
The Role of Honeypots in Cybersecurity
In the constantly evolving landscape of cybersecurity, organizations employ a variety of tools and strategies to detect and defend against cyber threats. One particularly intriguing method is the use of honeypots—decoy systems designed to lure cyber attackers and gather intelligence on their tactics. By posing as legitimate targets, they allow security teams to gain valuable insights into malicious activities, helping organizations enhance their defenses.
This article will explore the concept of honeypots, how they work, the different types available, and their practical applications in cybersecurity.

AI illustration of honeypots
What Is a Honeypot?
A honeypot is a deliberately vulnerable computer system or network designed to attract cyber attackers. It serves as a trap to detect, deflect, or study hacking attempts. Unlike traditional security tools like firewalls and intrusion detection systems that focus on keeping attackers out, honeypots aim to invite attackers in so their actions can be observed and recorded in a controlled environment.
A honeypot mimics the behavior of a real system, such as a web server, database, or an IoT device, to deceive attackers. However, it contains no valuable information, making it a low-risk way to observe cybercriminal behavior. The information gathered from attacks with this method can be used to improve threat detection and bolster defenses against real-world threats.
How Does a Honeypot Work?
The core functionality of a honeypot is to simulate a vulnerable system or network. When attackers attempt to breach it, their actions are monitored closely, and all their movements—such as the type of malware they use, vulnerabilities they exploit, or techniques they deploy—are logged. This data provides security teams with insights into emerging threats and attack vectors.
Honeypots can also serve as early warning systems. If attackers target a honeypot, it may indicate they are preparing to launch a broader attack. This gives defenders time to fortify their actual systems.
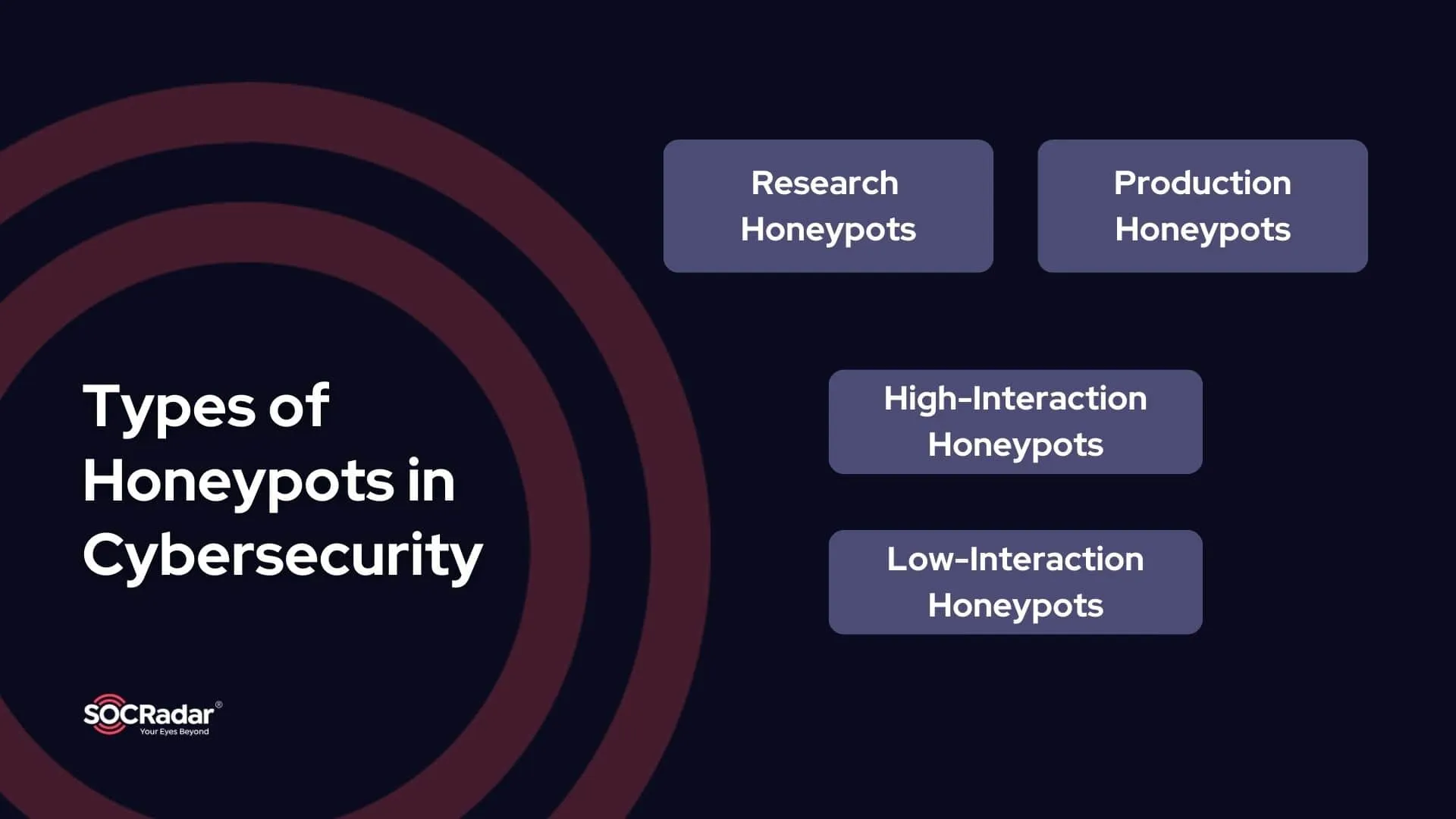
Types of Honeypots in Cybersecurity
Honeypots can be broadly categorized into two types: research and production. Each type serves a unique purpose, contributing to cybersecurity efforts in different ways.
Honeypot types
1. Research Honeypots
Research honeypots are primarily used for gathering intelligence on cyberattacks, attacker behavior, and new threats. Deployed by universities, cybersecurity researchers, and large enterprises, they simulate real-world systems to attract attackers and study their techniques in a controlled environment. These are crucial for advancing cybersecurity knowledge, enabling researchers to identify emerging trends in malware, tools, and attack strategies. The data gathered helps shape future defensive measures and improve existing security technologies.
By analyzing how attackers exploit vulnerabilities and navigate systems, security experts can create more effective defenses. For example, a research honeypot might reveal new types of malware or advanced tactics used by threat actors, offering invaluable insights for developing improved detection and response mechanisms.
2. Production Honeypots
Production honeypots, on the other hand, are used within operational environments to detect and mitigate ongoing threats in real-time. These act as decoy systems embedded in an organization’s network, attracting attackers away from critical assets while security teams monitor and analyze the attackers’ moves. Unlike those for research, which focus on collecting general attack data, production honeypots are designed to be an active part of a company’s defense system, often integrated with Intrusion Detection Systems (IDS).
Production honeypots provide immediate insights into cyber threats targeting an organization’s infrastructure. For instance, when an attacker engages with a production honeypot, it allows security teams to gain real-time information on the attack, enabling a swift response to protect the actual network. These are an essential tool for reducing the risk of data breaches and system compromises by diverting malicious activity away from critical operations.
Further classifications include high-interaction and low-interaction honeypots:
1. High-Interaction Honeypots
High-interaction honeypots emulate real systems with greater complexity, allowing attackers to interact with them extensively. This provides a deeper understanding of an attacker’s behavior, tools, and strategies. However, they are more resource-intensive and can carry higher risks if attackers manage to use them to pivot into actual systems.
Example: A high-interaction honeypot could be a fully functional web application, allowing attackers to explore vulnerabilities, try exploits, and deploy malware, while security teams monitor every move.
2. Low-Interaction Honeypots
Low-interaction honeypots simulate basic services and provide limited engagement with attackers. They are relatively simple to set up and maintain but only offer a superficial view of an attacker’s methods. These are typically used to detect automated attacks like botnets or worms.
Example: A low-interaction honeypot might mimic an FTP or SSH server, recording login attempts and the credentials used by attackers.
While low-interaction honeypots are effective at detecting automated attacks such as botnets, organizations must also proactively monitor external threats on the dark web to gain deeper insights into potential risks. This is where SOCRadar’s Advanced Dark Web Monitoring comes into play. By scanning dark web forums, stealer logs, and underground chatter, SOCRadar enables organizations to detect early signs of compromised data, including stolen credentials or botnet activity that could be targeting their systems.
SOCRadar’s Botnet Data real-time monitoring
Advantages of Using Honeypots
- Enhanced Threat Intelligence: Honeypots offer real-time insights into attackers’ Techniques, Tactics, and Procedures (TTPs), helping organizations stay ahead of emerging threats.
- Early Detection: By detecting and analyzing attacker activities early in the attack chain, a honeypot can provide critical intelligence that can be used to strengthen security measures before real systems are compromised.
- Resource Efficiency: Honeypots only engage with malicious traffic, reducing the noise of false positives commonly seen in other security tools, making them a cost-effective solution for detecting threats.
- Learning Opportunity: They provide an educational tool for cybersecurity professionals to learn more about real-world attacks in a controlled and safe environment.
Popular Honeypot Platforms
In the world of cybersecurity, there are a variety of honeypot platforms available to assist organizations in effectively deploying, managing, and monitoring decoy systems. The following are two widely recognized honeypot platforms:
1. T-Pot

T-Pot banner (Source:GitHub)
Deutsche Telekom developed T-Pot, an open-source honeypot platform that allows you to quickly create a comprehensive honeypot environment. It combines multiple honeypots, including Cowrie and Dionaea, into a single system, allowing security teams to monitor multiple attack vectors at once. T-Pot’s versatility makes it appropriate for both research and production environments, and its user-friendly dashboard allows for real-time analysis of active attacks.
T-Pot is especially useful for security teams looking to gather detailed threat intelligence on a variety of attacks, including botnets and malware.
2. Cowrie
Cowrie is a popular high-interaction honeypot that simulates a fully functional SSH and Telnet environment. Cowrie, which was originally designed to capture brute-force attacks and collect data on attacker behavior, has grown in popularity among researchers and organizations due to its ability to simulate real systems in a secure manner. Cowrie’s log of all interactions between attackers and the honeypot provides detailed insights into how cybercriminals attempt to exploit vulnerabilities.
Cowrie’s ease of deployment and robust logging capabilities make it an ideal choice for organizations looking to learn more about unauthorized network access attempts.
T-Pot and Cowrie are powerful tools for organizations looking to implement honeypot strategies, providing valuable data on attacker tactics and potential system vulnerabilities.
Risks and Limitations of Honeypots
While they provide many benefits, they come with certain risks and limitations:
- Attracting Advanced Threats: High-interaction honeypots can attract sophisticated attackers who may use them as launch points for more advanced attacks. Proper isolation and monitoring are critical to prevent these attackers from pivoting into real systems.
- Limited Scope: A honeypot can only detect attacks that target the specific system or services it mimics. It won’t catch attacks aimed at other parts of your infrastructure.
- Maintenance Requirements: Honeypots require ongoing maintenance and updates to stay relevant and effective. Attackers may quickly recognize if they are outdated and avoid them.
Practical Applications of Honeypots
- Network Security: Honeypots are often deployed in corporate networks to detect internal and external threats. They help detect malicious insiders or identify external attackers trying to breach the network.
- Web Application Security: Organizations can use honeypots to monitor and record web-based attacks, such as SQL injection, cross-site scripting (XSS), and brute force attacks. By imitating vulnerable web applications, they also allow security teams to analyze how attackers operate against such systems.
- IoT Security: With the rise of Internet of Things (IoT) devices, honeypots can mimic vulnerable IoT devices to attract attackers and study how they exploit these devices. This is especially useful for understanding botnet activity targeting IoT ecosystems.
- Dark Web Monitoring: Honeypots are also employed to gather intelligence on the dark web. They can be used to lure cybercriminals into revealing their techniques or even to gain insights into underground markets where stolen data and malware are traded.
SOCRadar’s Dark Web Monitoring helps protect organizations from financial fraud, data breaches, and emerging threats. This tool continuously tracks the exposure of Personally Identifiable Information (PII) and scans for mentions of your company in dark web discussions, giving you a head start in mitigating risks before they escalate into full-blown security incidents.
SOCRadar’s Dark Web Monitoring PII Exposure
Conclusion
Honeypots play an important role in modern cybersecurity strategies because they provide unique insights into attacker behavior and act as decoys to divert malicious activity away from critical assets. They help organizations gather valuable intelligence, strengthen defenses, and stay ahead of emerging threats by simulating vulnerable systems. Whether they are used in research to analyze new malware or in production to protect operational environments, continue to be an important tool for improving threat detection and response.
Honeypots are extremely effective, but they should be used as part of a larger, multi-layered defense strategy. When combined with other cybersecurity tools like SOCRadar’s Advanced Dark Web Monitoring and Threat Intelligence solutions, enable organizations to detect threats early on, secure sensitive data, and protect against a wide range of cyber risks.



































