P2Pinfect: A Worm-Like Botnet Malware Targeting Redis Deployments
[Update] June 26, 2024: “P2PInfect Botnet: Recent Developments and Ransomware Deployment”
Researchers have identified an unknown group of hackers employing a novel strain of malware named “P2Pinfect” to target publicly-accessible deployments of Redis. This popular data storage tool is extensively used by major companies, including Amazon, Uber, and Hulu.
P2Pinfect demonstrates advanced techniques, including cross-platform compatibility using Rust, sophisticated replication, and a peer-to-peer botnet structure. Notably, what sets this malware apart is its worm-like behavior, enabling it to self-propagate and infect other vulnerable Redis deployments autonomously, thereby expanding its botnet.
P2Pinfect Targets Linux and Windows by Exploiting the Replication Feature in Redis
Palo Alto’s Unit 42 initially analyzed the hacking campaign, revealing the malware’s exploitation of the critical Lua sandbox escape vulnerability, CVE-2022-0543 (CVSS score: 10.0), to hijack Redis applications and incorporate them into a botnet. This vulnerability was previously used to add devices into Muhstik botnet in 2022. However, the P2Pinfect malware is distinct from Muhstik and appears to belong to a different malicious network, as determined by Unit 42.
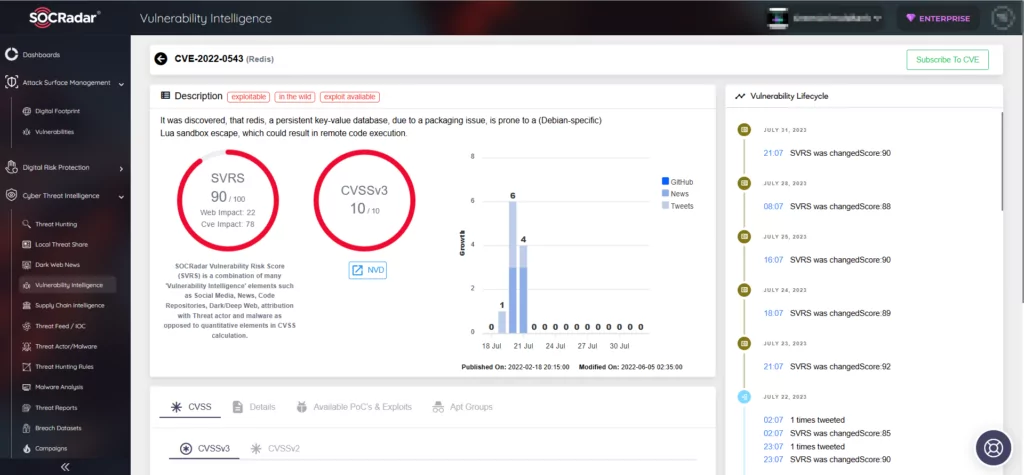
Cado Security also issued a report that largely aligns with Unit 42’s findings. Once connected to a host, the malware attempts to infect other hosts, expanding the botnet. Nevertheless, Cado Security identified two significant differences. First, the encountered malware sample did not employ CVE-2022-0543 as the initial access vector, but used the replication feature. Second, P2Pinfect targeted both Windows and Linux Redis instances.
The replication feature enables Redis instances to run in a distributed manner, forming a leader/follower topology where follower nodes exactly replicate the leader. The feature is intended to ensure high availability and data store failover in Redis; however, by exploiting it, the attacker gains access to the target’s Redis deployment. This allows them to load a malicious shared object file (exp.so) and obtain reverse shell access.
The Distribution of the Botnet Malware
The malware serves a dual purpose: it prevents other threat actors from compromising the Redis server while allowing it to function normally, so the owners remain unaware of the compromise. Once infected, the server becomes part of a peer-to-peer botnet, enabling communication between infected hosts without a centralized control server. The malware spreads further by gathering user information, IP addresses, and SSH access keys. Once it gains access to a host, it infects it by dropping a copy of itself and executing it with a list of nodes as an argument.
The Payloads of P2Pinfect
The primary payload of P2Pinfect comprises an ELF binary written in C and Rust. This payload is responsible for manipulating the host’s SSH configuration to enable backdoor access while employing iptables to permit legitimate Redis operators and block other threat actors.
Both security firms emphasized that P2Pinfect’s use of the Rust programming language facilitated seamless operation on Windows and Linux platforms while complicating code analysis.
P2Pinfect drops and executes a binary named “bash,” mimicking a legitimate instance of bash. It monitors processes and automatically restarts the main payload if it gets terminated. Additionally, a binary named “miner” is dropped, but it seems to remain inactive. Experts speculate that this file may serve as a placeholder for a future crypto miner, potentially activating once the botnet grows to a specific size.
Despite extensive research, the identity of the perpetrators and their ultimate goal remains unknown.
A Growing Peer-to-Peer Botnet Threat
Cado Security researchers discovered several Redis exploits being used for initial access. The malware conducts internet scans to find vulnerable Redis servers and then replicates itself in a manner similar to a worm. The attackers exploit the replication feature of Redis, which allows them to compromise exposed instances of the data store. This type of attack has been observed since 2018 in other cloud malware campaigns.
Unit 42 identified over 307,000 unique Redis systems communicating publicly in the last two weeks, with about 934 of them possibly being vulnerable to the worm variant. While most systems are not vulnerable, P2Pinfect will likely still attempt to compromise them. The number of infected hosts is growing, but the exact size of the P2Pinfect botnet is unknown.
Organizations should prioritize securing critical ports by closing, filtering or restricting access to certain source assets either on the asset serving the port or on the perimeter, such as firewalls.
P2PInfect Botnet: Recent Developments and Ransomware Deployment
Since our last update on August 1, 2023, the P2PInfect botnet has seen significant changes, evolving with new capabilities and posing an increased threat level. Initially discovered in July 2023, the botnet malware has now expanded its reach and introduced several new features, and its most recent attempts involve deploying ransomware.
In 2023, between August and September, P2PInfect showed a notable increase in breach attempts and introduced new persistence mechanisms, communication systems, and lockout capabilities. Then, in December, researchers identified a new variant for 32-bit MIPS processors, targeting routers and IoT devices, further extending the botnet’s reach.
Fast-forward to 2024, P2PInfect has progressed to deploying ransomware on infected devices and incorporating a user-mode rootkit. Additionally, there are speculations that it might be operating as a ‘botnet for hire,’ which significantly raises its threat potential.
Activation of Ransomware and Cryptocurrency Miner
Reportedly, on May 16, 2024, devices in P2PInfect’s botnet were commanded to download and execute a ransomware payload named ‘rsagen.’ Cado Security reports that the command will continue to be active until December 17, 2024.
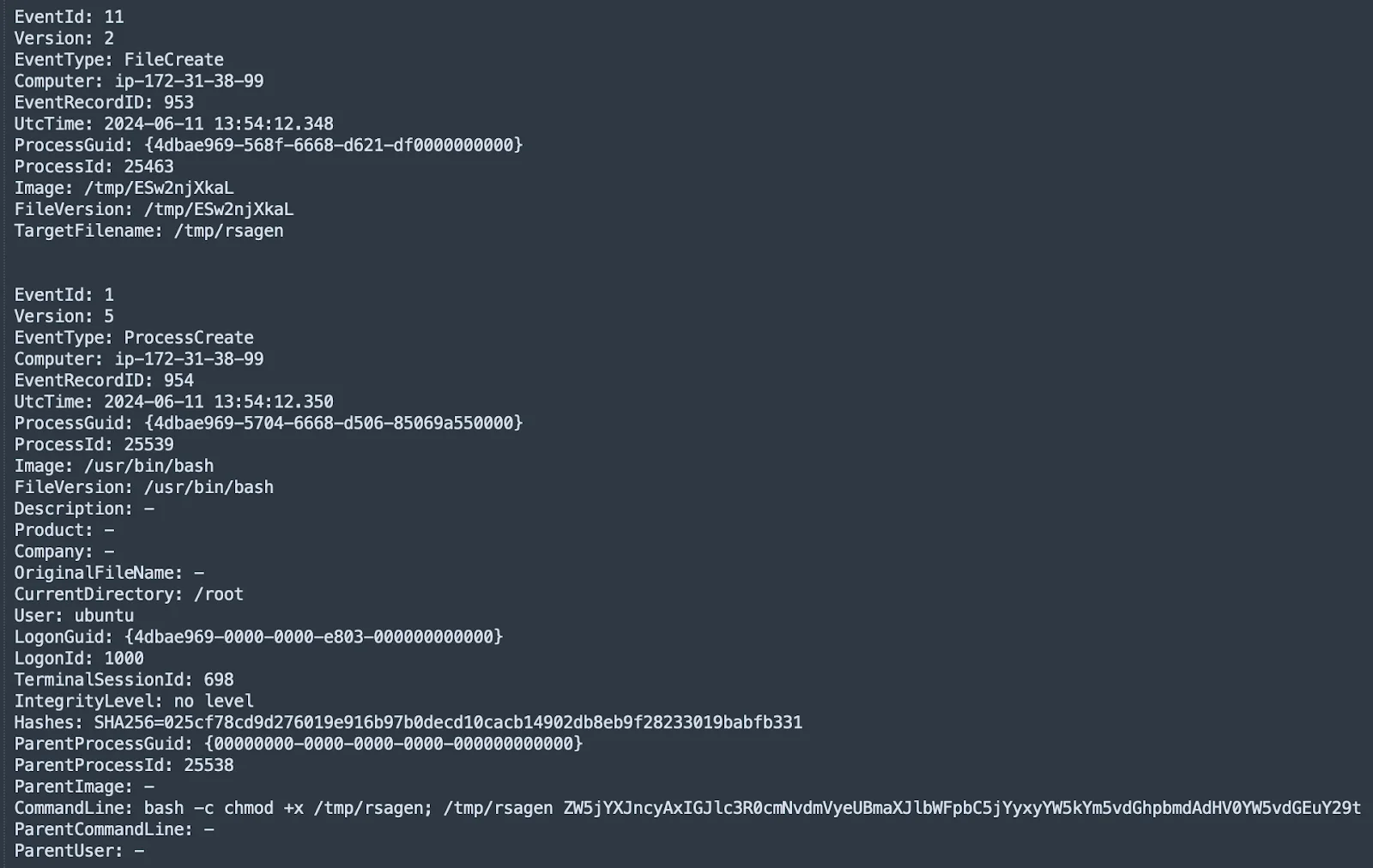
The download and execution of the ransomware file (Cado)
This ransomware encrypts files such as databases, documents, and media, appending the ‘.encrypted’ extension. It checks for a ransom note titled “Your data has been locked!.txt” to avoid re-encrypting compromised systems.
The ransomware mainly affects files accessible to the Redis user, with Redis typically being in-memory, limiting the range of files that can be encrypted. It stores a database of encrypted files in a temporary file with the ‘.lockedfiles’ extension.
Additionally, a previously dormant Monero (XMR) miner embedded in P2PInfect has been activated. The miner drops into a temporary directory and starts five minutes after the primary payload, using all available processing power, often interfering with the ransomware module’s operation.
Introduction of a User-Mode Rootkit
P2PInfect incorporated a user-mode rootkit aimed at concealing its malicious processes and files from security tools. This rootkit accomplishes its stealth by hijacking several processes.
While it is theoretically capable of hiding file operations and network connections, its effectiveness is restricted because Redis generally operates in memory.
P2PInfect May Be a Botnet for Hire
Cado researchers speculate that P2PInfect might be a botnet for hire due to the ransomware payload being delivered via a fixed URL command, allowing operators to deploy arbitrary payloads.
Supporting this theory are different wallet addresses for the cryptocurrency mining malware and ransomware, suggesting separate entities, and the miner’s resource-intensive operation, which interferes with the ransomware. The generic download and run command for ‘rsagen’ also contrasts with the custom command set for the miner.
However, contradictions exist, such as both the main P2PInfect binary and ‘rsagen’ being compiled with the same compiler string and both payloads being written in Rust, indicating a single author.
P2Pinfect IoCs (Indicators of Compromise)
| Filename | SHA256 |
| linux | 87a3fc1088449dbd3554fe029a1878a525e64ab4ccf71b23edb03619ba94403a |
| miner | b1fab9d92a29ca7e8c0b0c4c45f759adf69b7387da9aebb1d1e90ea9ab7de76c |
| bash | ce047893ac5bd2100db3448bd62c324e471ffcddd48433788bfe885e5f071a89 |
Indicators of Compromise (IoCs) Related to P2Pinfect’s Ransomware Deployment
Hashes
main
- 4f949750575d7970c20e009da115171d28f1c96b8b6a6e2623580fa8be1753d9
bash
- 2c8a37285804151fb727ee0ddc63e4aec54d9460b8b23505557467284f953e4b
miner
- 8a29238ef597df9c34411e3524109546894b3cca67c2690f63c4fb53a433f4e3
rsagen
- 9b74bfec39e2fcd8dd6dda6c02e1f1f8e64c10da2e06b6e09ccbe6234a828acb
libs.so.1
- Dynamically generated, no consistent hash
IPs
Download server for rsagen
- 129[.]144[.]180[.]26:60107
Mining pool IPs
- 88[.]198[.]117[.]174:19999
- 159[.]69[.]83[.]232:19999
- 195[.]201[.]97[.]156:19999
YARA Rules
Main
Cado warns that the main binary is UPX packed, and this rule only applies when unpacked.
rule P2PinfectMain {
meta:
author = "[email protected]"
description = "Detects P2Pinfect main payload"
strings:
$s1 = "nohup $SHELL -c "echo chmod 777 /tmp/"
$s2 = "libs.so.1"
$s3 = "SHELLzshkshcshsh.bashrc"
$s4 = "curl http:// -o /tmp/; if [ ! -f /tmp/ ]; then wget http:// -O /tmp/; fi; if [ ! -f /tmp/ ]; then ; fi; echo && /tmp/"
$s5 = "root:x:0:0:root:/root:/bin/bash(?:([a-z_][a-z0-9_]*?)@)?(?:(?:([0-9]\.){3}[0-9]{1,3})|(?:([a-zA-Z0-9][\.a-zA-Z0-9-]+)))"
$s6 = "/etc/ssh/ssh_config/root/etc/hosts/home~/.././127.0::1.bash_historyscp-i-p-P.ssh/config(?:[0-9]{1,3}\.){3}[0-9]{1,3}"
$s7 = "system.exec "bash -c \"\"""
$s8 = "system.exec """
$s9 = "powershell -EncodedCommand"
$s10 = "GET /ip HTTP/1.1"
$s11 = "^(.*?):.*?:(\d+):\d+:.*?:(.*?):(.*?)$"
$s12 = "/etc/passwd.opass123456echo -e "" | passwd && echo > ; echo -e ";/bin/bash-c" | sudo -S passwd"
condition:
uint16(0) == 0x457f and 4 of them
}Bash
Cado warns that the bash binary is UPX packed, and this rule only applies when unpacked.
rule P2PinfectBash {
meta:
author = "[email protected]"
description = "Detects P2Pinfect bash payload"
strings:
$h1 = { 4C 89 EF 48 89 DE 48 8D 15 ?? ?? ?? 00 6A 0A 59 E8 17 6C 01 00 84 C0 0F 85 0F 03 00 00 }
$h2 = { 48 8B 9C 24 ?? ?? 00 00 4C 89 EF 48 89 DE 48 8D 15 ?? ?? ?? 00 6A 09 59 E8 34 6C 01 00 84 C0 0F 85 AC 02 00 00 }
$h3 = { 4C 89 EF 48 89 DE 48 8D 15 ?? ?? ?? 00 6A 03 59 E8 DD 6B 01 00 84 C0 0F 85 DF 03 00 00 }
condition:
uint16(0) == 0x457f and all of them
}
XMRig Miner
rule XMRig {
meta:
attack = "T1496"
description = "Detects XMRig miner"
strings:
$ = "password for mining server" nocase wide ascii
$ = "threads count to initialize RandomX dataset" nocase wide ascii
$ = "display this help and exit" nocase wide ascii
$ = "maximum CPU threads count (in percentage) hint for autoconfig" nocase wide ascii
$ = "enable CUDA mining backend" nocase wide ascii
$ = "cryptonight" nocase wide ascii
condition:
5 of them
}rsagen
rule P2PinfectRsagen {
meta:
author = "[email protected]"
description = "Detects P2Pinfect rsagen payload"
strings:
$a1 = "$ENC_EXE$"
$a2 = "$EMAIL_ADDRS$"
$a3 = "$XMR_COUNT$"
$a4 = "$XMR_ADDR$"
$a5 = "$KEY_STR$"
$a6 = "$ENC_DATABASE$"
$b1 = "mdbmdfmydldfibdmyidbdbfwdbfrmaccdbsqlsqlite3msgemltxtcsv123docwpsxlsetpptppsdpsonevsdjpgpngziprar7ztarbz2tbkgztgzbakbackupdotxlwxltxlmxlcpotpubmppodtodsodpodgodfodbwpdqpwshwpdfaip64xpsrptrtfchmmhthtmurlswfdatrbaspphpjsppashcppccspyshclassjarvbvbsps1batcmdjsplsuoslnbrdschdchdipbmpgificopsdabrmaxcdrdwgdxfmbpspdgnexbjnbdcdqcdtowqxpqptsdrsdtpzfemfociiccpcbtpfgjdaniwmfvfbsldprtdbxpstdwtvalcadfabbsfccfudfftfpcfdocicaascgengcmostwkswk1onetoc2sntedbhwp602sxistivdivmxgpgaespaoisovcdrawcgmtifnefsvgm4um3umidwmaflv3g2mkv3gpmp4movaviasfvobmpgwmvflawavmp3laymmlsxmotguopstdsxdotpwb2slkdifstcsxcots3dm3dsuotstwsxwottpemp12csrcrtkeypfxder"
$c1 = "lock failedlocked"
$c2 = "/root/homeencrypt"
condition:
uint16(0) == 0x457f and (2 of ($a*) or $b1 or all of ($c*))
}
libs.so.1
rule P2PinfectLDPreload {
meta:
author = "[email protected]"
description = "Detects P2Pinfect libs.so.1 payload"
strings:
$a1 = "env_var"
$a2 = "main_file"
$a3 = "hide.c"
$b1 = "prefix"
$b2 = "process1"
$b3 = "process2"
$b4 = "process3"
$b5 = "owner"
$c1 = "%d: [0-9A-Fa-f]:%X [0-9A-Fa-f]:%X %X %lX:%lX %X:%lX %lX %d %d %lu 2s"
$c2 = "/proc/net/tcp"
$c3 = "/proc/net/tcp6"
condition:
uint16(0) == 0x457f and (all of ($a*) or all of ($b*) or all of ($c*))
}
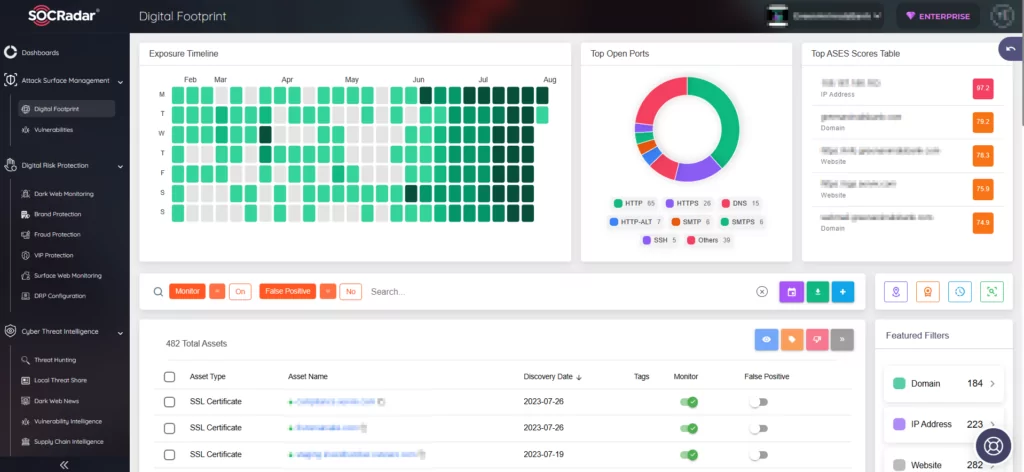
How Can SOCRadar Help?
SOCRadar offers continuous monitoring of digital assets, promptly generating alarms for any emerging threats. This proactive approach strengthens overall security and ensures prompt detection of potential exposures or vulnerabilities affecting your assets, including Redis deployments.
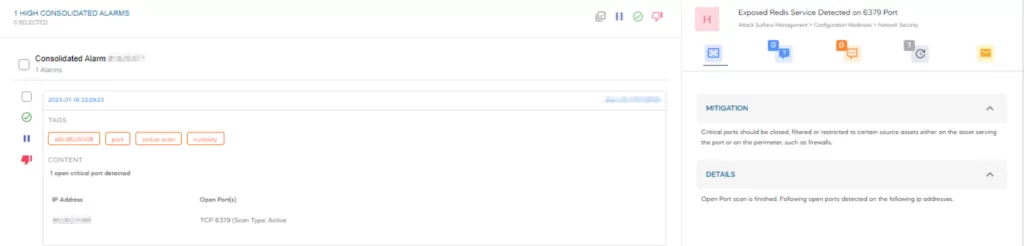
You can monitor organizational assets and efficiently manage alarms by using SOCRadar’s Attack Surface Management (ASM) module.