
VBScript Is Retiring: From Scripting to Security Threats
VBScript is facing retirement as Windows moves forward. In future Windows releases, VBScript will be offered as a feature on demand before its eventual removal from the operating system. This ensures that users have time to adjust, allowing uninterrupted use as they prepare for its ultimate retirement.
With each new Windows client version, fresh features are introduced while older ones may be phased out, typically to make way for newer alternatives.
VBScript, originally designed as a scripting language for Windows automation and administrative tasks, has had a versatile history. While it was initially intended for legitimate use, it has also been leveraged by threat actors in creation and distribution of malicious software.
In this blog, we will explore the journey of VBScript from its inception as a scripting language to its encounters with malicious software. We will also examine notable examples where VBScript was used for nefarious purposes, shedding light on the evolving relationship between VBScript and cybersecurity threats.
The Birth of VBScript Malware
When Windows introduced VBScript as a scripting language in 1996, it marked a significant development in automation and administrative tasks. VBScript, with its simplicity and compatibility with Windows systems, quickly gained popularity among developers and IT professionals for legitimate scripting purposes.
However, this newfound capability did not go unnoticed by malicious actors. VBScript’s integration into the Windows environment provided threat actors with a powerful tool that could be exploited for nefarious purposes. It was not long before VBScript was utilized to create the first-known instances of VBS malware.
One of the early examples of VBS malware was the “ILOVEYOU” worm, which emerged in May 2000. It was a VBScript-based malware distributed via email as a love letter or a romantic message. When unsuspecting users opened the attachment, the worm executed, overwriting files, stealing passwords, and spreading itself to the victim’s email contacts. The ILOVEYOU worm demonstrated the destructive potential of VBS malware and served as a wake-up call to the cybersecurity community.
In the years that followed, VBS malware continued to evolve and diversify. Threat actors exploited VBScript’s capabilities to create various forms of malicious software, including trojans, worms, and downloaders, targeting both individuals and organizations.
What Are the Common Types of VBScript Malware?
In the realm of cybersecurity, the versatility of VBScript shines through as it finds applications across various types of malware. From Remote Access Trojans to downloaders, macro-based threats, and self-propagating worms, VBScript’s adaptability has made it a favored tool for malicious actors.
In this section, we explore some of the better known diverse categories of VBS malware, shedding light on the specific roles VBScript plays in their execution, propagation, and potential harm.
VBS-based RATs (Remote Access Trojans):
Remote Access Trojans (RATs) are a category of malware that disguises themselves as legitimate software but are crafted to execute malicious activities on your device. Unlike viruses and worms, Trojans cannot replicate themselves, but they can wreak havoc.
Various Remote Access Trojans have harnessed VBScript for activities like Command-and-Control (C2) communication, granting malicious actors remote access and control over compromised systems.
VBS Downloaders:
Downloaders, akin to trojans, belong to a category that encompasses diverse VBScript-based tools used for fetching and executing additional malicious payloads from the internet. These malware types excel at downloading various forms of malicious content, including code, software, adware, and more.
VBScript plays a pivotal role in the functioning of these downloaders, ensuring the retrieval and execution of malicious payloads from remote servers.
VBS Macro Malware:
Cybercriminals often deploy macros that are embedded within Microsoft Office documents to enable by VBScript and deliver malware. This method is frequently employed through phishing emails.
Macros serve as a vehicle for the delivery of malware, allowing cybercriminals to target unsuspecting users via malicious documents.
While macros were previously enabled by default, the feature has been disabled, and Microsoft started to block Office macros in the Mark of the Web (MotW) labeled Office files in 2022. The phasing out of VBScript could also potentially impact cybercriminals’ use of macros in their malicious activities, and they may need to adapt to new techniques and strategies for delivering malware through macros.
VBS Worms:
Worms written in VBScript are capable of spreading through various means, including email attachments. These worms have been utilized to deliver other forms of malware and to propagate themselves.
What Are Some of the Known Malware That Used VBScript?
VBScript left a mark on cybersecurity history as it was harnessed by the infamous virus, named ILOVEYOU’, and its influence persists in contemporary malware.
In this section, we embark on a journey through the intricate landscape of VBS malware, exploring how VBScript has been utilized in a range of malicious software, from its earliest instances to its continued presence today.
ILOVEYOU Worm (Love Bug, Love Letter):
The “ILOVEYOU” computer worm, which surfaced on and after May 5, 2000, made a significant impact by infecting over ten million Windows personal computers. It propagated primarily through email, featuring the subject line “ILOVEYOU” and an attached file named “LOVE-LETTER-FOR-YOU.TXT.vbs.”
At that time, Windows systems typically concealed the “.vbs” file extension (representing a Visual Basic script) by default since it was a recognized file type, often leading unsuspecting users to perceive it as a standard text file. Upon opening the attachment, the embedded Visual Basic script was activated, initiating the infection process.
Code Red Worm:
The Code Red worm emerged in 2001 and exploited a vulnerability in Microsoft IIS web servers. While its primary payload was written in C, certain variants incorporated VBScript as part of their propagation technique, enhancing their ability to spread and infect vulnerable systems.
Emotet Loader Malware:
Emotet, a highly sophisticated malware strain, frequently serves as a delivery mechanism for other malicious software, such as banking trojans and ransomware. To facilitate its infiltration and propagation, Emotet utilizes VBScript in conjunction with macro-enabled documents to compromise systems.
You can learn more about this loader malware on our blog post:
What is EMOTET Malware and How to Protect Yourself
Dridex Trojan:
Dridex is a notorious banking trojan that has been used in multiple campaigns to steal financial data. This malware leverages various techniques for its distribution, often relying on phishing emails that contain malicious attachments. These attachments frequently use VBScript and macros embedded within Microsoft Office documents to entice victims into activating them, facilitating the malware’s infiltration and data theft.
Additionally, Dridex has been known to exploit vulnerabilities in widely used software, such as the specific vulnerability CVE-2017-0199 in Microsoft Office and WordPad, allowing for remote code execution.
Find out more about Dridex malware on CISA’s advisory.
GandCrab Ransomware:
Although active until early 2019, GandCrab made a significant impact as a prolific ransomware campaign. It utilized VBScript as a crucial component to deliver and execute its ransomware payload in campaigns involving malicious Word files distributed through spam emails.
Microsoft Office macros played a key role in enabling the VBS script to run and install the ransomware payload, aiding attackers in infecting machines.
TrickBot Trojan:
TrickBot, primarily recognized as a banking trojan, features a modular structure and utilizes various scripting languages, including VBScript. This flexibility empowers TrickBot to perform a wide range of malicious activities, further enhancing its notoriety in the threat landscape.
The TrickBot trojan has used VBS alongside malicious macros and has exploited the CVE-2017-0199 vulnerability – the same vulnerability in Microsoft Office exploited by Dridex – to achieve successful attacks.
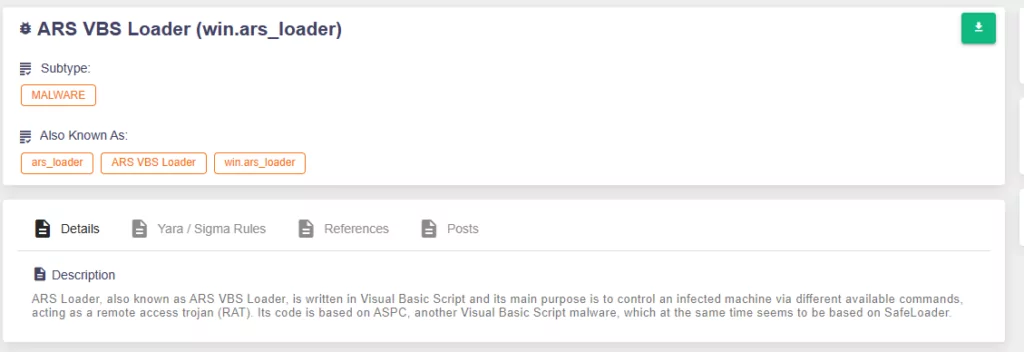
ARS Loader:
ARS Loader, also recognized as ARS VBS Loader, is a malicious script written in VBS. Its primary function is to assume control over a compromised system by executing various commands, effectively serving as a Remote Access Trojan (RAT).
QakBot (Qbot) Malware:
QakBot, also known as Qbot, is a multifaceted malware with a range of capabilities, including acting as a banking trojan, a worm, and a Remote Access Trojan. QakBot demonstrates the ability to download and execute malicious scripts, including VBScript, to achieve its objectives.
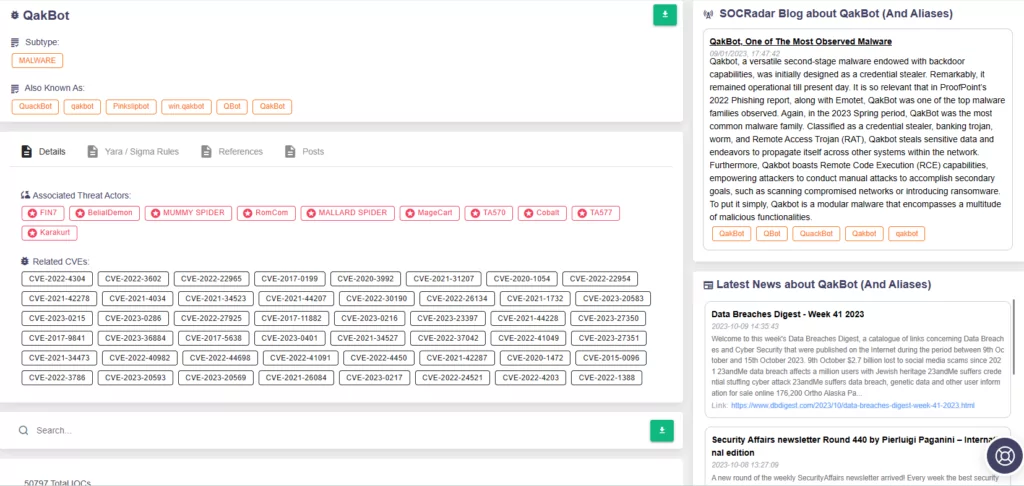
You can learn more about QakBot malware on our blog post: QakBot, One of The Most Observed Malware
Conclusion
In this journey from scripting to security threats, we have explored the multifaceted world of VBScript, a versatile tool that has transitioned from legitimate scripting to a favored choice for cybercriminals. From the early days of automation to the emergence of sophisticated malware, VBScript has left an indelible mark on the cybersecurity landscape.
While this blog post highlights several well-known examples of malware using VBScript, there are numerous other instances and evolving threats. For comprehensive information and up-to-date insights, you can explore our platform.
As we bid farewell to VBScript with Windows’ announcement, it is crucial to recognize that the threat landscape continues to evolve. The use of VBScript in modern malware has significantly declined due to increased security measures and the discontinuation of VBScript. However, threat actors constantly adapt and exploit new vulnerabilities. To stay ahead in this ever-changing environment, organizations must remain vigilant.
Threat intelligence platforms like SOCRadar are valuable resources in this battle. With SOCRadar’s intelligence-rich platform, organizations can access critical insights and receive timely alarms on threats, including those highlighted in this blog post. By embracing proactive cybersecurity measures and leveraging the right tools, we can navigate the evolving threat landscape with resilience and security.



































