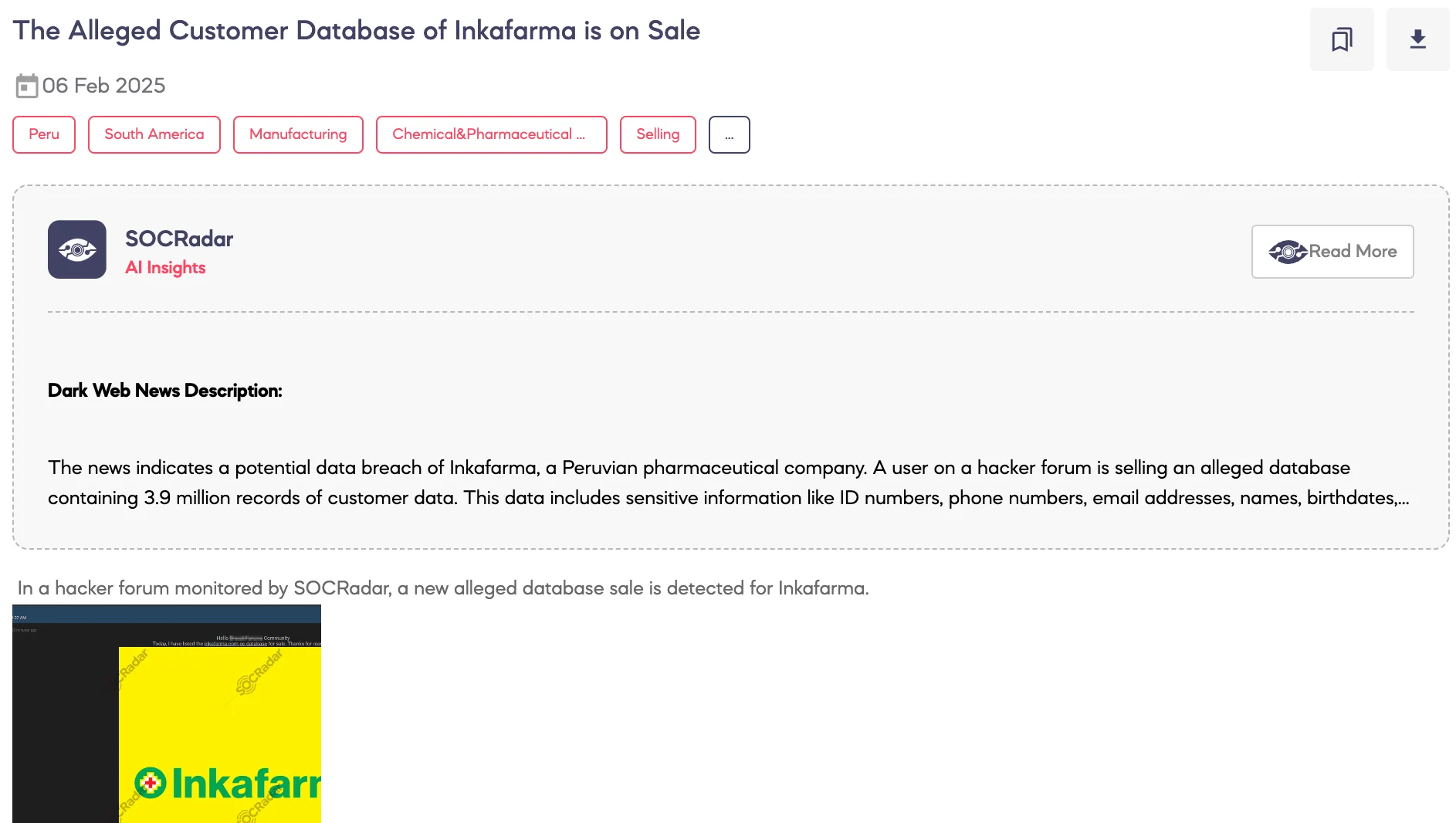
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to be selling the alleged customer database of Inkafarma, a pharmaceutical company based in Peru. According to the threat actor, the breach occurred on February 6, 2025, and affects approximately 3.9 million records. The dataset reportedly includes sensitive customer information such as identification numbers (DNI), phone numbers, email addresses, names, birthdates, and other personal details.
Alleged Unauthorized VPN Access Sale is Detected for an American Oil & Gas Company
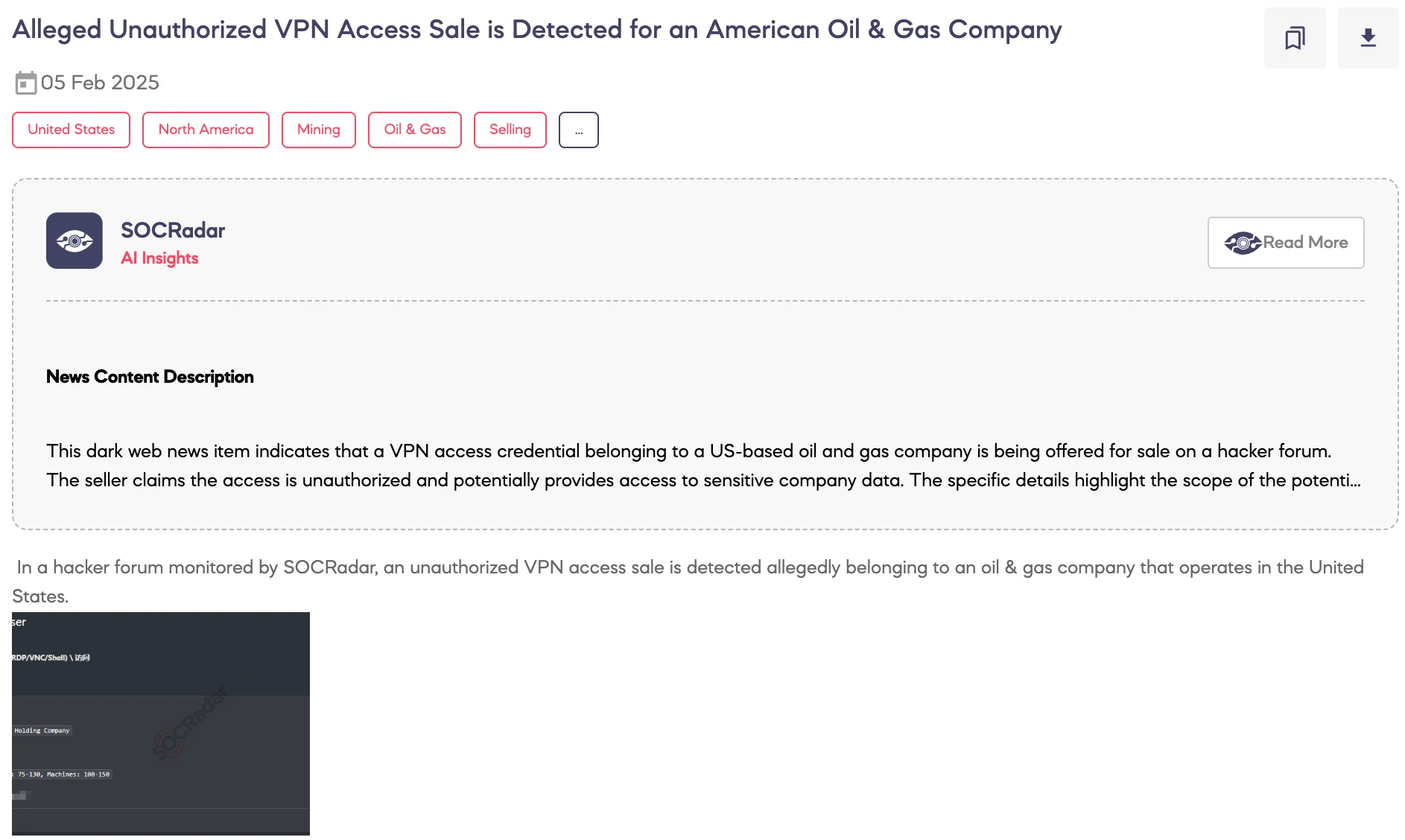
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to be selling unauthorized VPN access allegedly belonging to an oil and gas holding company operating in the United States. According to the threat actor, the access provides domain user-level privileges within the company’s network, which reportedly includes 75 to 130 active user accounts and 100 to 150 machines. The company’s revenue is claimed to be between $25 million and $40 million. The asking price for this unauthorized access is $500, with contact details provided for potential buyers.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.


































