
Securing the Digital Gateways: The Ivanti Sentry Vulnerability (CVE-2023-38035)
[Update] August 25, 2023: See the subheadings: “Proof-of-Concept (PoC) Exploit Available for the Ivanti Sentry Zero-Day,” and “CISA Warns for Active Exploitation of CVE-2023-38035.”
In the ever-evolving realm of cybersecurity, vulnerabilities continue to emerge, reminding us of the constant need for vigilance. Recently, a significant vulnerability has been unearthed, sending ripples across the cybersecurity landscape. This revelation brings to the forefront CVE-2023-38035, a significant vulnerability that impacts Ivanti Sentry, previously recognized as MobileIron Sentry.
Now, let’s dig deep into the intricacies of this flaw and unravel its potential consequences.
Unmasking the Ivanti Vulnerability: CVE-2023-38035
Published on August 21, 2023, on the forums.ivanti.com, the vulnerability labeled CVE-2023-38035 poses a serious threat to Ivanti Sentry users, specifically impacting versions 9.18 and prior. However, it is important to note that this vulnerability does not extend its reach to other Ivanti products like Ivanti EPMM or Ivanti Neurons for MDM. The heart of the matter lies in the unauthenticated actor’s ability to exploit sensitive APIs used for configuring Ivanti Sentry on the administrator portal.
The vulnerability primarily targets the administrator interface accessible through port 8443, commonly referred to as MICS, and has a critical CVSS score of 9.8 on Ivanti’s advisory. While the CVSS score indicates high severity, the actual risk is lower for users who do not expose port 8443 to the internet. In the hands of malicious actors, this flaw could lead to configuration alterations, execution of system commands, and unauthorized file writes.
The Anatomy of Exploitation
At its core, CVE-2023-38035 stems from an insufficiently restrictive Apache HTTPD configuration within the MICS Admin Portal. This loophole enables an unauthenticated attacker to bypass authentication controls on the administrative interface. The consequence? A potential compromise of the Sentry system and underlying operating systems. The gravity of this vulnerability becomes evident when considering that a successful exploitation could empower malicious actors to execute OS commands as root.
Shielding Against the Threat: Apply RPM Scripts Provided by Ivanti

To address this vulnerability, Ivanti promptly released RPM scripts tailored to each supported version of Sentry, including 9.18, 9.17, and 9.16. The process involves a careful application of the correct RPM script corresponding to the version in use. However, a word of caution: deploying an incorrect RPM script might hinder the remediation process or even lead to system instability.
For those using the affected versions, Ivanti recommends applying the appropriate RPM script to safeguard against potential exploitation. Moreover, to further mitigate risks, restricting external access to the System Manager Portal on port 8443 is recommended. Organizations are urged to keep this portal accessible only through internal management networks, ensuring that only authorized IT administrators can access it.
Proof-of-Concept (PoC) Exploit Available for the Ivanti Sentry Zero-Day
Horizon’s research has unveiled a Proof-of-Concept (PoC) that showcases the exploitation of the recently discovered vulnerability in Ivanti Sentry. This PoC sheds light on the technical intricacies of the vulnerability, emphasizing the potential risks associated with it.
The researchers devised the PoC exploit through patch diffing. They conducted a thorough comparison between Ivanti Sentry versions 9.12 and 9.18, which led to the identification of a removed service within the “remoting-servlet.xml” file. Additionally, they noted that the endpoint related to “services/” lacked authentication requirements.
Delving deeper into their investigation, they eventually leveraged an exposed endpoint to execute arbitrary commands, bypassing any authentication.
CISA Warns for Active Exploitation of CVE-2023-38035
CISA has added the CVE-2023-38035 vulnerability in Ivanti Sentry to its Known Exploited Vulnerabilities (KEV) catalog, underlining the significance of the ongoing security risk.
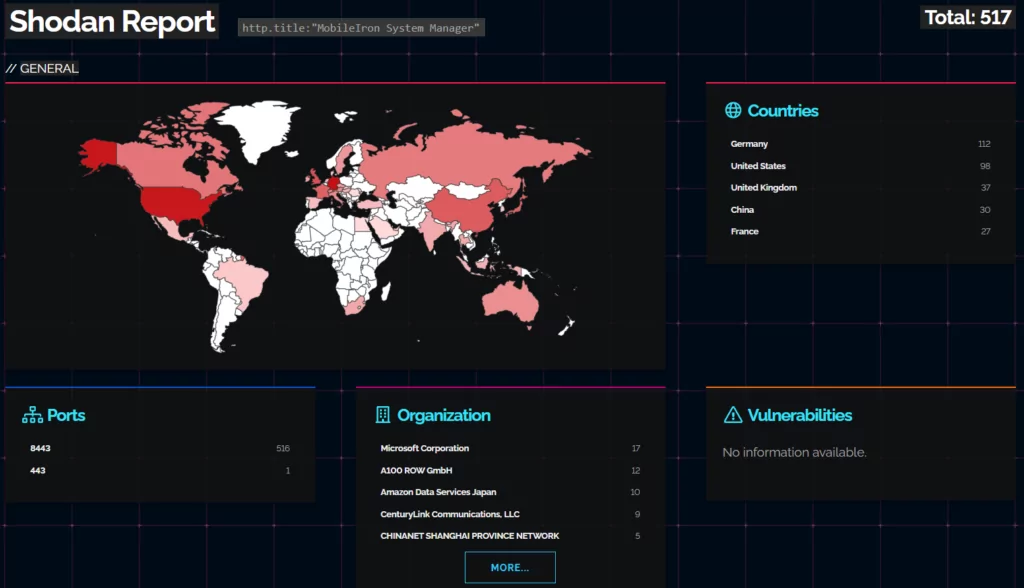
Here is a Shodan search, showing Ivanti Sentry instances that are currently accessible on the internet:
Facing the Future: Leveraging SOCRadar Vulnerability Intelligence
As we navigate the intricate web of vulnerabilities, solutions emerge. One such solution is the utilization of advanced cybersecurity tools like SOCRadar’s Vulnerability Intelligence and External Attack Surface Management capabilities. These tools not only provide real-time insights into emerging threats but also enable organizations to proactively identify, analyze, and mitigate potential risks.
In a world where cybersecurity challenges are ever-present, the Ivanti Sentry vulnerability serves as a stark reminder. The remedy lies in the collective effort to stay informed, adapt strategies, and employ the right tools. By embracing the power of proactive threat intelligence and bolstering external attack surface management, organizations can take meaningful steps toward a more secure digital landscape.




































