
Why Threat Intelligence is a Game-Changer for Pentesting & Red Teaming
Are You Testing Like a Defender… or Thinking Like an Attacker?
In cybersecurity, the difference between a strong defense and a false sense of security often boils down to how well you understand your adversary. Many organizations rely on Penetration Testing (Pentest) and Red Teaming to uncover weaknesses. But here’s the catch: Most security tests assume attackers play by the same rules as defenders.
Threat actors don’t follow predefined scripts—they adapt, improvise, and exploit the gaps traditional assessments often miss.
That’s where Cyber Threat Intelligence insights come in. They turn conventional security assessments into realistic attack simulations, giving you the upper hand against evolving threats. And if you’re wondering how to elevate your security testing game, our latest whitepaper Unleashing Dark Web Intelligence: Powering Up Red Teaming and Pentesting breaks it all down.

SOCRadar’s whitepaper for revolutionize Red Teaming and Pentesting
Why Traditional Pentesting & Red Teaming Are Falling Short
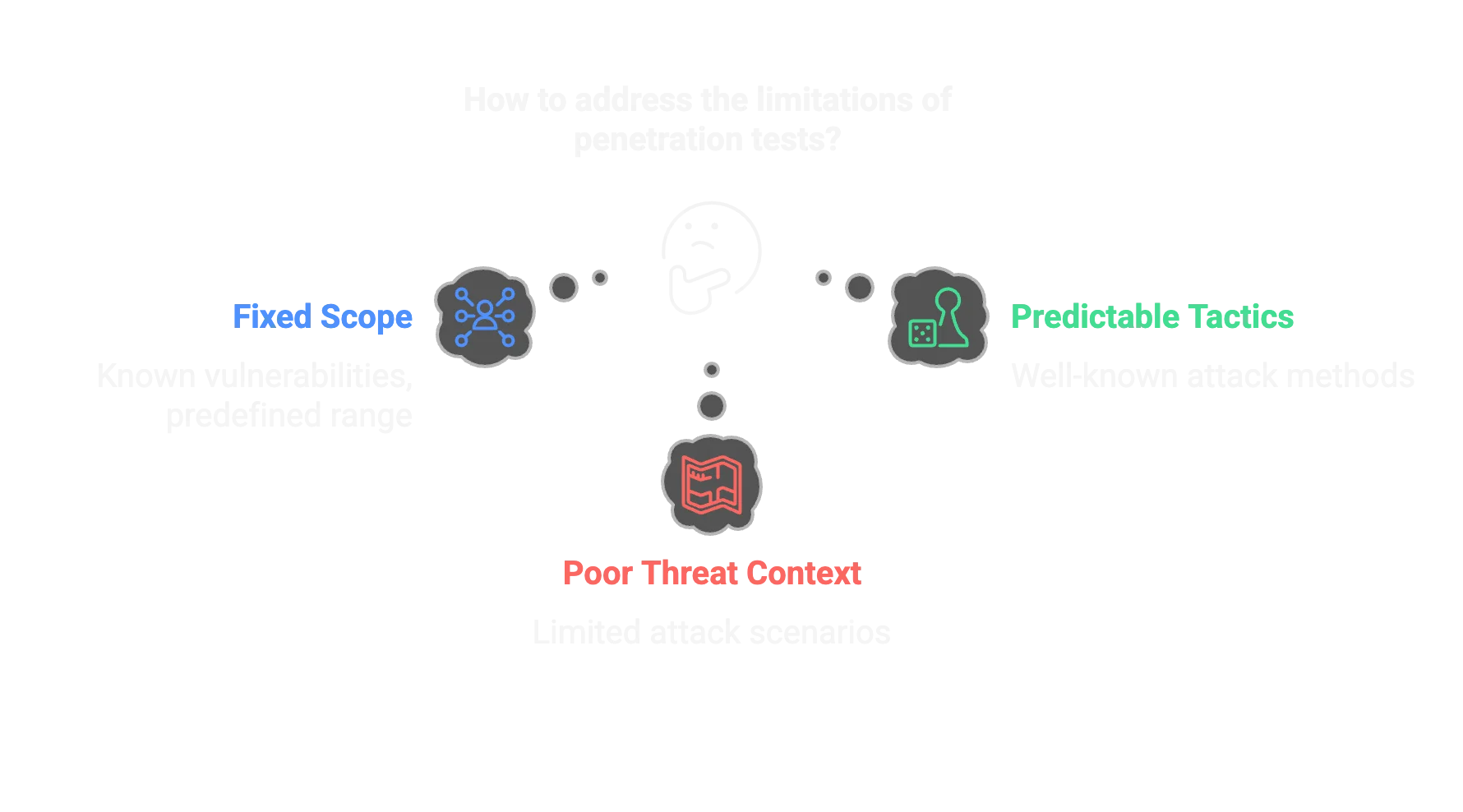
Limitations of Penetration Testing
Traditional penetration testing and Red Teaming exercises provide valuable technical insights, but they often fall short in replicating the tactics of modern cybercriminals. Several key limitations include:
Fixed scope: They focus only on known vulnerabilities within a predefined range.
Predictable tactics: They rely on well-known attack methods.
Lack of real-world threat context: Many fail to incorporate actual attacker behaviors.
Real attackers don’t care about your predefined scope. They don’t use pre-approved tools. They’re constantly evolving, using fresh tactics, stolen credentials, and real-world data leaks.
Consider this: In our latest research, we found that a US cloud security company’s pentest report was publicly exposed on a malware analysis platform! A treasure trove of vulnerabilities, configurations and security gaps, gift-wrapped for threat actors.
This isn’t a hypothetical scenario—this is a real world example, which raises a critical question:
If organizations are not proactively monitoring their own security assessments for leaks, how can they be certain that threat actors aren’t already using their weaknesses against them?
Turning the Tables: Why You Need Threat Intelligence in Your Security Tests
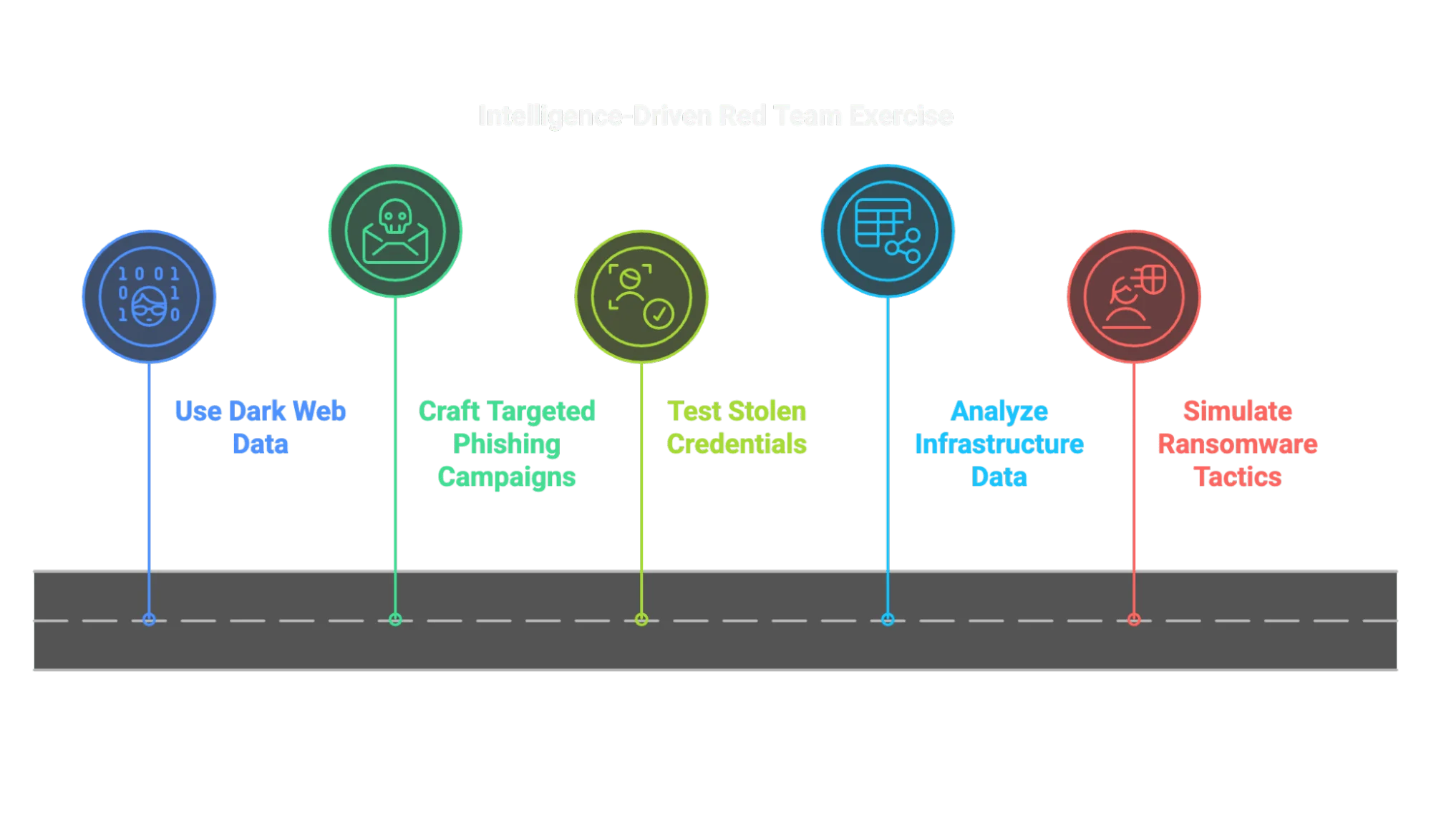
Advantages of Intelligence Driven Security Tests
To bridge the gap between traditional security testing and real-world threats, organizations need to think like adversaries. Intelligence-driven pentesting and Red Teaming incorporate insights from Dark Web marketplaces, stealer logs, leaked credentials, and hacker forums, allowing security teams to:
- Craft targeted phishing campaigns based on real exposed employee credentials.
- Simulate ransomware attacks using tactics observed in active cybercrime groups.
- Identify shadow IT assets and forgotten subdomains that may have been leaked.
- Test authentication security by validating stolen credentials against corporate systems.
One striking example of intelligence-driven security testing involved analyzing stealer logs, datasets containing credentials stolen by infostealer malware. By examining these logs, security teams can identify credential reuse patterns, expose weak password practices, and simulate credential stuffing attacks before real adversaries do.
This intelligence is already being weaponized by threat actors, why not use it to enhance security testing instead?
We break down real-world examples of intelligence-led pentesting in our latest whitepaper. Sounds interesting? Get the full insights here!
From Data to Action: How SOCRadar’s Solutions Give You the Edge
Having access to Dark Web data and threat intelligence is only part of the equation. You need to know how to use it effectively. That’s where SOCRadar’s solutions come in:
Dark Web Monitoring: Detects leaked credentials, sensitive documents, and hacker forum chatter in real-time.
Threat Hunting Module: Analyzes stealer logs, malware behaviors, and leaked access credentials to simulate realistic attacks.
Attack Surface Management: Uncovers hidden entry points, misconfigured APIs, and exposed subdomains before attackers do.
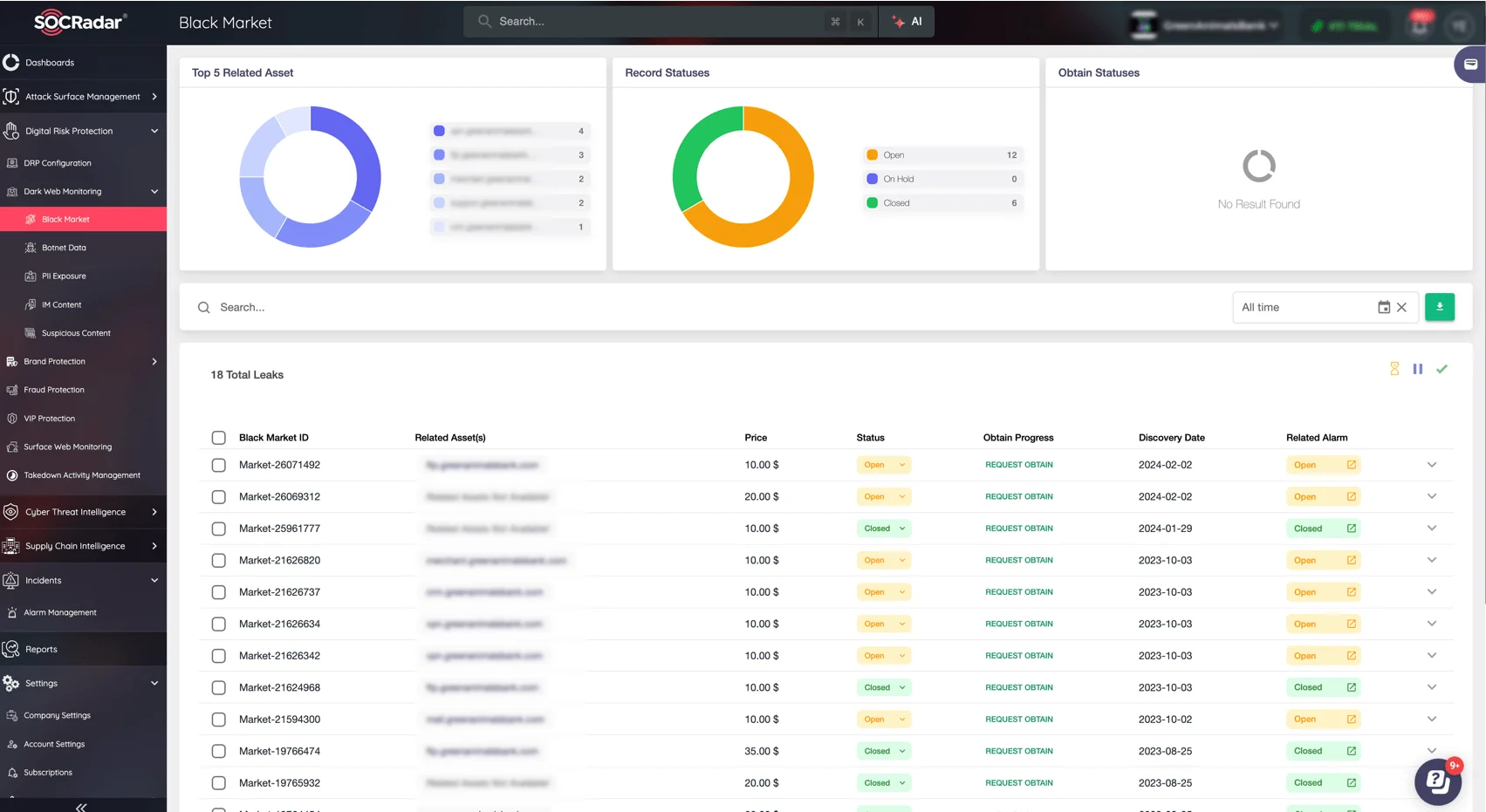
SOCRadar’s Dark Web Monitoring module
With the right intelligence, you can transform a standard security test into an adversary-level attack simulation. That’s the difference between checking the compliance box and actually improving security.
Final Thoughts: Are You Ready to Think Like a Threat Actor?
Cyber threats are evolving at an unprecedented pace. Organizations that continue to rely solely on conventional pentesting and Red Teaming methods risk overlooking critical security gaps. By integrating Threat Intelligence into security assessments, companies can simulate real-world adversary tactics, uncover hidden attack surfaces, and build a more resilient security posture.
To explore real-world case studies and methodologies for intelligence-led security testing, download our full whitepaper here.




































