The Role of Ethical Hackers in Cybersecurity: Protecting the Digital World
With cyber threats emerging at an unprecedented rate, ethical hackers play an important role in detecting vulnerabilities before criminal attackers exploit them.
Ethical hacking, often known as penetration testing or white-hat hacking, entails employing hacking techniques to identify security holes and reinforce defenses. Unlike cybercriminals, ethical hackers work with permission and follow a stringent code of conduct to improve cybersecurity without causing harm.
What is Ethical Hacking?
Ethical hacking is the process of probing computer systems, networks, and applications in order to identify vulnerabilities and address security risks before cybercriminals exploit them. Ethical hackers have the same skills as black-hat hackers, but they use them for defensive purposes. They collaborate with organizations to conduct controlled simulations of cyberattacks, allowing security teams to strengthen their systems against real-world threats.
Ethical hacking encompasses methodologies other than penetration testing, such as vulnerability assessments, malware analysis, and risk mitigation. These professionals assist businesses in complying with security regulations, safeguarding sensitive data, and improving overall security postures.
Ethical vs. Unethical Hacking
Ethical hackers follow legal and professional guidelines, making sure that their actions benefit rather than harm organizations. They obtain explicit permission before conducting tests, avoid causing system damage, and keep their findings confidential.
In contrast, unethical hackers, also known as black-hat hackers, exploit vulnerabilities for financial gain, cyber espionage, or disruption.
Gray-hat hackers operate in a gray area, exposing security flaws without permission, which can have both positive and negative consequences.
The Computer Fraud and Abuse Act (CFAA) was enacted to criminalize unauthorized access to computer systems, separating ethical hacking from illegal activity. Ethical hackers ensure that they follow legal guidelines while assisting organizations in protecting themselves from cyber threats.
Penetration Testing: A Key Ethical Hacking Tool
Penetration testing, or pentesting, is one of the core techniques ethical hackers use to simulate real-world cyberattacks and uncover vulnerabilities in systems before malicious actors do. While often used interchangeably with ethical hacking, pentesting is actually a subset of it. Penetration testers typically operate within a clearly defined scope, which usually includes specifying the systems to be tested, the types of tests allowed, the duration of the engagement, and the rules of engagement to avoid disrupting critical operations.
They target specific systems and produce detailed reports to help organizations remediate discovered risks.
Ethical hackers go beyond pentesting, using a wide array of tools and methods, like social engineering, vulnerability scanning, and malware analysis, to assess security more comprehensively. Pentesting remains essential in this toolkit, especially when powered by threat intelligence.
Modern pentests that leverage data from stealer logs, dark web leaks, and real adversary tactics offer more realistic simulations, helping organizations not just meet compliance requirements but build true cyber resilience.
Introducing Red Teaming: Going Beyond Pentesting
Where penetration testing focuses on identifying vulnerabilities, red teaming dives deeper into how attackers might exploit those vulnerabilities under real-world conditions. It’s a form of ethical hacking where specialists simulate adversaries—using advanced Tactics, Techniques, and Procedures (TTPs)—to challenge an organization’s entire security ecosystem.
Red teaming differs from pentesting in scope and strategy:
- Pentests are often short-term, technical, and checklist-based.
- Red team engagements simulate complex attacks over days or weeks, targeting people, processes, and technology.
Red teams act like determined threat actors. They don’t just look for vulnerabilities—they exploit them to understand how far an attacker could go. These engagements often include:
- Social engineering, such as phishing or impersonation
- Physical security testing, like attempting unauthorized building access
- Network and application attacks, including lateral movement and privilege escalation
- Endpoint and defense evasion, such as bypassing EDR or firewalls
By emulating real-world adversaries, red teams help organizations uncover blind spots in detection, response, and recovery. At the end of each engagement, the red team delivers a detailed readout with practical recommendations for closing security gaps.
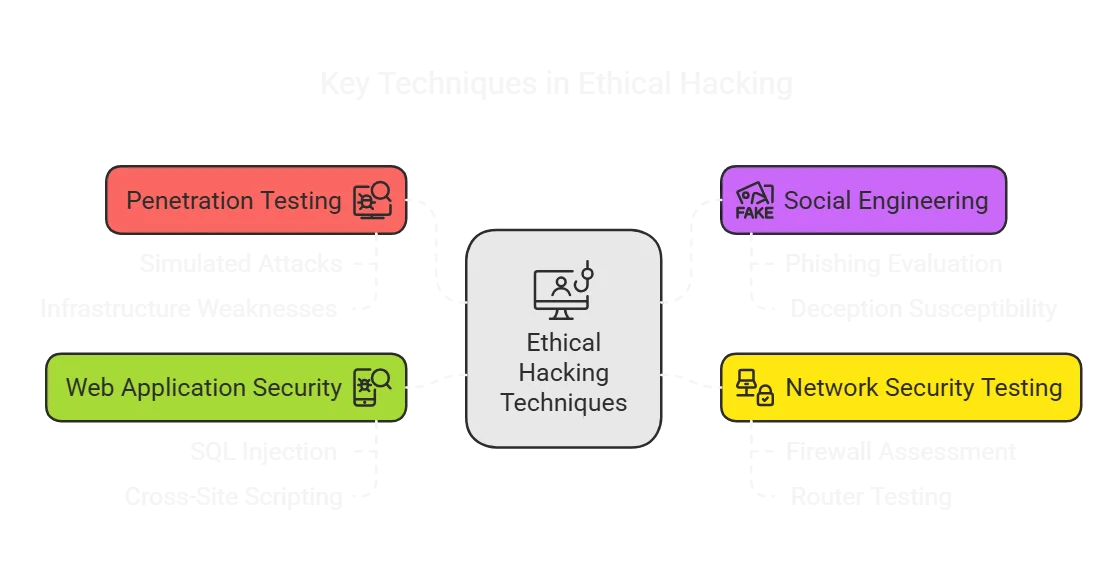
Key Techniques in Ethical Hacking
Ethical hackers use various methods to assess and enhance security, including:
- Penetration Testing: Simulating cyberattacks to identify weaknesses in security infrastructure.
- Social Engineering: Evaluating how susceptible employees are to phishing and deception-based attacks.
- Network Security Testing: Assessing firewalls, routers, and network defenses for potential breaches.
- Web Application Security: Identifying common vulnerabilities such as SQL injection and cross-site scripting (XSS).
Skills and Certifications for Ethical Hackers
To be effective, ethical hackers require a deep understanding of cybersecurity principles, programming, networking, and operating systems. Proficiency in platforms like Kali Linux, and tools like Metasploit and Wireshark is essential.
Many ethical hackers obtain certifications to validate their expertise. Some of the most recognized credentials include:
- Certified Ethical Hacker (CEH): Offered by EC-Council, this certification covers penetration testing techniques and cybersecurity fundamentals.
- Offensive Security Certified Professional (OSCP): Focuses on real-world penetration testing skills and hands-on exploitation techniques.
- CompTIA PenTest+: Covers penetration testing, vulnerability assessment, and management skills.
- SANS GIAC Penetration Tester (GPEN): Specializes in advanced penetration testing and ethical hacking methodologies.
The Growing Demand for Ethical Hackers
As cyber threats increase, organizations across industries are prioritizing cybersecurity investments. Ethical hackers are in high demand in sectors such as finance, healthcare, government, and e-commerce, where data protection and compliance are crucial. Companies recognize the value of ethical hacking in mitigating risks, preventing data breaches, and ensuring regulatory compliance.
How to Start a Career in Ethical Hacking
Aspiring ethical hackers should focus on developing technical skills in programming (Python, C++, Java), networking, and cybersecurity concepts. Gaining hands-on experience through ethical hacking platforms like Hack The Box and TryHackMe and bug bounty programs.
A structured approach includes:
- Building foundational knowledge in IT and cybersecurity.
- Learning ethical hacking techniques and tools.
- Earning relevant certifications.
- Gaining practical experience through security assessments and vulnerability research.
Strengthen Your Security Posture with SOCRadar’s Threat Hunting and Takedown Services
While ethical hackers reveal critical weak points and help organizations build stronger defenses, long-term security demands a shift from reactive measures to proactive strategies. That’s where SOCRadar’s Threat Hunting and Integrated Takedown services come into play—empowering security teams to detect and dismantle threats before they cause damage.
Stay One Step Ahead with SOCRadar Threat Hunting
SOCRadar’s Threat Hunting module is designed to do more than detect active threats—it helps you anticipate them. This forward-leaning approach sifts through massive volumes of data across dark web forums, messaging platforms like Telegram and Discord, and obscure cybercriminal communities to uncover hidden risks and adversarial movements.
By proactively identifying subtle indicators of compromise and malicious activity, SOCRadar transforms passive monitoring into strategic foresight. With precision filtering and behavior-based analytics, every alert becomes actionable intelligence—helping your security team respond swiftly and decisively.
In a digital landscape where timing is everything, agility matters. SOCRadar’s threat hunting delivers dynamic responses to emerging threats, arming your team with the insights needed to secure critical systems, sensitive data, and digital assets before attackers make their move.
Protect Your Brand with Integrated Takedown Capabilities
Your brand’s integrity is just as important as your infrastructure. That’s why SOCRadar’s Integrated Takedown service focuses on neutralizing digital deception at its source—counterfeit websites, impersonating domains, and fraudulent content that threaten your online identity.
From phishing scams that exploit your logo to cloned domains impersonating your business, digital impersonation can severely damage your brand’s reputation and erode customer trust. SOCRadar’s takedown service provides a responsive, targeted solution—identifying, verifying, and removing threats with speed and accuracy.
Whether you’re facing brand spoofing, domain hijacking, or malicious social impersonation, this service ensures your digital presence remains authentic, secure, and aligned with your brand’s values.
The Future of Ethical Hacking
With advancements in artificial intelligence and the growing complexity of cyber threats, ethical hacking will continue to evolve. Organizations will increasingly rely on ethical hackers to combat sophisticated attack methods, including AI-driven cyberattacks and deepfake phishing scams. As cybersecurity landscapes shift, ethical hackers will need to adapt by expanding their skill sets and staying ahead of emerging threats.
However, while ethical hacking reveals critical vulnerabilities, maintaining long-term security requires real-time visibility into the full scope of your digital exposure. That’s where SOCRadar XTI (Extended Threat Intelligence) becomes indispensable.