
The Importance of Supply Chain Security for Safeguarding Business Ecosystems
In today’s interconnected digital ecosystem, the security of a single organization doesn’t solely depend on its internal defenses. As the saying goes “A chain is no stronger than its weakest link.” an organization’s security is increasingly influenced by the security postures of numerous vendors within its supply chain. Attackers, recognizing this, often bypass robust cybersecurity defenses by exploiting vulnerabilities in comparably less secure, supporting vendor infrastructure.
In light of the interconnectedness of modern business ecosystems, recent supply chain attacks have underscored the critical importance of securing internal systems and the extended network of vendors and partners. These attacks remind us of the vulnerabilities inherent in supply chains and the potential for cascading disruptions across industries. Understanding the nature of these attacks and their implications is paramount for organizations seeking to bolster their cybersecurity posture and mitigate risks effectively.
Let’s delve into some significant examples highlighting the evolving threat landscape and the imperative for proactive supply chain security measures.
SolarWinds Supply Chain Attack (December 2020)
In late 2020, the SolarWinds Attack, a colossal cyber-espionage campaign, sent shockwaves through the cybersecurity world. Exploiting vulnerabilities in SolarWinds’ Orion platform, threat actors, notably APT29 (Cozy Bear), orchestrated a sophisticated infiltration.
Their tactics included inserting a SUNBURST backdoor into the software and deploying another malware, SUPERNOVA, separately onto servers. This dual-pronged attack enabled them to breach the defenses of numerous government agencies and organizations worldwide. More than 18,000 customers of SolarWinds had applied the Sunburst update, which then allowed the remote access trojan to infect all their customer systems and networks. Among the affected were critical institutions such as the US Treasury and the Department of Commerce, underscoring the attack’s severity and reach. The incident laid bare the inherent vulnerabilities in supply chain security, emphasizing the need for robust defense strategies across interconnected networks.
For more information about the Solarwinds Supply Chain Attack, visit our blog post.
SmoothOperator Supply Chain Attack Targeting 3CX VOIP Desktop Client (July 2021)
The SmoothOperator supply chain attack targeted the 3CX VOIP desktop client, compromised by a North Korean hacker group known as UNC4736, purportedly affiliated with the APT group Lazarus. This incident marked a significant milestone as the first-ever double supply chain attack involving compromised software chains of both 3CX and X_TRADER, a discontinued trading platform.
The attack, characterized by its complexity, involved the deployment of malware strains such as TAXHAUL, Coldcat, and a backdoor named VEILEDSIGNAL, impacting systems running on both Windows and macOS operating systems. The repercussions of this attack were far-reaching, affecting prominent clients including American Express, AirFrance, BMW, and Coca-Cola. With over 242,519 potentially compromised IP addresses, the attack posed a serious threat to the privacy and security of these organizations, leading to concerns about the theft of user credentials and sensitive data.
For more information about the SmoothOperator Supply Chain Attack, visit our blog post.
MOVEit Transfer Supply Chain Attack (May 2023)
In May 2023, CL0P emerged in the cybersecurity landscape by exploiting a zero-day vulnerability found in MOVEit Transfer (CVE-2023-34362). MOVEit Transfer, a managed file transfer software developed by Progress, became susceptible to remote code execution and data theft via SQL injection due to the vulnerability. MOVEit swiftly reported the vulnerability and deployed a patch on May 31, 2023.
The notorious CL0P Ransomware group capitalized on this vulnerability to initiate a series of cyberattacks. Notable victims of CL0P’s MOVEit Transfer campaign included Gen Digital, the parent company of Avast, Norton, AVG, and Avira, as well as PwC, Ernst & Young, and Medibank.
Following the initial exploit, another vulnerability, CVE-2023-35036, surfaced, compounding the impact of CL0P’s actions. Since the first disclosure, CL0P’s activities have affected 595 organizations and over 30 million individuals, underscoring the widespread consequences of these cyber incidents.
For more information about the MOVEit Transfer Supply Chain Attack, visit our blog post.
Considering the far-reaching effects of supply chain attacks, the interconnectedness in today’s digital ecosystem highlights a critical need for organizations to broaden their security focus, extending it beyond their own perimeters to actively assess and strengthen the security posture of their vendors.
Addressing this pressing need, SOCRadar has developed the Supply Chain Intelligence module, embodying a threat-focused approach that prioritizes the understanding and mitigation of real-world threats organizations face. By offering a holistic and proactive methodology, SOCRadar Supply Chain Intelligence transcends traditional boundaries, providing game-changing features that enhance organizational security in an interconnected world. With this module, you can assure your supply chain security and focus on your core business with peace of mind.
As we delve deeper into the capabilities of the Supply Chain Intelligence module, we extend a warm invitation for you to embark on a journey of discovery. Let’s explore how these advanced features can revolutionize your organizational security landscape.
Discover the Powerful Features of Supply Chain Intelligence
SOCRadar’s Supply Chain Intelligence module stands as a beacon of innovation in the cybersecurity landscape, offering a comprehensive suite of features designed to fortify the security posture of organizations globally.
With rich insights into over 50 million companies across 373 sectors in 249 countries, this tool empowers organizations with unparalleled visibility into their supply chain security.
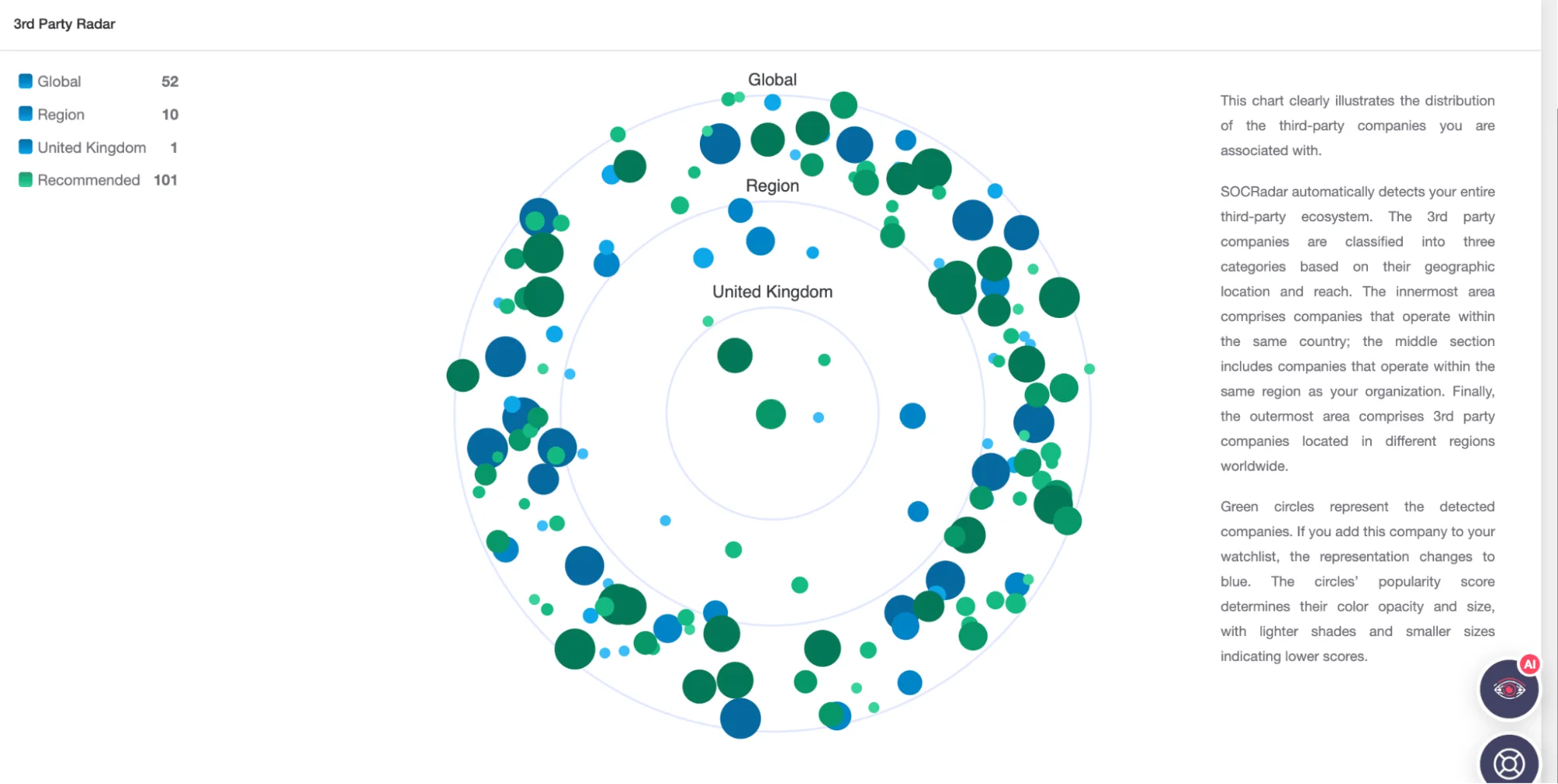
SOCRadar Supply Chain Intelligence – 3rd Party Radar
By automating the mapping process and generating actionable recommendations, the module ensures that organizations are informed and equipped to take decisive action. Additionally, the Supply Chain Intelligence module keeps you at the forefront of cybersecurity news by providing updates on the latest developments, trends, and incidents that could impact your operations.
The Analytics Board, an advanced feature of the module, allows for effortless monitoring of third-party firms and in-depth analysis of global trends, ensuring that strategic decisions are informed by comprehensive data. Real-time updates and continuous monitoring are core to the module’s offering, keeping organizations abreast of the evolving threat landscape.
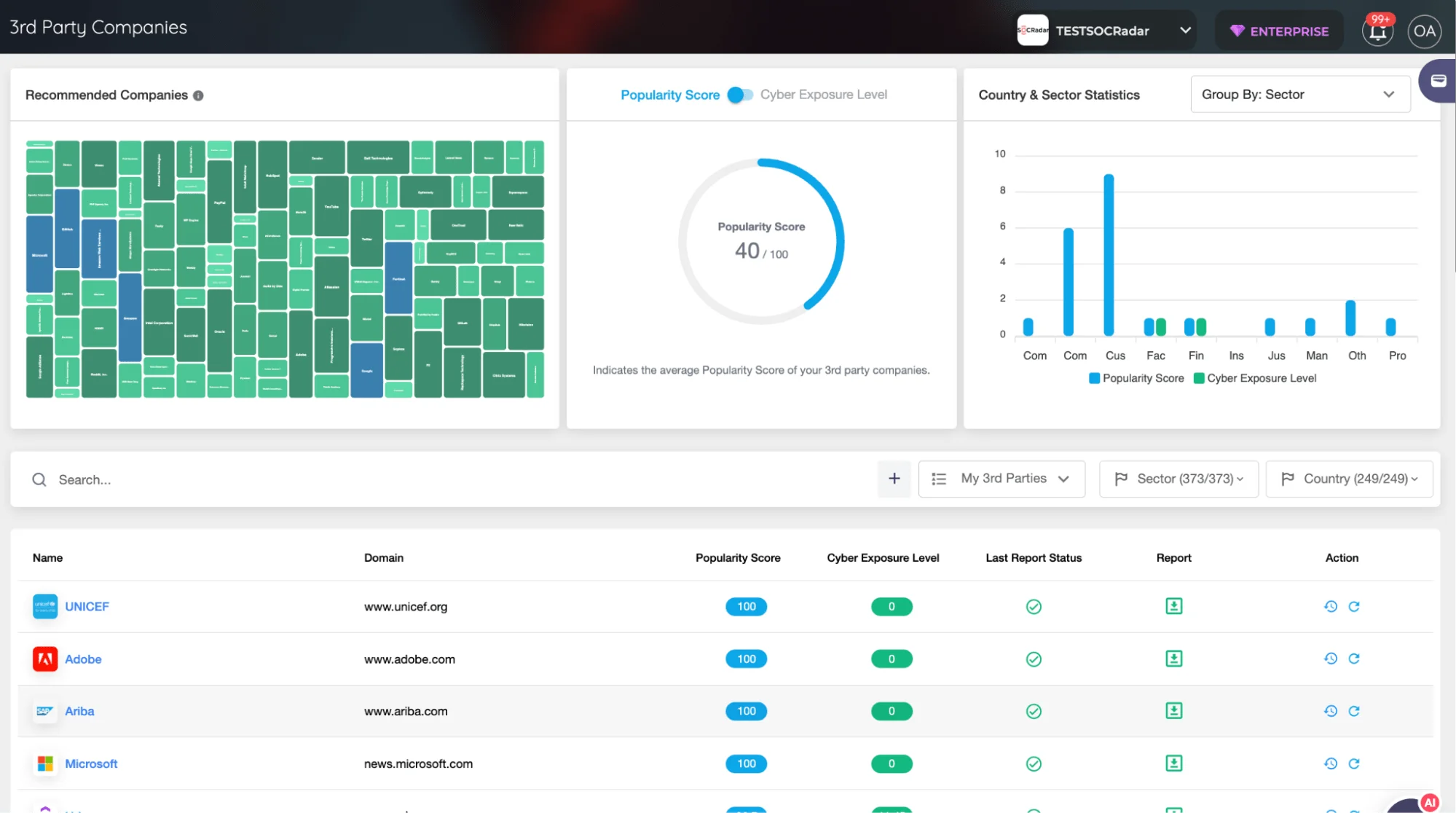
SOCRadar Supply Chain Intelligence – 3rd Party Companies
A sophisticated alarming system alerts you to critical events, potential risks, or noteworthy developments, enabling a proactive security posture. Moreover, it delivers comprehensive, up-to-date security reports on third-party vendors, offering deep insights into their operations and cybersecurity posture.
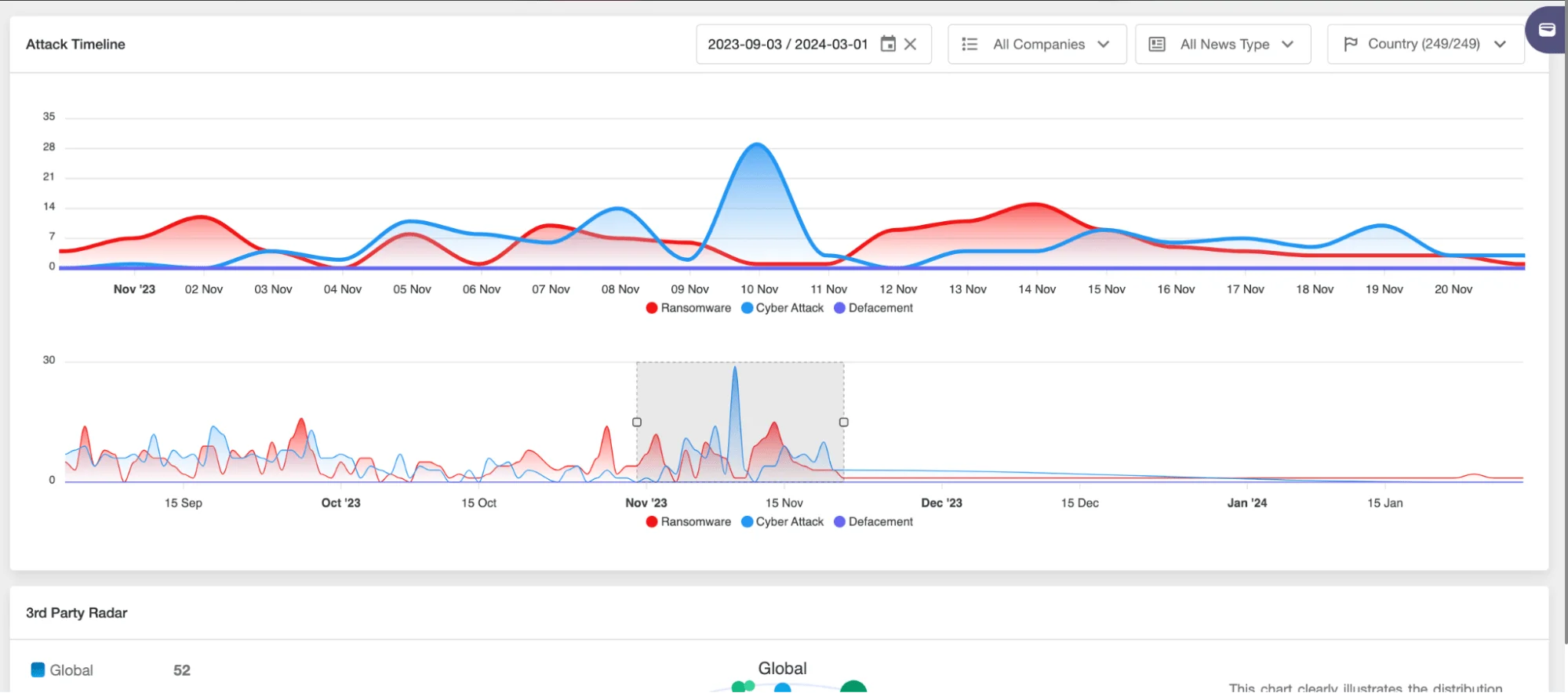
SOCRadar Supply Chain Intelligence – The Attack Timeline
A distinguishing aspect of SOCRadar’s Supply Chain Intelligence is its advanced scoring mechanisms for third-party companies, including the Cyber Exposure Level and Popularity Score. These mechanisms, alongside the creation of tier groups, form the cornerstone of a priority intelligence requirements approach.
This approach emphasizes the importance of focusing on suppliers that are not only crucial to business operations but also play a key role in achieving strategic goals, thereby offering a path to resilience and strategic advantage in the face of global cybersecurity threats.
Conclusion
In conclusion, as organizations increasingly rely on third parties like vendors, suppliers, contractors, and partners, the need for effective third-party risk management becomes paramount. The rise of supply chain attacks and expanding attack surfaces underscore the importance of Cyber Threat Intelligence in supply chain security, making the Supply Chain Intelligence module an indispensable component of every organization’s cybersecurity strategy.
Integrating Supply Chain Intelligence into your cybersecurity infrastructure is not just a recommendation, but a necessity to stay ahead of the evolving threat landscape. To discover how SOCRadar’s Supply Chain Intelligence can transform your cybersecurity approach, book your demo today and take the first step toward comprehensive supply chain security.




































