
September 2023 Patch Tuesday by Microsoft Fixes Five Critical, Two Zero-Day Vulnerabilities
[Update] September 15, 2023: See the subheading: “Proof-of-Concept (PoC) Exploit Available for CVE-2023-38146 (ThemeBleed).”
Microsoft’s Patch Tuesday for September 2023 has been released, addressing 59 security vulnerabilities. The update encompasses five critical vulnerabilities as well as two exploited zero-day vulnerabilities.
This month’s update includes the following vulnerability types:
- 23 Remote Code Execution (RCE) Vulnerabilities
- 16 Elevation of Privilege (EoP) Vulnerabilities
- 9 Information Disclosure Vulnerabilities
- 3 Denial-of-Service (DoS) Vulnerabilities
- 3 Security Feature Bypass Vulnerabilities
- 3 Cross-Site Scripting (XSS) Vulnerabilities
- 2 Spoofing Vulnerabilities
In this blog post, we will outline the fixed vulnerabilities and guide organizations to secure their systems.
Zero-Day Vulnerabilities Under Active Exploitation: CVE-2023-36802 and CVE-2023-36761
This month’s Patch Tuesday addresses two actively exploited zero-day vulnerabilities:
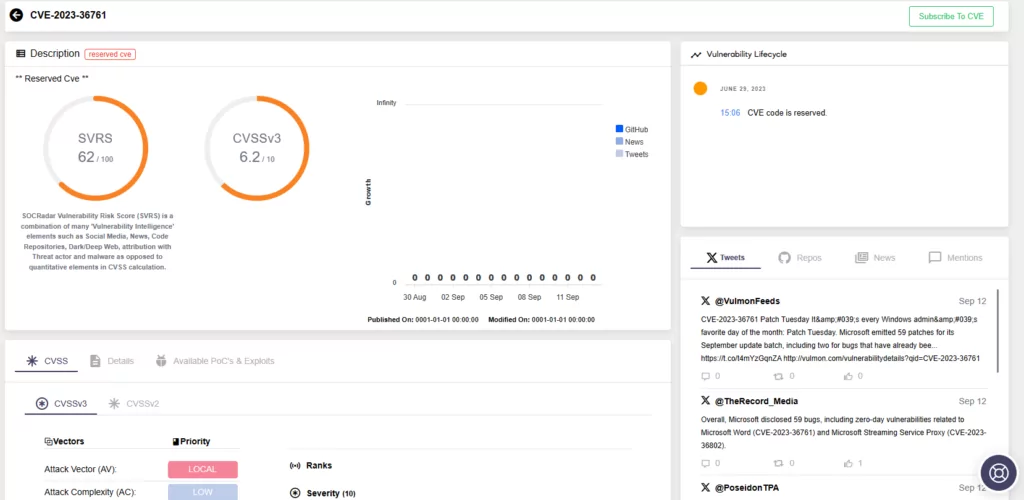
CVE-2023-36761: It is an information disclosure vulnerability in Microsoft Word. According to the advisory, the Preview Pane is also an attack vector, and exploiting the vulnerability could result in the disclosure of NTLM hashes. When opening a document, an attacker can steal these NTLM hashes and use them in NTLM Relay attacks to obtain access to accounts. The vulnerability has a CVSS score of 6.2 on the Microsoft advisory.
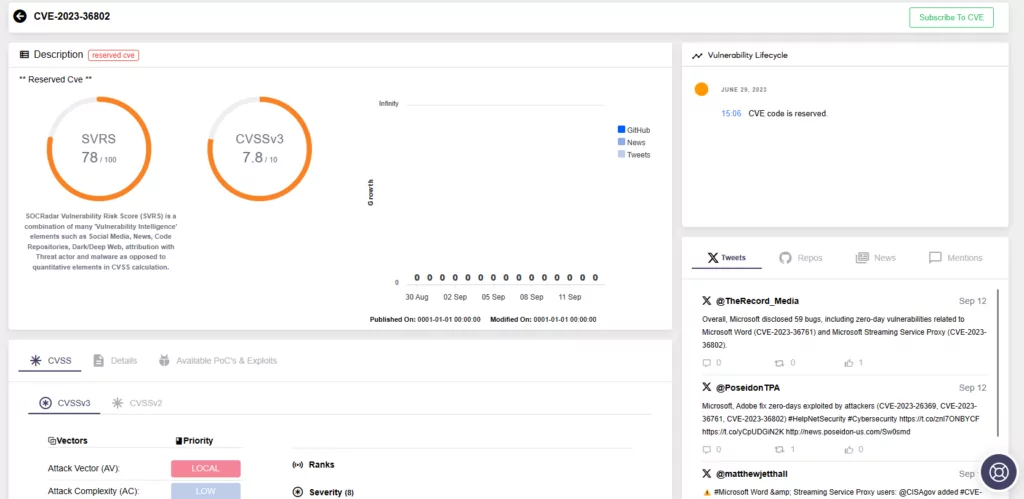
CVE-2023-36802: An Elevation of Privilege (EoP) vulnerability affecting Microsoft Streaming Service Proxy that, if exploited successfully, allows an attacker to gain SYSTEM privileges. The vulnerability has a CVSS score of 7.8 on the Microsoft advisory.
Critical Vulnerabilities in September 2023 Patch Tuesday
CVE-2023-36796, CVE-2023-36792, and CVE-2023-36793 are all critical vulnerabilities in Visual Studio that can lead to remote code execution (RCE). An attacker must persuade a user to open a maliciously crafted package file in Visual Studio in order to exploit these vulnerabilities. They have a CVSS score of 7.8 on Microsoft advisory.
Microsoft has addressed another RCE vulnerability, which affects the Internet Connection Sharing (ICS) service. The vulnerability is identified as CVE-2023-38148, with the update’s highest CVSS score of 8.8. An unauthorized attacker could exploit the vulnerability by sending a specially crafted network packet to the service. This attack is only applicable to systems connected to the same network segment as the attacker, and it can only be exploited if ICS is enabled.
The last critical vulnerability in the September 2023 Patch Tuesday update is CVE-2023-29332 (CVSS score: 7.5), which affects the Azure Kubernetes Service. A remote attacker who exploits this vulnerability successfully could gain Cluster Administrator privileges. Microsoft states that an attacker does not need extensive prior knowledge of the cluster/system to exploit this vulnerability and can achieve repeatable success.
Proof-of-Concept (PoC) Exploit Available for CVE-2023-38146 (ThemeBleed)
Recently, a Proof-of-Concept exploit surfaced for the Windows Themes vulnerability, CVE-2023-38146 (also known as ThemeBleed). This high severity vulnerability, which has a CVSS score of 8.8, has been patched as part of the September 2023 Patch Tuesday.
CVE-2023-38146 enables remote attackers to execute code by luring users into opening a malicious .THEME file. THEME files are typically used to customize the appearance of the operating system and refer to .MSSTYLES files, which are devoid of code.
According to researcher Gabe Kirkpatrick, utilizing the version number “999” triggers a race condition during the validation of a specific DLL’s signature, and permits attackers to substitute a verified DLL with a malicious one via a crafted .MSSTYLES file.
Downloading a theme file from the web usually triggers a Mark-of-the-Web (MotW) warning, but attackers can bypass this by packaging the theme into a THEMEPACK file.
Microsoft removed the version 999 functionality to address the vulnerability, but the underlying race condition and the lack of MotW warnings for THEMEPACK files remain unresolved.
You can access the PoC demonstration here. For in-depth information, refer to the researcher’s post.
Apply Updates for September 2023 Patch Tuesday
It is highly recommended to apply the patches promptly to safeguard your environment and enhance your security stance. To access additional details about the vulnerabilities addressed in September 2023 Patch Tuesday, see Microsoft’s Release Note.
Enhance Your Defense with SOCRadar
SOCRadar XTI platform’s comprehensive solutions empower you to swiftly identify, assess, and remediate vulnerabilities in real-time.
SOCRadar’s Vulnerability Intelligence enhances security by continuously monitoring vulnerabilities. This module allows you to search for vulnerabilities, access their details and related activities, and monitor hacker trends.
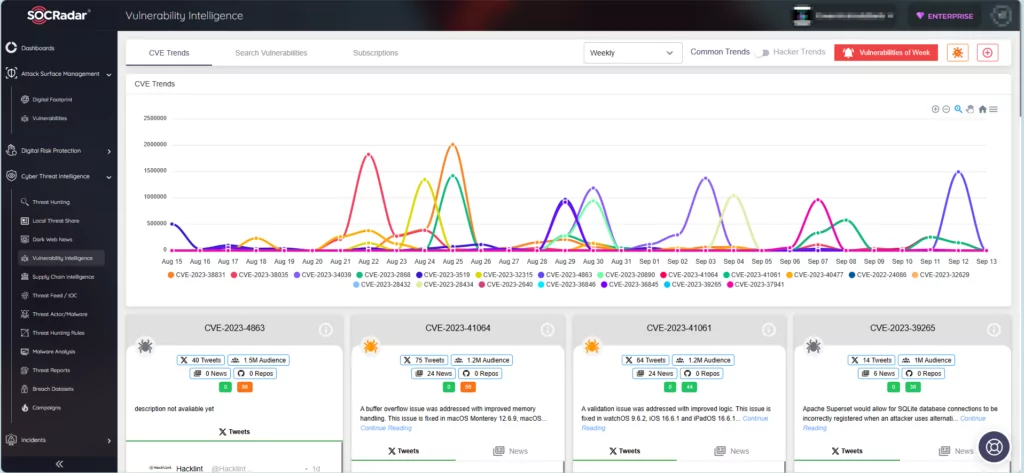
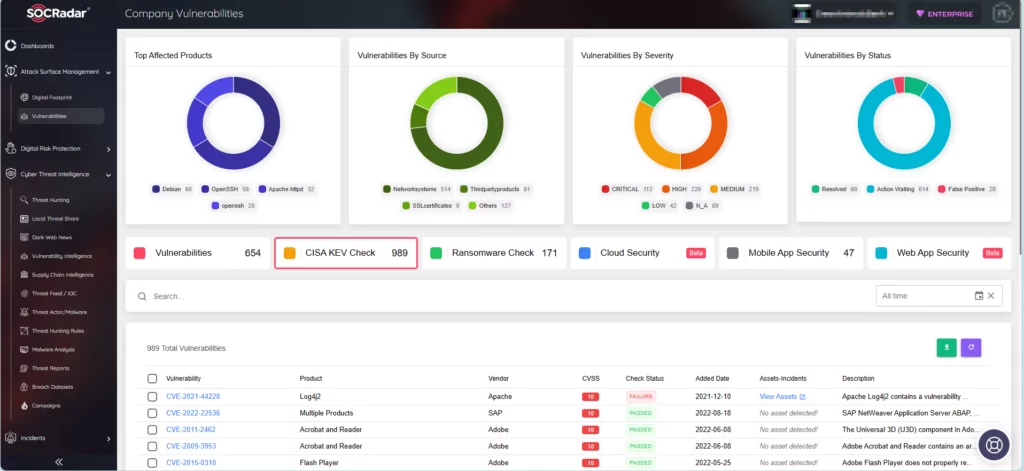
Furthermore, the Attack Surface Management module enables you to securely monitor your asset’s status and receive notifications about emerging vulnerabilities.
Sign up for the Free Edition to integrate SOCRadar into your security strategy and strengthen your defenses, maintain a proactive stance against emerging threats.

































