
Severe SLP Vulnerability Could Lead to Large DDoS Amplification Attacks
A new high-severity vulnerability was discovered, affecting Service Location Protocol (SLP). The vulnerability could allow attackers to launch massive volumetric denial-of-service (DoS) attacks, which could be amplified up to 2,200 times.
Researchers state that the vulnerability, identified as CVE-2023-29552 (CVSS score: 8.6), could lead to possibly the largest amplification attacks ever reported.
SLP Service Previously Exploited in Ransomware Attack
SLP is a service discovery protocol enabling devices to find services in a local network, such as printers and file servers.
Earlier this year, the SLP service was used in a ransomware attack targeting VMware ESXi servers worldwide. The attack targeted a vulnerability in OpenSLP, which is known as CVE-2021-21974. During the attack, it was discovered that 2,500 VMware ESXi servers were vulnerable to this vulnerability.
Over 2,000 Global Organizations Affected
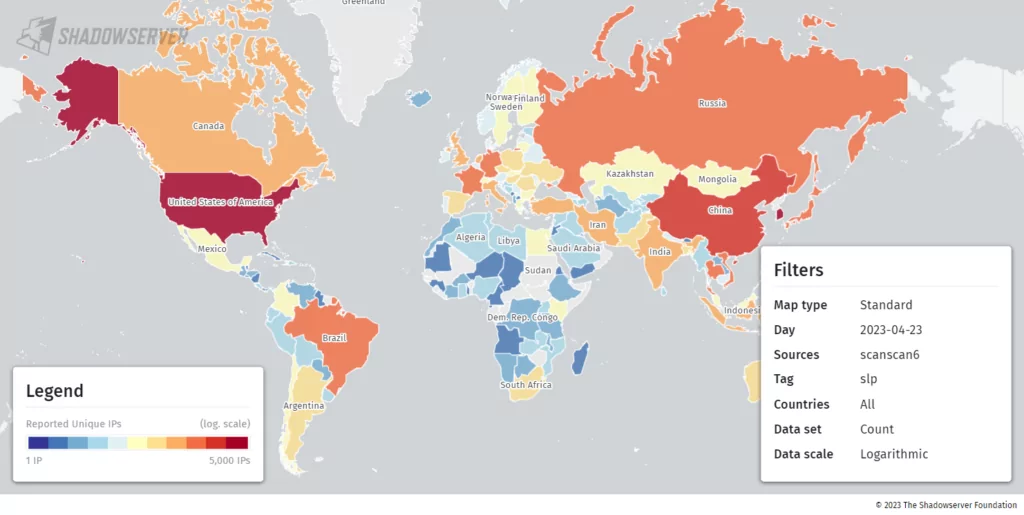
Over 2,000 Global Organizations Affected
The vulnerability, CVE-2023-29552, has been identified to affect over 2,000 global organizations and more than 54,000 SLP instances accessible via the internet, including VMWare ESXi Hypervisor, Konica Minolta printers, Planex Routers, IBM Integrated Management Module (IMM), SMC IPMI, and 665 other products.
The United States, the United Kingdom, Japan, Germany, and Spain are among the top countries affected by the CVE-2023-29552 vulnerability.
How Can Attackers Exploit CVE-2023-29552?
To launch a DDoS attack using SLP, an attacker must find an SLP server on UDP port 427, register services until SLP denies more entries, and repeatedly spoof a request to that service with a victim’s IP as the source address.
Cloudflare, a web security company, predicts that SLP-based DDoS attacks will increase significantly in the coming weeks as cybercriminals experiment with the new amplification vector.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has also warned about the vulnerability and potential attacks that could use SLP to conduct high amplification factor DoS attacks using spoofed source addresses.
Recommendations
VMware recommends upgrading to a supported release that is not vulnerable to the CVE-2023-29552 vulnerability.
As a mitigation strategy, users can disable SLP on systems that are directly connected to the internet or filter traffic on UDP and TCP port 427.
Furthermore, ESXi administrators must ensure that their ESXi hosts are not accessible through untrusted networks and implement strong authentication and access controls.
How Can SOCRadar Help?
The strategy SOCRadar establishes in asset protection can help you stay ahead of potential security risks and maintain the integrity of your organizational assets.
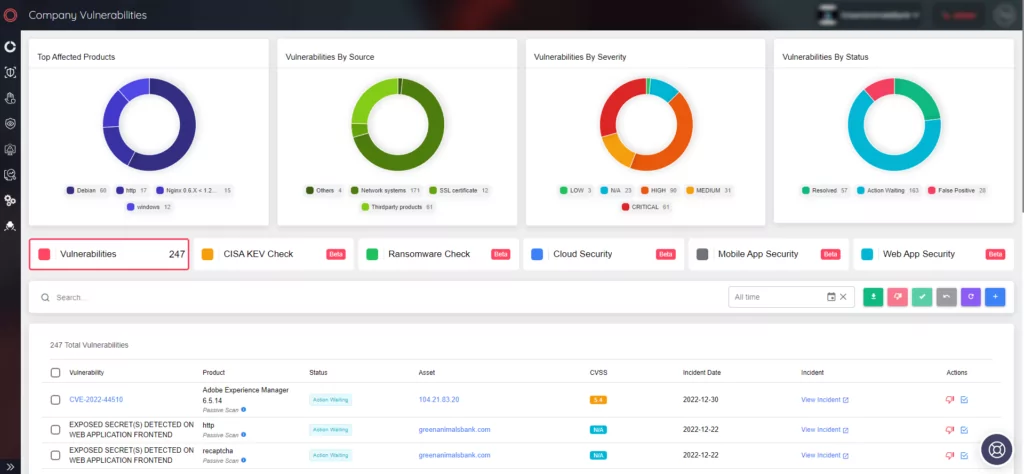
SOCRadar’s External Attack Surface Management solution continuously monitors your assets to detect emerging threats and alert you on time. A user-friendly interface lets you view all vulnerabilities affecting your assets and take appropriate actions to mitigate them.
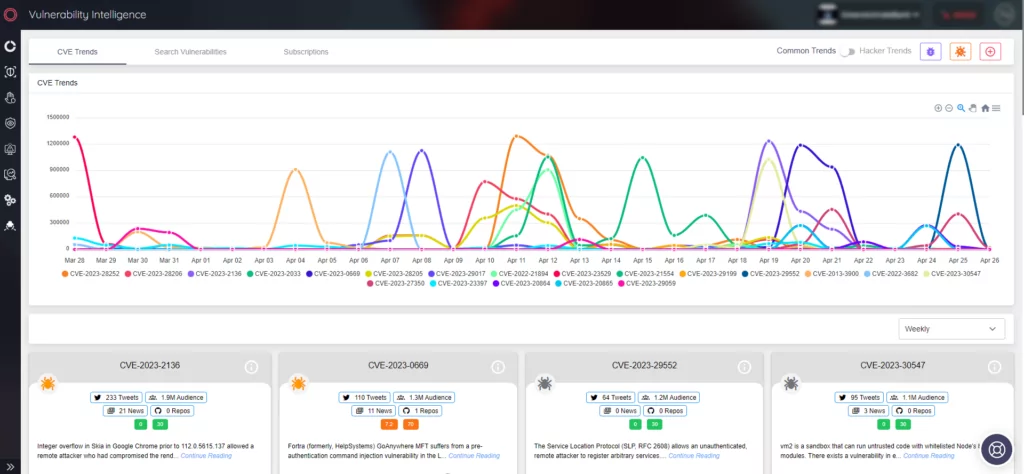
Additionally, SOCRadar’s Vulnerability Intelligence provides the latest details on vulnerabilities and keeps you informed about current trends in hacker activity.
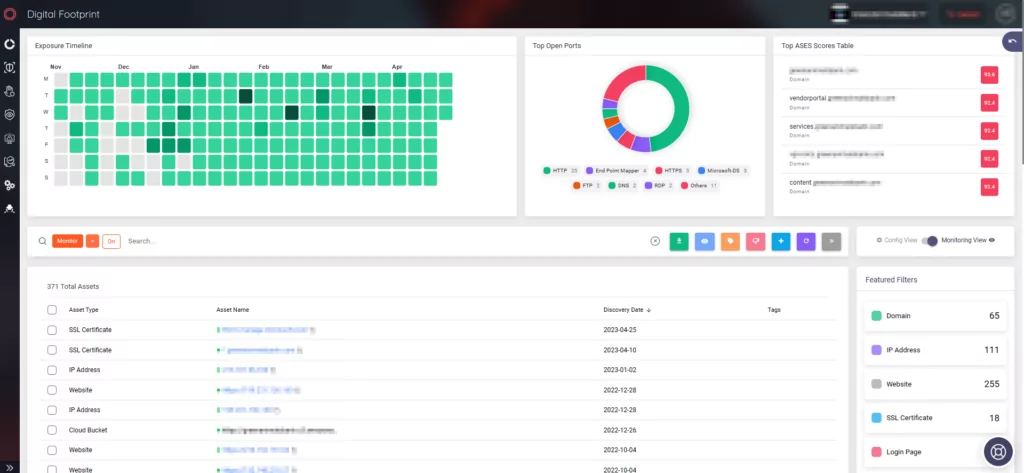
You can also monitor all publicly accessible assets and infrastructure, including IP addresses and DNS configurations, on the Digital Footprint tab.

Over 2,000 Global Organizations Affected

Over 2,000 Global Organizations Affected
The vulnerability, CVE-2023-29552, has been identified to affect over 2,000 global organizations and more than 54,000 SLP instances accessible via the internet, including VMWare ESXi Hypervisor, Konica Minolta printers, Planex Routers, IBM Integrated Management Module (IMM), SMC IPMI, and 665 other products.
The United States, the United Kingdom, Japan, Germany, and Spain are among the top countries affected by the CVE-2023-29552 vulnerability.
How Can Attackers Exploit CVE-2023-29552?
To launch a DDoS attack using SLP, an attacker must find an SLP server on UDP port 427, register services until SLP denies more entries, and repeatedly spoof a request to that service with a victim’s IP as the source address.
Cloudflare, a web security company, predicts that SLP-based DDoS attacks will increase significantly in the coming weeks as cybercriminals experiment with the new amplification vector.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has also warned about the vulnerability and potential attacks that could use SLP to conduct high amplification factor DoS attacks using spoofed source addresses.
Recommendations
VMware recommends upgrading to a supported release that is not vulnerable to the CVE-2023-29552 vulnerability.
As a mitigation strategy, users can disable SLP on systems that are directly connected to the internet or filter traffic on UDP and TCP port 427.
Furthermore, ESXi administrators must ensure that their ESXi hosts are not accessible through untrusted networks and implement strong authentication and access controls.
How Can SOCRadar Help?
The strategy SOCRadar establishes in asset protection can help you stay ahead of potential security risks and maintain the integrity of your organizational assets.
SOCRadar’s External Attack Surface Management solution continuously monitors your assets to detect emerging threats and alert you on time. A user-friendly interface lets you view all vulnerabilities affecting your assets and take appropriate actions to mitigate them.

Additionally, SOCRadar’s Vulnerability Intelligence provides the latest details on vulnerabilities and keeps you informed about current trends in hacker activity.

You can also monitor all publicly accessible assets and infrastructure, including IP addresses and DNS configurations, on the Digital Footprint tab.



































