
VPN Exploit, ATM Malware, and Database Leaks of MediSecure, Indian Voter Portal, and PetroERP
The SOCRadar Dark Web Team has uncovered several critical cyber threats within the past week. Among these findings are a zero-day exploit for the Pulse Connect Secure VPN, the sale of extensive customer databases from PetroERP and MediSecure, new malware targeting global ATM systems, and a significant leak of the Indian Voter Portal database.
Receive a Free Dark Web Report for Your Organization:
0-Day Exploit for Pulse Connect Secure VPN on Sale
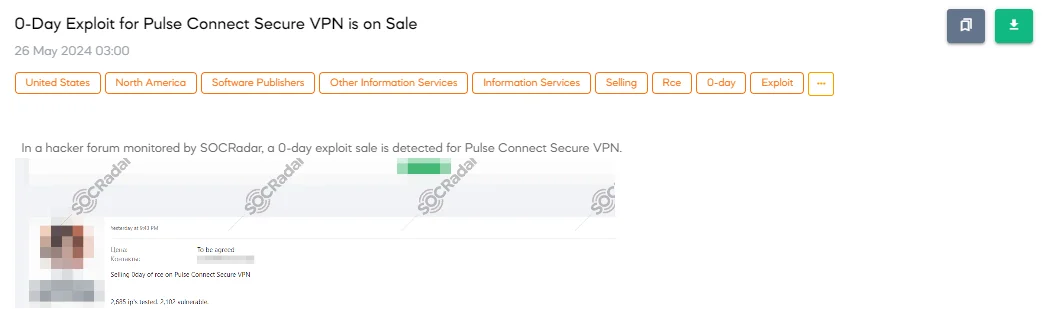
The SOCRadar Dark Web Team has detected a post in a hacker forum that a threat actor is allegedly selling a 0-day exploit for Pulse Connect Secure VPN. The threat actor claims the exploit has been tested on 2,685 IPs, with 2,102 found vulnerable. They are accepting payments in XMR and BTC and provided contact details for potential buyers.
The Alleged Customer Database of PetroERP is on Sale
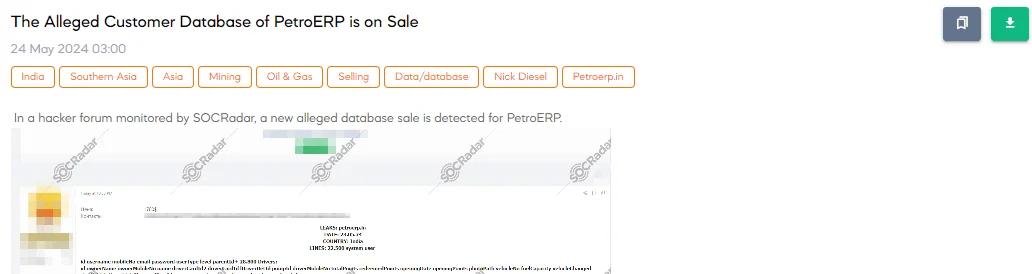
The SOCRadar Dark Web Team has detected a post in a hacker forum that a threat actor claims to have a new alleged database for sale, involving PetroERP. The threat actor states that the database contains sensitive information, including:
- System Users: 22,500 entries with user IDs, usernames, mobile numbers, emails, passwords, user types, levels, and parent IDs.
- Drivers:28,800 entries with driver IDs, owner names, owner mobile numbers, names, driver card IDs, pump IDs, driver mobile numbers, total points, redeemed points, opening dates, opening points, photo paths, vehicle numbers, fuel capacities, vehicle changes, DSM vehicle numbers, vehicle photos, refEmp IDs, usernames, activity statuses, creation dates, update dates, and updated by.
The threat actor also provided details about the company, mentioning that there are about 56,000 gas station owners across India who provide various petroleum products like petrol, diesel, and CNG on credit and cash basis.
A New Malware for ATM (Automated Teller Machine) is on Sale
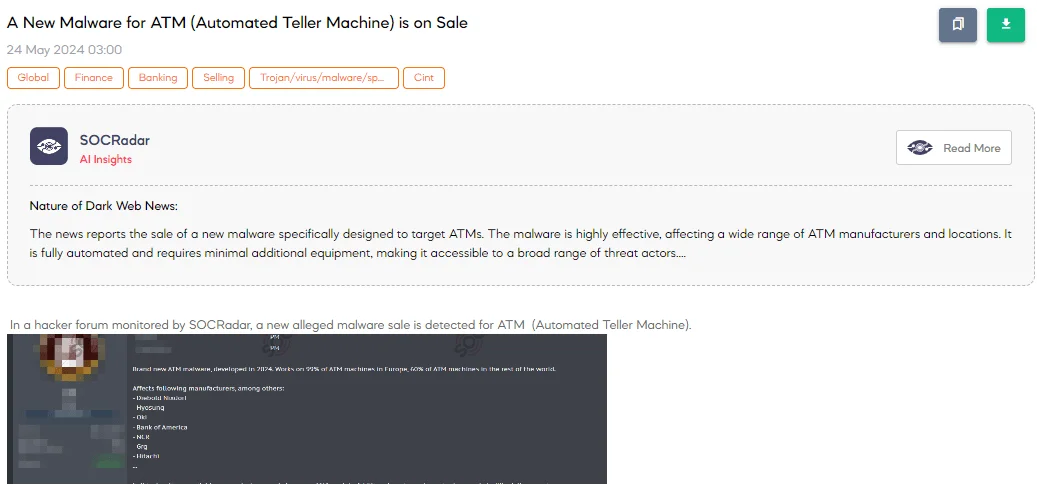
The SOCRadar Dark Web Team has detected a post in a hacker forum that a threat actor claims to be selling a new malware designed for Automated Teller Machines (ATMs). The alleged malware, developed in 2024, purportedly works on 99% of ATM machines in Europe and 60% of machines worldwide.
The malware is said to affect several manufacturers, including Diebold Nixdorf, Hyosung, Oki, Bank of America, NCR, GRG, and Hitachi. It comes with full instructions and operator’s manuals for many ATM models.
The Alleged Database of MediSecure is on Sale
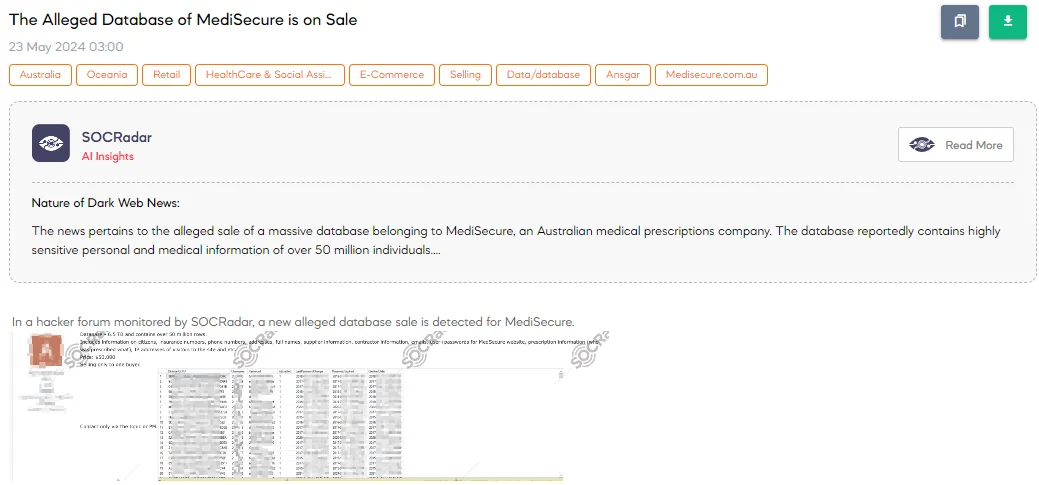
The SOCRadar Dark Web Team detected a post in a hacker forum that a threat actor claims to be selling a database of MediSecure, a former Australian medical prescriptions company. The alleged database is 6.5 TB in size and contains over 50 million rows of sensitive information, including citizen details, insurance numbers, phone numbers, addresses, full names, supplier and contractor information, emails, hashed passwords for the MediSecure website, prescription information, and IP addresses of site visitors. The asking price is $50,000, with the sale intended for a single buyer.
MediSecure has responded to this claim, stating: “MediSecure is aware that a data set containing the personal information and limited health information of our customers has been made available on a dark web forum. We urge Australians to not go looking for this data. Accessing stolen sensitive or personal information on the dark web only promotes future cyber criminal activities against Australian businesses. While MediSecure is urgently working towards notifying the impacted individuals, we wish to reiterate and reassure the Australian community that this cyber security incident does not impact any ongoing access to medication.”
MediSecure Ends Incident Investigation; 12.9 Million Australians Affected
As of July 18, 2024, MediSecure announced that it has ceased its investigation into the cyber incident. The company confirmed that approximately 12.9 million Australians had their personal and sensitive information, including contact and health information, stolen by a malicious third-party actor.
The breach was first reported in May 2024, and MediSecure went into voluntary administration in June 2024 due to the financial strain caused by the cyber incident. The Australian Federal Police continue to investigate the incident.
In a public statement, MediSecure detailed that the affected data included full names, phone numbers, dates of birth, home addresses, Medicare numbers, and Medicare card expiry dates, among other sensitive information.

MediSecure’s statement about the breach, dated July 18, 2024. Read the full statement here.
Despite the breach, there is no impact on the current national prescription delivery service, and Australians are advised to continue accessing their medications and filling their prescriptions as usual. MediSecure emphasized that it is not currently part of Australia’s digital health network and has no connections to the prescribing and dispensing of medications.
Furthermore, the Australian Government has refreshed its advice to Australians on protecting themselves in light of this breach, available on the Department of Home Affairs website. MediSecure implores individuals and organizations not to search for the stolen data online, as doing so could further the potential harm to Australians and may constitute a criminal offense.
Alleged User Database of Indian Voter Portal Leaked
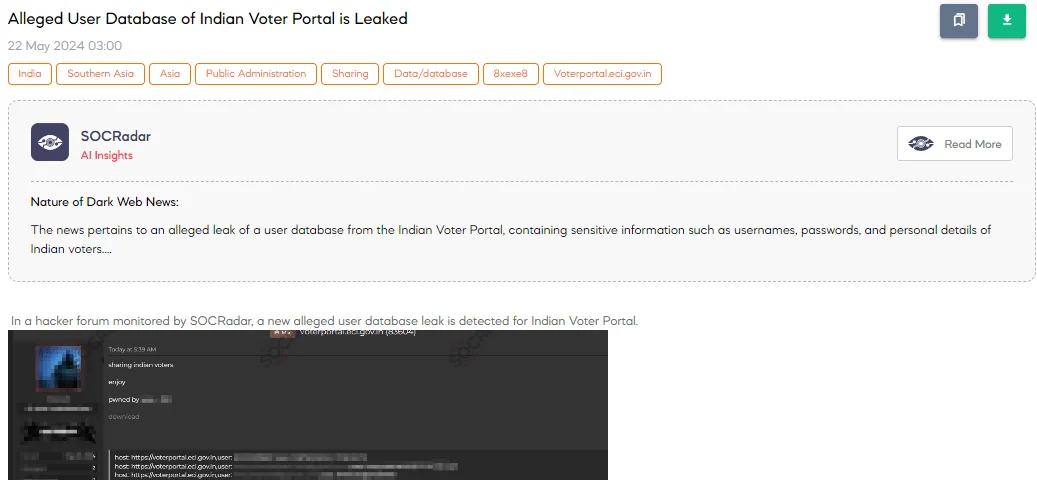
The SOCRadar Dark Web Team detected a post in a hacker forum that a threat actor claims to have leaked a user database for the official portal provided by the Election Commission of India for Indian citizens (https[:]//voterportal[.]eci[.]gov[.]in). The alleged leak includes credentials such as usernames and clear passwords for more than 20 accounts.
Upon querying some of the credentials using SOCRadar’s Threat Hunting module, it was found that these credentials had been previously shared on various Telegram channels and other dark web platforms. Additionally, a search for “voterportal.eci.gov.in” revealed more than 50 stealer log records.
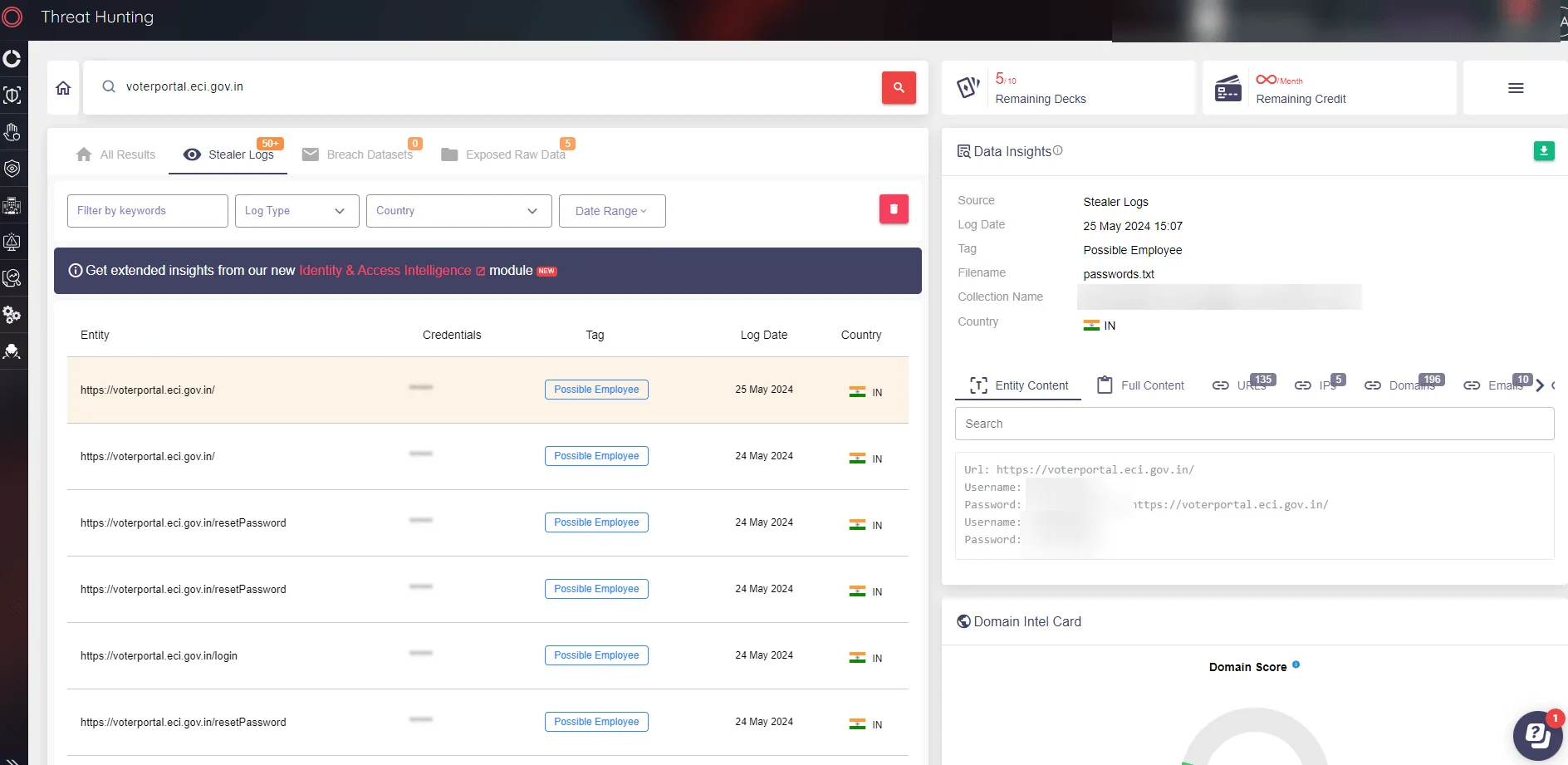
SOCRadar Threat Hunting
This indicates that the threat actor likely scraped the data from stealer logs, Telegram channels, or other dark web platforms. The breach potentially compromises the security and privacy of numerous Indian voters, posing significant risks of identity theft and fraud.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































