
Massive Swiss Medical Leak, Binance Phishing Panel, and WhatsApp Ban Service Found
SOCRadar’s Dark Web Team has uncovered several alarming cyber threats circulating on hacker forums this week. Key discoveries include an alleged data breach at Swiss Medical in Argentina, exposing clients’ personal information. Meanwhile, a sophisticated Binance phishing panel is being sold, capable of bypassing multiple authentication methods. Additionally, a threat actor is offering a zero-day exploit for Magento, a major e-commerce platform, with Remote Code Execution (RCE) capabilities. Other findings include unauthorized VPN access to a U.S. ISP, a leak of stolen credit card logs, and a Dark Web service allegedly designed to ban WhatsApp accounts on demand.
SOCRadar Dark Web News: Key highlights of this week’s detected threat actor activities
Receive a Free Dark Web Report for Your Organization:
Alleged Database of Swiss Medical is Leaked
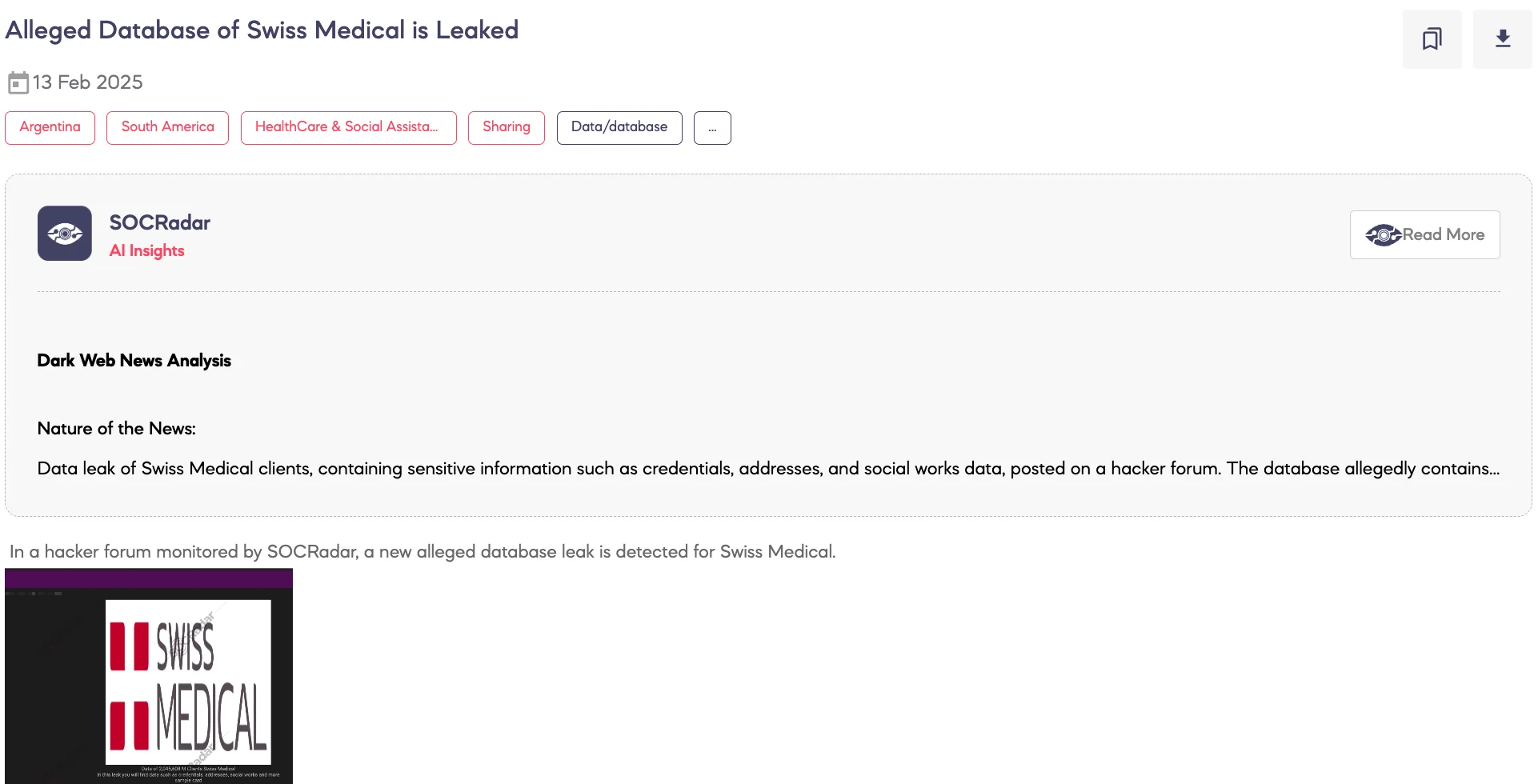
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to have leaked the alleged database of Swiss Medical, a private healthcare provider in Argentina. According to the threat actor, the dataset contains information on 2,045,608 clients, including credentials, addresses, social security details, and other sensitive data.
New Binance Phishing Panel is on Sale
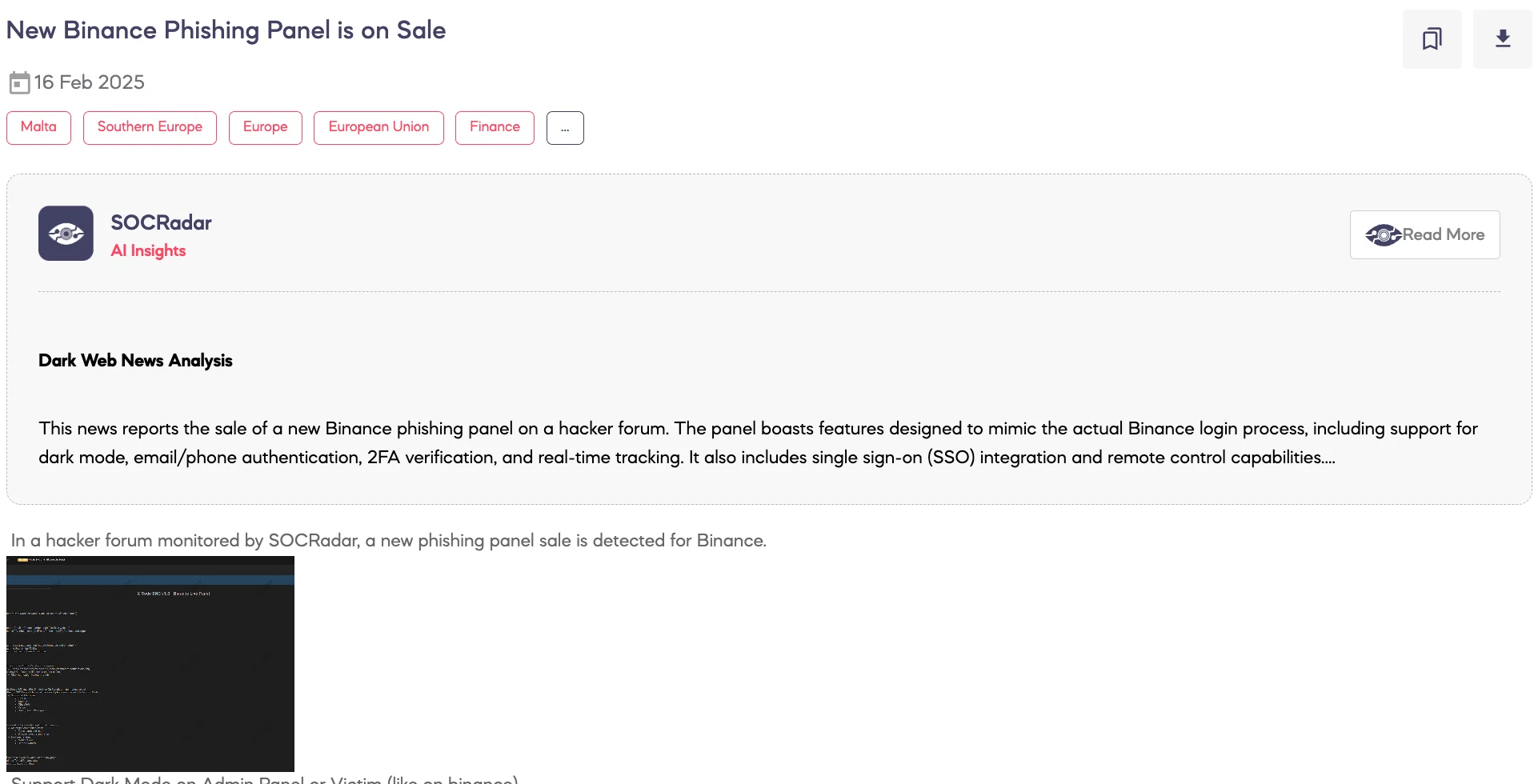
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to be selling a new phishing panel targeting Binance users. According to the threat actor, the panel mimics Binance’s authentication system, including email/phone login, two-factor authentication (2FA), and real-time tracking of victim interactions. The phishing panel also supports integration with multiple Single Sign-On (SSO) services, such as iCloud, Outlook, Office365, Yahoo, and Gmail, enabling the collection of credentials across different platforms. Additional functionalities include persistent session management, admin notifications via Telegram, and the ability to replay user actions.
An Alleged 0-Day Exploit is on Sale for Magento
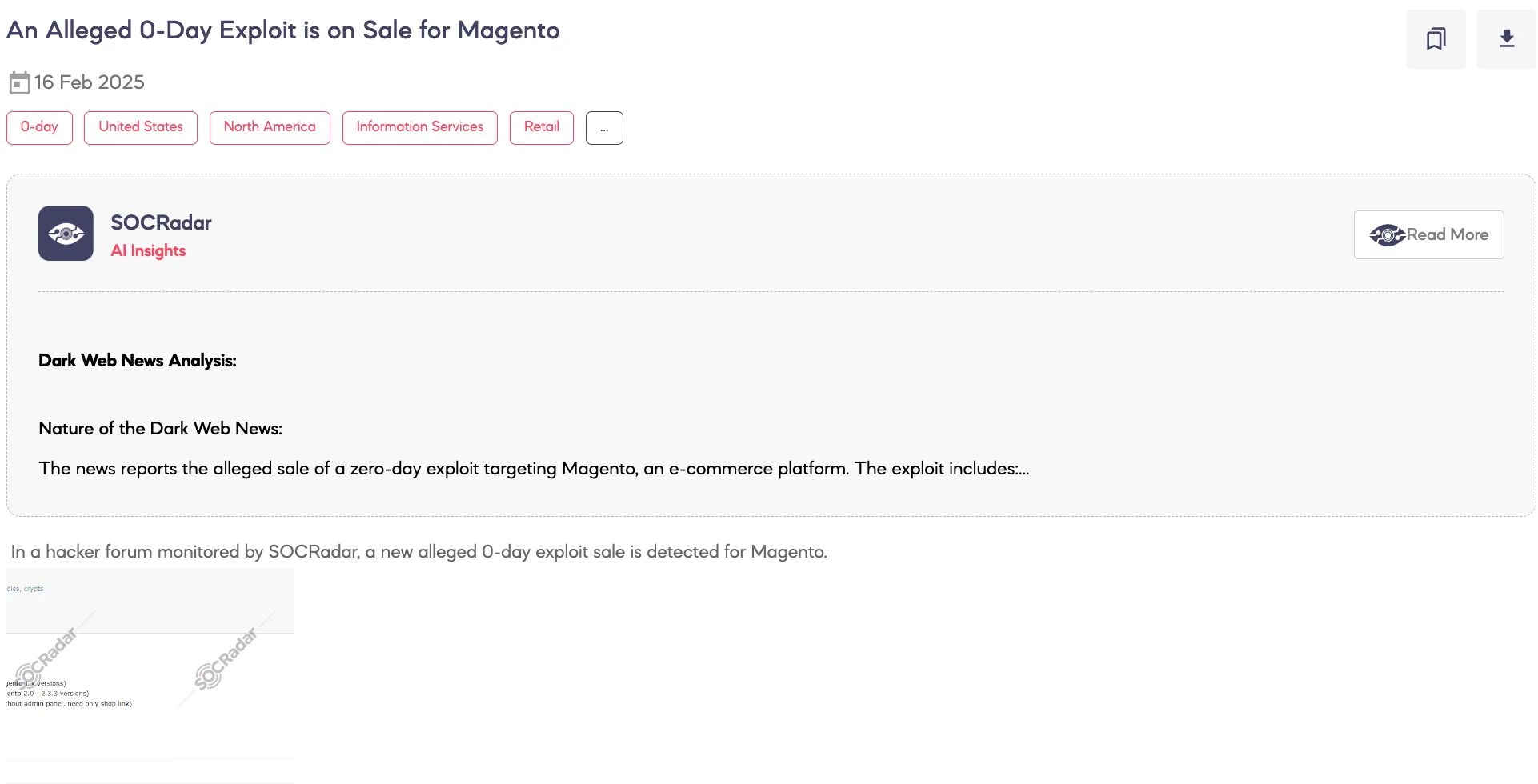
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to be selling a zero-day exploit for Magento. According to the threat actor, the exploit includes multiple methods for gaining unauthorized access:
- 0-day shell uploader via Admin Panel (for Magento 1.x versions)
- 0-day shell uploader via Admin Panel (for Magento 2.0 – 2.3.3 versions)
- Remote Code Execution (RCE) via the checkout page, which allegedly does not require admin access and only needs the shop’s URL.
The asking price for the exploit is $10,000.
An Alleged Unauthorized VPN Access Sale is Detected for an American ISP Company
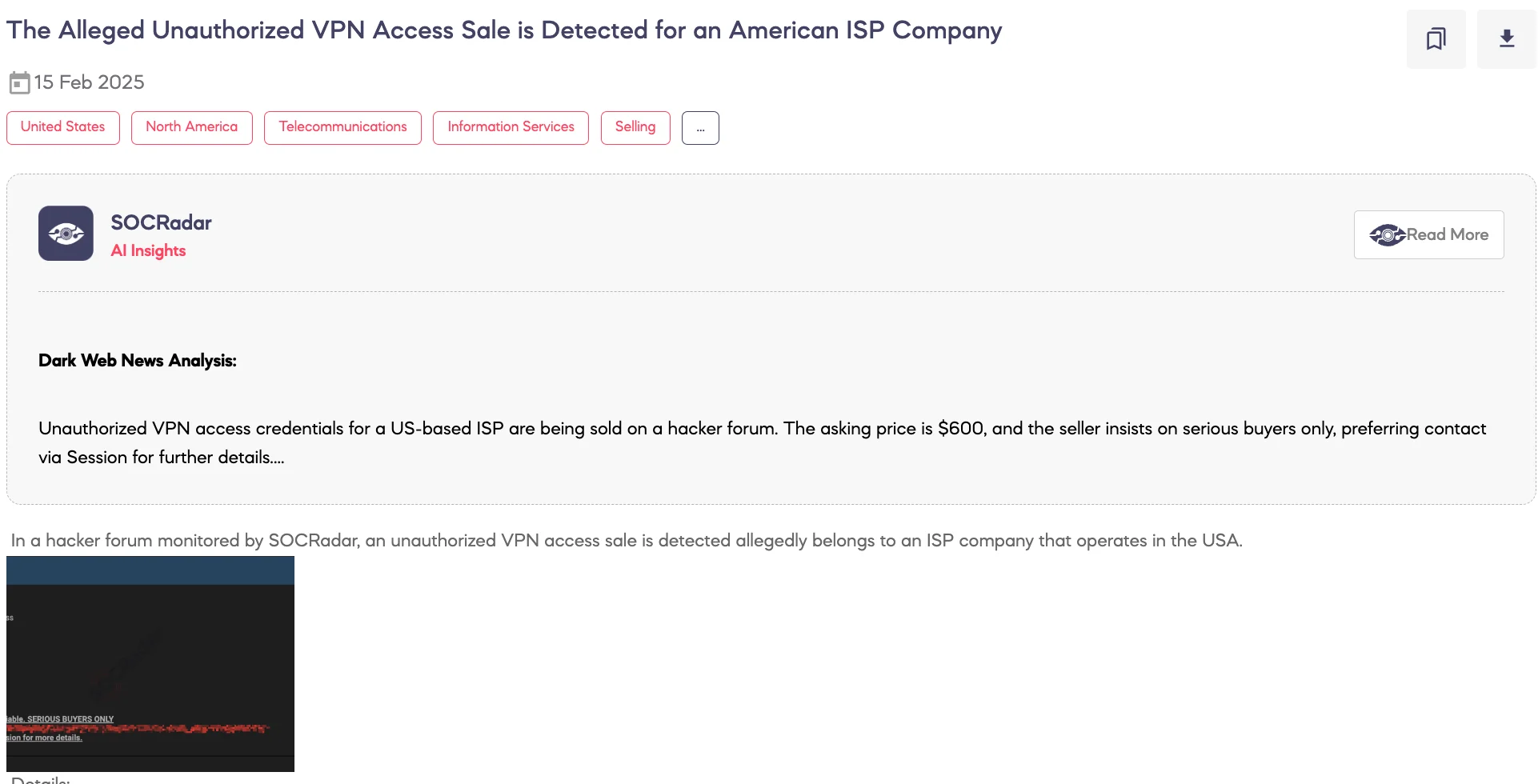
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to be selling unauthorized VPN access allegedly belonging to an Internet Service Provider (ISP) operating in the United States. According to the post, the sale includes VPN credentials, with access being offered for $600, and the price is non-negotiable. The threat actor provides contact details via Session for further inquiries.
Alleged 90,000 Credit Card Logs are Leaked
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to have leaked 90,000 credit card logs. The post provides minimal details but invites interested parties to make contact for further information regarding the dataset.
WhatsApp Ban Service is Detected
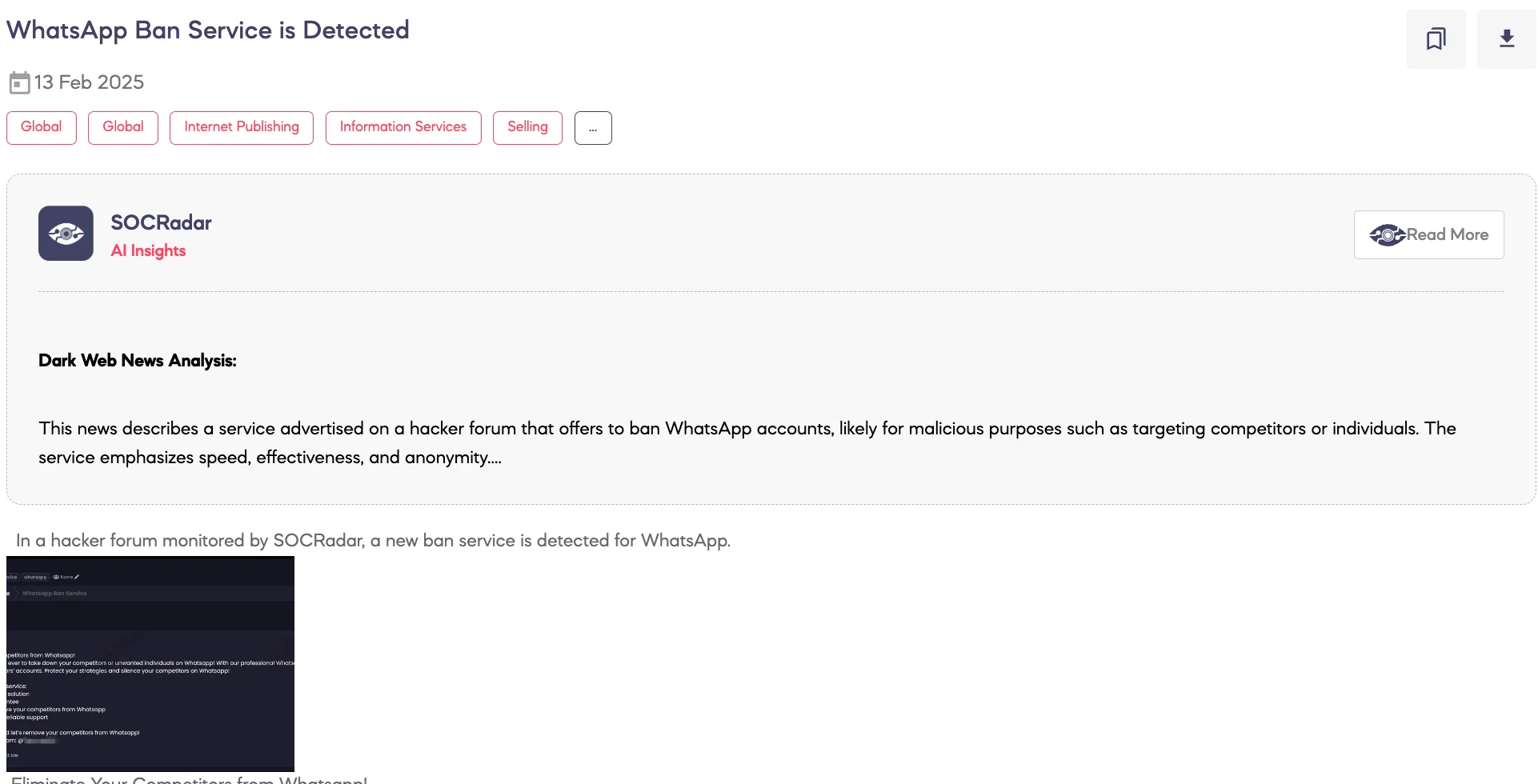
SOCRadar Dark Web Team detected a post on a hacker forum advertising a WhatsApp Ban Service, allegedly designed to disable competitors’ or targeted individuals’ accounts. The threat actor claims that the service offers fast and effective account removals with a full privacy guarantee, promoting it as a tool for eliminating competition on the platform. Contact details are provided via Telegram for further inquiries.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































