
Suspicious Domains Exploiting the Recent CrowdStrike Outage!
[Update] July 23, 2024: “Researchers Warn of Phishing Scenarios Exploiting the CrowdStrike Outage by Cybercriminals”, “Exploiting Real Time Response (RTR) Module”, “Hacktivist Threat Group Handala Targets Israeli Organizations with Phishing Campaign”
On Friday, a routine software update by CrowdStrike inadvertently triggered a critical disruption across various infrastructures and organizations. The update caused the notorious Blue Screen of Death (BSOD), rendering numerous systems inoperable. While initially not classified as a cybersecurity incident, the situation highlights the fragile nature of digital security and the potential for such disruptions to escalate into serious security threats.
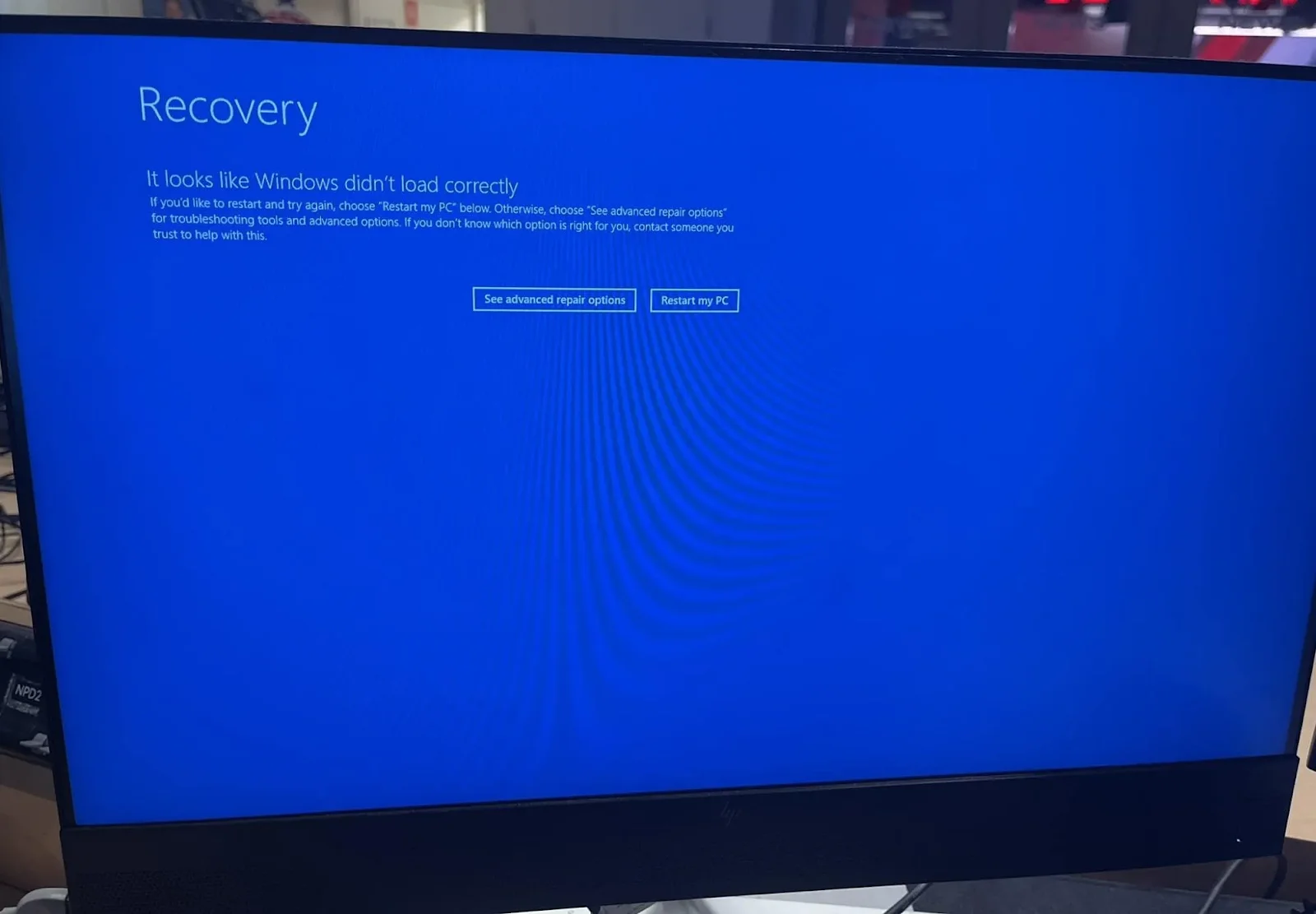
BSOD caused by CrowdStrike agent, (Source: X)
What Was the Initial Fallout?
The issues began surfacing shortly after users installed CrowdStrike’s latest update. System crashes and the dreaded BSOD were widespread, causing significant operational disruptions. Despite not being a direct cybersecurity breach, keeping systems operational is crucial for security.
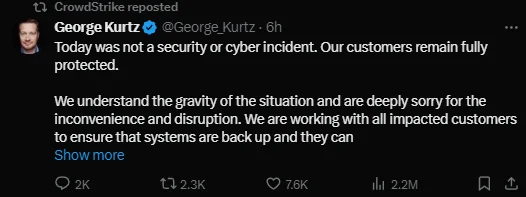
Statement of CrowdStrike’s President and CEO, George Kurtz (Source: X)
CrowdStrike’s President and CEO, George Kurtz, emphasized that the incident was not a cybersecurity attack. However, he acknowledged the severity of the disruption and reassured customers that a fix was underway. His statement underlined the importance of robust incident response measures even in cases of non-malicious disruptions.
How Are Cybercriminals Exploiting This?
The disruption caused by CrowdStrike has unfortunately opened doors for opportunistic threat actors. Cybercriminals have been quick to exploit the situation with social engineering attack by setting up scam domains and phishing pages, masquerading as solutions to the BSOD issue. For instance, one malicious domain redirected users to payment pages requesting cryptocurrencies such as Bitcoin and Ethereum under the guise of providing a fix.
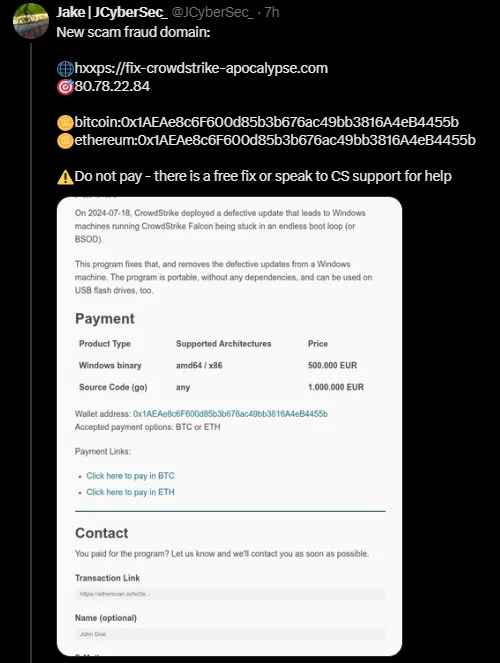
Screenshot of Fraudulent Domain (Source: X)
Another domain has surfaced, claiming to offer support services to companies affected by the issue. Caution is advised as these claims are potentially misleading and could pose additional security risks.
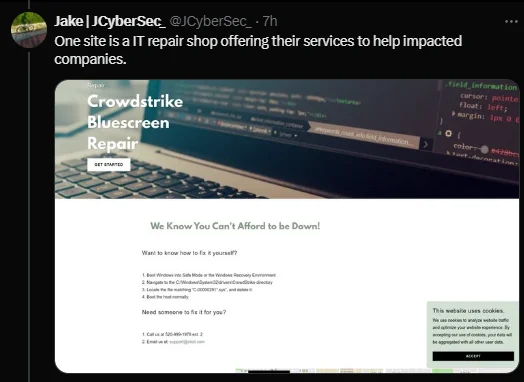
A fake website posing as a CrowdStrike support site, offering deceptive services. (Source: X)
Researchers Warn of Phishing Scenarios Exploiting the CrowdStrike Outage by Cybercriminals
With the recent disruption caused by the CrowdStrike update, there has been a significant rise in cybercriminal activities aiming to exploit this situation. A key concern is the increased likelihood of phishing attacks designed to harvest credentials from CrowdStrike users.
Exploiting Real Time Response (RTR) Module
Cybersecurity researcher Will Thomas warns that threat actors, such as the group Scattered Spider, might leverage phishing tactics to obtain CrowdStrike Falcon credentials. These attackers could use sophisticated techniques, including email and SMS phishing campaigns, to deceive users into providing their login details. A common method employed by such groups involves using an Adversary-in-the-Middle (AitM) proxy kit to intercept and steal credentials in real-time.
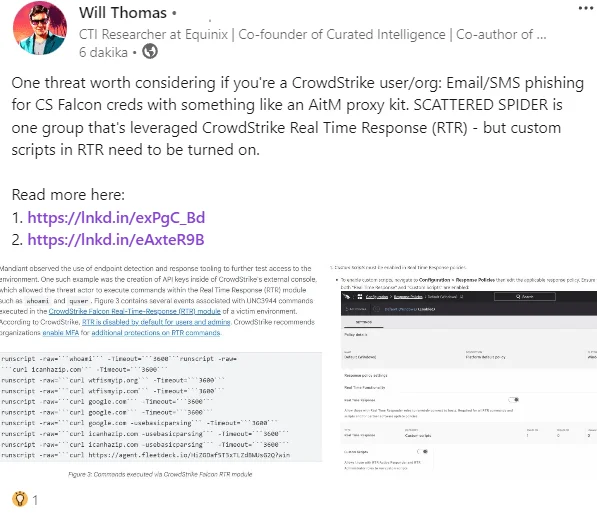
Will Thomas’ LinkedIn post
Once attackers gain access to CrowdStrike Falcon credentials, they could potentially exploit the Real Time Response (RTR) module (if enabled). This module allows for executing custom scripts and commands on the endpoints. Having enable the custom scripts within RTR policies, the threat actors could
remotely execute code on the victim host, and make use of PowerShell. This could escalate to a situation possibly leading to a complete system takeover.
Hacktivist Threat Group Handala Targets Israeli Organizations with Phishing Campaign
A pro-Palestinian hacktivist group named Handala has launched a phishing campaign targeting CrowdStrike users in Israel. The group claims to have used the recent CrowdStrike incident as a lure, delivering wiper malware via phishing emails to thousands of Israeli organizations. The Israeli government has issued a warning on its official portal, emphasizing the threat.
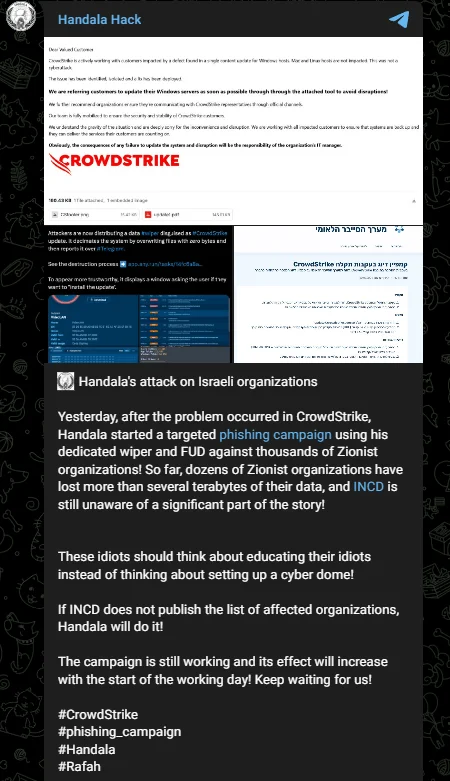
Threat actor’s announcement about cyber attack campaign
The alert from the Israel National Cyber Directorate highlights the following details:
- Phishing Emails: The phishing emails were sent from the address update@crowdstrike[.]com[.]vc.
- Email Contents: The emails contained a PDF file with a link to download an update via a file-sharing service. The downloaded ZIP file contained a malicious EXE file.
- Mitigation: Organizations are advised to monitor for the provided identifiers in all relevant security systems, including SIEM, AV, EDR, and email/file filtering systems. The National Cyber Directorate requests updates if any of these identifiers are found within organizational systems.
![The phishing email that was sent from the address update@crowdstrike[.]com[.]vc](https://socradar.io/wp-content/uploads/2024/07/crowdstrike-phishing-email.png.webp)
The phishing email that was sent from the address update@crowdstrike[.]com[.]vc
The domain crowdstrike[.]com[.]vc was registered on July 20, 2024, through the registrar NameCheap, Inc., and is reportedly being used by Handala.
Cybersecurity Concerns and Recommendations
This incident serves as a stark reminder of the vulnerabilities associated with system updates and the importance of cybersecurity vigilance. Organizations should:
- Verify Communication: Always ensure communication comes from official sources. In the wake of the update, phishing attempts may increase, with attackers impersonating CrowdStrike or other trusted entities.
- Secure Online Interactions: Utilize trusted services to verify the security of various websites and URLs, especially those claiming to offer support or fixes related to recent issues.
- Educate Staff: Educate employees about the risks of phishing and the importance of verifying the authenticity of requests for information or access.
What Are Indicators of Compromise (IoCs)?
Be vigilant for indicators of compromises (IoCs) that may signal malicious activity. Here are some of the suspicious domains that can be used by threat actors:
- crowdstrike-helpdesk[.]com
- crowdstrikebluescreen[.]com
- crowdstrike-bsod[.]com
- crowdstrikedown[.]site
- crowdstrike0day[.]com
- crowdstrikedoomsday[.]com
- crowdstrikefix[.]com
- crashstrike[.]com
- crowdstriketoken[.]com
- fix-crowdstrike-bsod[.]com
- bsodsm8rLIxamzgjedu[.]com
- crowdstrikebsodfix[.]blob[.]core[.]windows[.]net
- crowdstrikecommuication[.]app
- fix-crowdstrike-apocalypse[.]com
- crowdstrikeoutage[.]info
- clownstrike[.]co[.]uk
- whatiscrowdstrike[.]com
- clownstrike[.]co
- microsoftcrowdstrike[.]com
- crowdfalcon-immed-update[.]com
- crowdstuck[.]org
- failstrike[.]com
- winsstrike[.]com
- crowdpass[.]
- supportfalconcrowdstrikel[.]com
- crowdstrikehealthcare[.]com
- crowdstrikeclaim[.]com
- crowdstrikebug[.]com
- crowdstrikeupdate[.]com
- crowdstrikefail[.]com
- crowdstrikeoopsie[.]com
- crowdstrike[.]fail
- crowdstrike[.]woccpa[.]com
- crowdstrikereport[.]com
- crowdstrike-cloudtrail-storage-bb-126d5e[.]s3[.]us-west-1[.]amazonaws[.]com
- hoo[.]be/crowdstrike
- crowdstrike[.]orora[.]group
- sinkhole-d845c7b471d9adc14942f95105d5ffcf.crowdstrikeupdate[.]com
- crowdstrike-falcon[.]online
- crowdstrikerecovery1[.]blob[.]core[.]windows[.]net
- crowdstrikeoutage[.]com
- sedo[.]com/search/details/?partnerid=324561&language=es&domain=crowdstrike[.]es&ori…
- isitcrowdstrike[.]com
- crowdstrike[.]black
- crowdstrikefix[.]zip
- crowdstrikeold[.]com
- crowdstrikeout[.]com
- crowdstrike-out[.]com
- crowdstrikeoops[.]com
- crowdstrikefixer[.]com
- crowdstrikesucks[.]com
- crowdstrikeclaims[.]com
- crowdstrikeglitch[.]com
- crowdstrikelawsuit[.]com
- crowdstrikesuporte[.]com
- crowdstrikezeroday[.]com
- crowdstrikerecovery[.]com
- crowdstrike-bluescreen[.]com
- crowdstrikeclassaction[.]com
- crowdstrikewindowsoutage[.]com
- 96dec6e07229201a02f538310815c695cf6147c548ff1c6a0def2fe38f3dcbc8
- 4491901eff338ab52c85a77a3fbd3ce80fda738046ee3b7da7be468da5b331a3
- 70865e5a49b8c270eb8175c36cd2a2032c05445c0daf59dc67e78dad545ff9e4
- 1bbb795ce19f4dcc4ac9f8e8c12f3452f1f07c68a53ef631c76e392e1d06ea43
- crowdstrike[.]com[.]vc
- update@crowdstrike[.]com[.]vc
- crowdstrike[.]phpartners[.]org
See, Analyze, Secure: Navigating the Complex Cybersecurity Landscape of Over 50 Million Companies
The CrowdStrike outage highlights the importance of availability in cybersecurity, showcasing how such incidents pose real threats to cyber safety. Enhance your digital security with SOCRadar Supply Chain Intelligence, which provides insights on over 50 million companies worldwide. This platform enables effective decision-making through access to detailed cybersecurity updates, assessment reports, and cyber exposure levels.
SOCRadar Supply Chain Intelligence
SOCRadar’s AI-enabled Digital Risk Protection module meticulously analyzes registered domain names to identify and give alerts when malicious domains targeting your brand are detected. With real-time notifications about suspicious domains and the expiration of SSL certificates, SOCRadar ensures you stay ahead of threats, maintaining the integrity and security of your digital presence.
SOCRadar Digital Risk Protection




































