Top 10 Stealer Logs
Stealer logs are a critical concern as they involve the theft of sensitive information from infected systems. These digital threats, primarily aimed at acquiring data such as passwords, credit card details, and cryptocurrency wallets, pose significant risks to both individuals and organizations. As cybercriminals continue to develop more sophisticated methods, understanding and identifying stealer logs becomes essential for enhancing cybersecurity defenses.
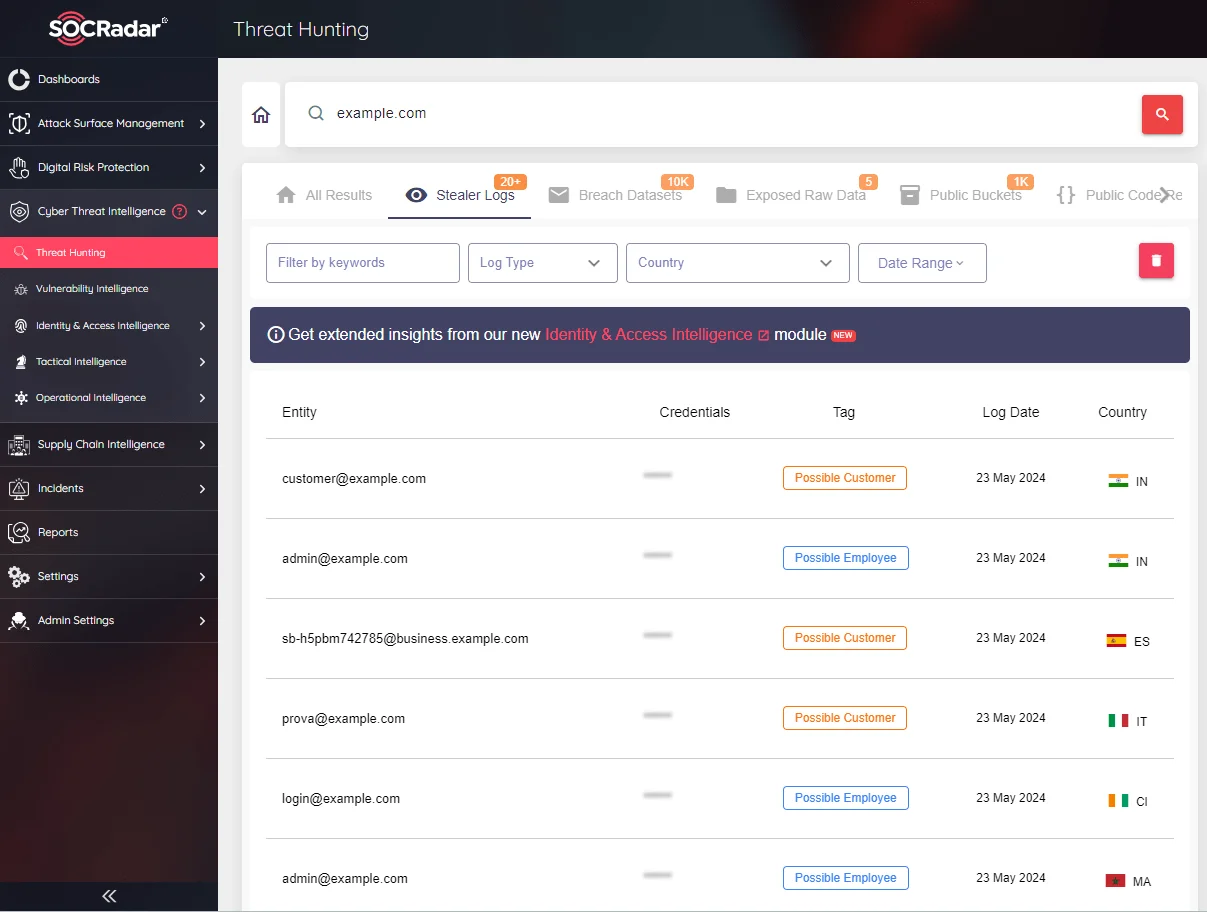
SOCRadar’s Threat Hunting allows you to search within stealer logs
Thus, SOCRadar scrutinizes millions of rows of stealer logs data, enabling its users to perform thorough threat hunting. This article will explore the top stealer logs based on SOCRadar’s data. Let’s get started.
1. Redline
Accounts Stolen: 3.1 Million
Redline, written in C++ and C#, is designed to steal a wide array of sensitive information, including passwords, credit card details, cryptocurrency wallets, browser data (such as cookies and history), and system information. Its capabilities are extensive: it captures every keystroke made by the user (keylogging), extracts data from forms filled out by users (form grabbing), and steals credentials for FTP servers and email accounts. Additionally, it can exfiltrate files from the infected system and supports customizable plugins that allow attackers to add new functionalities. Redline is often employed in targeted attacks aimed at specific victims.
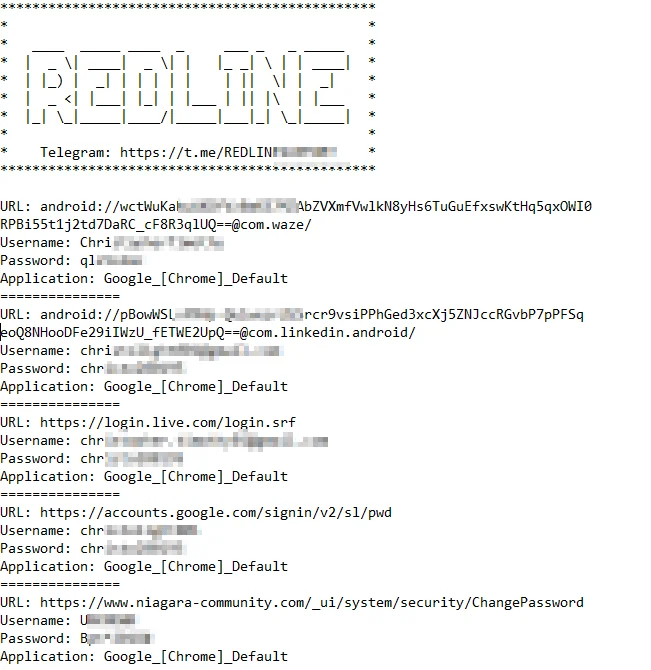
Compromised accounts of a machine through RedLine
To evade detection by antivirus software, Redline employs various obfuscation techniques, making its code harder to read and analyze. It also incorporates anti-analysis methods to avoid detection by security software, ensuring it can operate stealthily within the infected system.
2. Raccoon
Accounts Stolen: 585,800
Raccoon Stealer, written in C++ and recently in C, is a notorious piece of malware adept at stealing a wide range of sensitive information, including passwords, credit card details, cryptocurrency wallets, browser data (such as cookies and history), and system information. Emerging in 2019, it has been widely recognized and extensively used within the cybercriminal community, available for purchase through a subscription model.
Raccoon Stealer’s capabilities include the theft of web browser data, such as cookies, history, and saved passwords, as well as targeting popular cryptocurrency wallet software to steal digital currencies. It also possesses self-spreading capabilities, enabling it to propagate to other systems within a network.
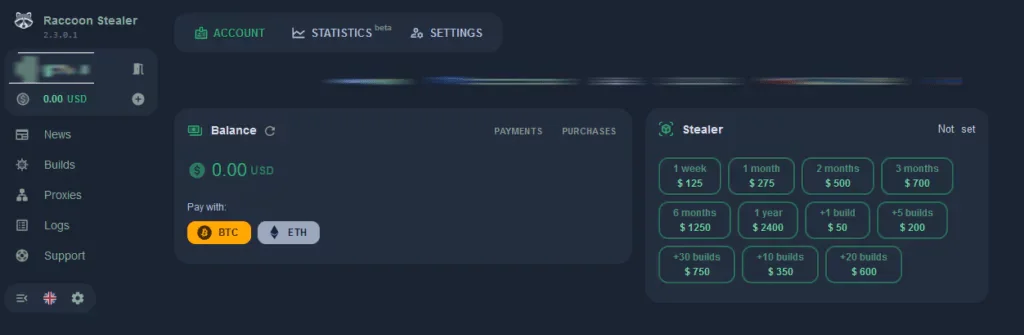
Website of the Raccoon Stealer
To evade detection by antivirus software, Raccoon Stealer employs several sophisticated techniques. It encrypts its code to avoid detection and utilizes polymorphism, which allows it to change its code slightly each time it runs, making it harder for signature-based detection methods to recognize it. The latest version, 2.3.0, introduced in August 2023, includes enhancements such as quick search for cookies and passwords, automatic bot blocking, detailed log statistics, and increased throughput, all aimed at improving the user experience and efficiency of the malware.
3. Meta
Accounts Stolen: 349,400
Meta Stealer is designed to target and exfiltrate sensitive information such as passwords, browser data, and cryptocurrency wallet details. Its capabilities, indicated by high account numbers, suggest a versatile approach to data theft, making it likely capable of stealing various types of information. Specifically, Meta Stealer targets popular wallet software to steal cryptocurrency and demonstrates adaptability, possibly being customizable for different types of attacks.
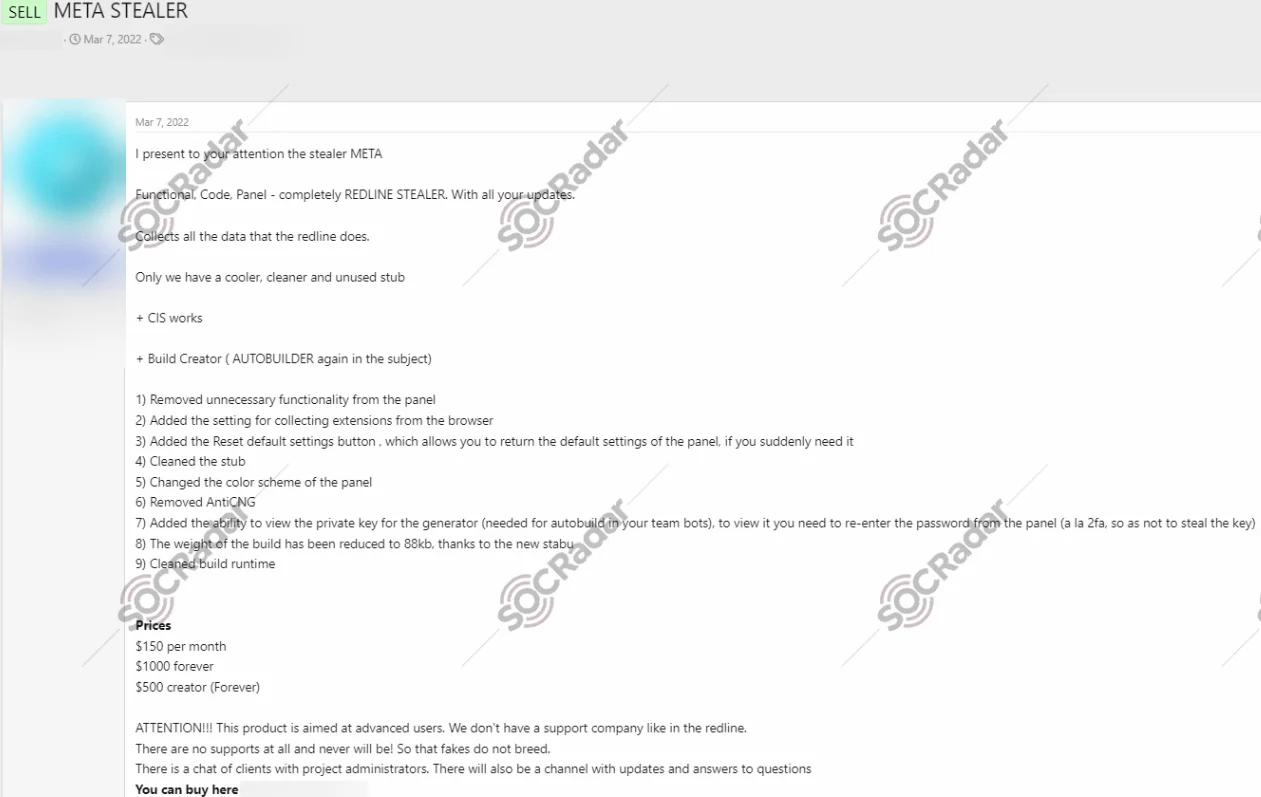
Meta Stealer sale in a hacker forum
In terms of anti-virus (AV) prevention, Meta Stealer employs sophisticated techniques such as obfuscation and anti-analysis methods to avoid detection by security software. Additionally, it often uses malspam campaigns to distribute payloads, including macro-laced Excel spreadsheets that download and execute the malware upon user interaction. Furthermore, the malware utilizes code encryption, allowing it to alter its code to bypass security measures and maintain persistence on infected systems. This includes modifying system settings like Windows Defender to exclude its files from scanning, enhancing its ability to evade detection.
4. StealC
Accounts Stolen: 96,100
StealC Stealer, developed in the C programming language, focuses on targeting a variety of sensitive data, including passwords, browser data, and cryptocurrency wallets. It has the capability to collect information from popular web browsers like Chrome, Firefox, and Opera, as well as from cryptocurrency wallets and desktop applications.
The capabilities of StealC include efficient data theft, allowing it to steal passwords, cookies, browsing history, and other sensitive data from both browsers and applications. It utilizes API resolution dynamically to enhance its functionality, making it adept at adapting to different environments.
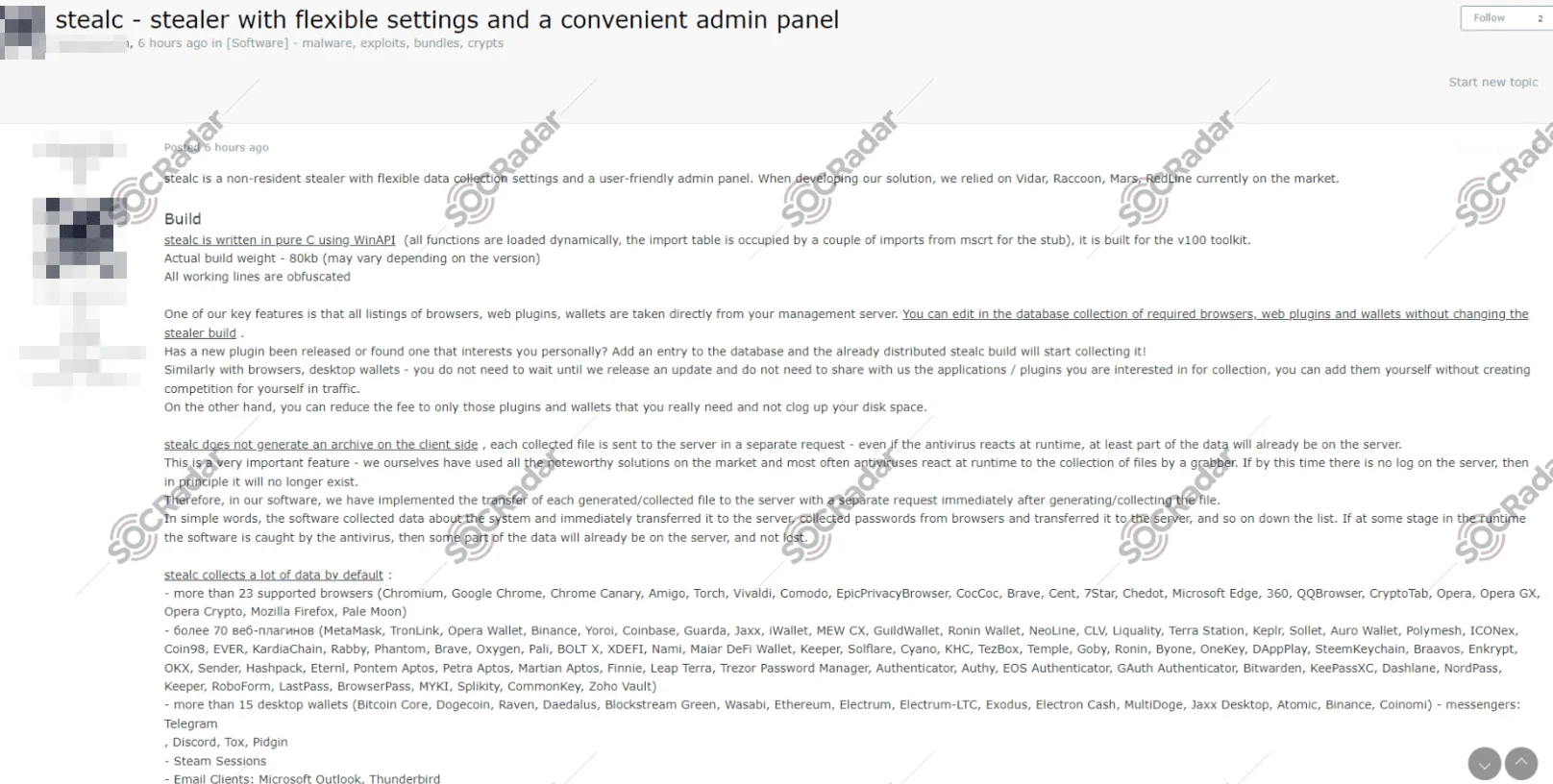
StealC is also disseminated in hacker forums
In terms of anti-virus (AV) prevention, StealC employs sophisticated techniques such as obfuscation and evasion. It utilizes obfuscation techniques along with legitimate Dynamic Link Libraries (DLLs) to evade detection by security software. Additionally, StealC avoids infecting systems based on certain criteria, such as geographical location, further enhancing its ability to evade detection and maintain stealth while carrying out its malicious activities.
5. Mystic
Accounts Stolen: 60,800
Mystic Stealer emerged in April 2023, offering a sophisticated tool for stealing valuable information. It targets a wide range of data sources, including over 40 web browsers, 70 browser extensions, cryptocurrency wallets, Steam, and Telegram. The malware employs heavy code obfuscation techniques like polymorphic string obfuscation and hash-based import resolution to evade detection.
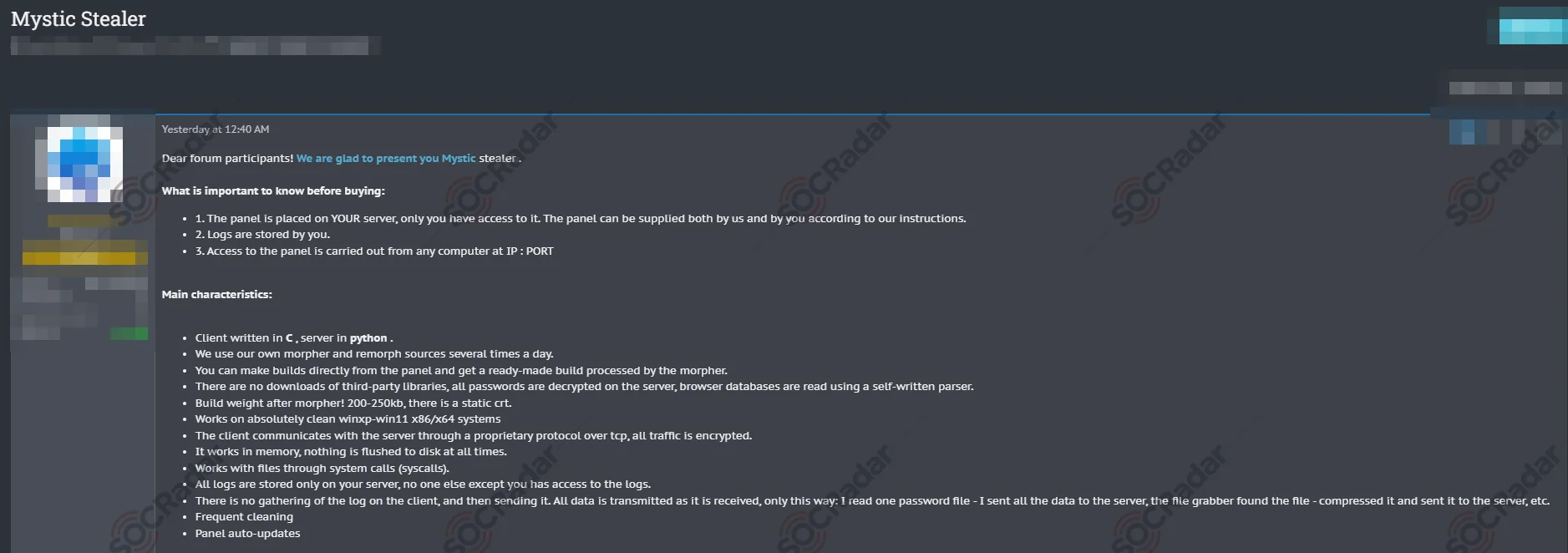
Mystic Stealer has been put on a sale in different forums by the same threat actor
Communication with its command and control (C2) servers is done through a custom encrypted binary protocol, ensuring data security during transmission. Mystic Stealer’s technical capabilities include collecting system metadata, browser data, cryptocurrency wallet information, and more.
Developed in C for the client-side and Python with Django for the control panel, Mystic Stealer incorporates anti-analysis measures such as binary expiration, anti-virtualization techniques, and dynamic constant calculation to thwart analysis attempts.
The malware communicates with distributed C2 servers, leveraging various hosting services that include reputable providers and potentially bulletproof hosting. Its introduction to underground forums in April 2023 indicates the high demand for such information-stealing tools in the cybercrime ecosystem.
6. Hawklog
Accounts Stolen: 57,800
This time it is not a stealer malware, but a private cloud group that disseminates stealer data. Hawklog, ranked 6th on the SOCRadar’s stealer repository, was sharing stealer logs data at regular intervals by offering monthly or weekly memberships to this group, but this data was also distributed by other threat actors.

An advertisement of Hawklog in a Telegram channel
In January 2024, a significant security breach was uncovered affecting the private cloud service Hawklog. The breach, attributed to the hacker group Mooncloud, resulted in the exposure of a massive amount of sensitive data totaling around 1.71GB, primarily comprising emails. The breach occurred within Telegram channels.
7. Taurus
Accounts Stolen: 42,400
In early June 2020, a new malware campaign named Taurus, developed by the “Predator the Thief” cybercriminal group, caught the attention of cybersecurity researchers. This stealer, available for sale on dark forums for $100 or with a new domain for $20, was designed to evade detection and steal sensitive information from victim systems.
Taurus boasts a range of capabilities, including the theft of passwords, cookies, autofill forms, and browsing history from Chromium- and Gecko-based browsers. It can also target popular cryptocurrency wallets, FTP client credentials, and email client credentials. Additionally, Taurus collects system information such as installed software and system configuration, sending this data back to the attacker.
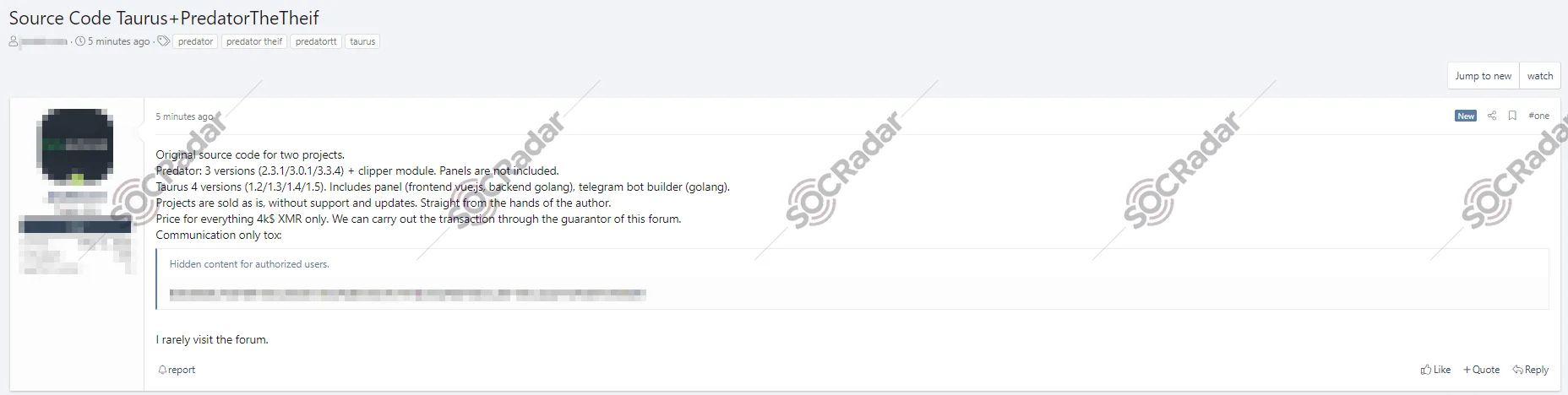
While Taurus was first offered for sale and service on hacker forums, its source code later appeared on hacker forums
The malware employs obfuscated code and anti-sandbox techniques to evade detection and analysis. It performs checks for sandbox environments, internet connectivity, specific files, and system information before proceeding with its malicious activities. Taurus also includes a fileless approach, compressing stolen data into a Zip file directly within memory before attempting to send it to a Command and Control (C&C) server.
8. Nexus
Accounts Stolen: 39,700
Nexus Stealer had emerged as another stealer in the cybercriminal realm in 2020, offering a comprehensive suite of capabilities aimed at extracting sensitive information from a diverse range of sources. Initially introduced on an underground forum, Nexus Stealer garnered attention for its extensive feature set tailored to the data theft objectives of malicious actors.
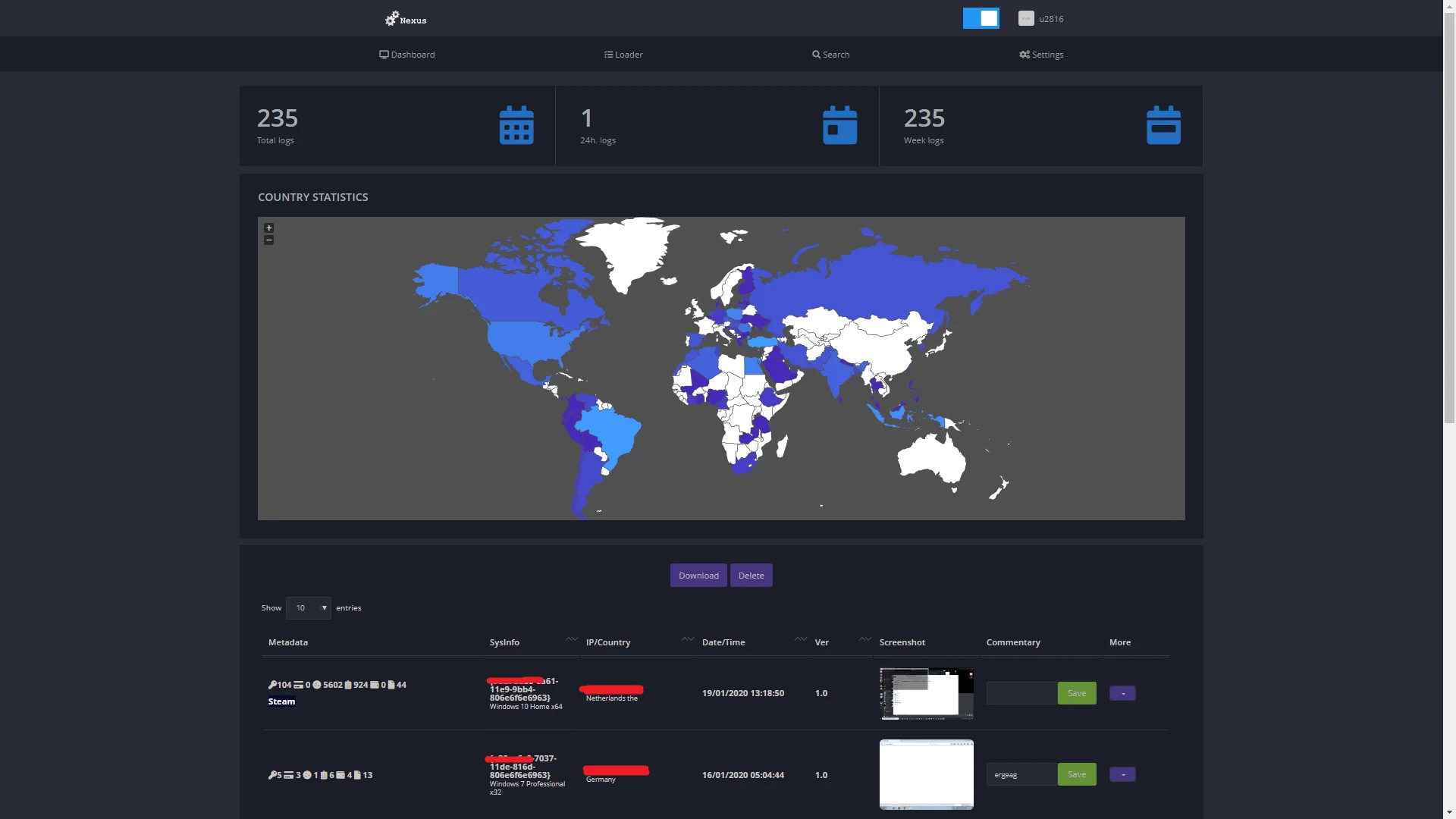
Nexus Stealer Dashboard (fr3d.hk)
Upon its release, Nexus Stealer was marketed as a versatile tool capable of targeting various applications and platforms commonly used by individuals and organizations. Its target list included popular web browsers like Chromium and Yandex-Browser, messaging platforms such as Authy, Telegram, Discord, and Steam, file transfer protocols like FileZilla and WinSCP, as well as other software like WindowsSecureVault, Internet Explorer, Edge, Pidgin, PSI, PSI+, NordVPN, and ProtonVPN. This wide-ranging compatibility made Nexus Stealer a potentially potent threat to a broad spectrum of users.
Functionally, Nexus Stealer operated by infiltrating target systems, harvesting a wide array of data, and transmitting this information to a centralized web panel accessible to threat actors. Its capabilities extend beyond mere data theft, encompassing features like capturing screenshots of infected systems and gathering comprehensive system information such as usernames, hardware profiles, CPU details, GPU specifications, memory status, and installed programs. This holistic approach to data collection allowed Nexus Stealer to create detailed profiles of compromised systems, enhancing its utility for cybercriminal operations.
Despite its initial impact and feature-rich design, Nexus Stealer’s novelty gradually waned as it became more familiar to cybersecurity professionals and security solutions. Over time, security measures evolved, and antivirus software became adept at detecting and neutralizing Nexus Stealer and similar malware variants.
9. Octopus
Accounts Stolen: 24,600
Octopus Scanner made its debut around 2018 and quickly gained notoriety within the cybersecurity community due to its unique method of targeting repositories on GitHub. Unlike traditional malware that targets end-user systems, Octopus Scanner takes aim at software developers by infecting repositories on GitHub. The infection occurs when a developer unwittingly downloads a compromised repository and incorporates it into their software projects. Once integrated, Octopus Scanner acts as a backdoor, enabling its creators to gather sensitive information from the infected systems.
Upon activation, Octopus Scanner conducts a scan on the compromised system to identify the presence of NetBeans IDE, a Java-based integrated development environment. If NetBeans IDE is detected, Octopus Scanner proceeds to infect the build files with a dropper, a type of malware designed to install other malicious software. In Octopus Scanner’s case, the dropper installs a Remote Access Trojan (RAT), granting attackers control over the infected machine.
An important characteristic of Octopus Scanner is its resilience against removal attempts. It prevents the replacement of infected projects with clean versions, ensuring the persistence of the malware. Furthermore, Octopus Scanner not only targets built files but also infects the source code of affected projects, making cleanup and mitigation efforts more challenging.
10. Lumma
Accounts Stolen: 18,800
The LummaC2 Stealer is a malicious program designed to steal sensitive data and install applications on infected devices. It is distributed through underground forums and poses significant risks, targeting operating systems from Windows 7 to Windows 11.
The stealer, typically hidden on infected machines, begins by gathering device details like OS version, CPU, and browsing history from browsers such as Chrome, Firefox, and Edge. It can also target cryptocurrencies and extract information like usernames, passwords, credit card details, and personally identifiable information. This data theft can lead to severe privacy breaches, financial losses, and identity theft.
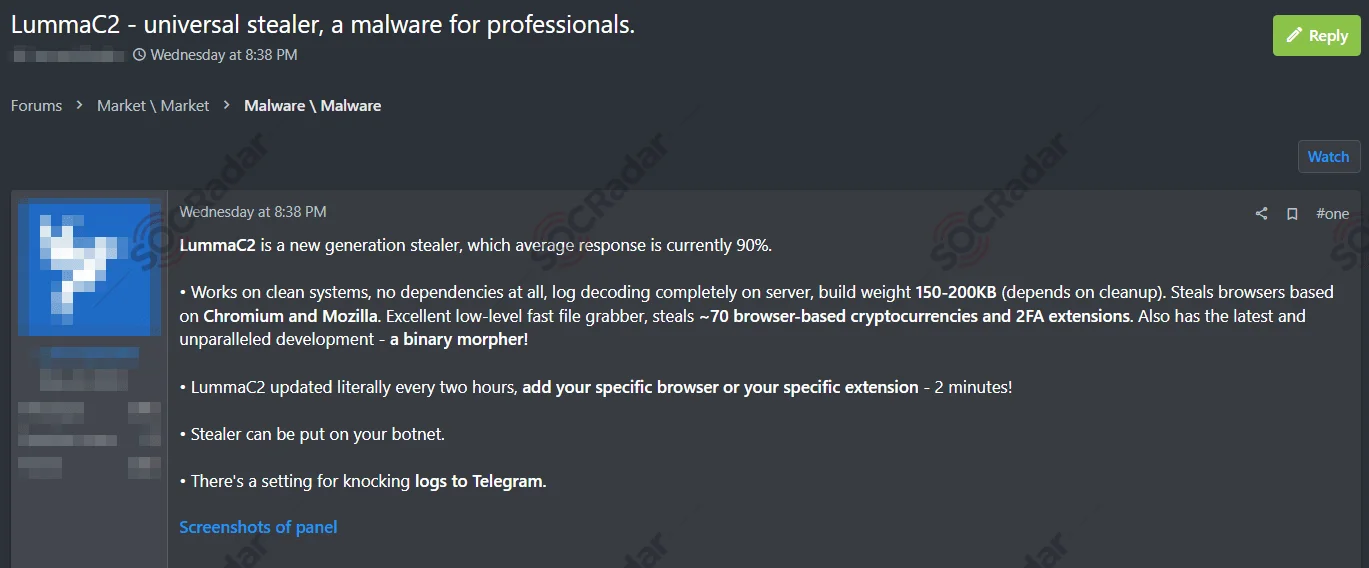
LummaC2 an upgraded version of LummaC was on sale around 2023
Static analysis of LummaC2 reveals its file properties, programming language, and use of anti-debugging techniques. The malware communicates with a remote server, transmitting stolen information as a zip file. Dynamic analysis uncovers its behavior, including bypassing anti-debugging measures and sending data to a designated C2 address.
LummaC2’s recent updates include anti-sandbox techniques using trigonometry, Google cookie revival capabilities, and integration with Discord CDN and API for distribution. These advancements make it more challenging to detect and remove, posing a serious threat to cybersecurity.
Conclusion
The top 10 stealer logs discussed here showcase the diverse capabilities and methodologies employed by cybercriminals to steal sensitive information from individuals and organizations. From well-known threats like Redline to newer entrants, each malware presents unique challenges and requires vigilant defense measures.
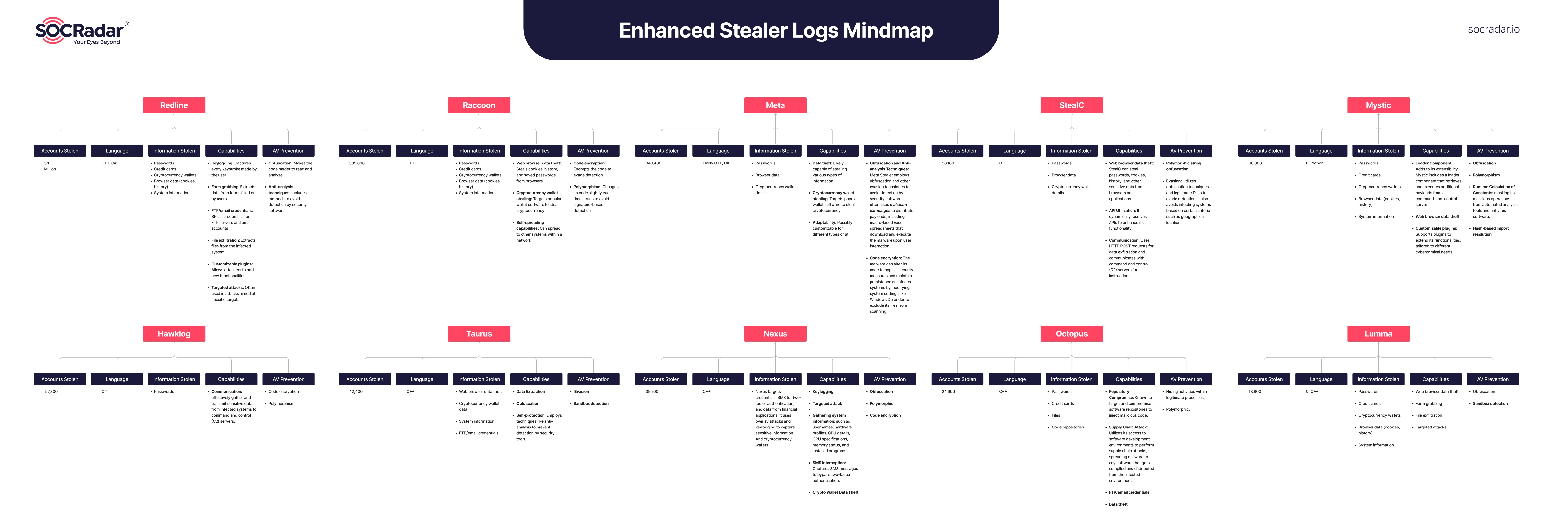
A mind map of the Top 10 Stealer Logs
The analysis of these stealer logs underscores the importance of robust threat hunting capabilities, such as those offered by SOCRadar. Tools that enable deep scrutiny of data volumes and patterns are crucial for early detection and mitigation of these stealthy threats. Moreover, the insights gained from dissecting these malicious programs shed light on the sophistication of modern cyberattacks and the need for continuous improvement in cybersecurity strategies.
As cybercriminals continue to innovate and refine their tactics, collaboration among cybersecurity professionals, threat intelligence platforms, and law enforcement remains paramount. By staying informed, implementing best practices, and leveraging advanced technologies, organizations can better defend against the pervasive threat of stealer logs and safeguard sensitive data from malicious actors.




































