
Pro-Russian APT Group Cadet Blizzard Targets Ukraine with WhisperGate Wiper Attacks
Ongoing investigations into Russia’s invasion of Ukraine have revealed insights into the tactics and tools used by Russian state-sponsored threat actors. These actors exhibit varying levels of sophistication and impact, showcasing their adaptability in hybrid warfare.
A significant development occurred on June 14 with the identification of a key Russian state-sponsored threat actor involved in the invasion’s lead-up. This marks a milestone in the fight against Russian state-sponsored cybercrime.
The APT group “Cadet Blizzard,” previously known as DEV-0586, played a crucial role from January to June of the preceding year, contributing to the invasion.
Microsoft has connected Cadet Blizzard to Russia’s GRU military intelligence agency and shared detailed information about their activities, including website defacements and the use of the destructive tool “WhisperGate” to render computer systems inoperable. These attacks preceded subsequent waves of attacks by another Russian group, Seashell Blizzard, following the Russian military’s ground offensive.
Who is Cadet Blizzard?
Cadet Blizzard is a Russian GRU-sponsored threat group that Microsoft has been tracking since disruptive events in Ukrainian government agencies in mid-January 2022.
They engage in website defacements and use the WhisperGate malware. Cadet Blizzard maintains control over compromised networks, exfiltrating data before launching attacks.
Apart from the operations against Ukraine, Cadet Blizzard’s activities demonstrate a diverse range of targets. Alongside using a unique wiper and defacement of government websites, the group actively manages a Telegram channel called “Free Civilian” and conducts attacks across Europe, Central Asia, and Latin America. Their targets extend beyond government agencies and encompass IT service providers, software supply chain manufacturers, non-government organizations, emergency services, and law enforcement agencies.
How Does Cadet Blizzard Operate?
Cadet Blizzard conducts disruptive operations as public signals to achieve destruction, disruption, and intimidation; it is not concerned with remaining undetected, unlike other Russian-affiliated espionage groups.
The group gains initial access to targets through well-known vulnerabilities in Internet-facing Web servers like Microsoft Exchange and Atlassian Confluence. Once inside a network, they move laterally, acquiring credentials and escalating privileges, and establishing persistence using Web shells. Their objectives include stealing sensitive data and deployingWhisperGate, their destructive malware.
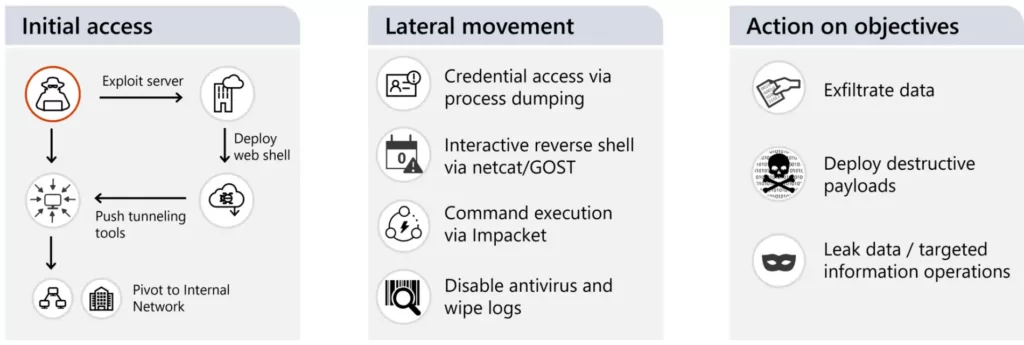
However, Cadet Blizzard is not as proficient as other GRU-affiliated groups like Seashell Blizzard (Iridium) and Forrest Blizzard (Strontium). While Seashell Blizzard’s wiper attacks affected over 200 systems in February 2022, Cadet Blizzard’s WhisperGate attack in January 2022 had a significantly smaller impact.
Cadet Blizzard’s activity peaked between January and June 2022, followed by a weakening period before resurfacing in early 2023. Compared to their GRU counterparts, Cadet Blizzard’s recent cyber operations have not achieved the same level of impact. Microsoft’s assessment also reveals that Cadet Blizzard operates with lower operational security compared to established Russian groups with advanced capabilities.
Stay Informed and Analyze Threat Actors with SOCRadar
By regularly updating its knowledge base, the Threat Actor panel on SOCRadar enables users to stay up-to-date with the latest information regarding threat actors. Moreover, this panel provides the opportunity for a comprehensive analysis of threat actors, offering detailed insights.
Indicators of Compromise Related to Cadet Blizzard
Microsoft has listed IoCs (Indicators of Compromise) to identify Cadet Blizzard threat activity. For more information and related threat-hunting queries, refer to Microsoft’s blog.
Domain:
- justiceua[.]org – Sender for non-weaponized emails containing only antagonistic messaging: volodimir_azov@justiceua[.]org
IP Address:
- 179.43.187[.]33 – Hosted the JusticeUA operation between March and April 2022
PE Import Hash:
- 3a2a2de20daa74d8f6921230416ed4e6 – Matches WhisperGate malware
SHA-256 Hash:
- 3e4bb8089657fef9b8e84d9e17fd0d7740853c4c0487081dacc4f22359bade5c – Web shell (p0wnyshell)
- 20215acd064c02e5aa6ae3996b53f5313c3f13625a63da1d3795c992ea730191 – Web shell (p0wnyshell)
- 3fe9214b33ead5c7d1f80af469593638b9e1e5f5730a7d3ba2f96b6b555514d4 – Web shell (WSO Shell)
- 23d6611a730bed886cc3b4ce6780a7b5439b01ddf6706ba120ed3ebeb3b1c478 – Web shell (reGeorg)
- 7fedaf0dec060e40cbdf4ec6d0fbfc427593ad5503ad0abaf6b943405863c897 – Web shell (PAS)
Tools Cadet Blizzard has commonly used in malicious activities include:
- Tor
- Python
- SurfShark
- Teamviewer
- dbus-rpc[.]exe Meterpreter in known instances
- IVPN
- NGROK
- GOST[.]exe (often masked as USORead[.]exe)
- reGeorg web shell




































