VMware Vulnerability Exploit, Invicta Stealer, and Source Code Sales
This week’s headlines feature some developments that highlight the ongoing threats posed by cybercriminals. First up, we have news of a remote code execution exploit for VMware Workspace ONE that has been shared on the dark web, potentially putting many organizations at risk. In addition, we’ve learned about a new strain of malware called Invicta Stealer that is being shared among cybercriminals. On top of this, an American e-commerce company has been hit with an unauthorized admin access sale while the source code and backup file of MarineTraffic are up for sale. Last but not least, AlphVM BlackCat ransomware announced its latest victim: Constellation Software.
Here are the details on these issues.
Find out if your data has been exposed.
Find out if your data has been exposed.
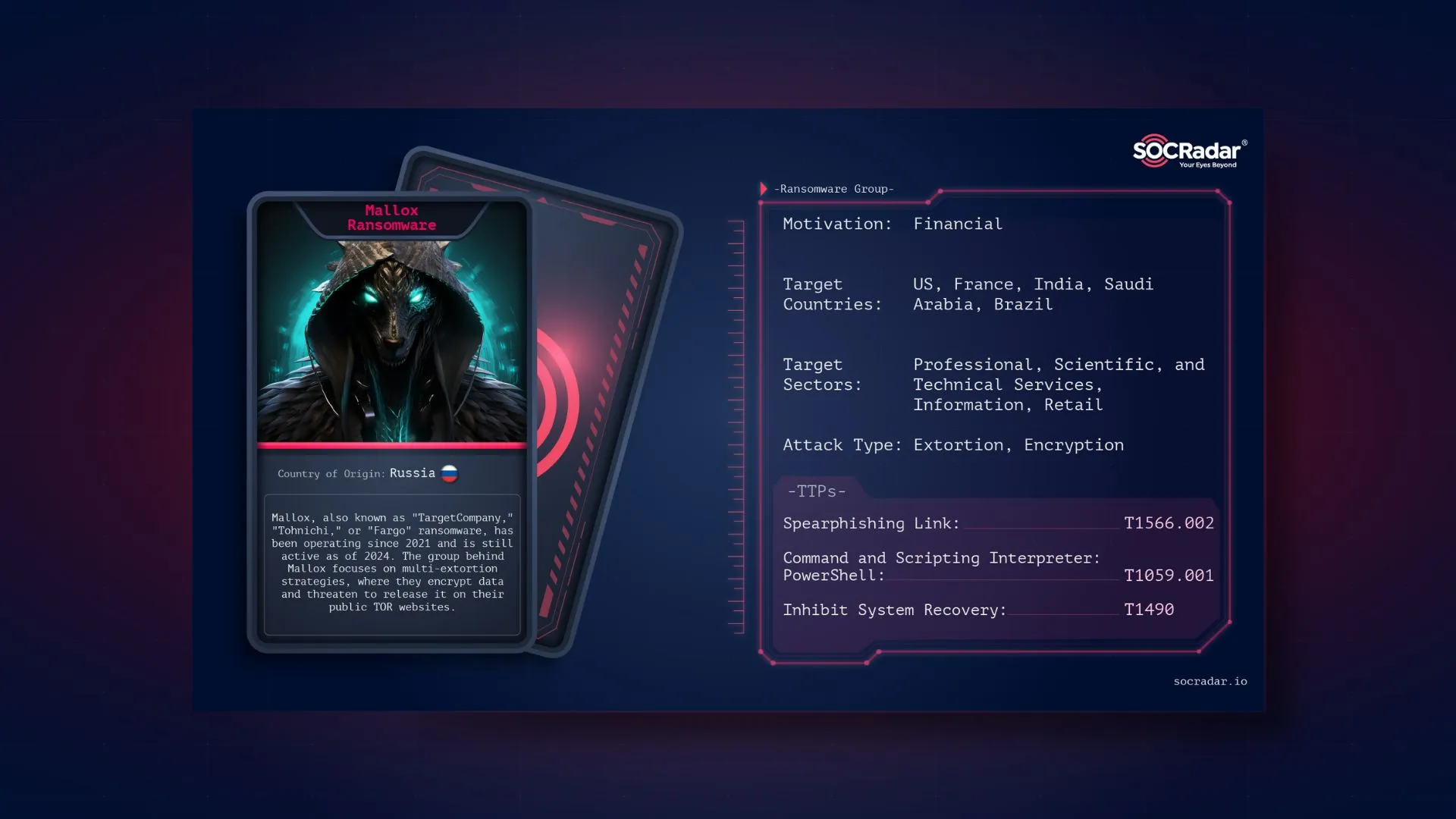
Remote Code Execution Exploit for VMware Workspace ONE is Shared
SOCRadar dark web analysts have detected a post detailing a remote code execution (RCE) exploit for VMware Workspace ONE. The threat actor shared a Metasploit module that targets multiple vulnerabilities, specifically CVE-2022-22956, CVE-2022-22957, and CVE-2022-22960.
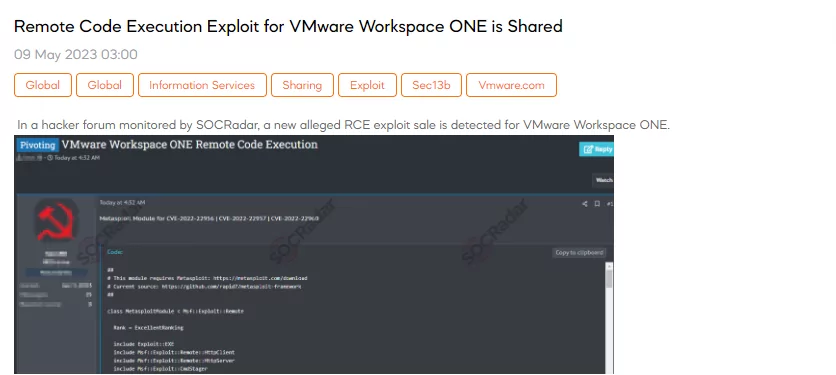
A New Invicta Stealer is Shared
SOCRadar dark web analysts have discovered a post where a threat actor claims to have developed a potent native stealer called Invicta Stealer. The post describes Invicta Stealer as an actively improved C++ tool with contributions from the community. It allegedly targets various browsers, Discord, crypto wallets, sensitive directories and files, FTP clients, gaming clients, and password managers and collects system information. The threat actor also mentions the use of anti-analysis techniques.
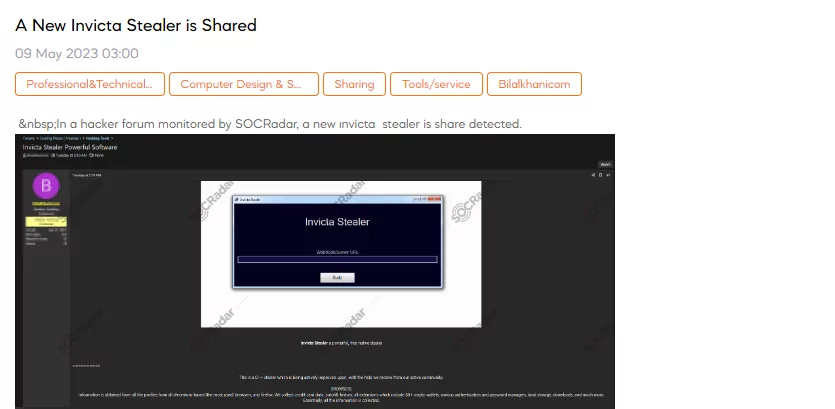
Unauthorized Admin Access Sale is Detected for an American E-commerce Company
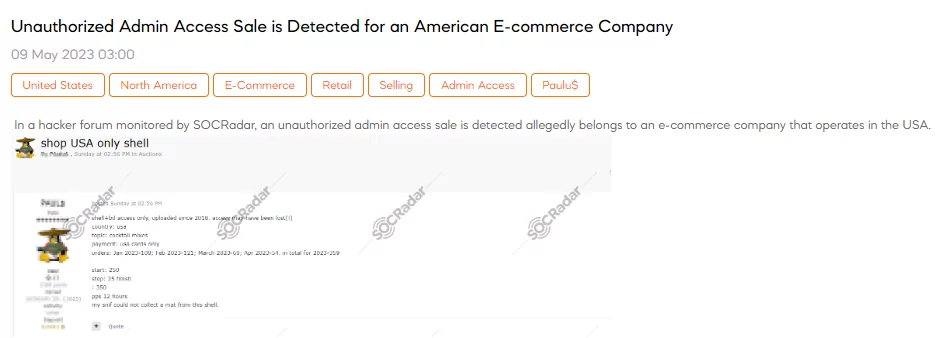
SOCRadar dark web team has discovered a post on a hacker forum. The post claims to have detected unauthorized admin access for sale, targeting an e-commerce company in the U.S. The compromised access, uploaded in 2018, may have been lost over time. The threat actor’s post reveals that the e-commerce company specializes in cocktail mixes and accepts payment only through US cards. With a total of 359 orders placed in 2023, the severity of the breach becomes apparent. Immediate action should be taken by the e-commerce company and law enforcement agencies to investigate and address this potentially significant security threat.
Source Code and Backup File of MarineTraffic is on Sale
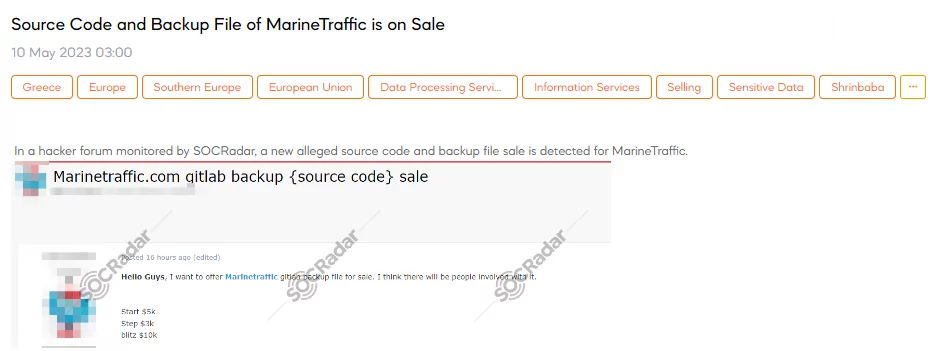
On May 10, a SOCRadar researcher identified a post where a threat actor claimed to have a Marinetraffic Gitlab backup file for sale. The threat actor believes that interested parties will be in this illicit business endeavor. The price for the backup file is initially set at $5,000, with subsequent increments of $3,000 and a final price of $10,000.
The New Ransomware Victim of AlphVM Blackcat: Constellation Software
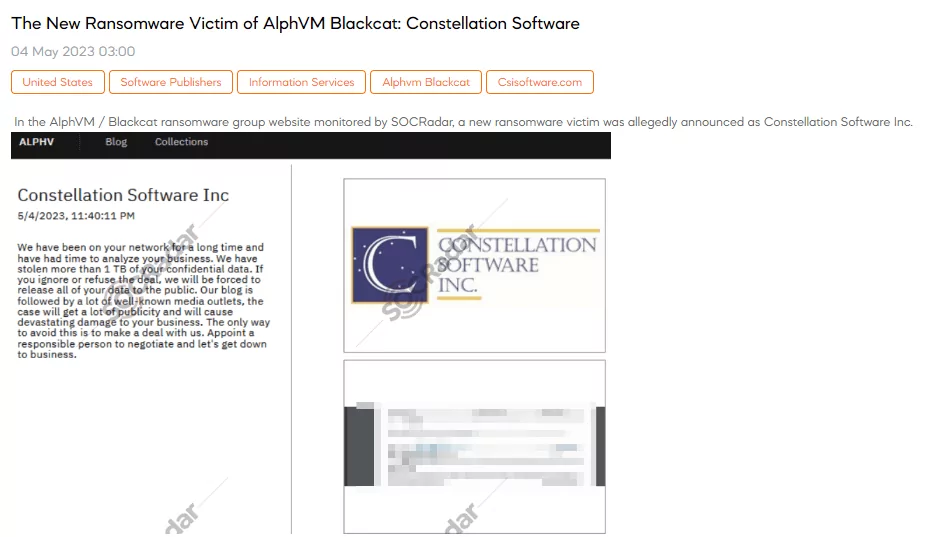
A SOCRadar researcher discovered a post claiming that the AlphVM BlackCat gang had added Constellation Software to its victim list. The threat actor claimed to have been present on Constellation Software’s network for an extended period, allowing them ample time to analyze the company’s operations. They claim to steal over 1 TB of highly confidential data.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.