
Termite Ransomware Attack on Blue Yonder: What You Need to Know
In late November 2024, Blue Yonder, a critical provider of supply chain management solutions, fell victim to a ransomware attack attributed to the newly emerged Termite ransomware group.
The attack disrupted operations for several prominent businesses, including major grocery chains in the UK and US, exposing the vulnerabilities that organizations could face in supply chain operations.
As a subsidiary of Panasonic, Blue Yonder offers AI-powered supply chain solutions to over 3,000 high-profile clients – including Microsoft, Procter & Gamble, Renault, Tesco, and Starbucks. The firm’s services are integral to the easy flow of goods across industries.
In this article, we’ll look at the attack’s timeline and its impact on Blue Yonder’s customers, as well as what Termite ransomware is and what lessons can be learned from this incident to improve supply chain security.
Inside the Ransomware Incident Impacting a Major Supply Chain Platform
Blue Yonder notified its customers that it experienced an intrusion targeting its managed services hosting environment, on November 21, 2024. This incident disrupted its services and highlighted the potential vulnerabilities of third-party supply chain platforms.
In its initial notice, dated November 22, the company confirmed a ransomware attack and outlined steps to address the incident, including working with external cybersecurity firms and implementing defensive and forensic measures. Updates on November 23 and 24 reiterated ongoing recovery efforts and steady progress but offered no definitive timeline for restoration.
The incident’s effects were felt across Blue Yonder’s extensive client base, including grocery store chains and global retailers.
By December 1, Blue Yonder reported that several impacted customer systems had been restored, showcasing progress in its recovery process. However, the company also recognized claims of stolen data by December 6, confirming that investigations into the matter were continuing with the help of external cybersecurity experts.
Later, on December 9, the emerging Termite ransomware group claimed responsibility for the attack, alleging the theft of 680GB of data, including database dumps, email lists, internal documents, and insurance files.
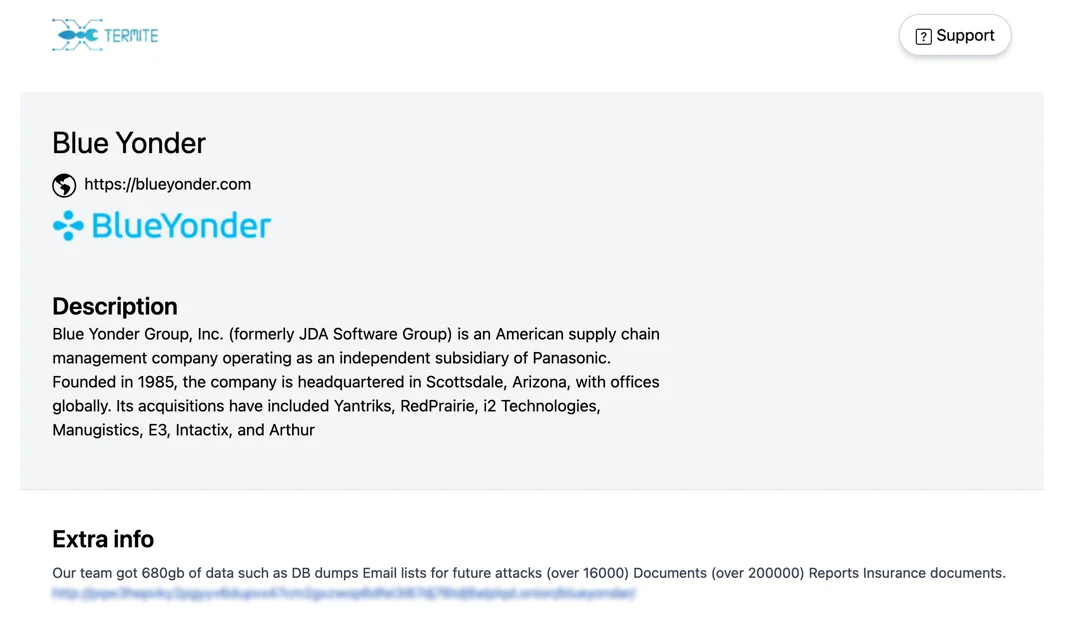
Victim listing of Blue Yonder on Termite Ransomware’s data leak site
The group threatened to leak the allegedly stolen data publicly, increasing the pressure on affected companies.
How the Outage Disrupted Operations of Customers
The ransomware attack on Blue Yonder caused operational disruptions for several high-profile organizations. Media outlets reported that UK grocery chains, such as Morrisons and Sainsbury, were among the companies adapting to the outage with contingency measures. Morrisons reverted to a slower backup process to manage warehouse operations for fresh produce, while Sainsbury relied on pre-established contingency plans to ensure minimal disruption.
In the United States, Starbucks was reportedly forced to abandon its automated scheduling software, managed by Blue Yonder, and temporarily resort to manual processes to ensure its employees were paid accurately. The situation disrupted operations across numerous locations, underlining how even routine processes like payroll can be impacted by supply chain platform outages.
In addition, French manufacturer BIC also faced shipping delays due to the incident, further emphasizing the vulnerabilities in logistics systems when third-party providers are affected. These challenges collectively highlight the growing interdependence between enterprises and their software providers, where a single point of failure can cascade into broader operational issues.
SOCRadar’s Supply Chain Intelligence module offers a modern solution to secure your supply chain against emerging cyber threats. With visibility into over 50 million companies, it enables you to monitor suppliers for vulnerabilities, breaches, and suspicious activities.
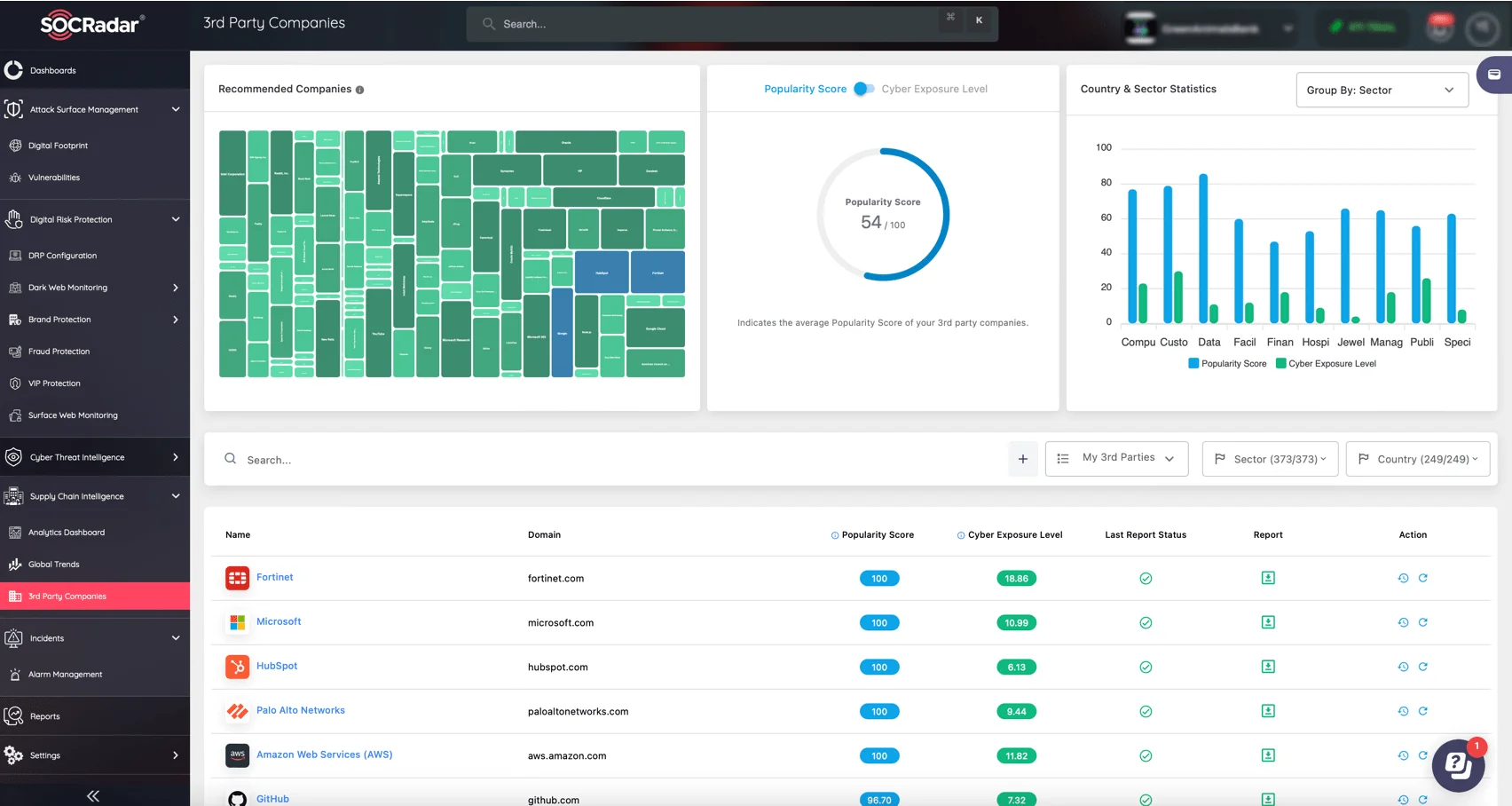
Monitor 3rd party companies with SOCRadar’s Supply Chain Intelligence
The Supply Chain Intelligence module’s key features include:
- Scoring Systems: Prioritize high-risk suppliers with Cyber Exposure Level and Popularity Score.
- Advanced Monitoring: Track vulnerabilities, breaches, and weak points in your supply chain.
- Dynamic Alerts: Receive actionable recommendations to respond swiftly and reduce exposure.
From mapping your supply chain ecosystem to assessing third-party cybersecurity posture, this tool enables your organization to mitigate risks proactively and maintain operational resilience.
Who is Behind Blue Yonder Attack? Meet Termite Ransomware
The Termite ransomware group has claimed responsibility for the November attack on Blue Yonder, listing the company on their Dark Web data leak site on December 9, 2024.
This emerging group is a new variant of the infamous Babuk ransomware. Known for its aggressive double extortion tactics, Babuk’s methods have been adapted by Termite.
Despite being relatively new, Termite is rapidly establishing its presence, with seven victims listed on its leak site so far. These victims include names such as:
- Nifast
- Culligan
- Oman Oil
- Lebenshilfe Heinsberg
- Conseil scolaire Viamonde
- Département de La Réunion

All companies currently listed by Termite Ransomware
The group’s double extortion approach – encrypting victims’ systems while threatening to leak stolen data – has proven effective in maximizing their leverage over targeted organizations. In Blue Yonder’s case, Termite claims to have exfiltrated 680GB of sensitive data.
The Dark Web is a hub for stolen data, ransomware strategies, and other cybercriminal activities. Without insight into this hidden ecosystem, your organization could be at risk. To combat this threat, SOCRadar’s Dark Web Monitoring module offers:
- Real-Time Alerts: Notifications when your organization’s data is detected on dark web forums and marketplaces.
- Threat Detection: Identification of compromised credentials and sensitive information.
- Proactive Risk Mitigation: Early identification of potential threats before they escalate.
Additionally, integrated into SOCRadar’s Cyber Threat Intelligence (CTI), the Ransomware Intelligence module takes your defense further by allowing you to:
- Search Indicators of Compromise (IoCs) across 2.5 billion records to detect ransomware activities and threat actors.
- Create and integrate ransomware-specific IoC collections into SIEM, EDR, and Firewall solutions for active prevention.
- Add newly detected phishing URLs to IoC collections, shielding your organization from evolving ransomware tactics.
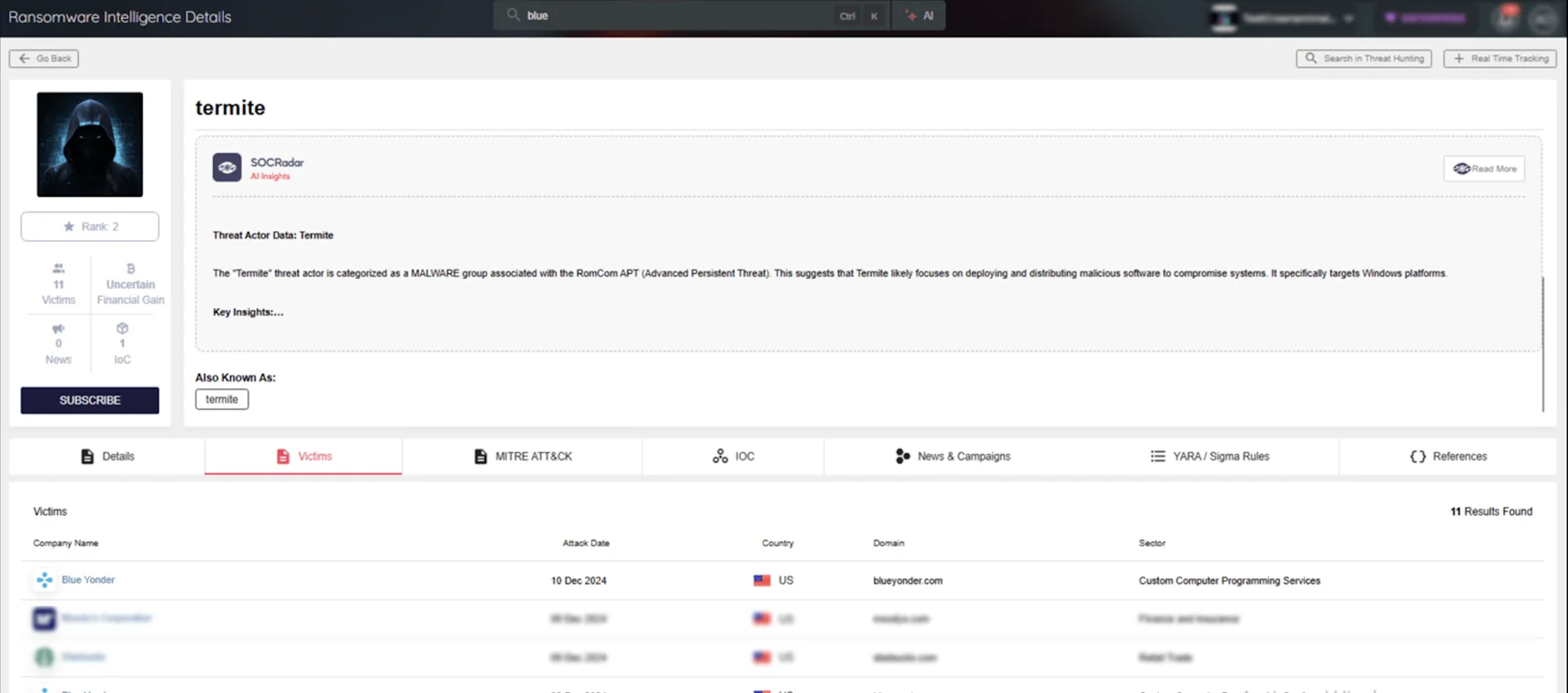
Who is the Termite Ransomware Group? Learn more about its TTPs, IOCs, and latest operations with SOCRadar Ransomware Intelligence
Together, these tools provide the actionable insights and real-time intelligence you need to counter ransomware and Dark Web threats, ensuring your organization remains resilient in an ever-changing threat landscape.
Proactive Measures to Mitigate Supply Chain Cyber Risks
As organizations rely more on third-party vendors for critical operations, proactive monitoring of these relationships is critical to risk mitigation. Cyberattacks like this highlight the need to address the tactics used by groups like Termite ransomware, which use double extortion methods to threaten both operational disruption and data exposure.
Blue Yonder’s ongoing recovery efforts, including collaboration with external cybersecurity experts, highlight the importance of swift incident response and transparent communication. As they work to restore operations, organizations must reflect on the lessons from this attack to fortify their own defenses. For ongoing updates, refer to Blue Yonder’s official customer update page.
Solutions such as SOCRadar’s Supply Chain Intelligence module offer essential capabilities for monitoring third-party vendors, identifying vulnerabilities, and mitigating risks before they escalate. Combined with Dark Web Monitoring to detect potential threats and Ransomware Intelligence for understanding adversaries’ tactics, SOCRadar XTI equips organizations with the tools needed to protect their supply chains against emerging cyber threats.




































